Kerberos authentication protocol uses tickets for verifying the identities and thereby enabling trusted communication in a network. It facilitates mutual authentication where the user and the server verifies each other's identity.
This protocol is built on symmetric key cryptography and requires a trusted third party. It may also use the public-key cryptography to intensify the authentication process during certain phases. By default, Kerberos uses UDP port 88.
Fun fact:Did you know that the name was taken from the Greek mythology? Kerberos (Cerberus) was believed to be a ferocious three-headed dog that guards the gates of Hades.
Kerbaroasting is an attack method that allows an attacker to take advantage of how service accounts leverage Kerberos authentication with Service Principle Names (SPN). It allows the attacker to crack the passwords of the service accounts in Active Directory. Cracking the password is often done offline to avoid being detected. While the attacker doesn't exploit any security loophole, all that is being done is using the working of the protocol to get into the network and persist.
Step 1: The first step involves scanning the Active Directory for user accounts with SPN values set and AdminCount =1. This is done using several techniques such as PowerShell and LDAP queries, using the default scripts in Kerberoast toolkit, or using PowerSploit.
Step 2: After listing down the targeted accounts, request service tickets from AD using the SPN values.
Step 3: Extract the service tickets and hashes to the memory using tools like Mimikatz and save the information to a file.
Step 4: Brute force the encrypted passwords to obtain the actual clear text.
Step 5: Using the user accounts with privileges, move laterally or cause destruction.
Note: It's easy to crack service accounts as their passwords rarely change. Moreover, since the cracking happens offline, it'll not cause any domain traffic or account lockouts. Hence, it is undetectable.
Log360 is an unified SIEM solution with integrated DLP and CASB capabilities which provides threat detection and response, correlation, alerts, and reporting. These features can help detect and mitigate attacks related to kerberoasting.
Here are some common Event IDs related to Kerberos in a Windows environment
| Event ID | Event type | Description |
|---|---|---|
| 4768 | Success, Failure | This event is logged when a Kerberos authentication ticket (TGT) is requested by domain controller. |
| 4769 | Success, Failure | This event is logged for a Kerberos Ticket Granting Service (TGS) ticket request. |
| 4770 | Success | This event is logged when a Kerberos service ticket is renewed. |
| 4771 | Failure | This event is logged when a Kerberos pre-authentication failed. |
| 4772 | Failure | This event is logged when a Kerberos authentication ticket request has failed. |
Setup a honeypot Kerberos Service Account
Malicious actors often search a domain controller for accounts with service principle names (SPNs). So, security admins can set up a Kerberos service honeypot account by creating a service or user account with fake SPNs. Since these service accounts are not linked to the real services running for them, any request raised for these decoy accounts won't be valid and can be helpful to detect kerberoasting activity.
An alert for suspicious Kerberos TGS requests
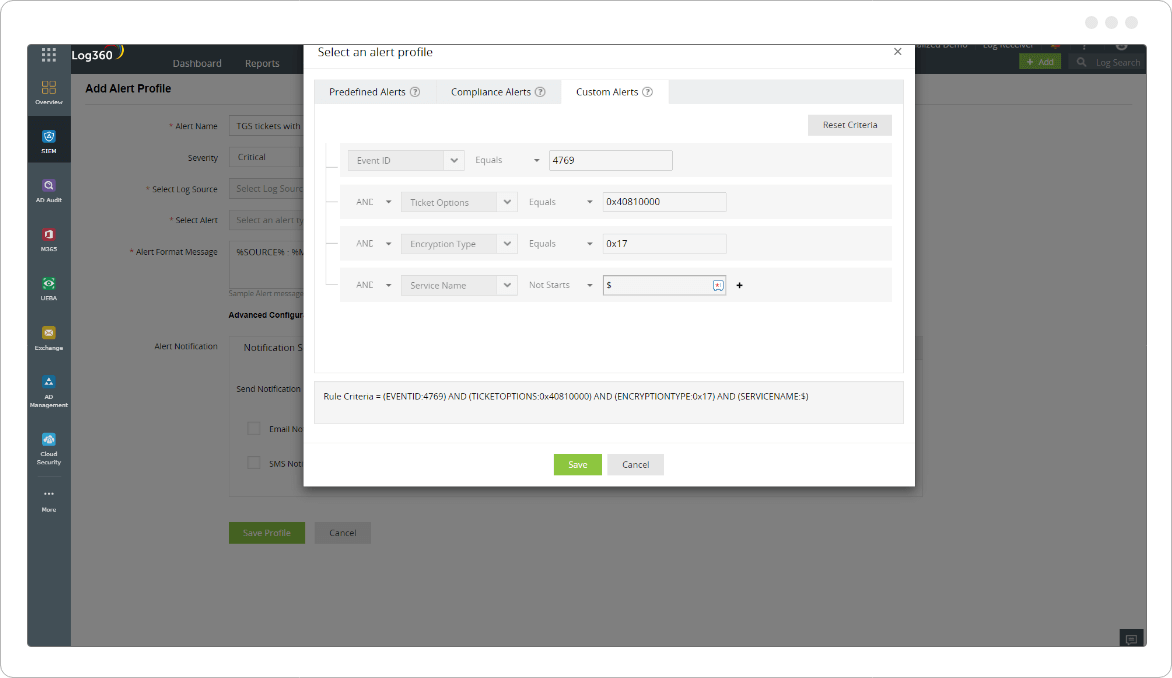
Examining Event ID 4769 in general is a tedious task as Kerberos Ticket Granting Service (TGS) requests take place most of the time to access resources. Therefore, security analysts should filter these events and monitor Event ID 4769 (Kerberos TGS was requested), and be on alert if:
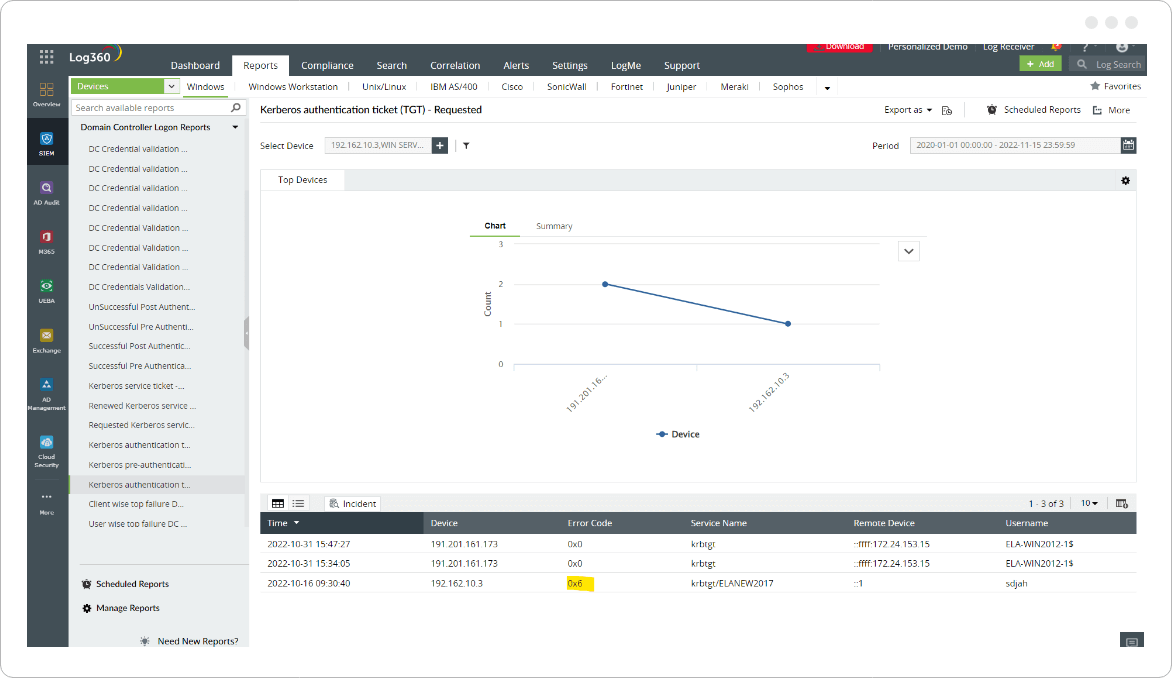
Log360 collects security log data and also has 1,000+ built-in reports to assist threat hunters track any important changes taking place, providing details about any cyber events.
It also provides detailed reports on Kerberos-related events, helping security analysts to respond quickly and effectively to mitigate the impact of an attack.
For instance, in the images above we can see the encryption type 0x17 (Kerberos RC4 encrypted tickets) for Kerberos TGS request. 0x17 is an encryption type specified for RC4 and is a weaker encryption compared to 0x12, and it is rare to see in logs. Adversaries try to use it to raise tickets as it is easier for them to crack the hash offline.
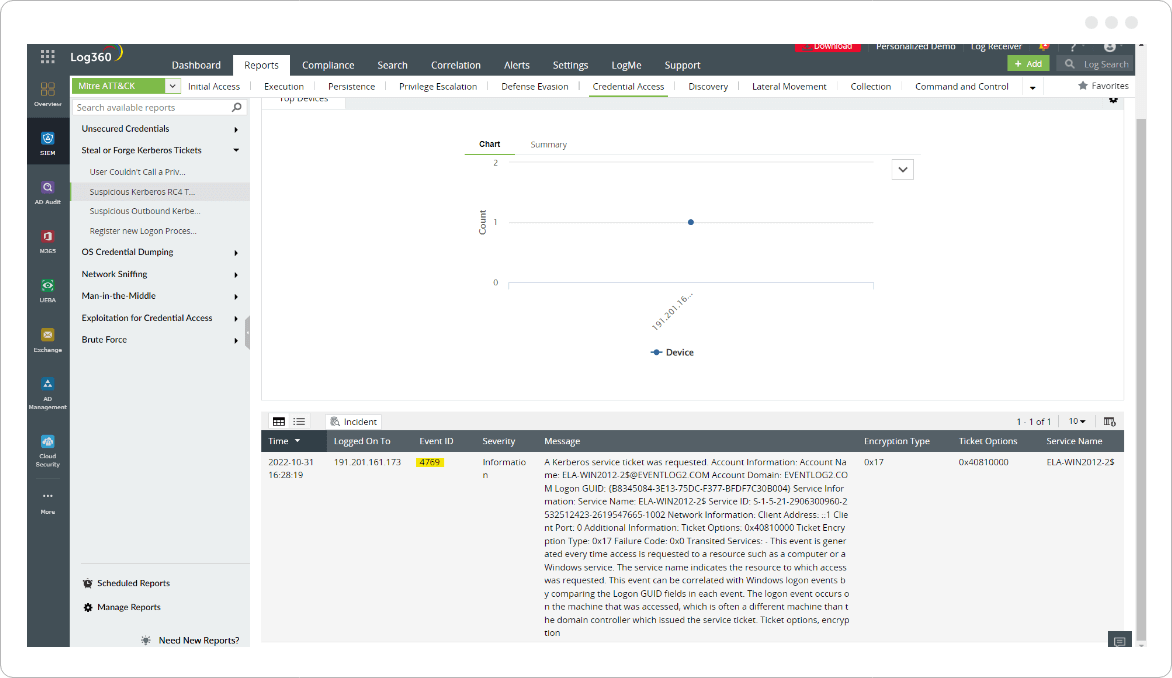
The Suspicious Kerberos RC4 Ticket Encryption report shows the Event Id 4769 being logged with encryption type 0x17. This event is generated every time the Key Distribution Center (KDC) receives a Kerberos TGS ticket request.
Event ID 4771 is generated every time the Key Distribution Center fails to issue a Kerberos Ticket Granting Ticket (TGT). Examine when Event ID 4771 is generated along with error code 0x18, which indicates a bad password.
ManageEngine Log360, a comprehensive SIEM solution, helps you to detect and contain kerberoasting and other AD-based attacks. The solution's real-time correlation engine comes with predefined rules that are drafted based on the indicators of compromise (IoCs) for these attack. Upon attack detection, Log360 provides you with real-time notifications and automates the remediation workflow. It can also raise attacks as an incident ticket in your central help desk control to ensure accountability in resolution. That's not all Log360 can do, explore more about it here.
Downloaded the FBI Checklist Ebook
Zoho Corporation Pvt. Ltd. All rights reserved.