A passkey is a digital credential for identity verification that uses public-key cryptography. It comprises a cryptographic key-pair that is stored in the user's device and the application or online service they are accessing. During authentication, the user's device and the online service use these keys to communicate behind the scenes as the user authenticates themselves with their device's biometrics or a PIN.
Unlike passwords, passkeys do not require users to memorize them, since they are digitally tied to the device they possess. This makes passkeys a convenient, quick, and attack-resistant authentication method compared to traditional passwords.
Passkeys were developed by the Fast Identity Online (FIDO) Alliance, a group of companies focused on enhancing authentication standards. The FIDO Alliance includes several major companies such as Apple, Google, Microsoft, Amazon, 1Password, Dashlane, American Express, Intel, Mastercard, Meta, PayPal, Samsung, and Visa. The collaboration among these companies led to the creation and implementation of passkeys as a more secure and user-friendly alternative to passwords.
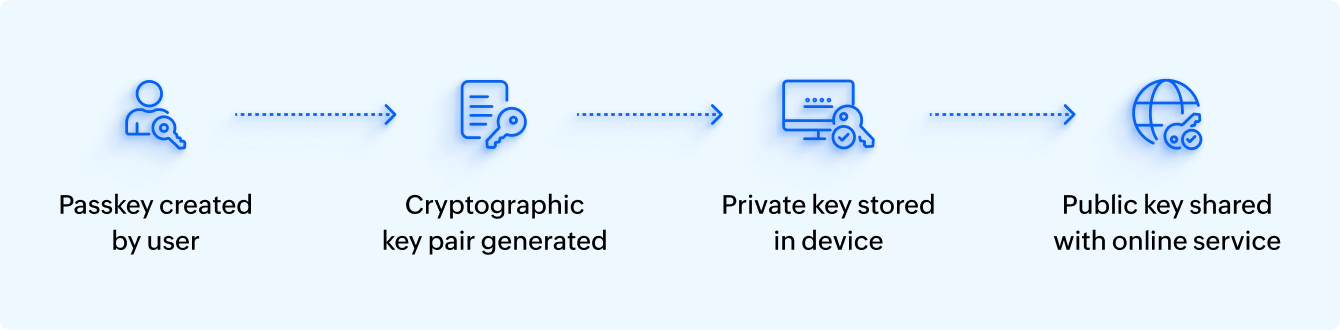
Passkeys leverage public-key cryptography to verify a user's identity. When a user creates a passkey, their device generates a pair of cryptographic keys—a public key and a private key. The public key is shared with the online service and the private key remains securely stored on the user's device.
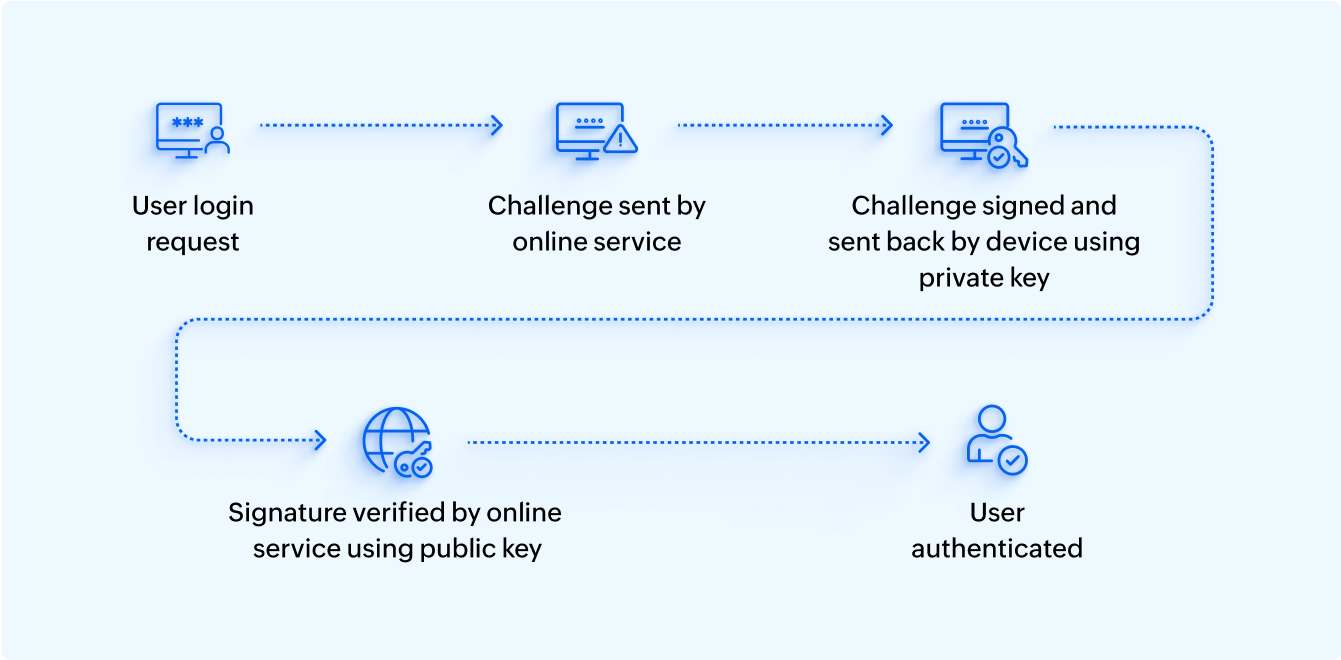
When the user wants to log in, the online service sends a random challenge to the user's device. The device uses its stored private key to sign this challenge and sends the signed challenge back to the service. The service then verifies the signature using the stored public key. If the signature is valid, it confirms the user’s authenticity, as only the holder of the private key could have generated the valid signature. Once authenticated, the user is logged in and can access the online service.
To use a passkey, users typically authenticate themselves on their device through a biometric method, such as fingerprint, face recognition, or a PIN. This is the key benefit of passkeys since it is a combination of something the user has (their device)and something the user is (biometric data) or knows (PIN). This makes it a highly secure and convenient method of authentication.
The specific passkey authentication process, however, may vary depending on the type of passkey used. The following are the most commonly used passkey types with examples:
Passkeys eliminate the need for users to create and remember tough passwords, which are susceptible to theft, phishing, and compromise. Since passkeys use public-key cryptography with securely encrypted private and public keys, they are impossible to be deciphered by attackers.Since they are also unique to a specific service, passkeys eliminate the risks of re-using passwords across multiple services. Moreover, passkeys remove the need for strict password policies, which can be inconvenient and often lead to poor password practices.
All these make passkeys more secure than passwords in resisting attacks, making them a preferred option for authentication. So, will passkeys replace passwords? Looking at FIDO Alliance's study on the adoption rate of passkeys, there wereseven billion passkey accounts equipped for passwordless logins in the past year. Therefore, it is safe to say that passkeys have already overtaken passwords in the race for MFA.
To learn more about the difference between passkeys and passwords, check out our blog on passkeys vs. passwords.
Passkeys and security keys, though quite similar, have distinct characteristics. Both are secure authentication mechanisms that eliminate passwords. Passkeys use public-key cryptography and are typically stored on a user’s device, verifying them with the device's biometric data collection mechanism or a PIN. Security keys also utilize public-key cryptography but are physical hardware devices that resemble a USB device and store the cryptographic keys used for authentication. When plugged in, they communicate encrypted authentication information with the online service, confirming that the user who is in possession of this security key is legitimate.
To learn more about security keys, check out our blog on what is a security key.
ADSelfService Plus, an identity security solution with MFA, SSO, and password management capabilities, provides adaptive MFA with 20 different authentication methods to secure endpoints such as servers, workstations, applications, VPNs, OWA, and RDPs. It provides passwordless login using the phishing-resistant FIDO passkey authenticator to secure your business endpoints. ADSelfService Plus' FIDO passkey authenticator is secure and customizable, supporting both platform and roaming FIDO2 authenticators.
No, it is not easy to steal or hack passkeys since they are represented using unique cryptographic keys that are stored securely between the services. During authentication, the keys themselves are not transmitted over the network, eliminating potential interception of the same.
The following are some disadvantages of using passkeys:
A passkey can be generated with the click of a button. However, users must register with the particular website or application for which they want to create a passkey. The FIDO passkey authenticator in ADSelfService Plus allows you to enroll up to three FIDO2 credentials corresponding to different devices and platforms. To learn more about how you can generate a passkey using ADSelfService Plus' FIDO passkey authenticator, click here.
Yes, a passkey is safer than a password because it does not need to be memorized, uses secure cryptographic keys, and cannot be stolen or intercepted.
A passkey comprises a cryptographic key-pair that your device and the online service store and communicate behind the scenes as you verify your identity using biometrics or a PIN. So, you don't have to enter your passkey anywhere during login.
A passcode is an authentication method similar to a password but is less secure because it is shorter and has only numeric characters. Passcodes must be remembered by users, and so, like passwords, they are unsecure and susceptible to attacks. But passkeys are digital credentials that are stored as cryptographic key-pairs and communicated between your device and the online service as you verify your identity using your device's biometrics or a PIN.