- Free Edition
- Quick Links
- MFA
- Self-Service Password Management
- Single Sign-On
- Password Synchronizer
- Password Policy Enforcer
- Employee Self-Service
- Reporting and auditing
- Integrations
- Related Products
- ADManager Plus Active Directory Management & Reporting
- ADAudit Plus Real-time Active Directory Auditing and UBA
- Exchange Reporter Plus Exchange Server Auditing & Reporting
- EventLog Analyzer Real-time Log Analysis & Reporting
- M365 Manager Plus Microsoft 365 Management & Reporting Tool
- DataSecurity Plus File server auditing & data discovery
- RecoveryManager Plus Enterprise backup and recovery tool
- SharePoint Manager Plus SharePoint Reporting and Auditing
- AD360 Integrated Identity & Access Management
- Log360 (On-Premise | Cloud) Comprehensive SIEM and UEBA
- AD Free Tools Active Directory FREE Tools
What is the CJIS?
The Criminal Justice Information Services Division (CJIS) is a division of the Federal Bureau of Investigation (FBI) that sets standards and appropriate controls to protect, transmit, store, and access criminal justice information (CJI). The CJIS enables law enforcement professionals to access and share critical CJI, including biometrics, identity history information, and case history. Any organization with access to CJI in any of its forms must ensure that it complies with mandated CJIS regulations.
What are the CJIS password requirements
The following table explains the password policy requirements found in CJIS Security Policy v6.0 and how ADSelfService Plus helps your organization comply with them.
| CJIS requirement | Requirement description | How ADSelfService Plus helps satisfy the requirement |
| Section 5.5.2.2 | System access control Prevent multiple concurrent active sessions for one user identification, unless the agency grants authority based upon operational business needs. |
ADSelfService Plus prevents a single user from having multiple concurrent active sessions. |
| Section 5.5.3 | System access control Ensure that only authorized personnel can add, change, or remove component devices, dial-up connections, and remove or alter programs. |
ADSelfService Plus performs identity verification using strong authentication factors before allowing authorized users to modify necessary settings in the system. |
| Section 5.5.3 | Unsuccessful login attempts Where technically feasible, the system shall enforce a limit of no more than five consecutive invalid access attempts by a user (attempting to access CJI or systems with access to CJI). The system shall automatically lock the account for a ten-minute period unless released by an administrator. |
ADSelfService Plus allows you to configure the number of failed logon attempts that are allowed for users within a specified time. You can also configure the lockout duration and whether admin intervention is required to unlock users. |
| Section 5.5.6 | Remote access The agency shall authorize, monitor, and control all methods of remote access to the information system. |
ADSelfService Plus provides MFA for remote access sessions, which can be applied either at the client or target machine level. It employs strong authenticators such as biometrics, YubiKey, and TOTPs. |
| Section 5.6.1 | Identification policy and procedures Each person who is authorized to store, process, and/or transmit CJI shall be uniquely identified. A unique identification shall also be required for all persons who administer and maintain the system(s) that access CJI or networks leveraged for CJI transit. |
ADSelfService Plus uniquely stores and identifies each user, assigning authenticators individually for each user. It prohibits the sharing of authentication factors among multiple users. |
|
Basic password standards |
||
| Section 5.6.2.1.1.1 | Minimum password length Passwords shall be a minimum length of eight characters (for standard passwords) on all systems. |
With ADSelfService Plus' Password Policy Enforcer, you can customize the minimum password length to be eight characters or more, depending on your requirement. You can also customize the maximum password length as needed. |
| Section 5.6.2.1.1.1 | Password complexity Passwords shall not be a dictionary word or proper name. |
ADSelfService Plus allows you to restrict users from utilizing dictionary words, palindromes, and predictable patterns while setting new passwords. By integrating with Have I Been Pwned?, a breached password database, it ensures that your users do not set weak or compromised passwords during password resets and changes. |
| Section 5.6.2.1.1.1 | Password uniqueness Passwords shall not be the same as the user ID. |
ADSelfService Plus allows you to restrict users from utilizing repeated characters as well as consecutive characters from usernames and old passwords while setting new passwords. |
| Section 5.6.2.1.1.1 | Password expiration Passwords must expire within a maximum of 90 calendar days for standard passwords, or up to one year for long-form passwords. |
ADSelfService Plus offers customizable password expiration notifications, letting admins adjust the content and frequency to match organizational needs. Multiple reminders can be scheduled before password expiry and delivered via email, SMS, or push notification, ensuring timely alerts through users’ preferred channels, whether passwords expire every 90 days or annually. |
| Section 5.6.2.1.1.1 | Password history Passwords shall not be identical to the previous ten passwords. |
ADSelfService Plus allows you to specify the number of previous passwords that a user cannot repeat while choosing a new password. |
| Section 5.6.2.1.1.1 | Password entry Passwords shall not be displayed when entered. |
ADSelfService Plus does not display passwords by default when entered but gives users the option to view them, if required. |
|
Advanced password standards |
||
| Section 5.6.2.1.1.2 | Minimum password length and complexity Passwords shall be a minimum of twenty characters in length (for long-form passwords) with no additional complexity requirements imposed. For example, ASCII characters, emojis, all keyboard characters, and spaces will be acceptable. |
ADSelfService Plus allows you to enforce password policies based on password length. For long-form passwords (20 characters or more), you can waive complexity requirements, while shorter passwords (fewer than 20 characters) can be made to follow stricter rules, such as requiring special characters. |
| Section 5.6.2.1.1.2 | No password hints Password Verifiers shall not permit the use of a stored “hint” for forgotten passwords and/or prompt subscribers to use specific types of information when choosing a password. |
ADSelfService Plus can be configured to not provide password hints for users during identity verification. |
| Section 5.6.2.1.1.2 |
Banned passwords
During user password creation, change, or reset requests, verifiers shall compare prospective passwords against the "banned passwords" list and advise that users choose a different password if a match is identified. |
ADSelfService Plus allows you to restrict users from utilizing dictionary words, palindromes, predictable patterns, repeated characters, and consecutive characters from usernames and old passwords while setting new passwords. By integrating with Have I Been Pwned?, a breached password database, it ensures that your users do not set weak or compromised passwords during password resets and changes. |
| Section 5.6.2.1.1.2 | Annual password changeVerifiers shall force a password change annually or if there is evidence of an authenticator compromise. | ADSelfService Plus does not encourage frequent or periodic end-user password changes but allows admins to trigger an automatic password reset action for users with potentially compromised passwords. |
| Section 5.6.2.1.1.2 | Unique authentication factors When user-based certificates, such as smart cards, software tokens, hardware tokens, biometric systems, and public key infrastructure (PKI) certificates, are used for authentication, they must be specific to an individual user and not be shared between multiple users. |
ADSelfService Plus assigns authentication factors, like security tokens, smart cards, and PKI certificates, uniquely to individual users and prohibits their sharing among multiple users. |
| Section 5.6.2.2 | Multifactor authentication (MFA) MFA is required for all personnel accessing criminal justice data via cloud services, regardless of location (including headquarters, patrol cars, and remote sites). |
ADSelfService Plus provides strong, adaptive MFA with 20 different authentication factors, including FIDO passkeys and biometrics, to safeguard access to criminal justice data. It allows you to configure two or more MFA factors, and the success of all factors is mandatory before access is granted. |
Simplify CJIS compliance using ADselfService Plus
ADSelfService Plus' Password Policy Enforcer satisfies CJIS requirements and can be enforced for all or specific AD users based on their domain, OU, or group membership. With its adaptive MFA techniques, ADSelfService Plus ensures your organizational identities are effectively secured for a comprehensive Zero Trust environment.
- Ban dictionary words and patterns: Block leaked or weak AD passwords as well as patterns, dictionary words, and palindromes.
- Restrict characters from usernames: Restrict specific or repeated characters from a username.
- Enforce password history: Ensure password strength by enforcing password history during native password resets in the Windows Active Directory Users and Computers (ADUC) console.
- Set a custom password length: Enforce longer passwords for Windows domain users by specifying the minimum password length.
- Increase password strength: Restrict users from using copy and paste in the password field. Help users pick strong passwords using the Password Strength Analyzer, which indicates password strength.
- Ensure password complexity: Ensure user passwords contain uppercase, lowercase, special, and numeric characters.
- Mandate MFA for users: Secure user access to sensitive defense-related data by enabling adaptive MFA for endpoints, such as for machine logons, application logons, VPN logons, RDP logons, and OWA logons. Choose from a range of 20 different MFA authenticators, including FIDO passkeys and biometrics, to verify users' identities.
- Password Policy Enforcer
- MFA
Restrict users from reusing any of their previously used passwords during password creation.
Configure the minimum password length and the inclusion of alpha-numeric characters in passwords.
Choose the minimum number of complexity requirements your users' passwords should satisfy as per your organization's security needs.
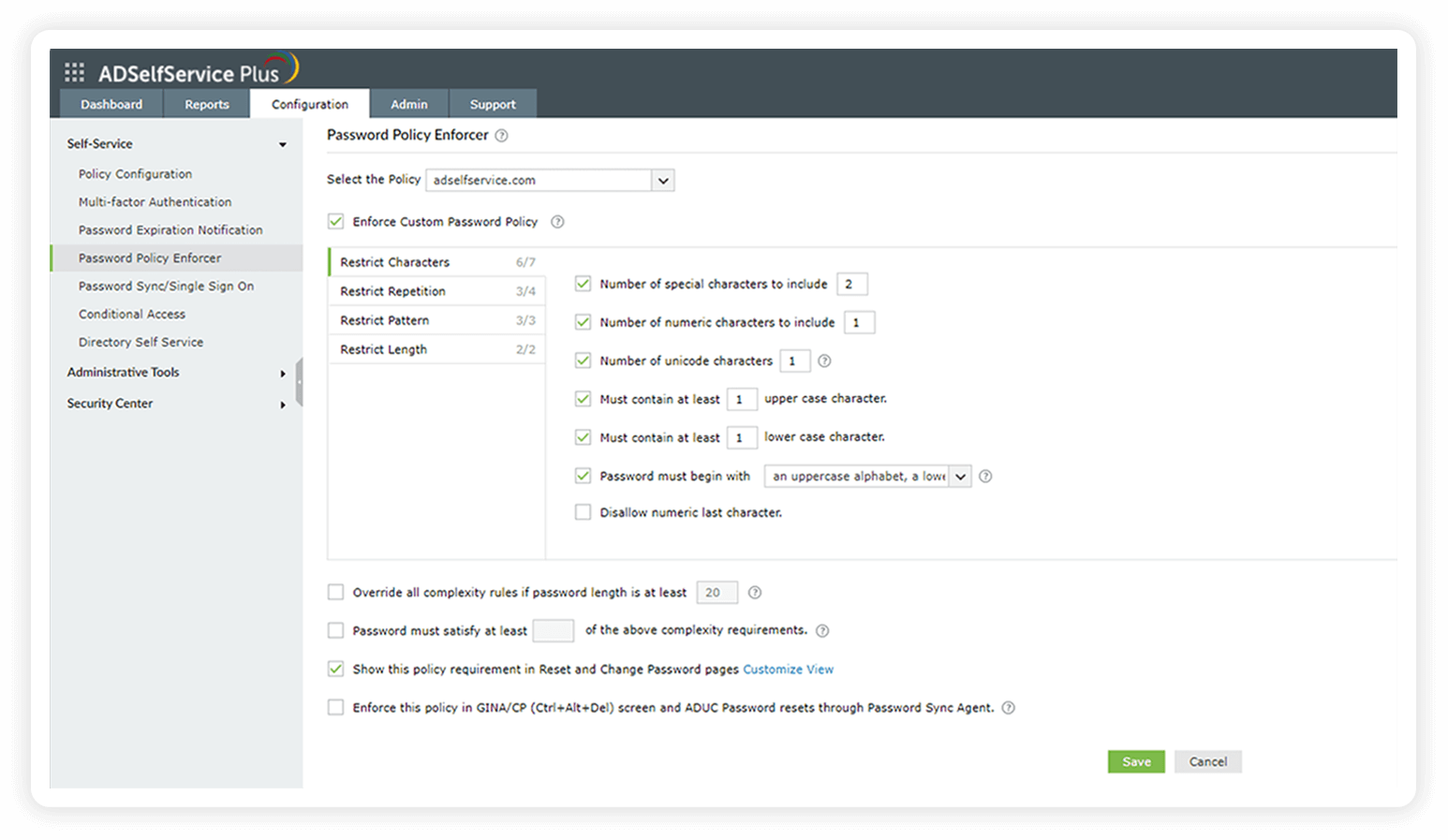
Restrict users from reusing any of their previously used passwords during password creation.
Configure the minimum password length and the inclusion of alpha-numeric characters in passwords.
Choose the minimum number of complexity requirements your users' passwords should satisfy as per your organization's security needs.
Choose from a plethora of different authenticators to verify your users' identities.
Secure all endpoints in your network using MFA.
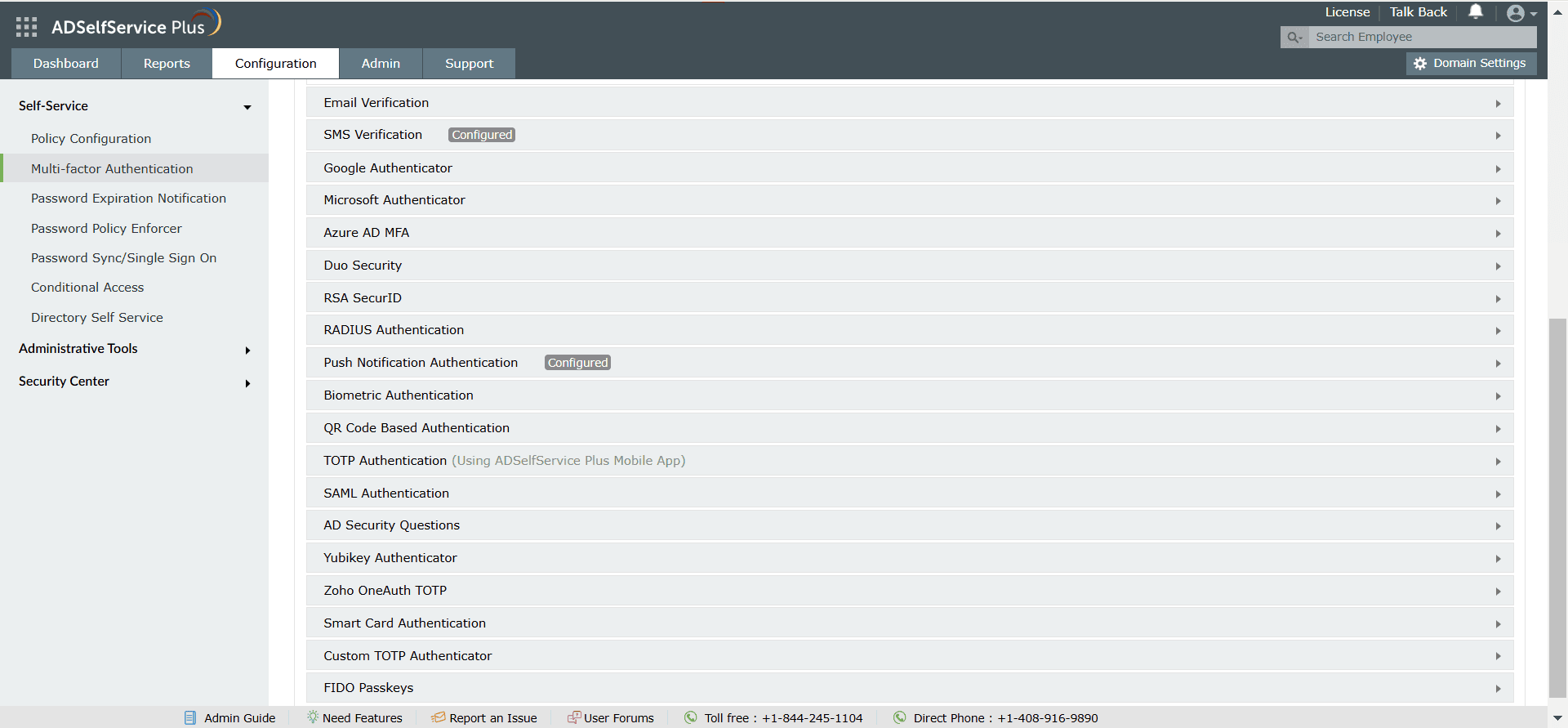
Choose from a plethora of different authenticators to verify your users' identities.
Secure all endpoints in your network using MFA.
Benefits of using ADSelfService Plus to comply with the CJIS
- Enforce OU- and group-based policies
Granularly enforce multiple password policies in the same AD domain based on OU and group memberships.
- Increased password security
Enforce passphrases and restrict the repetition of characters from old passwords and usernames.
- Notify users about password expiry
Use custom password expiration notifications and ensure that users change their passwords on time.
- Custom template creation
Create multiple password policies that comply with the PCI DSS, HIPAA, NIST SP 800-63B, SOX, and CJIS standards.
Highlights of ADSelfService Plus
Password self-service
Eliminate lengthy help desk calls for Windows Active Directory users by empowering them with self-service password reset and account unlock capabilities.
One identity with single sign-on
Get seamless one-click access to more than 100 cloud applications. With enterprise single sign-on, users can access all their cloud applications using their Windows Active Directory credentials.
Password synchronization
Synchronize Windows Active Directory user passwords and account changes across multiple systems automatically, including Microsoft 365, Google Workspace, IBM iSeries, and more.
MFA
Enable context-based MFA with 20 different authentication factors for endpoint, application, VPN, OWA, and RDP logins.
Password and account expiration notifications
Notify Windows Active Directory users of their impending password and account expiration via email and SMS notifications.
Password Policy Enforcer
Strong passwords resist various hacking threats. Enforce Windows Active Directory users to adhere to compliant passwords by displaying password complexity requirements.










