Firewall rules allow business-essential traffic to move through the network and block unsafe traffic from entering. This control over the internet traffic going to and from the company's network ensures network security. The rule set should be strong and shouldn't contain any loopholes.
Unused rules form a major loophole and are easy for attackers to exploit. An unused rule is as bad as a weak rule. Unused rules are anomalous by nature. Any anomaly in the rule set can make the entire network vulnerable.
The firewall cleanup process involves two steps. The first step is to identify the unused rules, and the next step is to remove unused firewall rules. To do this you need an efficient firewall policy cleanup tool. Clean up firewall rules to make your rule set stronger by simply removing any unused rules.
Firewall Analyzer is an efficient firewall rule cleanup tool that enables network security administrators to simplify firewall rule cleanup. It fetches firewall rules from the device and correlates the log data fetched from the firewall to discover which rules are being used and which are unused. Administrators can use the rule cleanup report generated by this tool to prune unused rules from the rule set.
Firewall Analyzer is firewall rule cleanup software that helps identify unused firewall rules. Deleting unused rules will improve firewall performance.
This firewall rule cleanup reporting tool provides the following reports:
The Unused Rules report enumerates the rules that are not being used by the firewall to control traffic. These unused rules make the network vulnerable to attacks. You can analyze these rules for anomalies, learn of the impact they may have on existing rules, and clean the firewall rule base by modifying or deleting the rules. This will weed out unwanted rules in the firewall, resulting in a sleek and efficient rule set.
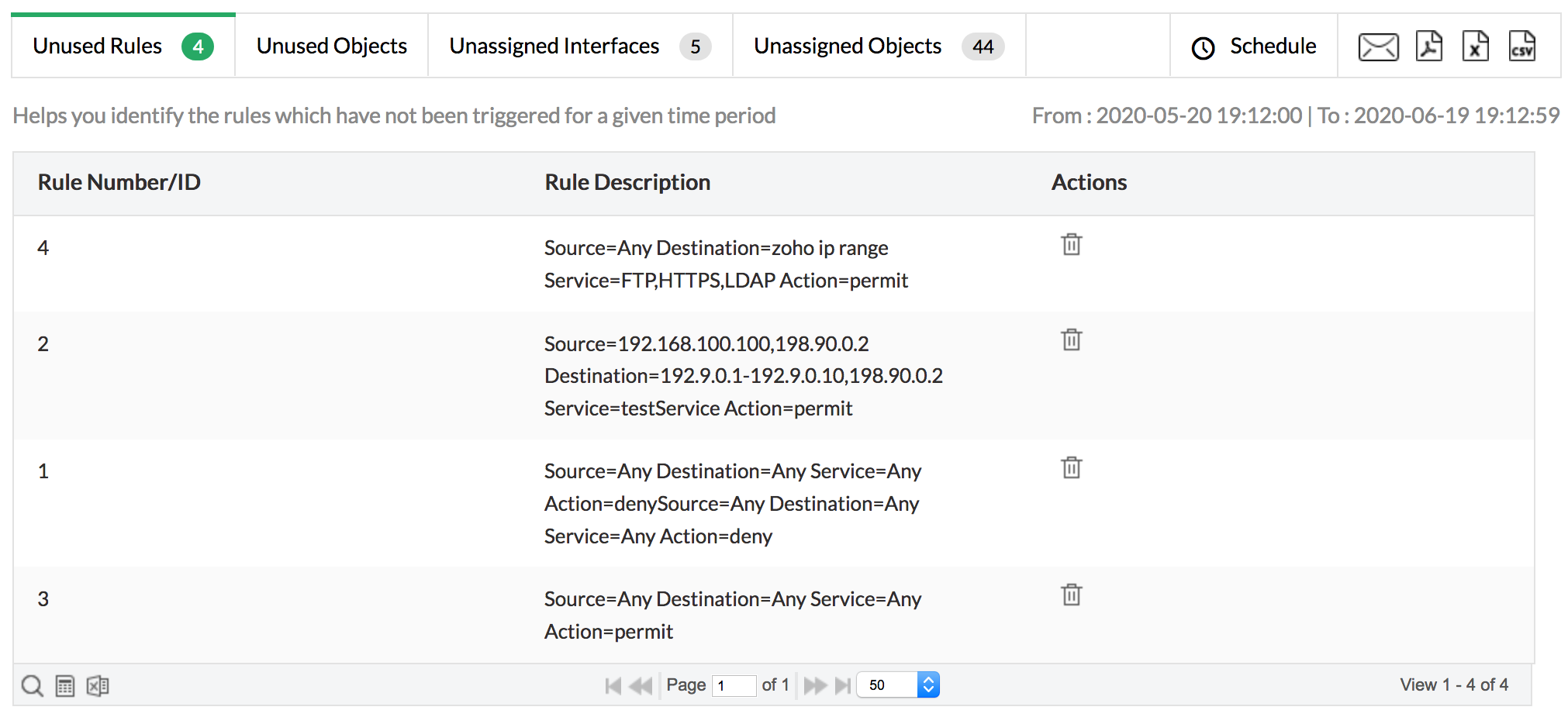
Firewall Analyzer fetches all the objects from the firewall, correlated with firewall log data, and generates the unused objects report. Unused objects also pose a risk for network security. If an attacker discovers an unused object, they may attempt to exploit the objects for an attack. Objects need to be pruned to fill all the security gaps in your firewall.
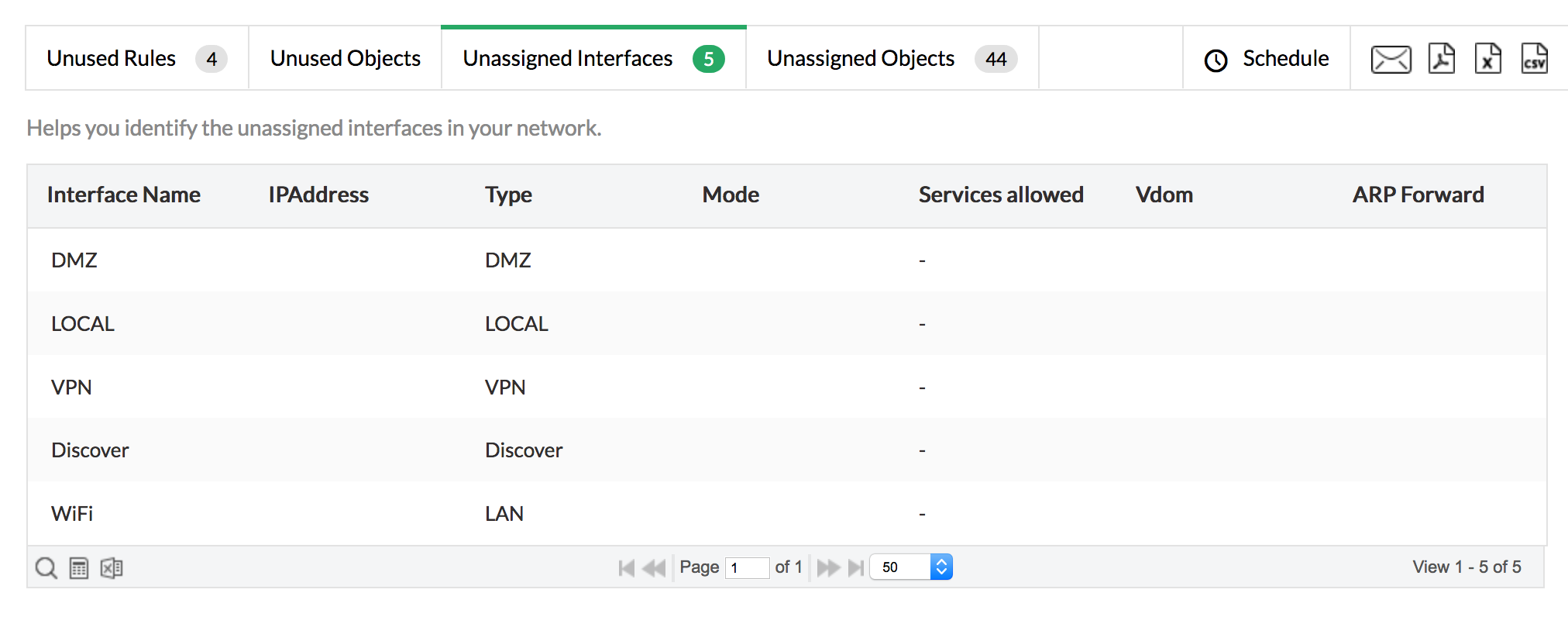
These dangling interfaces, which are not assigned in the network, leave room for manipulation by attackers, so these also need to be addressed. From the report, you can find the unassigned interfaces, and remove or modify them.
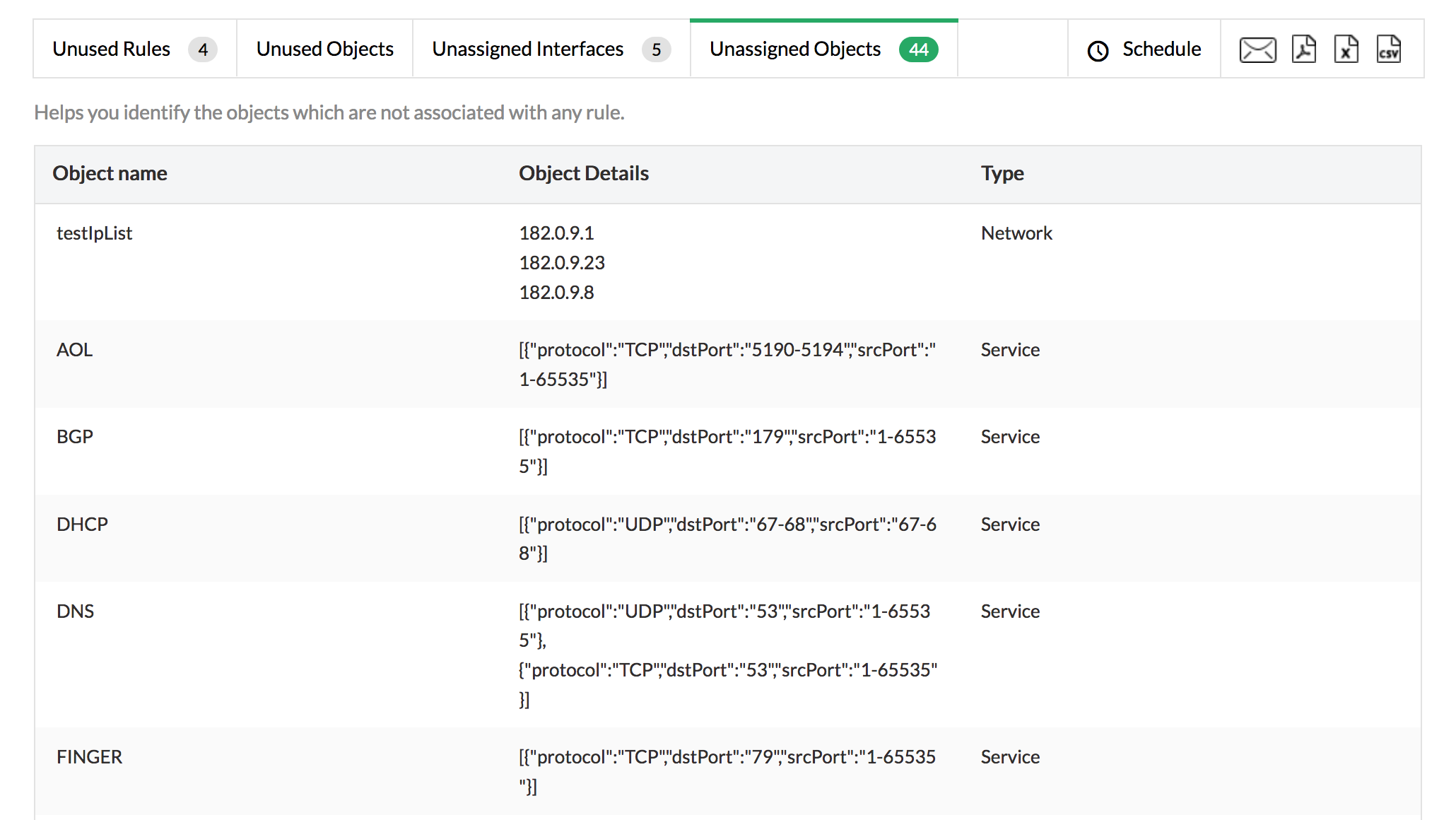
Unassigned objects are not tied to any of the firewall rules. These objects make object sets superfluous and inefficient. You can use the Unassigned Objects report to analyze the objects and assign rules to them, or remove them accordingly.
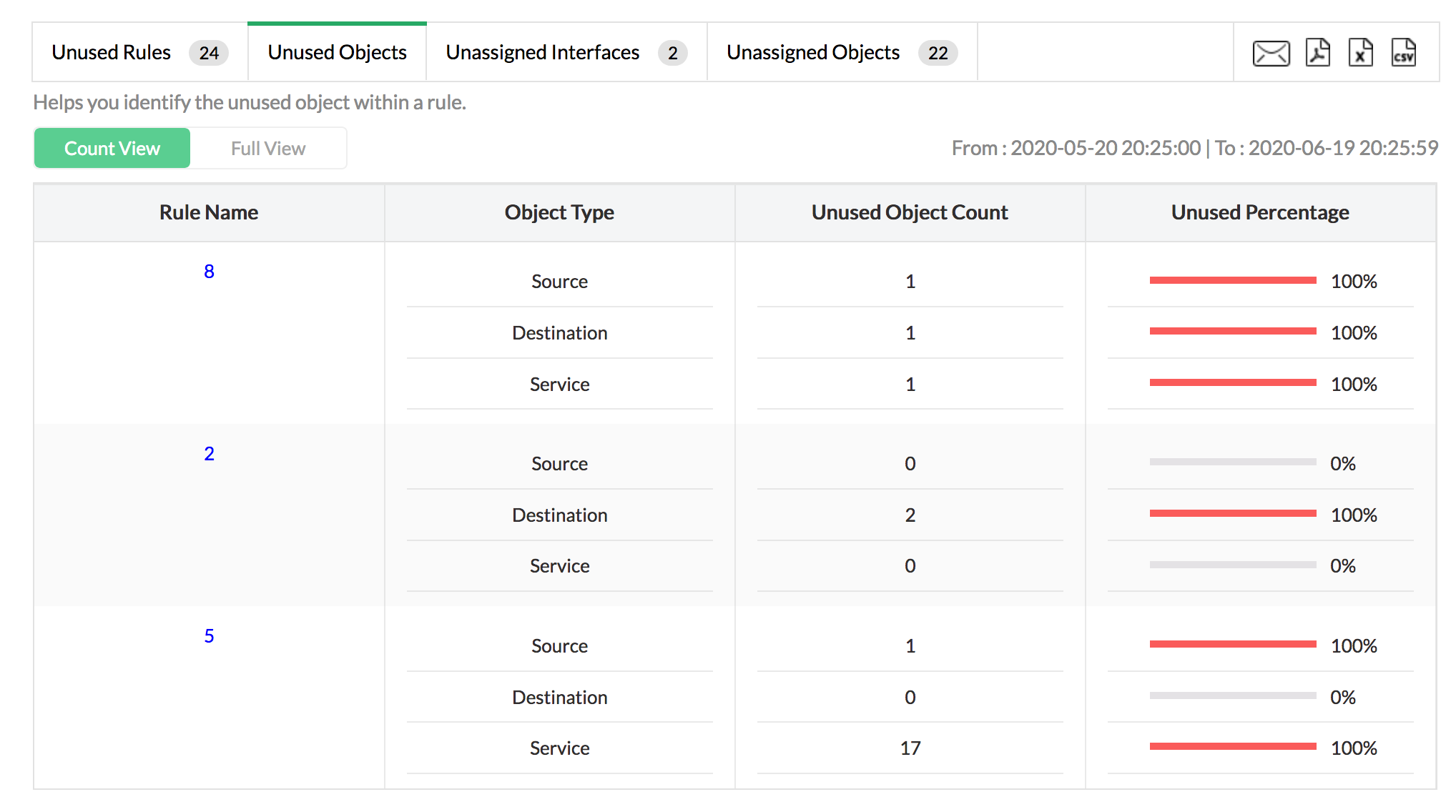
Rule cleanup reports simplify unused firewall rule and object management to help automate the process of cleaning up the firewall rules and enable security administrators to stick to firewall rule best practices. Download a free trial of Firewall Analyzer today, and get the most out of your firewall.
Refer Configure Firewall Rules page to know how to configure firewall rules.
Refer the following help documents:
Featured links
Get a slew of security and traffic reports to asses the network security posture. Analyze the reports and take measures to prevent future security incidents. Monitor the Internet usage of enterprise users.
Integrated compliance management system automates your firewall compliance audits. Ready made reports available for the major regulatory mandates such as PCI-DSS, ISO 27001, NIST, NERC-CIP, and SANS.
Unlock the wealth of network security information hidden in the firewall logs. Analyze the logs to find the security threats faced by the network. Also, get the Internet traffic pattern for capacity planning.
With live bandwidth monitoring, you can identify the abnormal sudden shhot up of bandwidth use. Take remedial measures to contain the sudden surge in bandwidth consumption.
Take instant remedial actions, when you get notified in real-time for network security incidents. Check and restrict Internet usage if banwidth exceeds specified threshold.
MSSPs can host multiple tenants, with exclusive segmented and secured access to their respective data. Scalable to address their needs. Manages firewalls deployed around the globe.