- Free Edition
- Quick Links
- MFA
- Self-Service Password Management
- Single Sign-On
- Password Synchronizer
- Password Policy Enforcer
- Employee Self-Service
- Reporting and auditing
- Integrations
- Related Products
- ADManager Plus Active Directory Management & Reporting
- ADAudit Plus Real-time Active Directory Auditing and UBA
- Exchange Reporter Plus Exchange Server Auditing & Reporting
- EventLog Analyzer Real-time Log Analysis & Reporting
- M365 Manager Plus Microsoft 365 Management & Reporting Tool
- DataSecurity Plus File server auditing & data discovery
- RecoveryManager Plus Enterprise backup and recovery tool
- SharePoint Manager Plus SharePoint Reporting and Auditing
- AD360 Integrated Identity & Access Management
- Log360 (On-Premise | Cloud) Comprehensive SIEM and UEBA
- AD Free Tools Active Directory FREE Tools
What is a phishing attack?
Phishing is a type of cyberattack in which hackers steal users' sensitive information by sending convincing fraudulent emails or messages containing malicious links in disguise. There are many types of popular phishing attacks, namely email phishing, spear phishing, whaling, smishing, and vishing.
A study by Valimail, an email security company, indicates that approximately 3 billion malicious emails are sent daily, which accounts for nearly 1% of all emails sent.
How and why are phishing attacks successful?
Phishing, unlike most cyberattacks, directly interacts with users and exploits their lack of discernment. In the case of other cyberattacks, like brute-force and dictionary attacks, IT admins can intervene and deploy mechanisms such as Active Directory MFA to defend against them. But, in phishing, the success of the attack and the security of an organization depends solely on users and their ability to distinguish and dodge these attacks.
Phishing attacks are cleverly devised to trick users. To ensure that there is a certain degree of truth in the messages, attackers throw disinformation into the mix—like creating a fake scenario that mentions the correct names of people or locations associated with the targeted victim. Phishing emails or messages will aim at creating a sense of urgency in users. In their panic, users fail to validate the authenticity and logic of the message and fall victim to the attack.
What is phishing-resistant MFA and how does it work?
Phishing-resistant multi-factor authentication (MFA) is an identity verification technology which is not susceptible to phishing attacks. This is because, contrary to traditional MFA methods like SMS OTPs and push notifications, phishing-resistant MFA does not require action from the user, removing the vulnerable human element from the MFA process.
The US Federal Government's Zero Trust strategy talks about two phishing-resistant MFA technologies: the FIDO2 WebAuthn standard and PIV smart cards. These technologies utilize asymmetric cryptography principles and respond solely to valid authentication requests while also verifying user intent throughout the authentication process.
The FIDO standard was created by the FIDO Alliance, a non-profit consortium consisting of several organizations worldwide. In FIDO2-based authentication technology, the identity provider (IdP) creates a unique cryptographic key pair, also known as asymmetric or public-key cryptography, for the device (mobile device or special token, like YubiKey) that a user enrolls with. Based on this key pair, the IdP can know and trust the device, and all communication to and from the device will be recognized as legitimate and not from a malicious actor. But, since there is a possibility of the device being stolen, biometric authentication is mandated on top of this process. This means that from the user's perspective, biometric authentication will be perceived as the only identity verification method involved.
The personal identity verification (PIV) standard is quite similar to the FIDO2 standard and uses smart cards to provide secure phishing-resistant MFA.
Phishing-resistant MFA with ADSelfService Plus
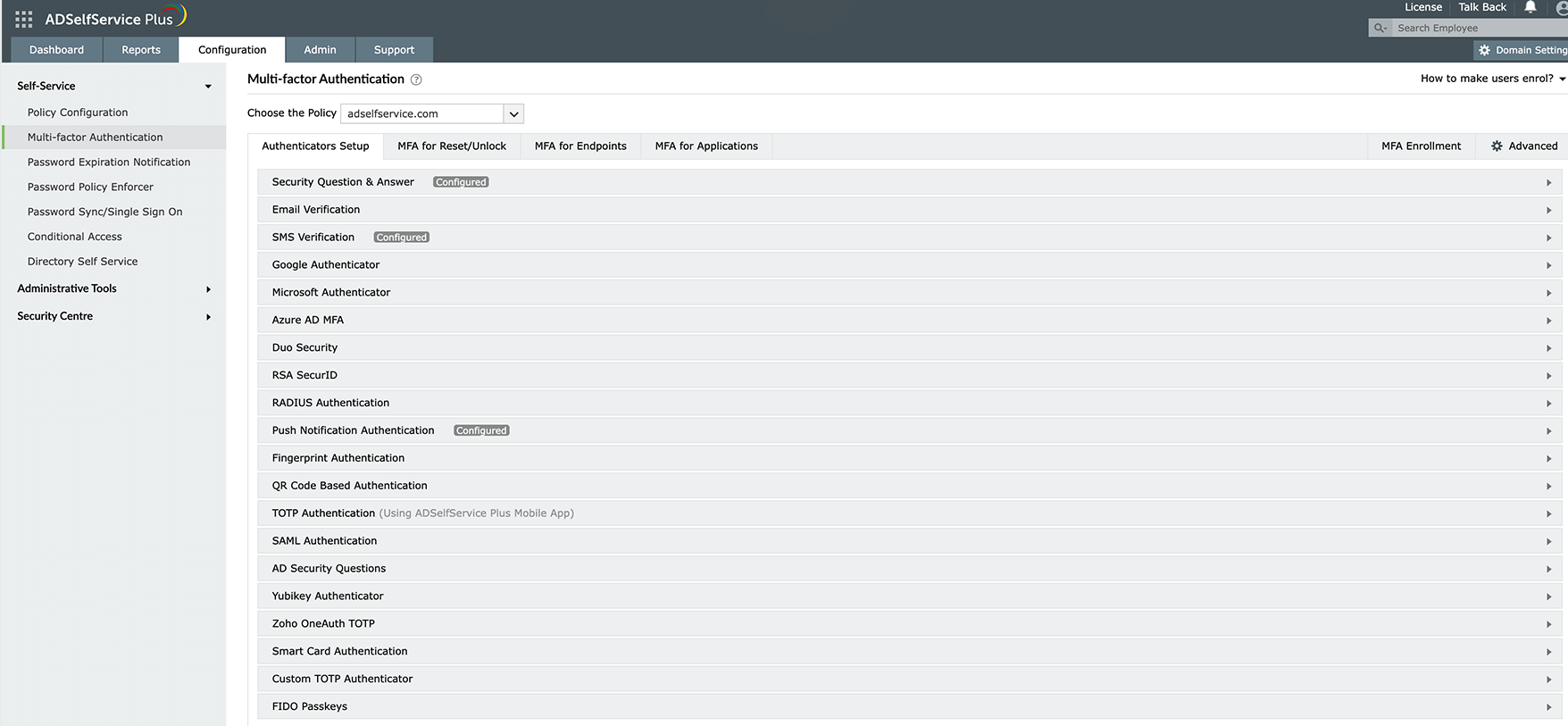
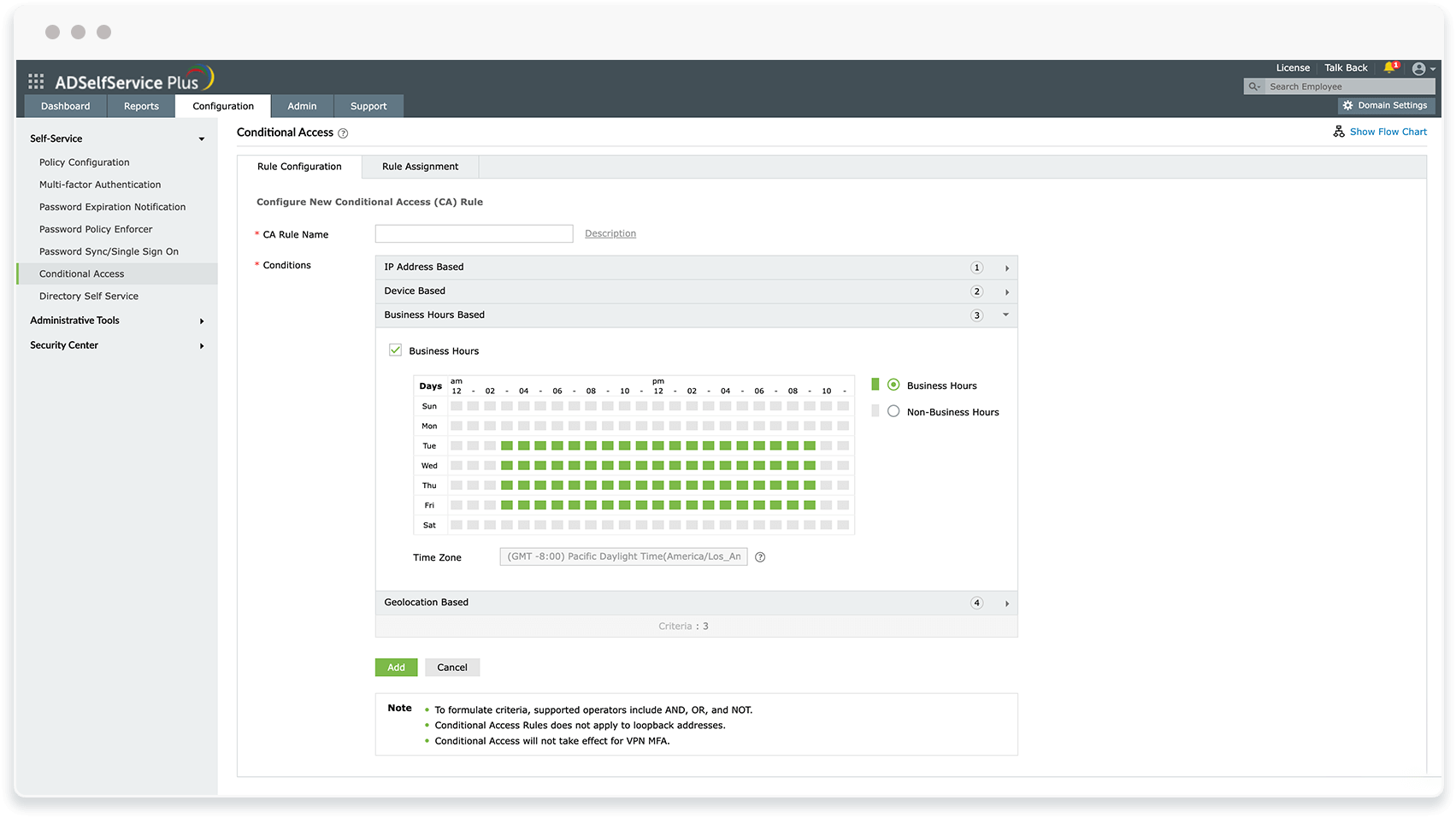
ManageEngine ADSelfService Plus offers adaptive MFA with 20 different authenticators, including the phishing-resistant FIDO2 authenticator. You can deploy MFA to secure on-premise and cloud application logins, machines, VPNs, OWA, and self-service password management activities. With ADSelfService Plus, you can customize the MFA authentication flow for different user accounts based on their OU and group memberships, so you can more tightly secure privileged accounts and activities from cyberthreats.
Multiple MFA authenticators
Conditional access
Benefits of implementing phishing-resistant MFA using ADSelfService Plus
-
All access points secured with MFA
Implement phishing-resistant MFA for your users logging in to endpoints, cloud and on-premises applications, VPNs, and OWAs.
-
Multiple customizable authenticators
Tailor MFA for users based on their privileges and choose from 20 different authenticators to do so.
-
Compliance with regulatory standards
Make your organization comply with various regulatory standards including NIST SP 800-63B, PCI DSS, and HIPAA.
Highlights of ADSelfService Plus
Password self-service
Unburden Windows AD users from lengthy help desk calls by empowering them with self-service password reset and account unlock capabilities.
Multi-factor authentication
Enable context-based MFA with 20 different authentication factors for endpoint, application, VPN, OWA, and RDP logins.
One identity with single sign-on
Get seamless one-click access to more than 100 cloud applications. With enterprise single sign-on (SSO), users can access all their cloud applications using their Windows AD credentials.
Password and account expiry notifications
Notify Windows AD users of their impending password and account expiry via email and SMS notifications.
Password synchronization
Synchronize Windows AD user passwords and account changes across multiple systems automatically, including Microsoft 365, Google Workspace, IBM iSeries, and more.
Password policy enforcer
Strong passwords resist various hacking threats. Enforce Windows AD users to adhere to compliant passwords by displaying password complexity requirements.