Firewalls play a crucial role in network security. The complex network architecture of modern enterprises with multiple firewalls like a circuit-level firewall, an application-level firewall, and an advanced next-generation firewall (NGFW) requires an automated firewall management and centralized firewall monitoring tool to ensure security at the perimeter level. ManageEngine EventLog Analyzer is a comprehensive network firewall security and log management tool that helps you manage your firewall rules; detect malicious traffic that surpass your firewall defenses; and centrally collect, analyze, correlate, and archive your firewall logs.
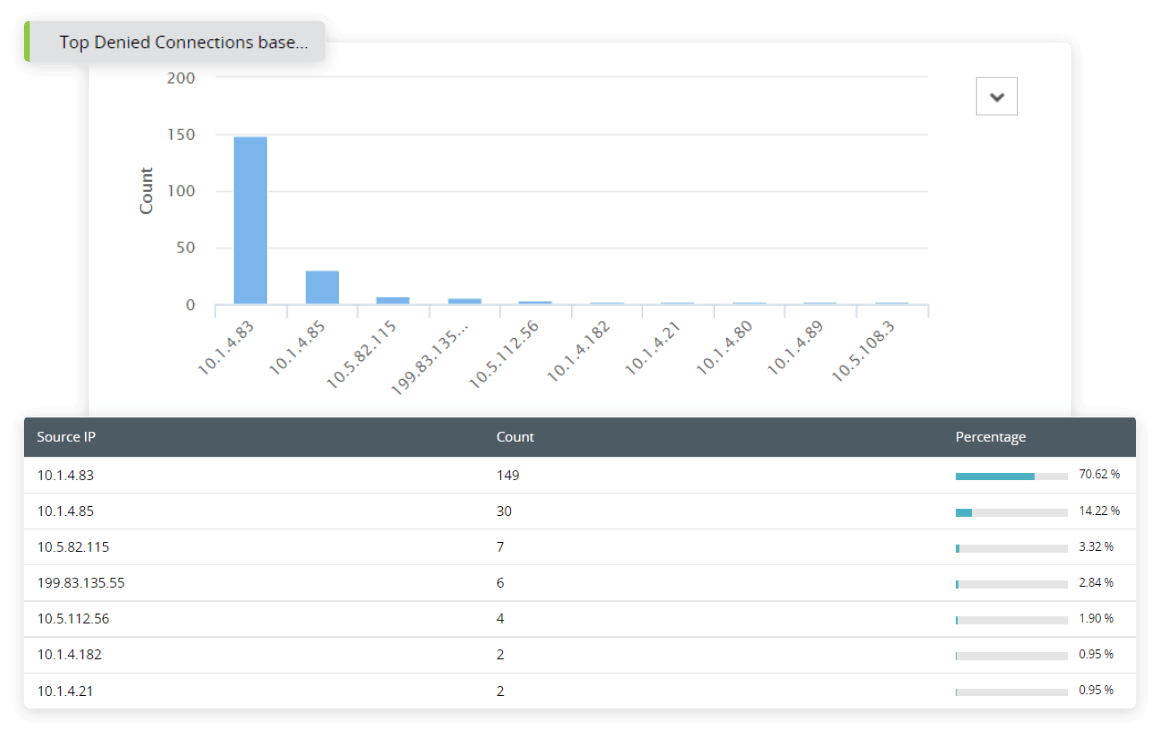
Analyze and investigate external attack attempts such as port scan attacks targeting open ports, malware trying to reconfigure firewall rules, SYN attacks, and denial-of-service attacks by correlating firewall logs with our built-in threat databases. EventLog Analyzer's firewall security analytics dashboards help you get insights into allowed and denied firewall traffic based on users, devices, IPs, ports, and protocols.
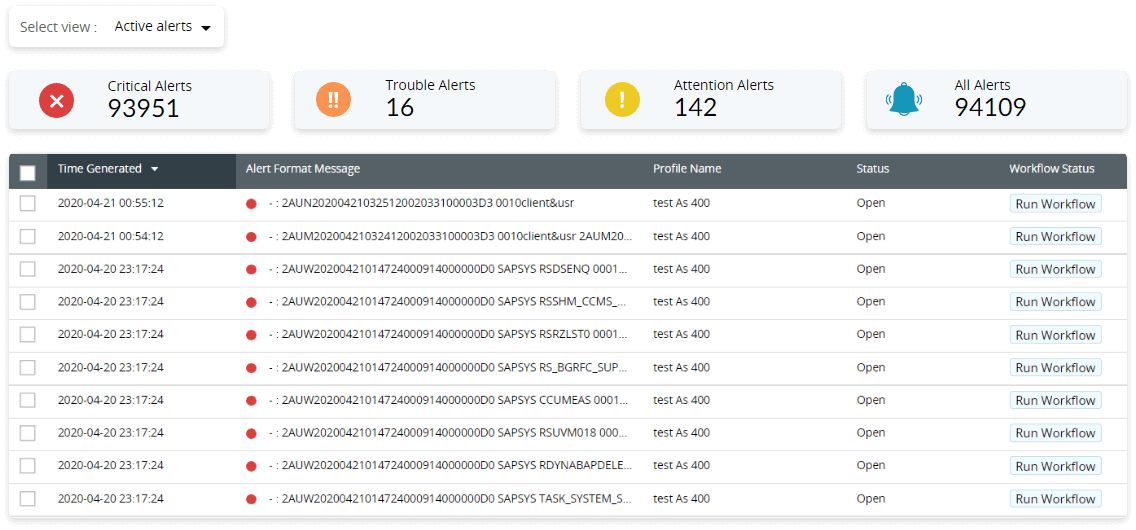
Access hundreds of pre-enabled alert profiles, add additional criteria, and categorize and set priorities based on the severity of the event. You can also respond to the detected firewall security incidents and remediate threats by automating standard response measures through workflows.
With a processing rate of 25,000 logs per second, EventLog Analyzer can efficiently spot anomalies in the huge volume of events recorded in the firewall logs. Suspicious incidents such as multiple failed connections from a single source, insecure outbound connections, and IP spoofing are precisely detected and correlated to help security admins combat ongoing attacks.
Troubleshoot and fix firewall issues with the Device Severity Reports and System Events reports that record critical information on:
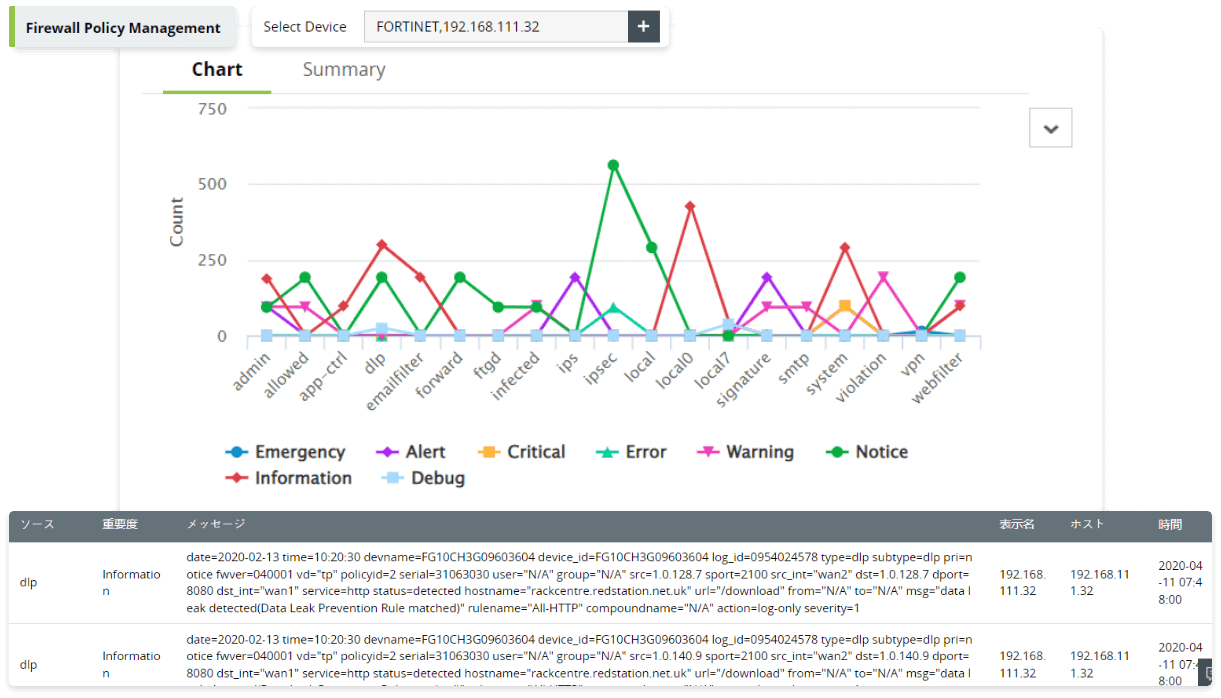
Monitor your network admin activities on firewalls to prevent privileged access abuse. Get detailed audit reports on the accounts used to access firewalls and the changes implemented. Secure your firewall from malicious insider access by tracking recently added, deleted, and modified admin accounts; newly added groups; and unauthorized escalations in user privileges.

Analyze and investigate external attack attempts such as port scan attacks targeting open ports, malware trying to reconfigure firewall rules, SYN attacks, and denial-of-service attacks by correlating firewall logs with our built-in threat databases. EventLog Analyzer's firewall security analytics dashboards help you get insights into allowed and denied firewall traffic based on users, devices, IPs, ports, and protocols.
Access hundreds of pre-enabled alert profiles, add additional criteria, and categorize and set priorities based on the severity of the event. You can also respond to the detected firewall security incidents and remediate threats by automating standard response measures through workflows.

With a processing rate of 25,000 logs per second, EventLog Analyzer can efficiently spot anomalies in the huge volume of events recorded in the firewall logs. Suspicious incidents such as multiple failed connections from a single source, insecure outbound connections, and IP spoofing are precisely detected and correlated to help security admins combat ongoing attacks.
Troubleshoot and fix firewall issues with the Device Severity Reports and System Events reports that record critical information on:
EventLog Analyzer provides out-of-the-box support for built-in firewall systems like Windows firewall and third-party security solutions from leading vendors. The tool can read and analyze logs in any human readable format, enabling it to monitor a diverse set of devices and applications.
Access the custom log parser to add additional fields for log analysis, utilize the reports exclusively created for different security solutions, and navigate through the centralized dashboard with an easy-to-use interface.
Along with firewall monitoring, EventLog Analyzer also supports auditing network devices like switches, routers, IDSs and IPSs, vulnerability scanners, and more. Use the custom reporting features to group multiple devices and generate consolidated reports on your network perimeter security.
Learn moreThe firewall analyzer and the high speed search engine with flexible querying functions support security incident mining and thorough inquiry on network intrusions. The advanced search option lets you correlate multiple query results to investigate firewall attack attempts and get a detailed time line of related events.
Learn moreEventLog Analyzer's centralized log collection, analysis, correlation, and reporting features solve the complexity of monitoring layered firewall architectures in modern enterprises and ensures comprehensive firewall management.
EventLog Analyzer's exhaustive audit reports help you examine the effectiveness of your firewall security rules, any existing loopholes, and your network traffic trends.
Correlate firewall traffic logs with suspicious events detected across your network using EventLog Analyzer's predefined correlation rules and filters. Define new attack patterns with the custom rule builder and set parameters to raise alerts.
Standardized information exchange with international threat databases enable EventLog Analyzer to immediately identify millions of globally blocklisted IPs and malicious sources. Access the insights from the threat analytics reports to reconfigure your firewall rules and strengthen the perimeter security.
Automate your security incident response with emergency measures like isolating affected systems and adding new inbound and outbound rules to firewall devices. You can use the workflow management page with an easy drag-and-drop UI to configure the flow of steps to be implemented.
Firewall logs record details of the traffic interacting with your network and the actions implemented by the firewalls.
They mainly include the:
Here's a list of commonly used firewall systems and the default firewall log storage paths:
After Step 4, uncheck the box next to Not configured. Find the Size limit field and enter the custom file size in KB.
Enterprises use a combination of hardware-, software-, and even cloud-based firewalls (Firewall as a Service). This creates an environment with a heterogeneous set of network entities. To monitor them manually, security admins need to enable logging, manage log storage, and study and analyze the logs in different formats.
Considering the massive amount of logs generated by firewalls, these laborious tasks need to be automated with a firewall security log management tool like EventLog Analyzer, which offers a wide range of useful features to secure networks, like dynamic threat handling, real-time alerting, log storage management, firewall-specific reports, and analytical dashboards.