Stop Ransomware before it stops you
Take control of your endpoints with swift ransomware detection and neutralization while restoring operations with unmatched speed and resilience.
Ransomware is a ticking bomb. One wrong click can cripple your organization and its consequences are immediate and devastating. Attackers are moving fast, and so must you. Our multi-layered Anti-ransomware solution identifies threats in the real-time, isolates infected systems and restores endpoints in minutes. With the intelligence to prevent future threats, we ensure that ransomware doesn't disrupt operational continuity. Protect your endpoints against downtime. Make your business unbreakable.
Kills ransomware while coexisting with your security stack.
Your backups stay away from the prying eyes of ransomware.
Restore operations within minutes, giving you the best of speed and simplicity.
24/7 autonomous security on every endpoint.
With low false positive rates, we focus on real threats, not false alarms.
Effortless efficiency meets uninterrupted business productivity.
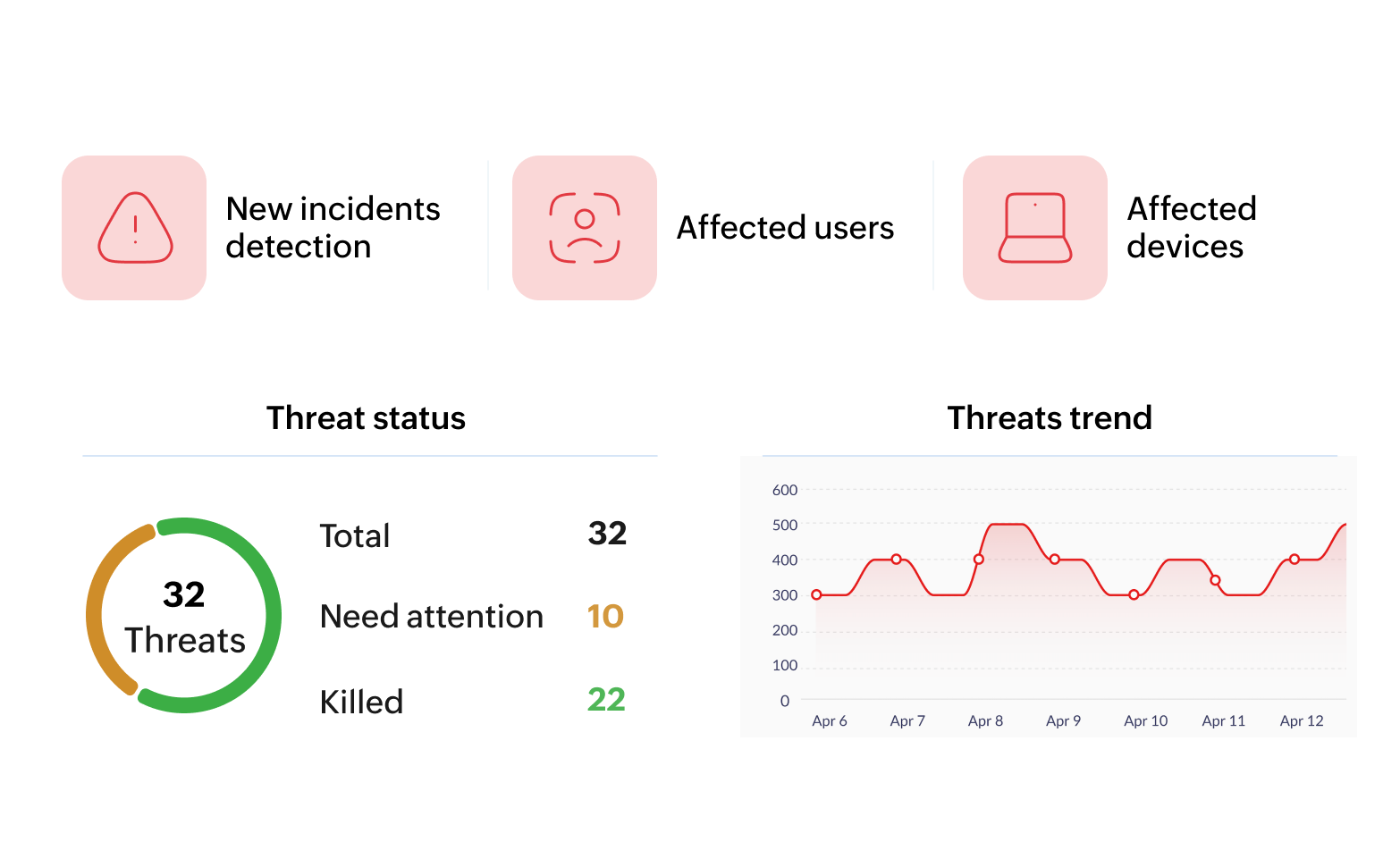
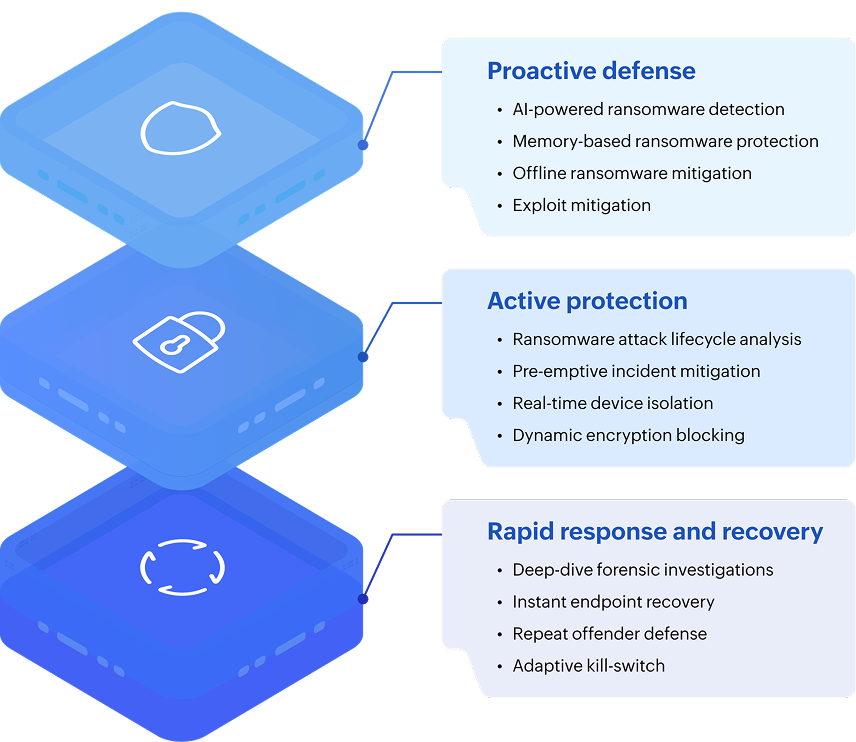
Safeguard your enterprise with comprehensive end-to-end ransomware protection
Analyze processes and file behaviour to detect unusual alteration, deletion, or modification patterns instead of relying on signature-based detection.

Detect ransomware running directly in memory or through scripts, bypassing traditional antivirus methods.
Reduce dependency on regular definition updates for ransomware detection. Protect your endpoints even in low/no network conditions.

Map the entire ransomware attack lifecycle, from device entry point to process information, for deeper insights.

Identify TTPs (tactics, techniques, and procedures) of ransomware attacks on the VirusTotal community and from the MITRE technique ID.
Pinpoint hashes of malicious files, IPs and URLs used for malicious files associated with ransomware attacks.

Prevent suspicious activities, such as encrypting files and modifying critical system files.
Detect and neutralize ransomware that leverages software vulnerabilities for access.
Automatically quarantine infected endpoints to prevent ransomware from spreading across the network.
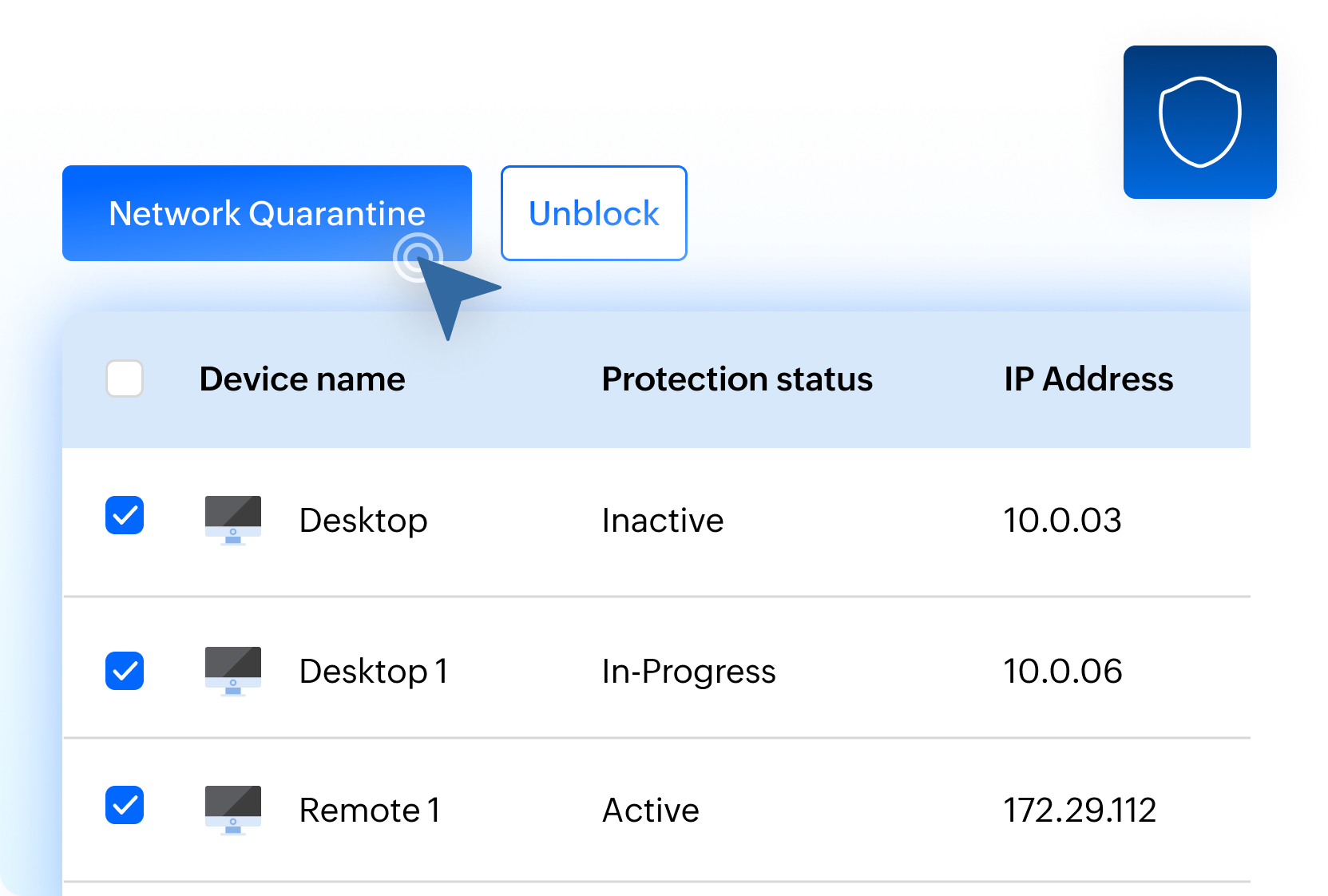
Instantly kill ransomware processes or intervene manually to remediate infected files.
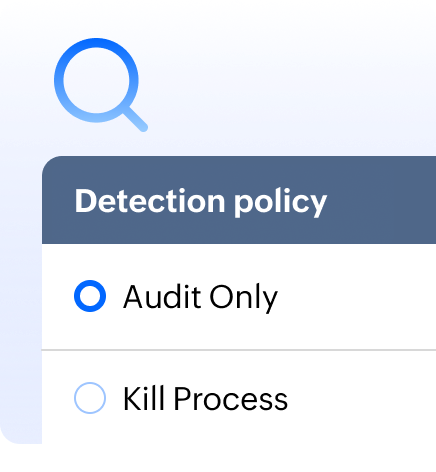

Detect programs exhibiting behaviours tied to known ransomware and instantly neutralize the threat before it causes any damage.
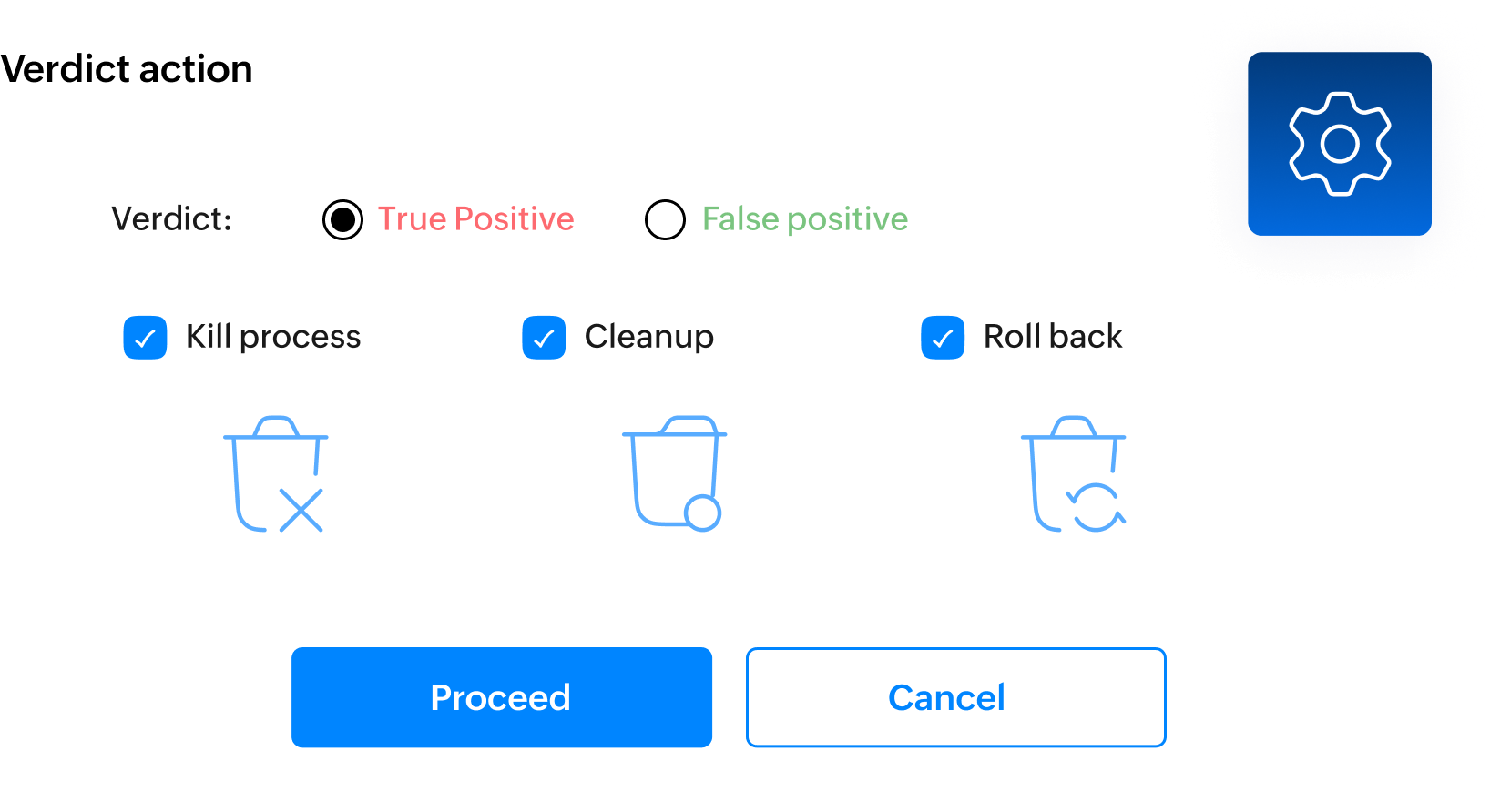
Quickly roll back infected systems to a pre-attack state, minimizing downtime and impact. Our Anti-ransomware utilizes Microsoft VSS to create copies of endpoint files every three hours and automatic restoration will occur in the event of a ransomware attack.
Defend your business operations and reputation with comprehensive protection against ransomware attacks



system bandwidth used by our agent, minimizing resource footprint.
endpoints currently under continuous 24/7 protection
ransomware detection accuracy with patented behaviour analytics engine
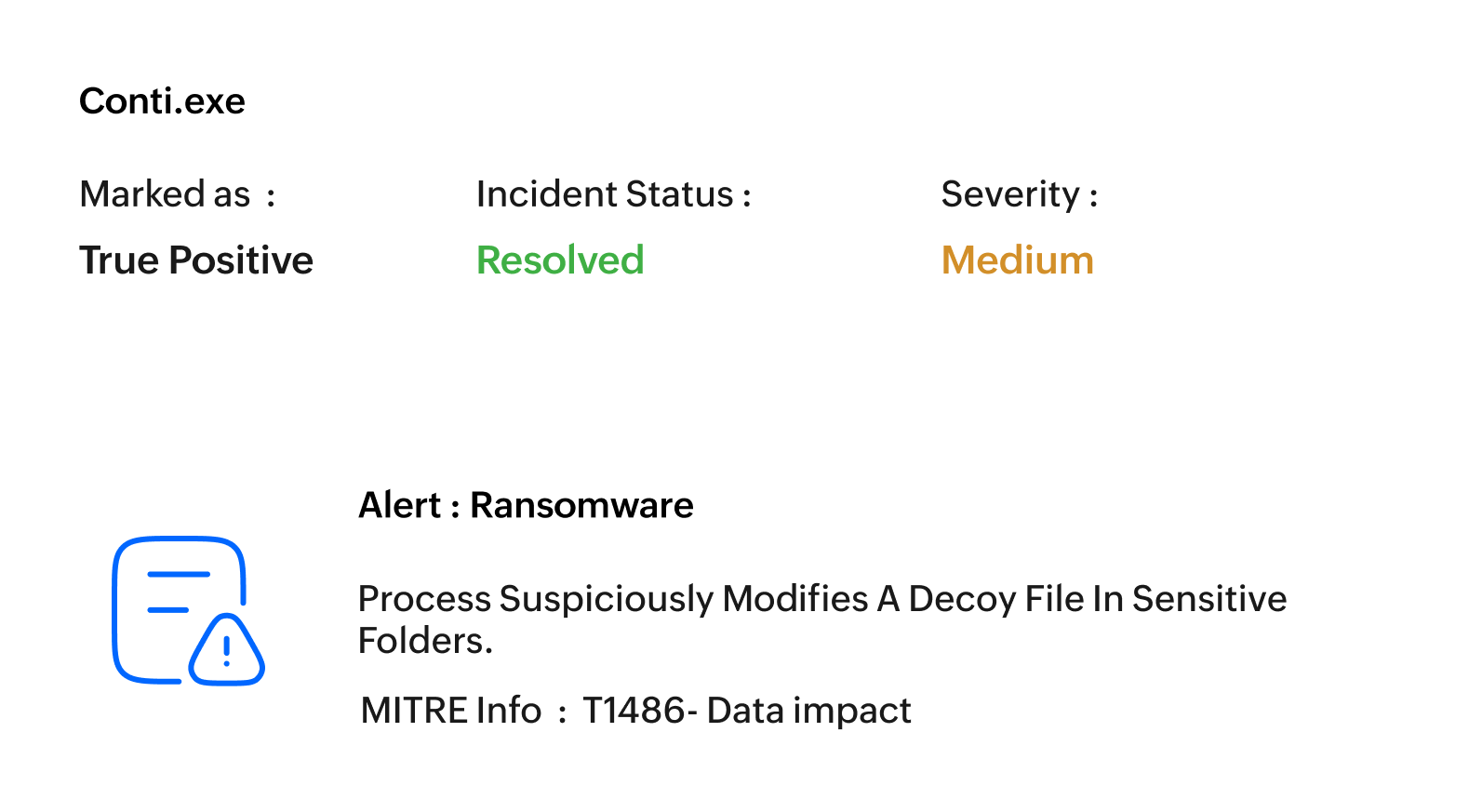
See through every ransomware attack from its source to the systems affected with detailed root cause analysis.
VIEW REPORTAccess a suite of endpoint management and security operations solutions in one place.
Secure your workplace with integrated endpoint protection and meet compliance mandates.
Optimize your budget by combining endpoint management and security into a single, efficient platform.