- Home
- Logging Guide
- How to create user in Linux
How to create a user in Linux
In this page
- How to create a user in Linux using:
- The adduser command
- The useradd command
- Setting a password for the new user
- Verifying user creation
- Customizing user settings
- Best practices for Linux user management
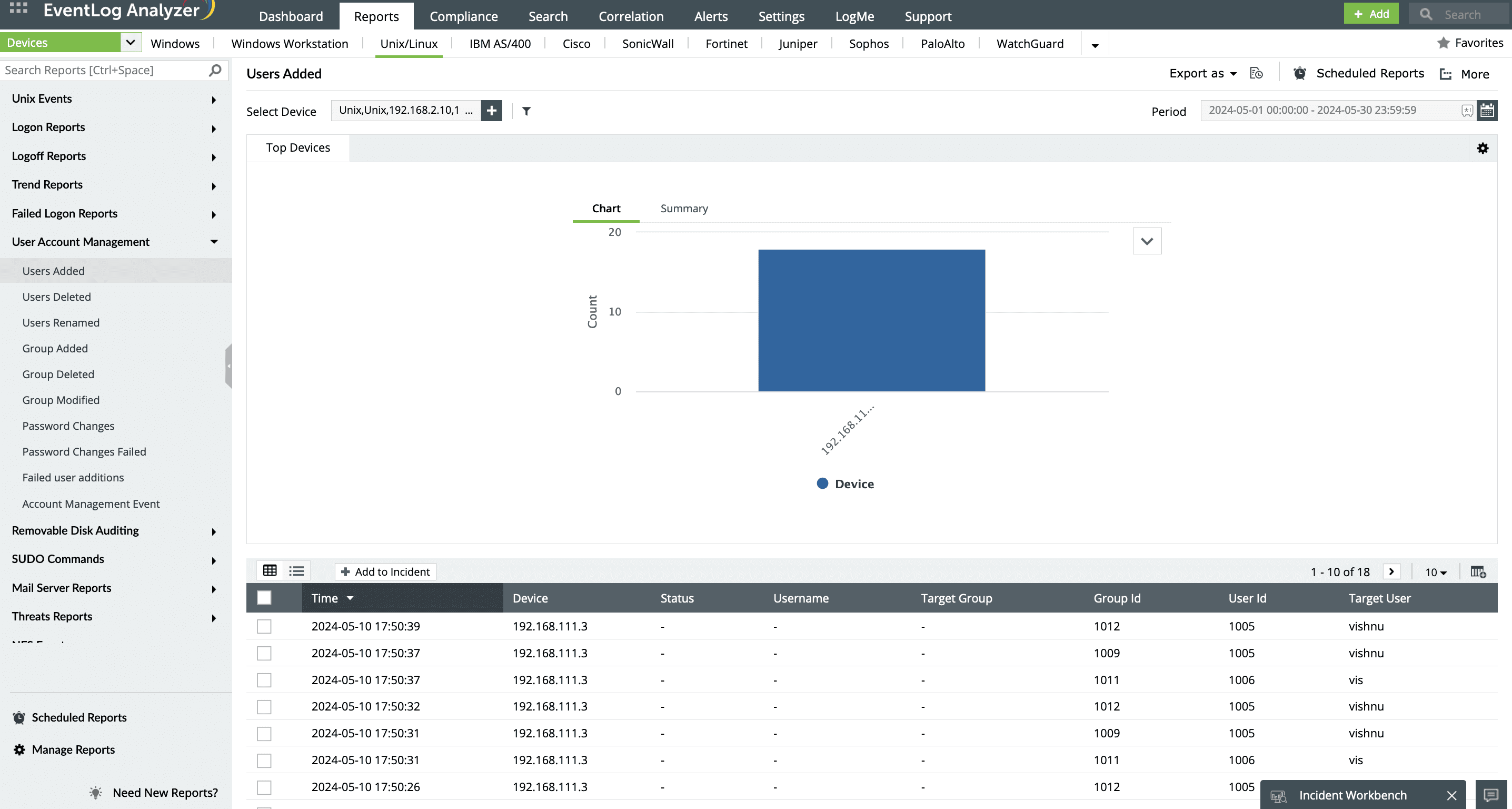
- How EventLog Analyzer streamlines Linux user account management
Creating user accounts in Linux enables you to efficiently manage access and resources, especially when overseeing a system with multiple users. Two commonly used command-line tools for adding a new user in Linux are adduser and useradd. In this article, we’ll guide you through the process of creating a user in Linux, explain the key differences between these two commands, and explore their syntax and the various options available for customizing user accounts.
1. How to create a user in Linux using adduser command
The adduser command is a user-friendly tool for creating new user accounts in Linux. It automatically configures settings like home directories and user groups during user creation. Only users with root privileges can add new users, so you’ll need to log in as the root user or use sudo to execute the adduser command.
Syntax: sudo adduser <username>
Example: sudo adduser joe
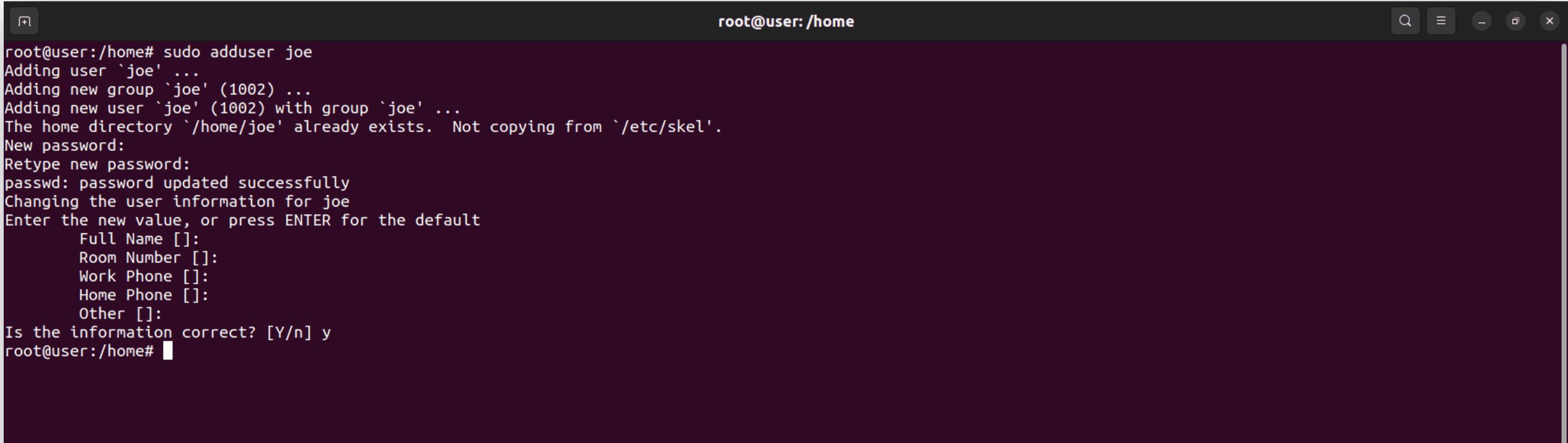
After running this command, you’ll be prompted to set a password for the user account and provide additional details like the user’s full name. This command automatically creates the user’s home directory, sets appropriate permissions, and assigns a default login shell.
The adduser command updates the following necessary system files with new user information:
- /etc/passwd: Stores user account details.
- /etc/shadow: Contains encrypted password information for users.
- /etc/group: Stores information related to user groups.
The default configuration file for the adduser command is located at /etc/adduser.conf.
2. Creating a user in Linux using the useradd command
The useradd command offers more customization for user creation than adduser, allowing you configure various user attributes, such as user ID (UID), home directory, and group memberships. This command is well-suited for managing a large user base, as it doesn’t prompt for user information interactively. Instead, you need to provide all the required details through command-line options. Unlike adduser, useradd won’t create a home directory by default unless you include the -m flag.
Syntax: sudo useradd [OPTIONS] <username>
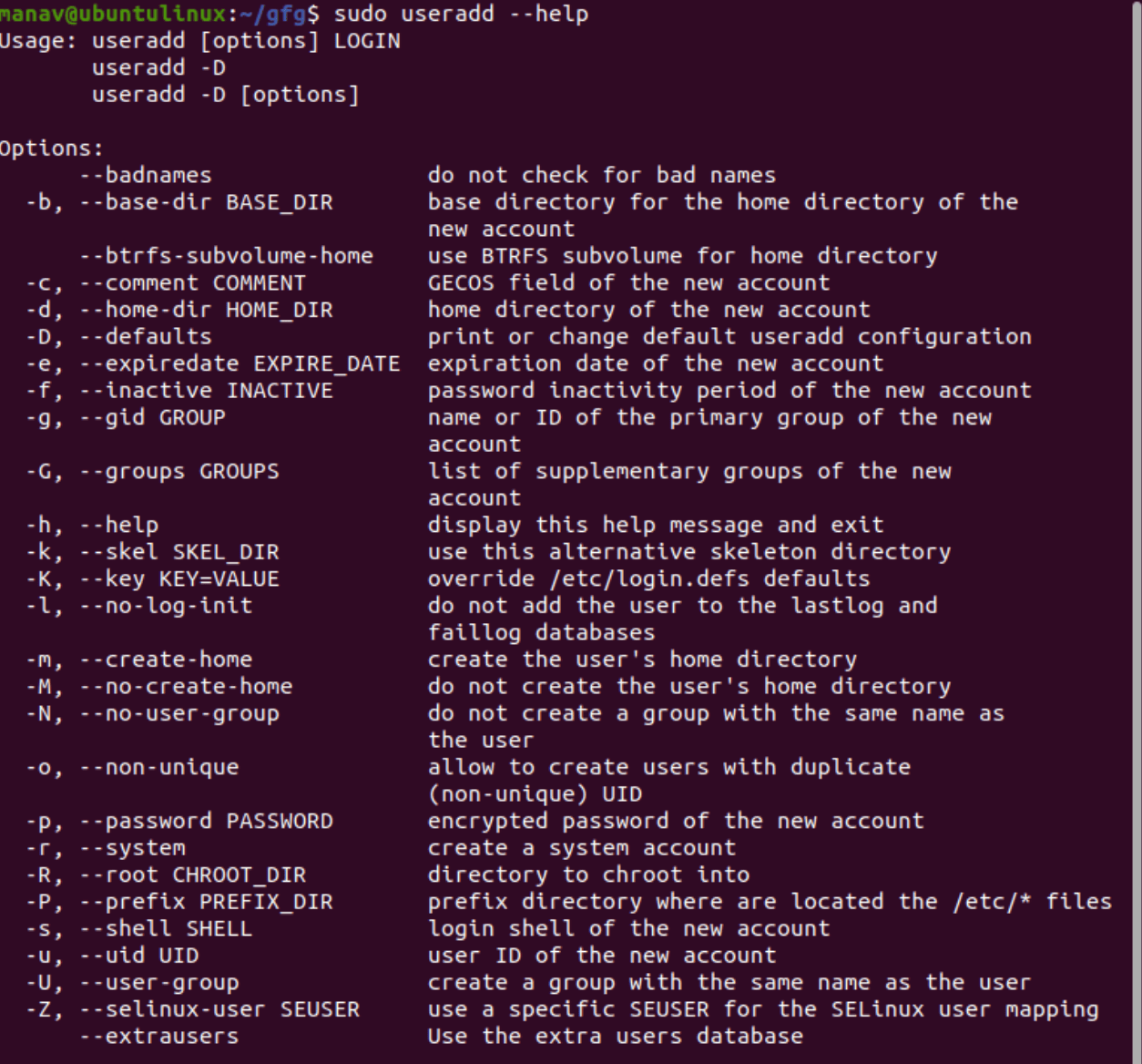
You can use several options with the useradd command to customize user accounts, as shown below:
| Option | Description | Example |
|---|---|---|
| -m | Create a home directory for the user. | sudo useradd -m joe |
| -u | Specify a unique UID. | sudo useradd -u 1005 joe |
| -g | Assign a primary group. | sudo useradd -g users riya |
| -G | Add the user to multiple secondary groups. | sudo useradd -G wheel,docker ram |
| -c | Add a comment (usually a full name or description). | sudo useradd -c "Admin User" admin |
| -d | Specify a custom home directory. | sudo useradd -d /custom/home riya |
| -s | Set the login shell for the user. | sudo useradd -s /bin/bash joe |
| -e | Set the account expiration date (YYYY-MM-DD). | sudo useradd -e 2025-12-31 tempuser |
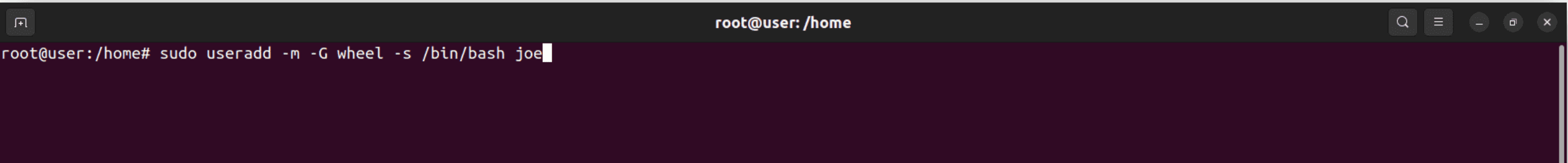
Example: sudo useradd -m -G wheel -s /bin/bash joe
In this example, you’re creating the user joe, giving the user a home directory, adding the user to the wheel group (typically for administrative privileges), and assigning /bin/bash as their default shell.
Setting a password for the new user
Regardless of whether you use adduser or useradd, you must set a password to allow the user to log in. Use the passwd command for this purpose.
Syntax: sudo passwd <username>
After running this command, you will be prompted to enter and confirm the password.
Verifying user creation
After creating a user, it’s important to verify that the user was added successfully. There are several ways to confirm user details:
- Check /etc/passwd: This command shows the details of the user in the system's user database.
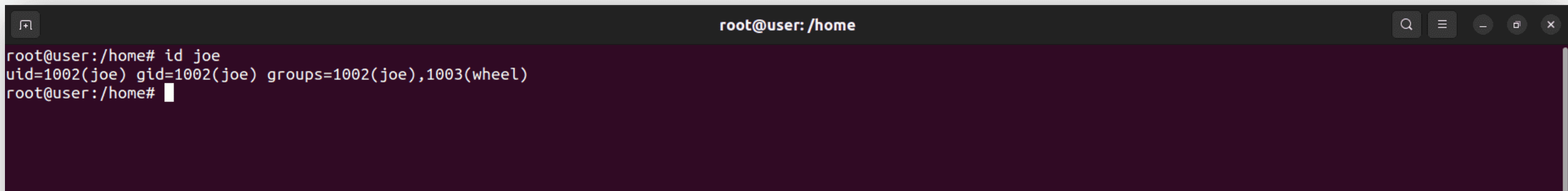
- Use the id command: This command displays the user's UID, GID, and group memberships.
Syntax: cat /etc/passwd | grep <username>
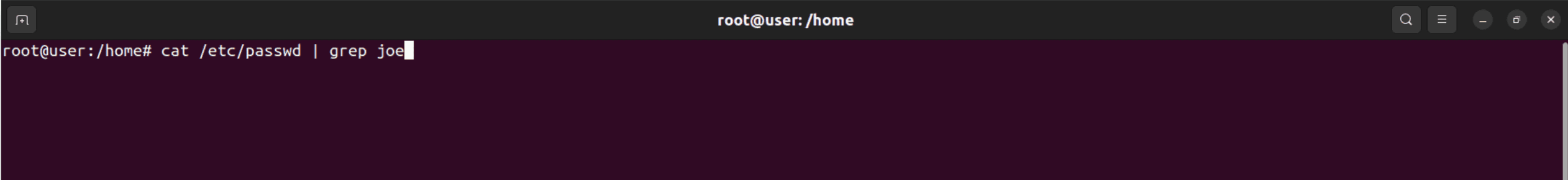
Syntax: id <username>
Customizing user settings
You can customize various aspects of a user's profile during or after creation. Some common settings include:
Add users to secondary groups: This command adds joe to the sudo and ftp groups, granting him additional permissions.
Syntax: sudo useradd -G sudo,ftp joe
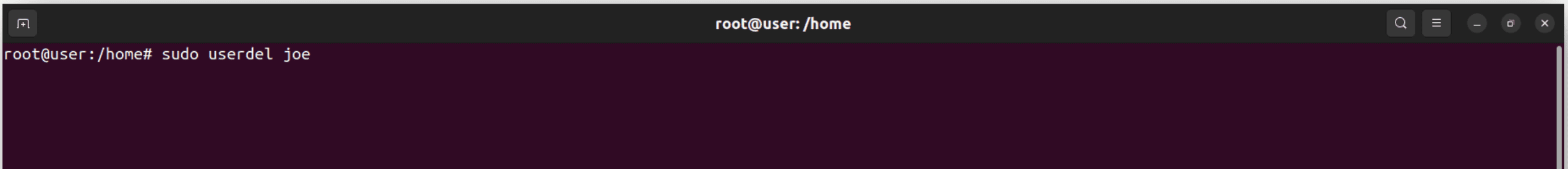
Delete users: At some point, you may need to remove users from the system. To do so, use the userdel command.
Syntax: sudo userdel <username>
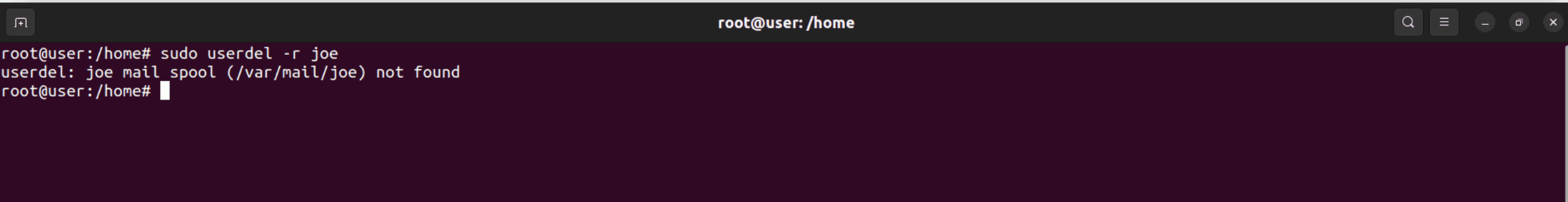
To also delete the user's home directory and mail spool:
Syntax: sudo userdel -r <username>
Best practices for Linux user management
Linux provides the necessary tools for efficient user management, allowing you to choose between the adduser command for simplicity or the useradd command for greater flexibility. Both methods integrate seamlessly with system files and permissions, helping you maintain a secure and organized environment. By following these best practices, you can streamline user management while enhancing system security:
- Always enforce strong password policies to strengthen security.
- Assign users to appropriate groups to simplify permission management.
- Implement password expiration policies to ensure regular password updates.
- Regularly audit user activity to ensure compliance with security standards.
How ManageEngine EventLog Analyzer simplifies Linux user account management
ManageEngine EventLog Analyzer, a comprehensive log management and compliance tool, helps you with effective user auditing. This log management tool acts as a centralized syslog server, capturing logs across Linux and other syslog environments. The solution offers predefined reports and alerts to monitor user account activities, including:
- User creation activity monitoring: EventLog Analyzer provides detailed reports for each instance of user creation, tracking who created the account, the time of creation, and the privileges assigned. This helps you maintain a clear audit trail of all user accounts, ensuring transparency. The solution also alerts you if there is abnormal user creation activity happening on a critical server using its real-time alerting system.
- Suspicious user creation detection: EventLog Analyzer offers real-time alerts to notify you of any unusual or unauthorized user creation attempts. This proactive detection helps prevent unauthorized access before it becomes a security threat.
- User deletion and group modification monitoring: EventLog Analyzer also monitors and audits other critical user account management activities, such as user deletion, renames, users being added to groups, and password changes to user accounts. These critical activities need continuous monitoring to detect lateral movement and privilege escalation attempts and help you respond to potential risks effectively.