The number of vulnerabilities has skyrocketed in recent years, and organizations around the globe are puzzled over how to conduct a successful vulnerability assessment. To address this concern, you need to start by determining what you are trying to achieve with a vulnerability assessment process so you can fine-tune it to meet your organization's individual needs.

We'll cover:
The objective of vulnerability management is to keep IT infrastructure risks under control at all times. A crucial part of the vulnerability management life cycle, the vulnerability assessment process helps you qualify the risks vulnerabilities pose to your ecosystem so that you can distinguish what should be prioritized immediately and what can be patched on a scheduled basis. However, while trying to minimize the risk, you might encounter situations where there is no direct way to fix vulnerabilities, or fixing the issue would lead to undesirable consequences.
To be effective, a comprehensive vulnerability assessment process should guide you in understanding, and deciding on the optimal course of action in these four common scenarios:
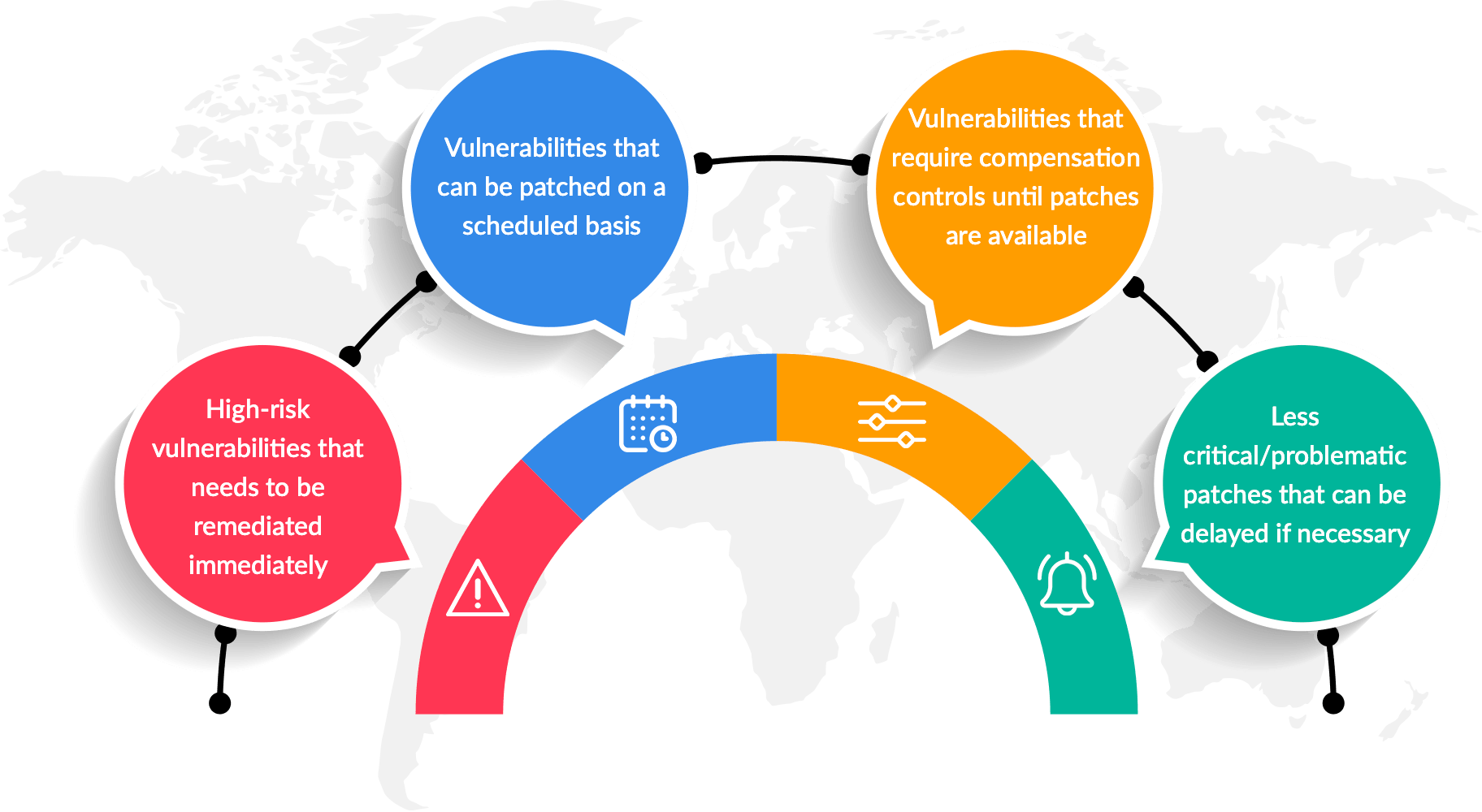
Let's get into the specifics of ManageEngine's vulnerability assessment tool, including how it helps you identify vulnerabilities that belong to each of the cases mentioned above so that you can respond accordingly.
Vulnerability Manager Plus is a prioritization-focused threat and vulnerability management solution with built-in patch management. Vulnerability Manager Plus leverages multipurpose agent technology to continuously monitor all your endpoints, whether they're in your local network, at a remote location, and on the move. This ensures all vulnerabilities impacting your endpoints are discovered and displayed in a web console that provides meaningful context and actionable insights.
Watch the short video below to have a quick glance at the Vulnerability Manager Plus console and see how it works
Continue reading to learn everything you need to know about Vulnerability Manager Plus's vulnerability assessment process.
Many organizations face too many vulnerabilities but have too little time to patch them. For instance, it's impractical to have all Windows machines be up-to-date with all the newly released patches the day after Patch Tuesday. But attackers are increasingly successful at developing exploits within a week or so of public disclosures. That is why organizations need to patch smartly rather than attempt to patch faster and deploy untested patches that may break the network and extend downtime. Vulnerabilities don't pose equal risk. Some vulnerabilities are imminently exploitable and even wormable without a hacker's instigation. This is where Vulnerability Manager Plus' risk-based vulnerability assessment process comes into play.
The primary goal of a vulnerability assessment process is to prioritize high-risk vulnerabilities. The risk of a vulnerability generally corresponds to how exploitable it is, and how big an impact would result if the infrastructure were exploited. Severity ratings and Common Vulnerability Scoring System (CVSS) ratings only give you a superficial assessment of risk. Learn why relying entirely on CVSS scores for your vulnerability assessment process presents you with a substantial number of vulnerabilities classified as Severe but which pose little to no risk.
In addition to CVSS scores, Vulnerability Manager Plus equips you with a comprehensive set of risk factors to perform a multivariate, risk-based vulnerability assessment process.. These include:
Now that we've extracted the variables essential to rigorously assess your risk, let's discuss how they help you in other areas.
Knowing whether an exploit is publicly available for a vulnerability is pivotal to vulnerability prioritization. These are the vulnerabilities that need immediate attention, since the exploit is out in the wild and anyone could leverage it to break into your network and steal sensitive data. If you only patch vulnerabilities based on severity, you might miss out on other threatening vulnerabilities that are easily exploitable. Nine out of 12 publicly exploited vulnerabilities resolved by Microsoft in 2019 were only rated as Important, not Critical. Vulnerability Manager Plus, besides providing the exploit availability information, keeps you informed on exploit activity on newly disclosed vulnerabilities via a continually updated security newsfeed. This helps you immediately focus your effort on securing your endpoints from these high-profile issues.
Once the vulnerability information is out, the clock starts ticking and the game is on between your security teams and threat actors. It's essential to keep track of how long severe vulnerabilities have been lurking within your endpoints. Also, a vulnerability that may seem less critical initially might prove to be fatal over time, since attackers eventually develop programs that can take maximum advantage of these flaws in ways you might never imagine. The best practice is to immediately resolve vulnerabilities that have an exploit available, as well as Critical ones. Vulnerabilities categorized as Important are more difficult to exploit, but should nevertheless be remediated within 30 days. Any vulnerability considered lower priority than Critical or Important should be remediated within 90 days.
Some assets are more important than others. Since web servers are at the perimeter of your network and are exposed to the internet, they’re easy targets for hackers. Database servers—which record a wealth of information like your customers’ personal information and payment details—should also be prioritized over other assets when defining the scope of your assessment, since even a lower-rated vulnerability on a business-critical asset like this might pose a high risk. Vulnerability Manager Plus provides you with a drilled-down view of assets displaying whether web servers, database, or content management systems are installed on them, along with vulnerabilities on those particular installations.
If a moderate to critical-level vulnerability is found to be impacting a larger proportion of IT assets, then it only makes sense to patch them immediately to lower the overall risk. In such cases, you can leverage Vulnerability Manager Plus to wipe out a group of vulnerabilities across multiple endpoints with a single patch deployment task.
Though ease of exploitation plays a significant role in risk assessment, exploitable vulnerabilities don’t necessarily warrant an attack. In fact, attackers don't focus on vulnerabilities just because they’ve have a readily available exploit or require less effort to exploit, but because the vulnerability furthers their goals. Only then is the availability, and ease of an exploit factored in. Vulnerability Manager Plus has filters to easily identify vulnerabilities that pose a particular impact such as denial-of-service, remote code execution, memory corruption, privilege elevation, cross-site scripting, sensitive data disclosure, etc.
It's safe to assume that vulnerabilities are a constant threat to the network. Manual intervention is required to accurately assess and address the high profile vulnerabilities consistently. But given the rate at which new vulnerabilities surface, manually it's both easy to overlook certain critical vulnerabilities, as well difficult to reduce the total number of unpatched vulnerabilities in your network.
While you focus on what matters the most, let Vulnerability Manager Plus' built-in patching module regularly clean up the vulnerabilities in your network by automating the entire cycle of patching—including missing patch detection, download, testing, and deployment—to Windows, Mac, Linux, and over 300 third-party applications. The comprehensive patching functionality enables you to choose the criteria of patches to be automated, specific target machines/custom groups to be patched, flexible deployment policies, patch testing, and approval as well as deployment schedules based on your business requirements. What's more, you can use pre-built Patch Tuesday-based deployment policies to synchronize your patching with monthly Patch Tuesdays, and more. Explore the exhaustive capabilities of Vulnerability Manager Plus' automated patch management.
When details about a highly-critical vulnerability have been released, but no patches are available yet from the vendor, it's important to stay vigilant and take actions swiftly to safeguard your assets. Some common occurrences and how Vulnerability Manager Plus helps you mitigate them early are described below.
When the proof of concept (PoC) code of a vulnerability is exposed before the security hole is acknowledged by the vendor, a zero-day exploit can occur. These vulnerabilities remain undisclosed and unpatched while presumably being exploited in the wild, even before the vendor knows about it.
Disgruntled security researchers might release details of vulnerabilities to the public to provoke unresponsive vendors to fix product security flaws promptly. There are also instances of vendors accidentally revealing information about flaws in security bulletins before patches are in place. A good example of this is the recently leaked details of the EternalDarkness flaw in Microsoft SMB v3.
You can also implement further security controls, such as isolating the affected machine or blacklisting the application, until a patch or work-around is available using an application control solution. Learn in detail about the ways in which Vulnerability Manager Plus can defend your network against zero-day exploits, zero-day vulnerabilities, and publicly disclosed vulnerabilities.
The risks of running an end-of-life software outweighs its benefits. End-of-life software doesn't receive security updates from the vendor, and will remain forever vulnerable. A legacy OS often can't run the latest applications, meaning it is stuck with legacy applications, which will eventually reach end of life. Businesses in regulated industries may also face significant fines for running out-of-date systems. Vulnerability Manager Plus helps you keep track of which applications and OSs are approaching or have already reached end of life. Once they reach end of life, you can take further steps, like implementing compensation controls such as host or network based intrusion prevention systems, but it's recommended that you migrate to the latest version of the end-of-life software to eliminate the risks for once and all.
Not all vulnerabilities need to be patched. Sometimes, patching may introduce new problems that exceed its benefits. Let's look at some of those not-so-normal scenarios when we can postpone or refrain from patching.
Servers have a thin window of time when changes and computer restarts are permitted. It is always recommended to patch them only when necessary, and postpone patches that resolve less-critical vulnerabilities to prevent extended downtime and disruption to ongoing business activities. Vulnerability Manager Plus enables you to create customized groups so you can isolate servers, such as those dedicated to mission-critical purposes. With that completed, you can exclude less critical patches when scheduling automated patch deployments to those server groups.
Some patches may turn out to be problematic during Vulnerability Manager Plus' automated patch testing, and they may cause downtime or disrupt application functionality when deployed to the production network. In these cases, Vulnerability Manager Plus gives you the option to decline those patches, and wait till vendors release a revised version of the patch.
In short, Vulnerability Manager Plus is the only overarching solution you need to tackle all the expected scenarios that arise during your vulnerability assessment procedure.
Don't wait! Claim your free, 30-day trial of Vulnerability Manager Plus and step up your vulnerability assessment process!