Time to time, zero-days will rear their ugly heads, so poise yourself with a secure foundation by ensuring ideal security configurations are established and maintained in your endpoints, so that your organization doesn't fall apart from a single vulnerability.
Security configuration management involves continually detecting configuration drifts and misconfigurations across various components in your endpoints, and bringing them back into alignment.
In this article, you'll learn how Vulnerability Manager Plus, a complete threat and vulnerability management solution, facilitates the entire cycle of security configuration management including detecting misconfigurations, categorizing and profiling them, resolving them with built-in remediation, and reporting the final configuration posture—all from a single interface.
Equip yourself with the Vulnerability Manager Plus's Security Configuration Management dashboard, built exclusively to track and combat misconfigurations - try now for free!
Endpoint security doesn't end with vulnerability assessment. If vulnerabilities are the gateway into the network, it's the overlooked misconfigurations that attackers leverage to laterally move and exploit other machines within the network. Basically, any poorly documented configuration changes, default settings, or a technical issue across any component in your endpoints could lead to a misconfiguration. But the question is how equipped you are to address these configuration drifts?
For instance, try asking yourself the following questions. How many users in your network retain their default passwords? Do your employees have administrative privileges by default? Have you restricted your TLS/SSL communications from using weak and insecure cipher suites? Are new computers brought into your network left with default configurations and insecure protocols? Are you aware of these and other security misconfigurations?
A simple flaw like a default password or an open share can be leveraged by an attacker to thwart an organization's security efforts. Attackers could use malware and ransomware to exploit legacy protocols and open shares, as occurred in the worldwide 2017 WannaCry attack. All the stated concerns underscore the necessity of having a comprehensive security configuration management tool to be able to monitor and regulate the configuration posture of your endpoints to ensure security.
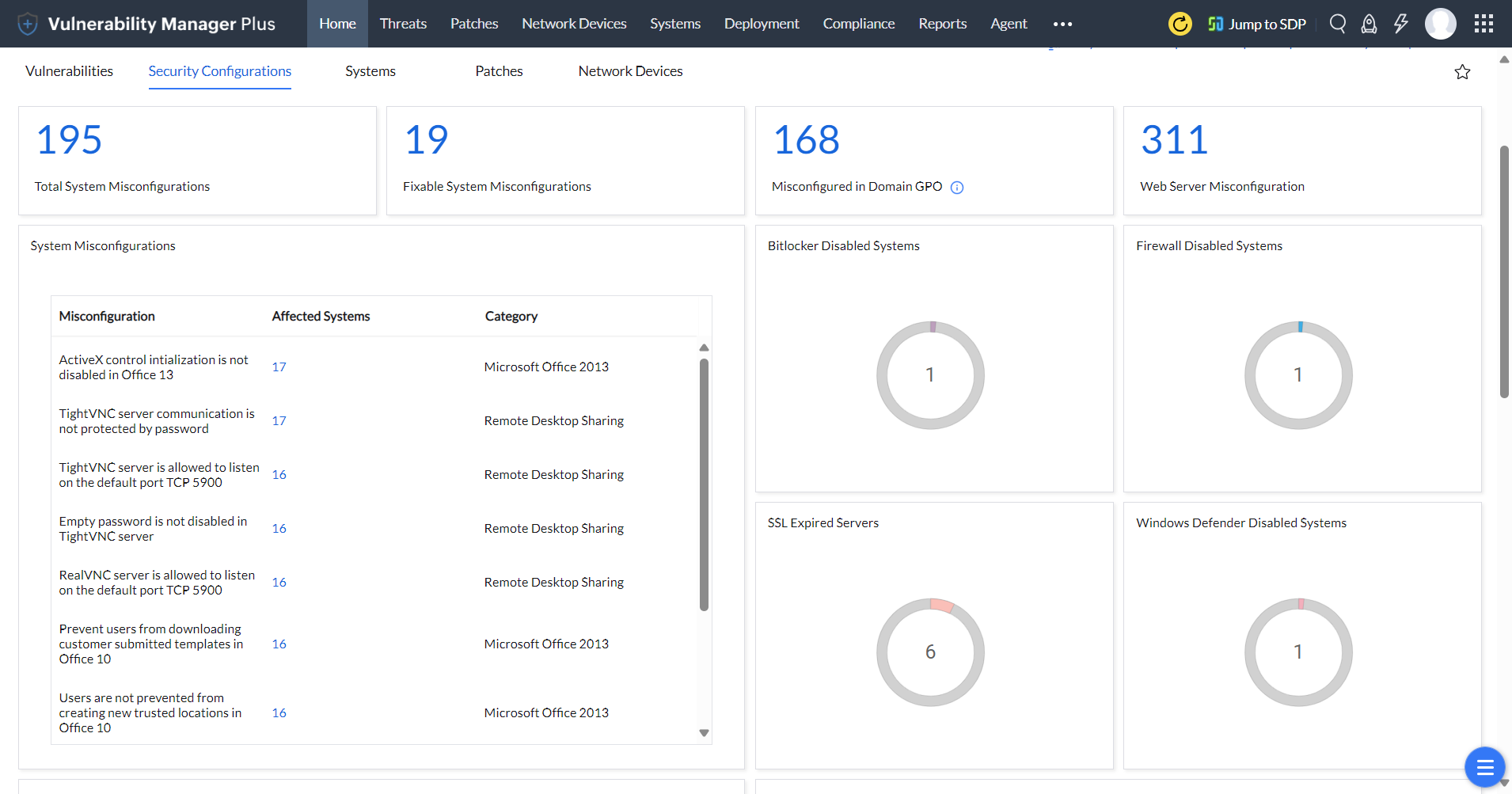
To err is human, but to detect misconfigurations and bring them back to compliance is the job of Vulnerability Manager Plus. With a predefined library of security configuration baselines derived from industry standards and best practices, it continuously detects, without user's instigation, systems that are not in alignment and reports it on the console. You can see details such as the category of the misconfiguration, number of affected systems, and the severity levels.
When you select an item from the list, a flyout panel opens with an elaborate description and resolution. You can push the resolution right from there to all affected machines and close the SCM loop instantly. This panel also displays whether an attribute for a particular component is misconfigured in domain GPO. In that case, a knowledge base article with detailed resolution steps linked in place of resolution navigates the users to alter security configurations in the GPO. Vulnerability Manager Plus can even predict potential network complications that may arise in the future due to configuration modifications, which helps you safely alter the configurations without impeding critical business operations.
Finally, you can generate executive reports to track your efforts and keep higher authorities informed of your organization's security configuration posture. It's also important to note that security configuration management not only improves cyber resilience, but also enhances operational efficiency.
While this feature deals with a wide range of security settings across various components of your systems, OS, and applications, let's cast a brief look at the notable ones that we're often concerned with.
A firewall misconfiguration can fail to prevent unsecure traffic from penetrating an endpoint in your network. With security configuration management, you can check whether a built-in windows firewall is enabled or a third-party firewall is present. You can also ensure connections are blocked in the firewall to the NetBIOS trio, the infamous WannaCry abettor port 445, and other vulnerable ports that allow unauthorized and unintended actions.
Weak passwords are the most common security misconfiguration that plagues the enterprises quite often. "The longer the password, the stronger it is" no longer applies. Attackers are constantly developing new strategies, such as purchasing credentials used in previous breaches to launch password-based brute force and dictionary attacks. Moreover, 62 percent of users admit reusing a password. Besides enforcing long passwords, you can make users adhere to a mix of predefined password policies such as password complexity, minimum password age, maximum password age, how many unique passwords that must be used before old passwords can be reused.
Ensure potentially unsafe features and contents are disabled and optimum security controls are enabled in Microsoft Office applications. This may include enabling Trustbar notifications, secure encryption methods for the files and metadata the applications use, password protection for files, Automation Security settings and much more.
Not protecting your disk volumes can lead to data breaches. You can ensure that BitLocker encryption is enabled to encrypt entire disk volumes to prevent unauthorized access to disks and exfiltration.
By securing your remote desktop connections with a strong password and preventing the server from listening on default ports, you can hamper a threat actors's attempts to establish an unauthorized remote connection.
It's important to monitor and have control over what you share within your network. Ransomware and other malware can easily identify and spread to the computers that have shared folders with write permissions from a compromised computer. Gaining details on which folder shares and default admin shares are enabled helps you eliminate network share misconfigurations.
Security configuration management allows you to ensure secure logon is enabled, and that sensitive details are not displayed at the lock screen. This helps you enforce account lockout duration, account lockout threshold, and reset lockout counter after policies from a centralized location to prevent brute-force attacks.
Removing users' admin rights could resolve 94 percent of all critical Microsoft vulnerabilities, according to a recent study. Security configuration management enables you to revoke user rights to unintended users, enforce least privilege, and ensure admin accounts are not displayed during elevation, thereby enhancing endpoint security.
Identify and disable default built-in accounts, such as guests, built-in administrator, and other local admin accounts that serve as an easy target for brute-force attacks.
User Account Control (UAC) prevents unauthorized changes to your computer by displaying elevation prompt in secure desktop mode, prompting administrators for consent, enabling Admin Approval Mode for the Built-in Administrator account, prompting standard users for administrative credentials on the secure desktop, and much more.
OS security hardening establishes a miscellaneous set of security controls, such as disabling autoplay for devices and restricting autorun commands. You need to make sure memory protection settings, logon authentication settings, Structured Exception Handling Overwrite Protection (SEHOP), Data Execution Prevention (DEP), Address Space Layout Randomization (ASLR), and other security settings are configured appropriately for the OS.
Certain browser misconfigurations, such as firewall traversal from remote host, geolocation tracking, allowing unsecure plugins, and enabling users to bypass smartscreen warnings can lead to browser-based attacks. With Vulnerability Manager Plus to eliminate browser misconfigurations, you can enable safe browsing, restrict unsecure plugins, deploy browser updates, and implement other safe browser security settings quickly and efficiently.
To ensure the confidentiality and integrity of the data transmitted between server and clients, security configuration management disables cryphotographically insecure TLS/SSL encryption protocols and enables the latest and more secure TLSv1.2. Also, it restricts the TLS encrypted communications from using default, NULL, or other insecure cipher suites and algorithms.
Legacy protocols, such as Telnet, SMB (Server Message Block), SNMP (Simple Network Management Protocol), TFTP (Trivial File transfer Protocol), and other legacy protocols might reveal system configuration information, provide unintended access to remote hackers, and pave the way for denial of service attacks. You can find out devices in which these protocols are enabled, and put an end to them quickly.
View a list of the security misconfigurations detected by Vulnerability Manager Plus along with their resolution, GPO location and security considerations.
It is imperative that you take proactive measures to avoid becoming a cyberattack victim. Download a 30-day, free trial of Vulnerability Manager Plus now to establish a secure foundation and thwart rogue hackers.