- Home
- Logging Guide
- How to check ports in Linux
How to check ports in Linux
On this page
- How to check ports in Linux
- How to show ports using the ss command
- How to show ports using the lsof command
- How to show ports using the netstat command
- Securing open ports: A critical step in network security
- Best practices to secure open ports
- How ManageEngine EventLog Analyzer ensures security through port monitoring
Network ports in Linux serve as logical connection points for communication between the systems, devices, and applications. Various protocols like TCP and UDP utilize these ports for communication. Depending on the network setup, these ports can be open, closed, or listening.
- Open ports actively accept incoming connections through specific protocols. They can be in various states, including listening and established.
- Closed ports are not actively accepting incoming connections. They accept only predetermined connections from servers or applications. Other connection requests are blocked by the firewall.
- Listening ports are a specific type of open port that is actively waiting for an incoming connection. They are typically associated with services that are running in the system and are waiting for clients to connect.
Open ports are categorized into different types, each serving a different purpose, as illustrated below:

A listening port can only accommodate one service at a time. For example, if a web server is already using port 80, any additional web server will need to use a different port number.
Troubleshooting operational issues and ensuring the security of Linux systems often involve checking for open network ports. This article elaborates on the different Linux commands that can be used to check for open ports, aiding in server security and auditing.
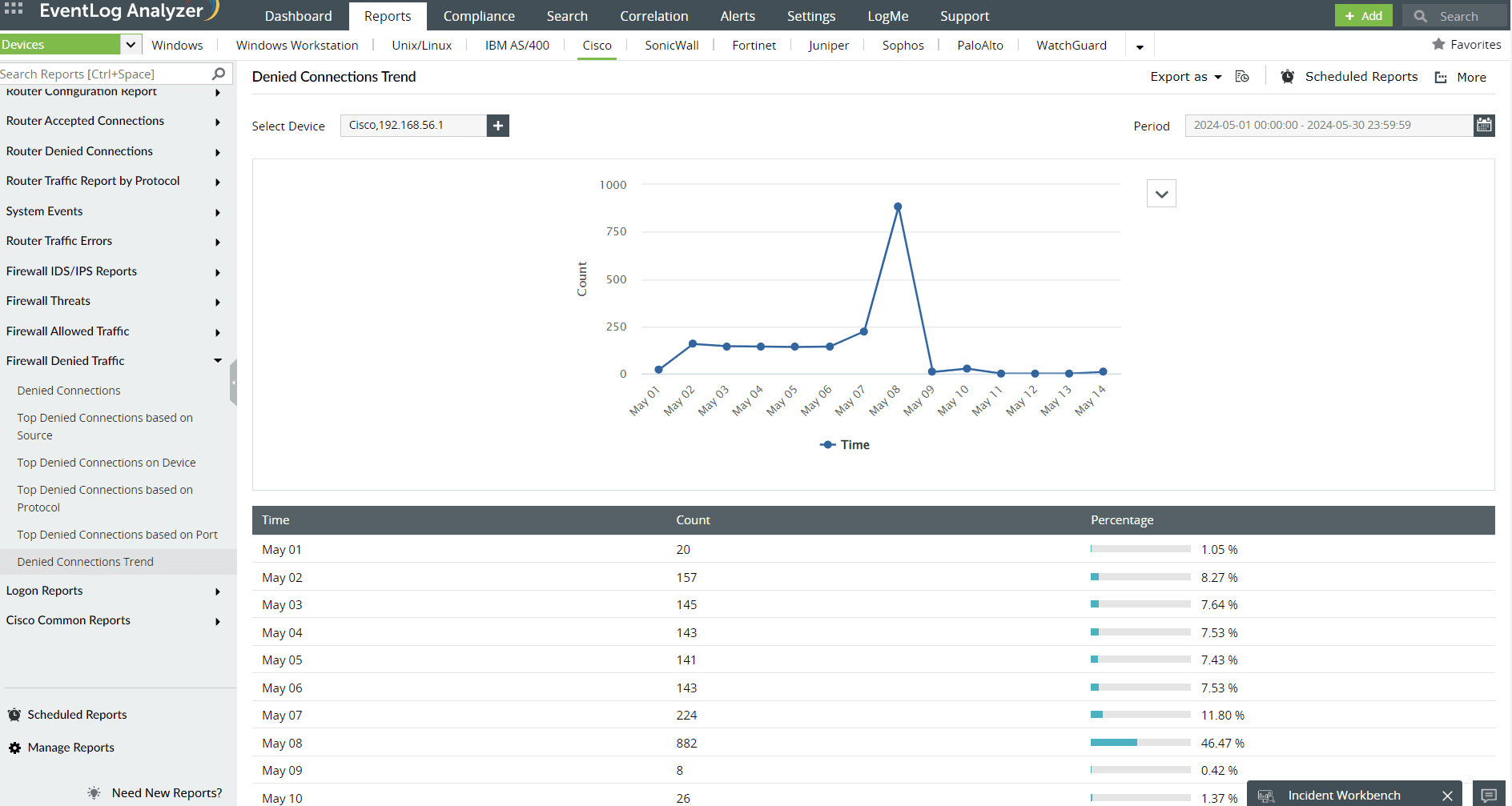
How to show ports using the ss command
The socket statistics (ss) command is a tool in Linux that provides information on sockets, connections, and network interfaces. The table below illustrates the different options this command offers to check ports in Linux:
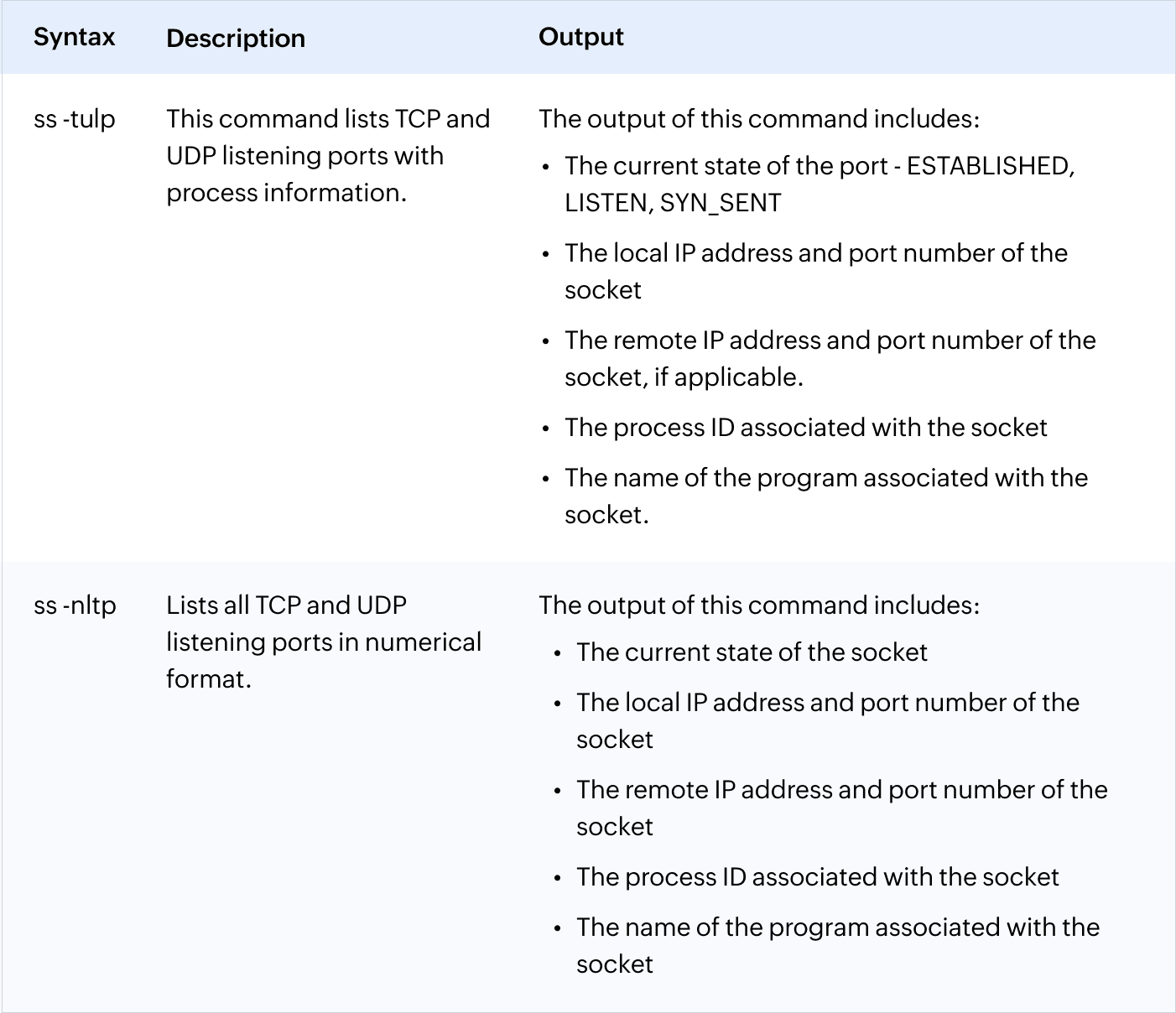
How to show ports using the lsof command
While the lsof command is primarily used to list information about open files, it can also be a valuable tool for identifying open ports. This is because network connections are often represented as files in the operating system.
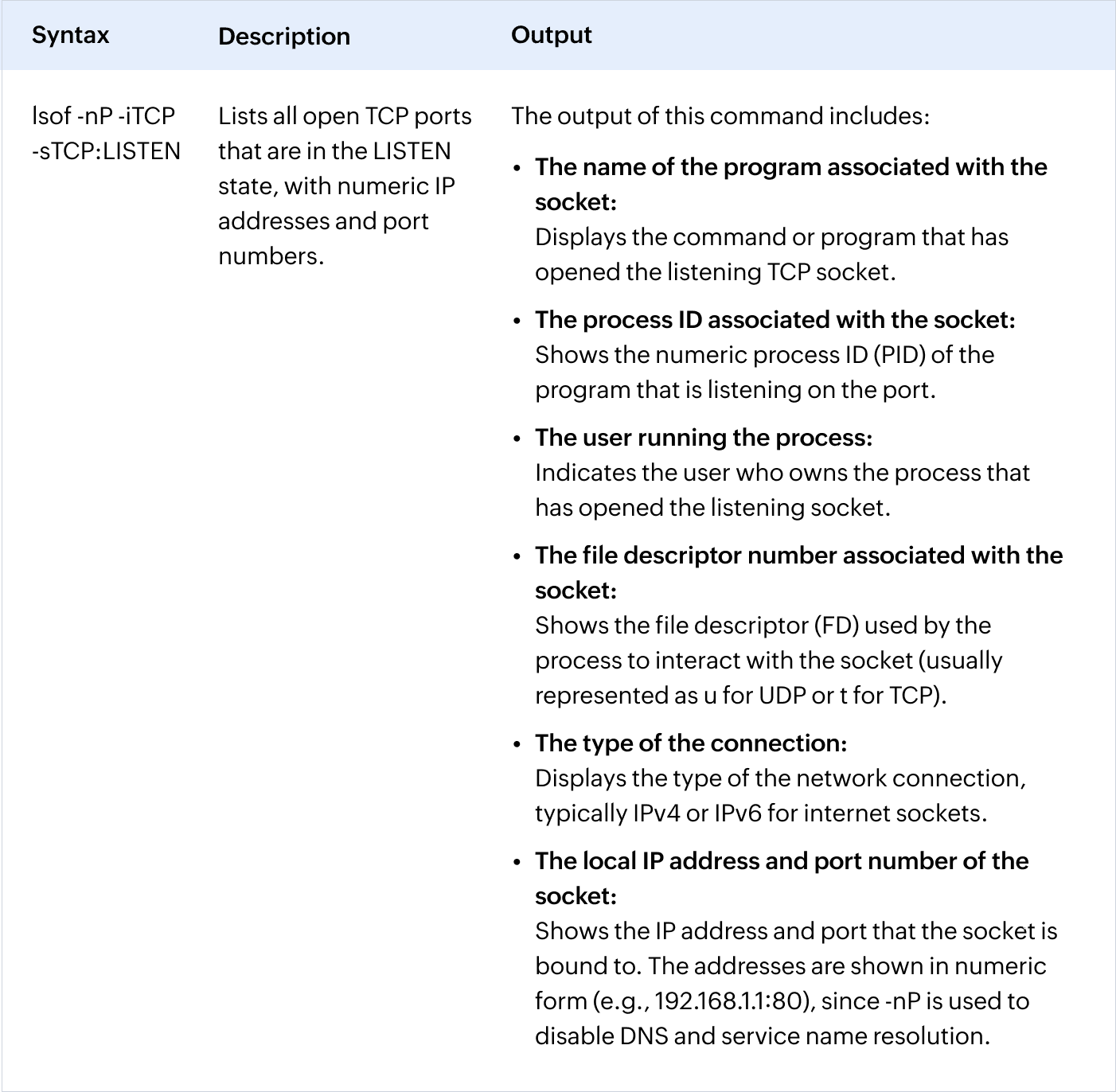
How to show ports using the netstat command
The netstat command in Linux is a powerful tool used to display network-related statistics and information about TCP/IP connections. It provides details about active connections, listening ports, routing tables, interface statistics, and more.
Securing open ports: A critical step in network security
Open ports can allow anyone from outside the organization to access your system, depending on the configuration of the service running on the port. If a service runs on an open port without security measures, it can be vulnerable to attacks. For instance, a web server running on port 80 without proper security measures is vulnerable to SQL injection or cross-site scripting.
Therefore, it is essential for you to secure the open ports with proper firewall rules and other security configurations. To reduce the risk of intrusion through open ports, you can:
- Set up firewall rules to block incoming traffic on open ports.
- Enhance the security configurations of services to prevent unauthorized access via open ports.
Best practices to secure open ports
- Close unnecessary ports: If a service is not needed, close the associated port to reduce the attack surface.
- Use strong authentication: Implement strong authentication mechanisms such as adaptive authentication and MFA for services running on open ports.
- Apply security patches: Keep services and software running on open ports up to date with the latest security patches.
- Use firewall: Configure firewall rules to block incoming traffic on unnecessary ports and restrict access to authorized users only.
How ManageEngine EventLog Analyzer ensures security through port monitoring
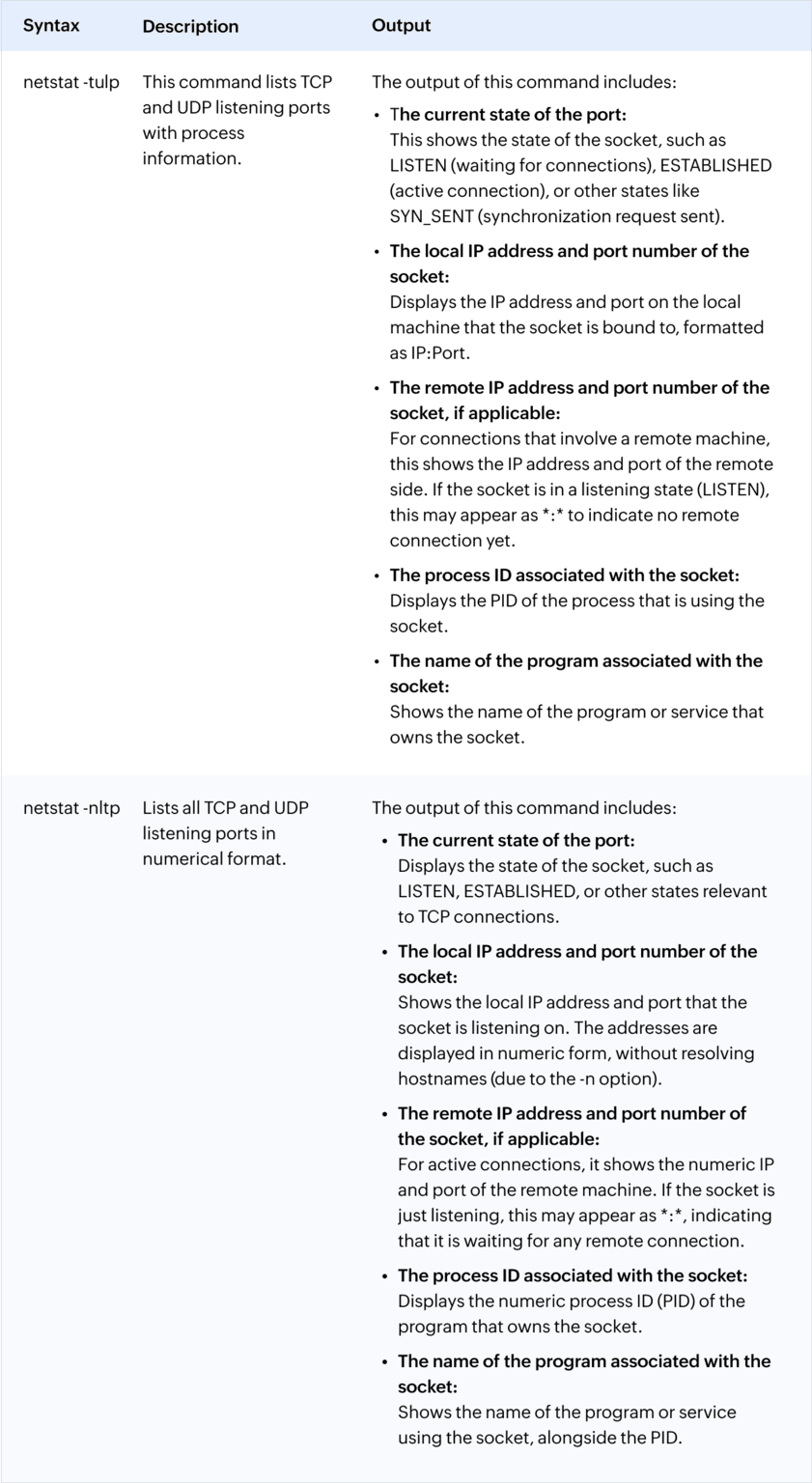
EventLog Analyzer, a comprehensive log management and IT compliance solution, can help you monitor port scans and traffic through open ports to detect suspicious and unauthorized access to your network. The solution monitors logs from firewall devices, such as Cisco, SonicWall, Fortinet, Juniper Networks, and Sophos devices, and tracks traffic trends for specific ports, denied connections on ports, and port scans happening in the network.
By analyzing traffic trend reports for the ports, you can identify suspicious inbound traffic, assess its legitimacy, and block it if you deem it unnecessary. Additionally, by reviewing denied connection attempts, you can detect patterns that may indicate unauthorized access attempts. This helps you improve security configurations for services and applications running on those ports.