Fortinet log analyzer
If you want to prevent potential threats to your network from turning into full-blown attacks, you need to monitor your logs regularly. However, manually sifting through hundreds of logs daily to find security events of interest is no easy task. Our comprehensive log management solution, EventLog Analyzer, can simplify the entire process for you.
EventLog Analyzer can collect logs from Fortinet's FortiGate firewalls, analyze them, and generate graphical reports that can help you monitor the key security events happening in your network.
Monitoring FortiGate firewall logs using EventLog Analyzer
Analyze network threats using FortiGate log reports
EventLog Analyzer includes predefined graphical reports that are generated instantly when logs are collected. These reports can help you analyze the network for possible security threats and meet various compliance regulations such as PCI DSS, HIPAA, and GDPR. In the event of a compliance violation, an alert will be generated immediately. You can also schedule these reports to be generated at regular intervals and export them in PDF or CSV formats.
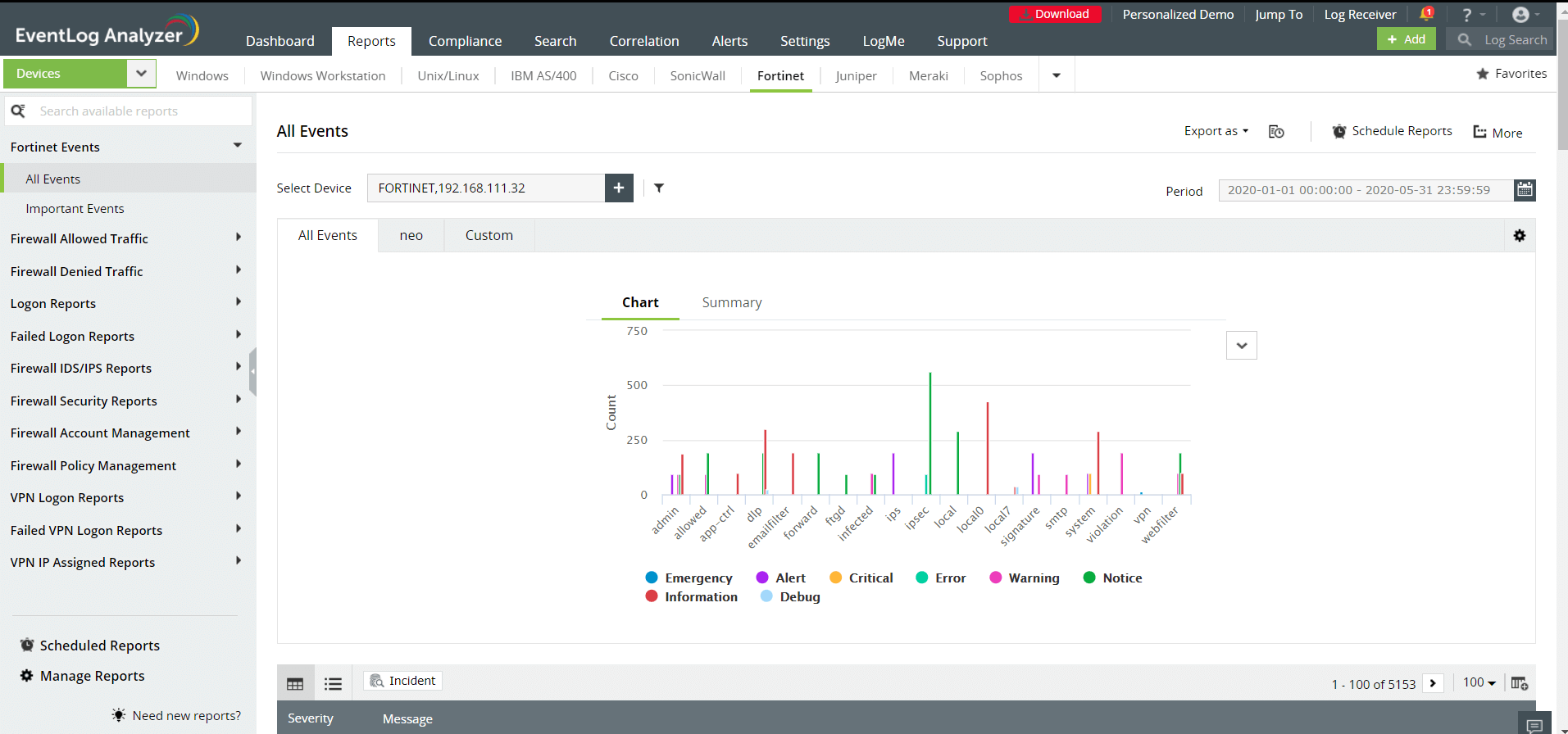
Here are some of the reports generated by EventLog Analyzer for Fortinet devices:
- Fortinet Events: The reports in this category provide information regarding all events taking place on Fortinet devices, along with their severity levels.
Available Reports
All Events | Important Events
- Firewall Allowed Traffic | Firewall Denied Traffic: The reports in these two categories provide information regarding traffic that has been allowed or denied entry into the network. The traffic is categorized by source, destination, protocol, and port. Information about traffic trends is also included.
Available Reports
Allowed Traffic | Top Traffic based on Source | Top Traffic based on Protocol | Top Traffic based on Port | Allowed Traffic Trend | Denied Connections | and more
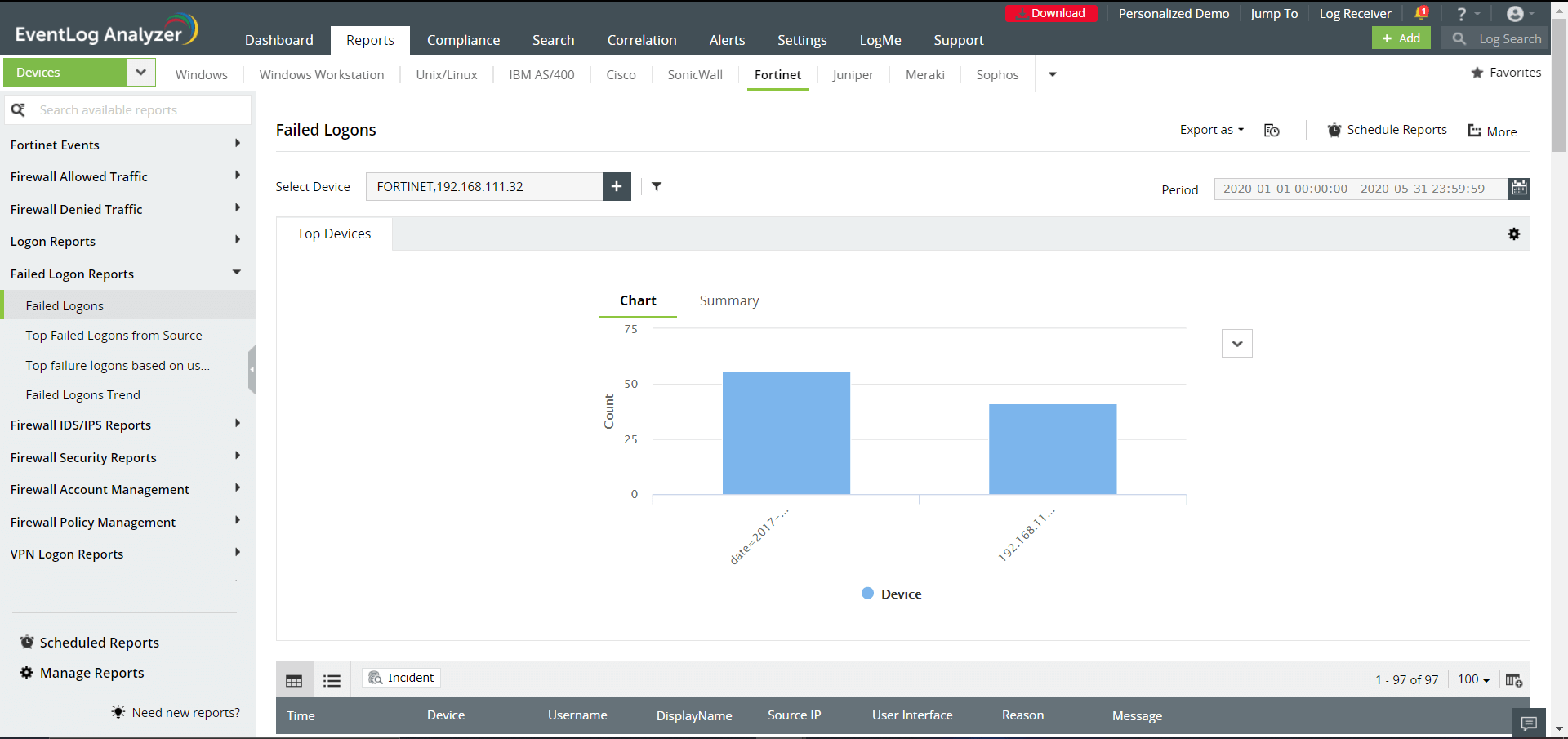
- Logon Reports | Failed Logon Reports: These two categories include reports regarding successful and failed logons, which are categorized by source IP address and username. The reports also include information on logon trends.
Available Reports
Logons | Top Successful Logons from Source | Top logons based on users | Logons Trend | Failed Logons | Top Failed Logons from Source | Top failure logons based on users | Failed Logons Trend
- VPN Logon Reports | Failed VPN Logon Reports: These two categories include reports regarding successful and failed VPN logons, which are categorized by remote device IP address and username. The reports also include information on VPN logon trends.
Available Reports
VPN Logout | VPN Logons | Top VPN logons based on Remote devices | Top VPN Logon based on users | Failed VPN Logons | Top Failed VPN Logons based on User | and more
- Firewall IDS/IPS Reports: The reports in this category provide information regarding possible and critical attacks, which are classified by source IP address and destination IP address. The reports also include information on attack trends.
Available Reports
Possible Attacks | Critical Attacks | Top Attacks | Top Attacks based on Source | Top Attacks based on Destination | Attacks Trend
- Firewall Policy Management: These reports provide information regarding firewall policies that have been added, modified, or deleted.
Available Reports
Policy Added | Policy Modified | Policy Deleted
- Device Severity Reports: This category includes reports of various events based on their severity.
Available Reports
Emergency Events | Alert Events | Critical Events | Error Events | Warning Events | Notice Events | Information Events | Debug Events
EventLog Analyzer also allows you to create custom reports based on your requirements. Click here to learn more.
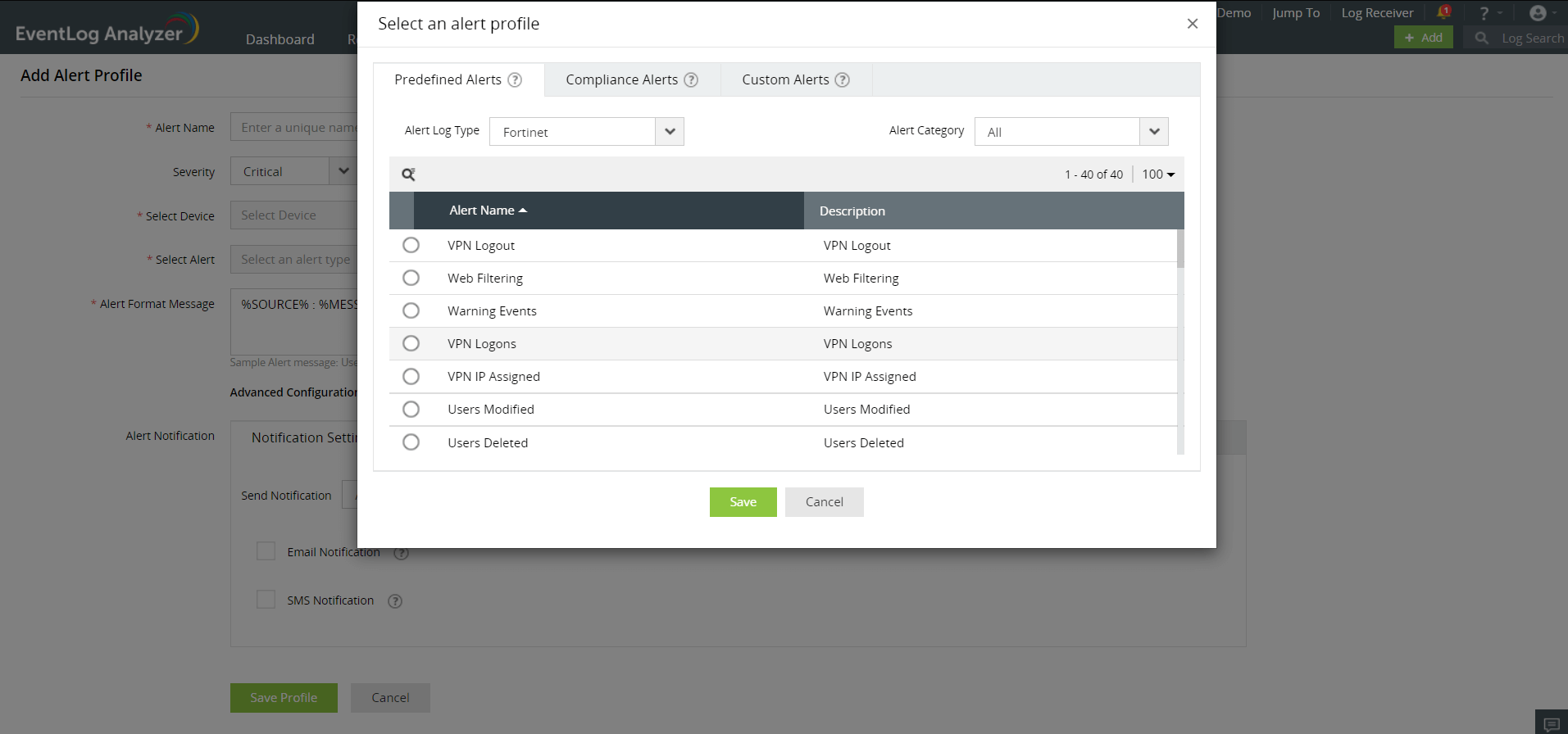
Get notified when suspicious events occur with real-time alerts
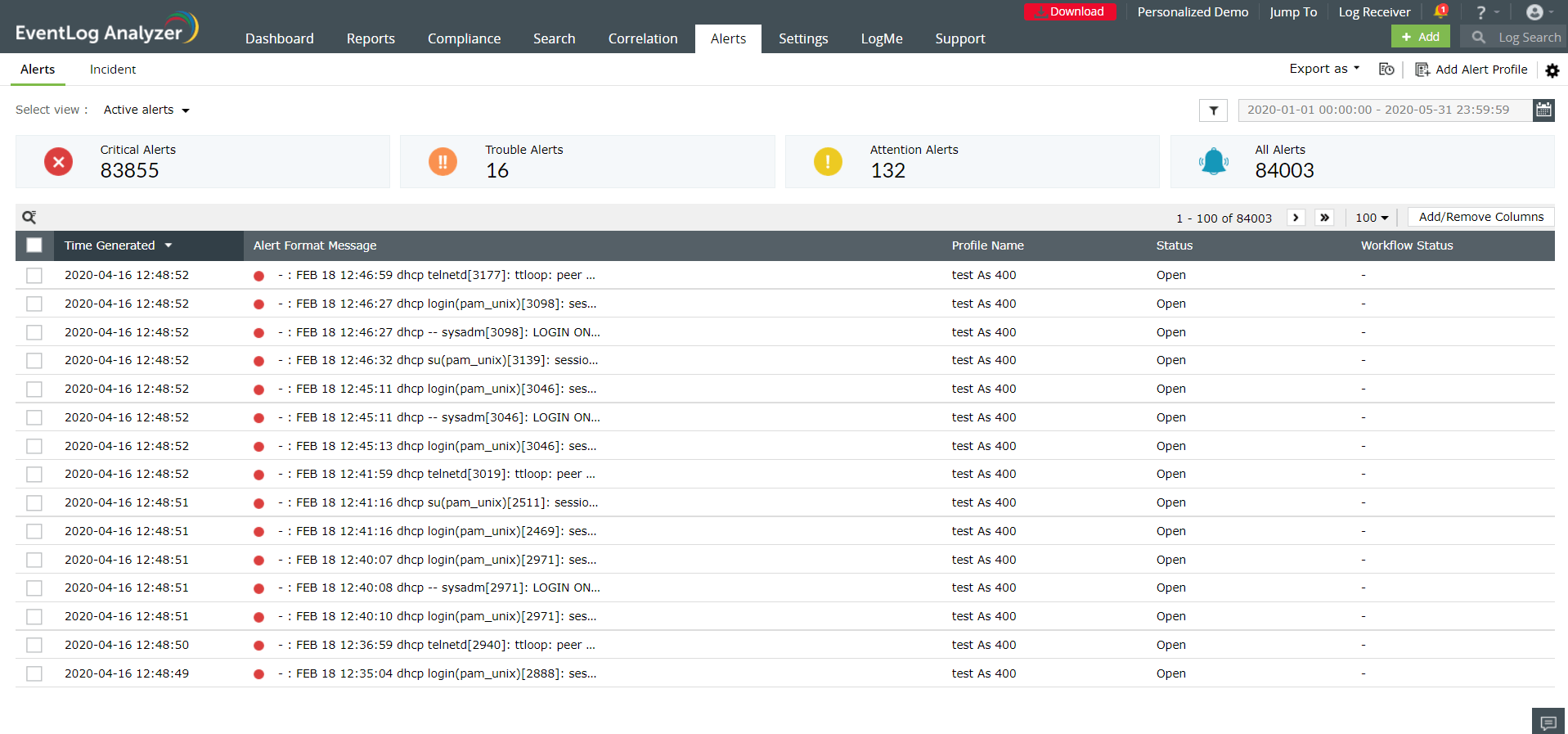
Minimize the amount of time spent on detecting and responding to any attack with the help of EventLog Analyzer's real-time alerting system. Whenever there is any sign of a threat in your network, alerts will be triggered, and EventLog Analyzer will immediately notify you via email or SMS.
The alerts have three severity levels: Attention, Trouble, and Critical. The severity level will help you prioritize the alerts so that you can remediate the most critical ones immediately.
With EventLog Analyzer, you can set up alerts to monitor specific events on Fortinet devices, such as denied connections, failed logons, system shutdowns, modified policies, and VPN logouts.