Are you a diligent IT admin with your hands glued to your system, eyes riveted on the monitor? Are you constantly probing the internet for new threats and categorizing discovered vulnerabilities in a vain attempt to prevent your organization from falling victim to a cyberattack? Well, you may be biting off more than you can chew.
New vulnerabilities are identified every 90 minutes. But don't panic; ManageEngine has the solution. Vulnerability Manager Plus is a smart, comprehensive vulnerability assessment tool that saves you time and effort by helping you:
Watch the video below for a quick glance at the Vulnerability Manager Plus console.
Vulnerability Manager Plus is a well-rounded vulnerability assessment tool that regularly scans your network for vulnerabilities, delivers insights into risk, and helps close the vulnerability management loop instantly with direct remediation from the console.
Eliminating blind spots is the key to efficient vulnerability assessment. As soon as it’s active in your network, Vulnerability Manager Plus automatically discovers all your Active Directory domains and workgroup endpoints. Enterprises that scale up quite often need not worry since new assets will be discovered once they're added to the network. Leveraging endpoint agent technology, you can keep tabs on your desktops, servers, laptops, virtual machines, web servers, databases, and workstations at all times. Whether your assets are in your local office, distributed across remote locations, located within a closed network like a demilitarized zone, or on the move, you can secure them all from a single console.
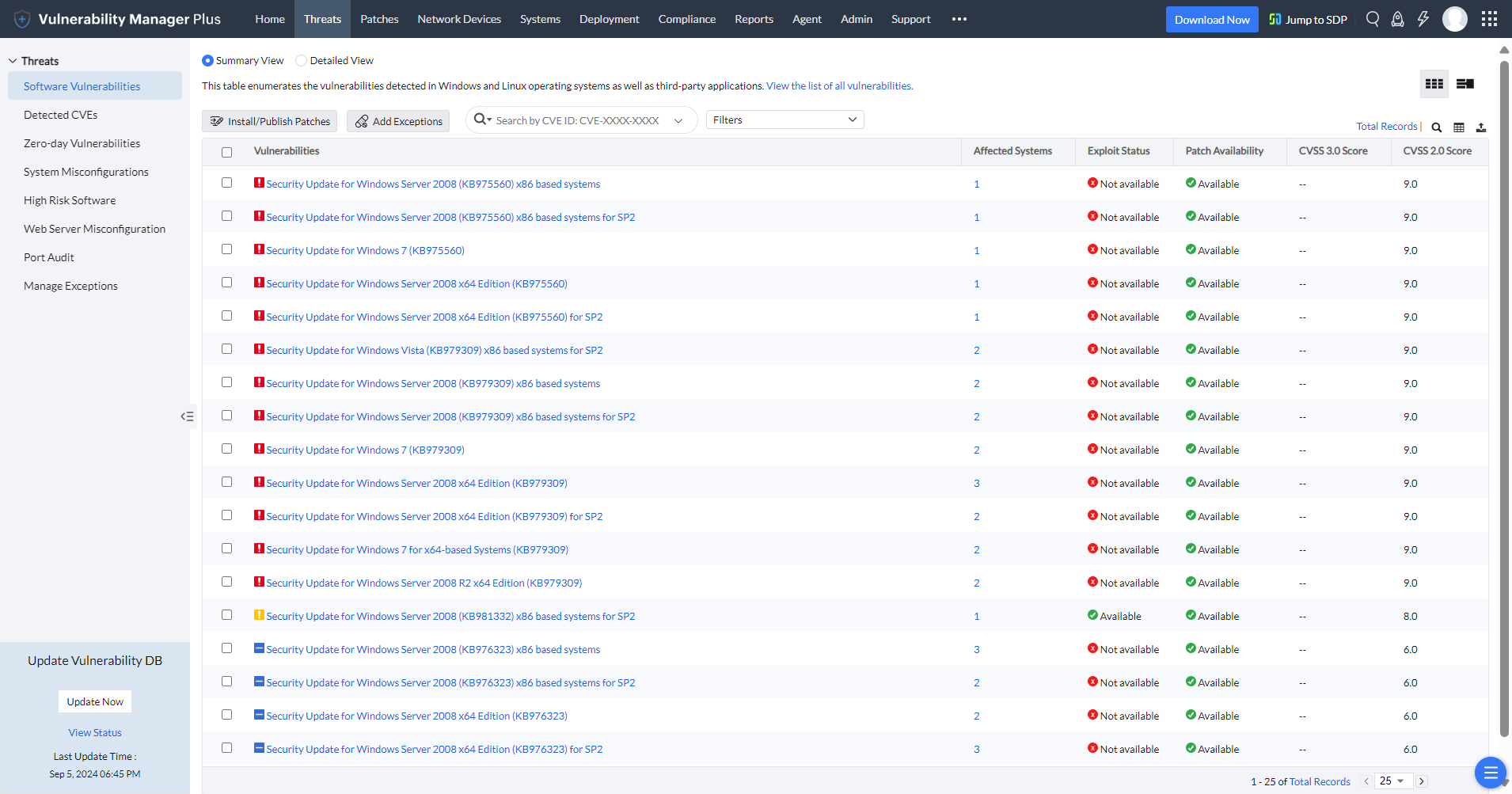
Detect all known and emerging vulnerabilities in all supported Windows operating systems and over 850 third-party applications, including content management systems, web servers, and database software. Extend your visibility beyond just software vulnerabilities, and keep tabs on misconfigurations, risky software, active ports, and more to ensure no threats fly under your radar.
There's a chance that you might fail to take timely action when you perform manual or scheduled vulnerability scans. Every new endpoint or software brought into your network introduces new vulnerabilities, leaving your IT exposed to prying hackers. To ward off dangers like this, you need to continually monitor your endpoints to identify and resolve new vulnerabilities as they emerge. Since Vulnerability Manager Plus utilizes agent-based scanning, it scrutinizes your endpoints every 90 minutes for new vulnerabilities without disrupting your network operations.
The primary goal of a vulnerability assessment is to make your data actionable. So, besides enumerating the vulnerabilities, the vulnerability assessment tool you're planning to deploy must help answer the following questions:
Attackers have a good idea of what works and what doesn't, so you need to learn, too. In addition to CVSS, Vulnerability Manager Plus sheds light on risk factors such as the availability of exploits, vulnerability age, affected asset count, CVE impact type, and patch availability to help triage exploitable and impactful vulnerabilities. What's more, you can directly search for the CVE IDs you're looking for or filter them to focus on high-impact vulnerabilities.
Vulnerability Manager Plus also features a security news feed that's continually updated with articles on recent vulnerabilities that attackers are discussing, experimenting with, or using, along with current exploits circulating in the wild.
To top it all off, a dedicated zero-day view grants instant visibility into actively exploited and publicly disclosed vulnerabilities.
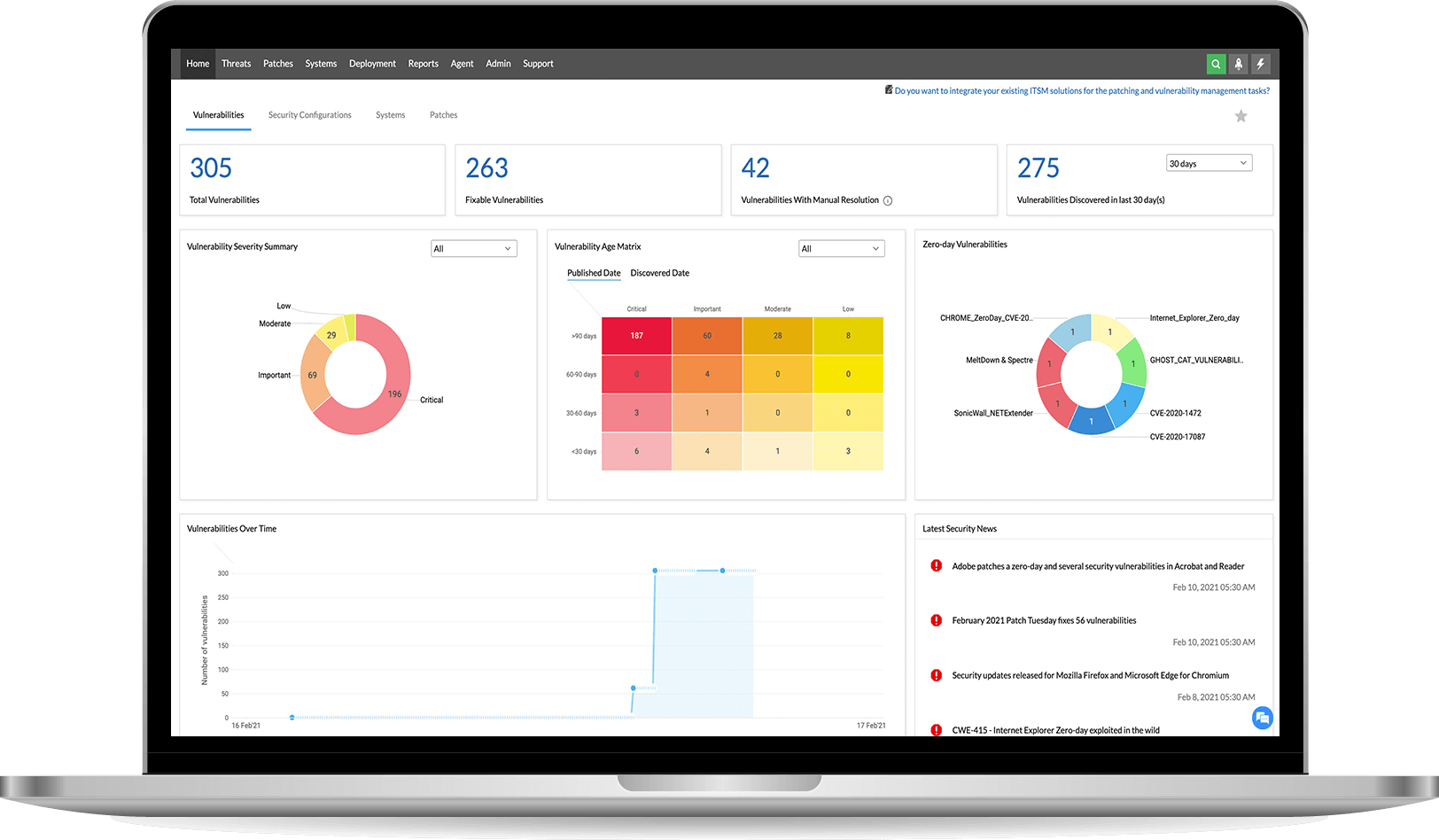
The vulnerability information collected across multiple endpoints is consolidated in a web console for centralized management and represented with meaningful context in dashboard widgets, translating to reliable and timely results. These interactive dashboard widgets are tailored to direct your attention to the most alarming areas in your network.
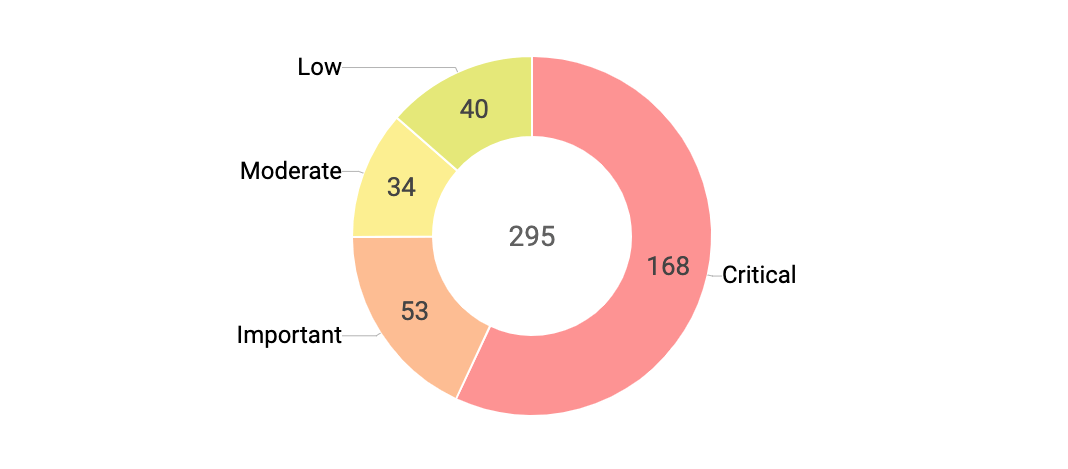
Don't dismiss the importance of severity rankings; they're the universal vulnerability risk assessment standard. The Vulnerability Severity Summary helps you track the number of vulnerabilities you need to resolve for each severity level, providing better visibility over how many critical vulnerabilities, like the easily exploitable remote code execution (RCE), elevation of privilege, and wormable vulnerabilities, are left unaddressed in your network.
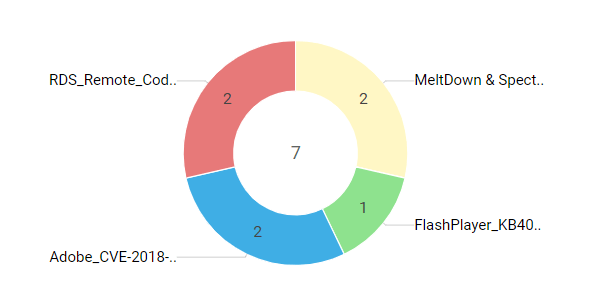
One of the most crucial aspects of a security vulnerability assessment is how effectively your vulnerability assessment tool keeps you informed of zero-day vulnerabilities. Zero-day vulnerabilities are the easiest targets for hackers since they are made known to the public or exploited in the wild before the vendor is able to release a patch to fix the flaw, so it's critical to ensure they don't get buried among the trifles. Vulnerability Manager Plus, along with a zero-day count chart, gives you an isolated view of zero-day vulnerabilities in your network so you can identify them promptly and either patch them or use an alternative mitigation measure available while waiting for a fix from the vendor. Take a look at how you can mitigate zero-day vulnerabilities with Vulnerability Manager Plus.
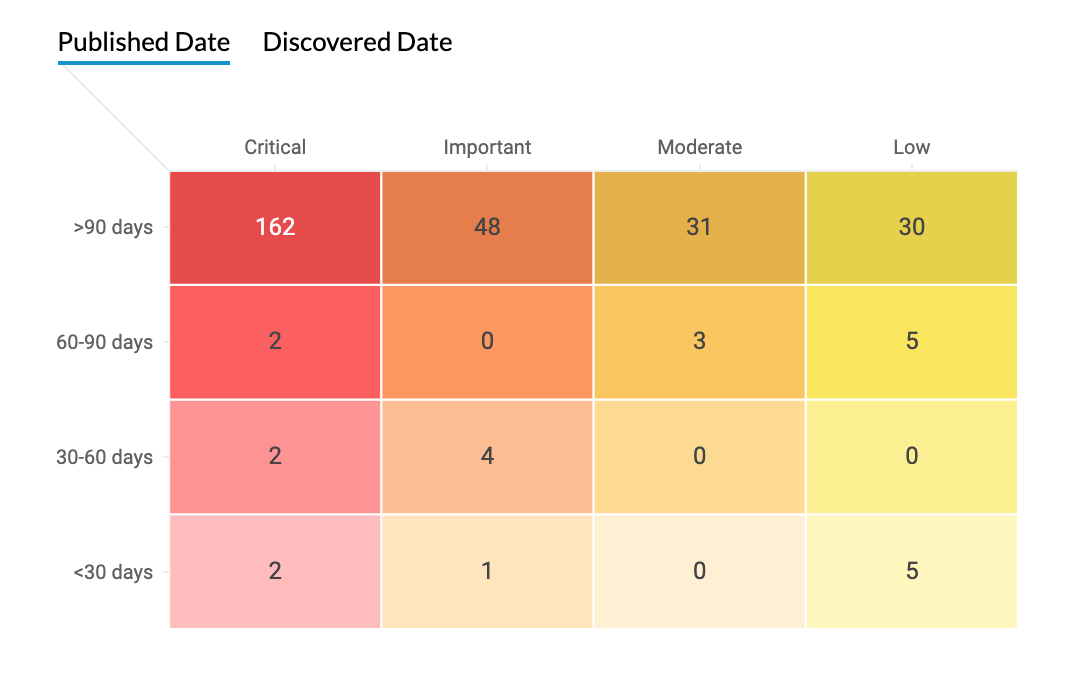
When it comes to vulnerabilities, time is the name of the game. The time between the vulnerability announcement and the exploit code disclosure has considerably shrunk in recent years. The longer you wait, the longer you leave your network wide open to attacks.
Critical vulnerabilities can often be exploited automatically without any user interaction, so these flaws have to be resolved immediately. Vulnerabilities categorized as important are more difficult to exploit, but should nevertheless be remediated within 30 days. Any vulnerability considered lower than critical or important should be remediated within 90 days.
The Vulnerability Age Matrix delivers a consolidated view of the age and severity of vulnerabilities, so you can focus your attention on vulnerabilities that need to quashed before the deadline. You can either choose to view the vulnerability age from the day it's published or from the day it's discovered in your network. You can also use the filter to display only vulnerabilities that have public exploits.
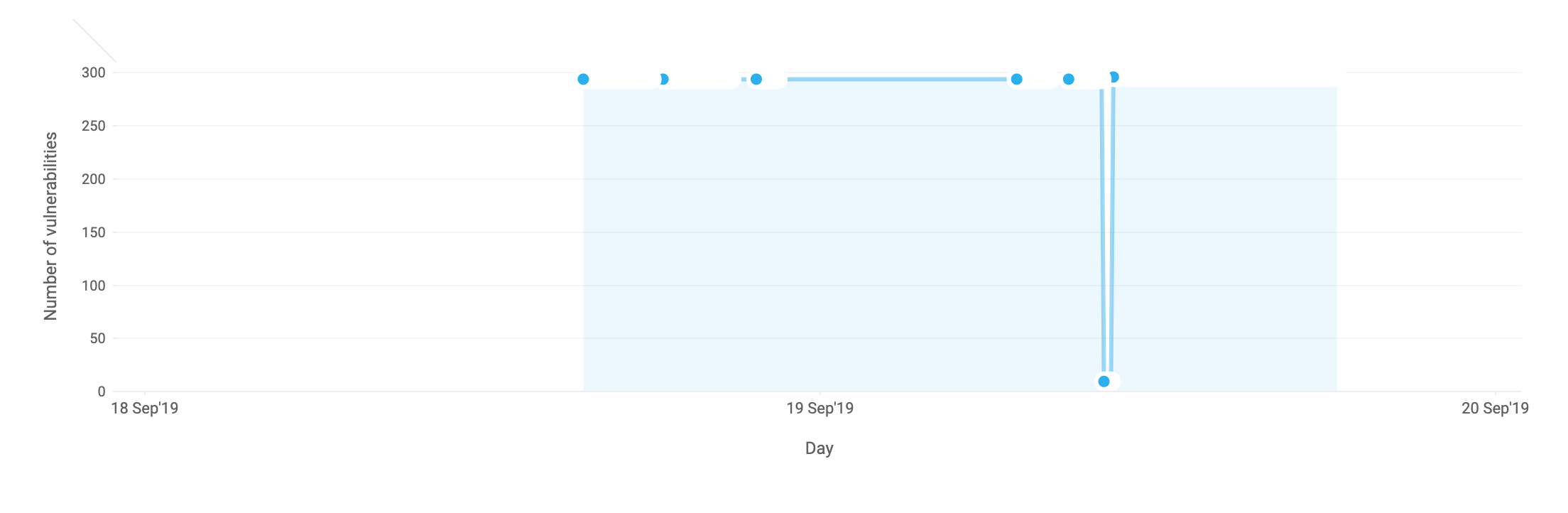
Think of vulnerabilities like holes in a ship. Individually, these holes might not pose a big issue, but eventually their combined effects may end up sinking your entire organization. A quick glance at the vulnerability trend can give you an idea of how well your vulnerability management efforts are paying off. Track your vulnerability assessment progress and stay on top of vulnerabilities. How secure would you feel if you could just bring the number of vulnerabilities close to, if not to, zero?
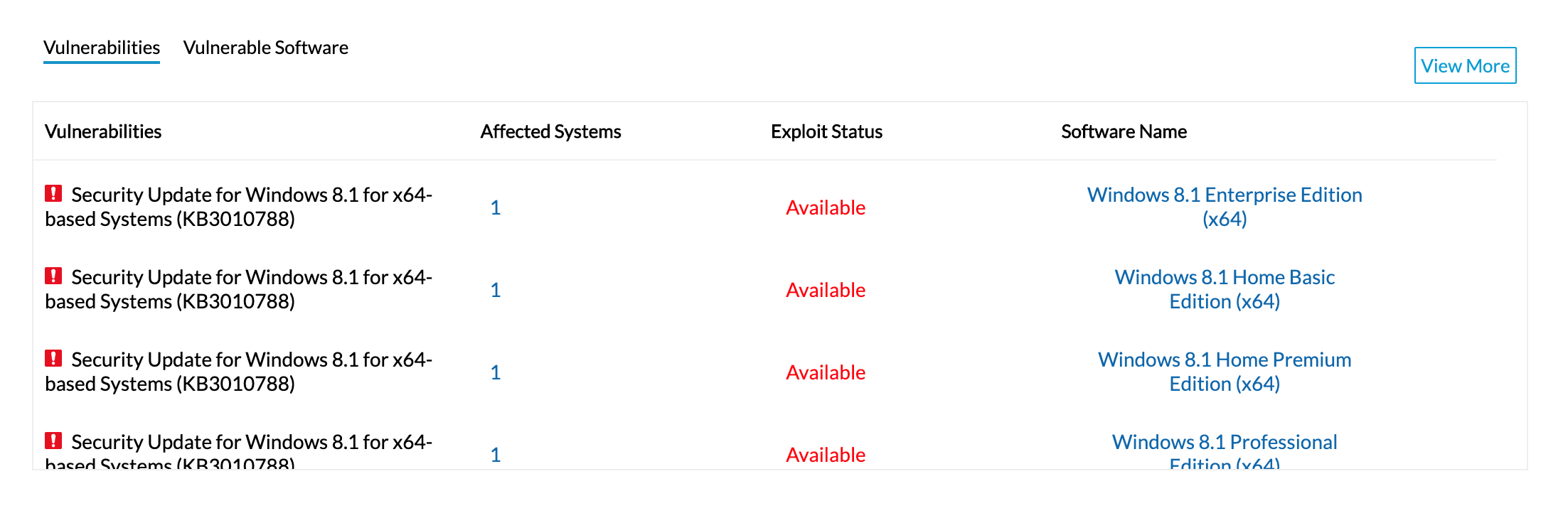
Vulnerability Manager Plus automatically curates a list of vulnerabilities that are on the verge of exploitation. This list takes various risk factors into account, such as how easily exploitable a vulnerability is, its severity, age, and patch availability. This table helps you ensure that you haven't left out any essentials in your vulnerability assessment process.
With the built-in patching functionality automatically correlating patches with corresponding vulnerabilities, you can deliver instant remediation to all affected machines directly. Not only can you decide when patching should begin and end, but you can also customize every aspect of your patching process using flexible deployment policies. Affected target systems are automatically listed; here, you can add or remove targets as desired. You can also retry patch deployments on failed targets as many times as you want and choose to be notified about the deployment status at a frequency of your choosing.
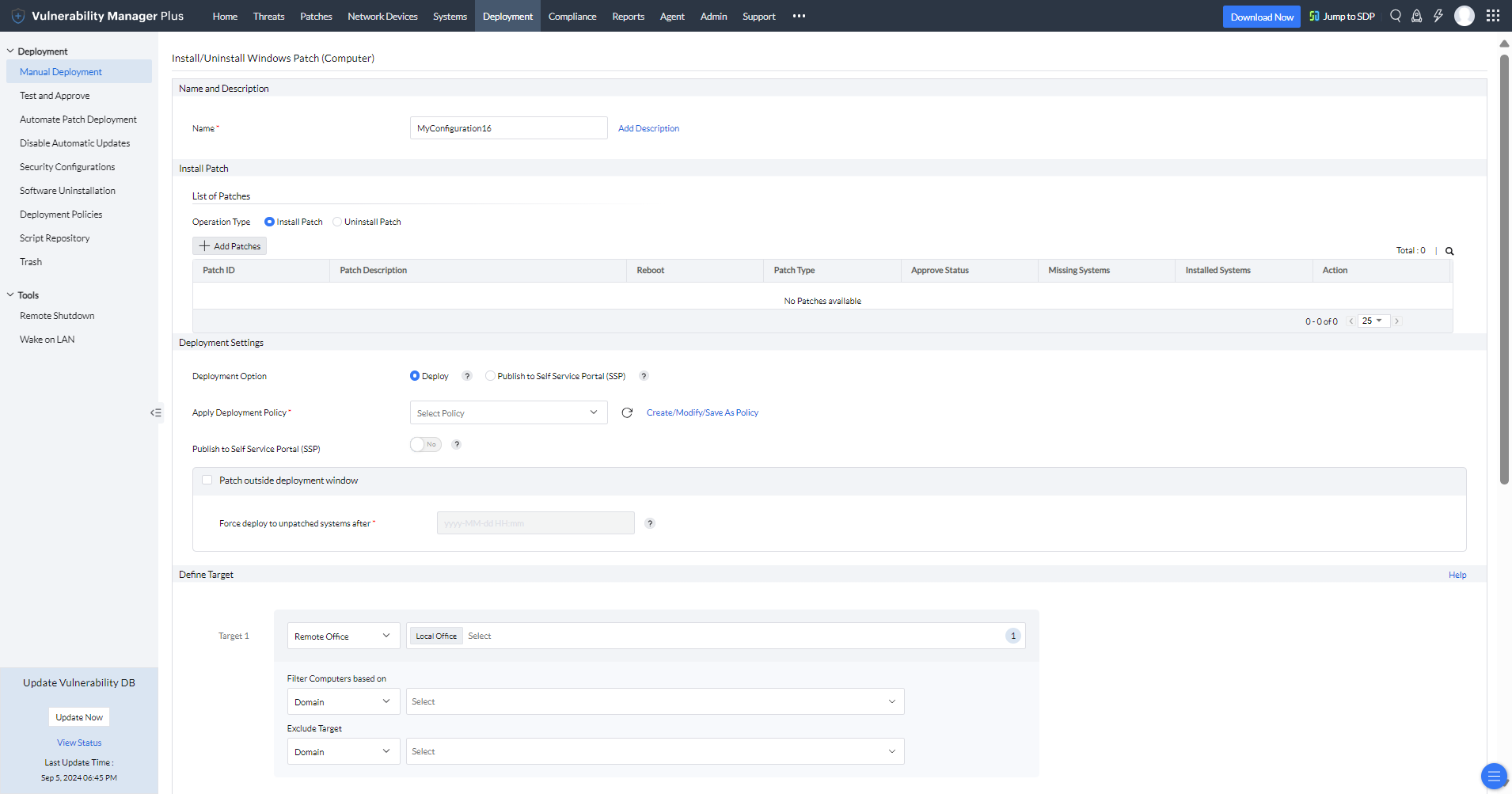
This integrated vulnerability and patch management approach eliminates the need for multiple agents, disparity in data transferred between multiple solutions, potential delays in remediation, unnecessary silos, and false positives. Vulnerability Manager Plus also empowers you with a separate patch management module to completely automate your regular patching schedules, enabling your IT staff to spend more time on assessing and prioritizing high-risk vulnerabilities.
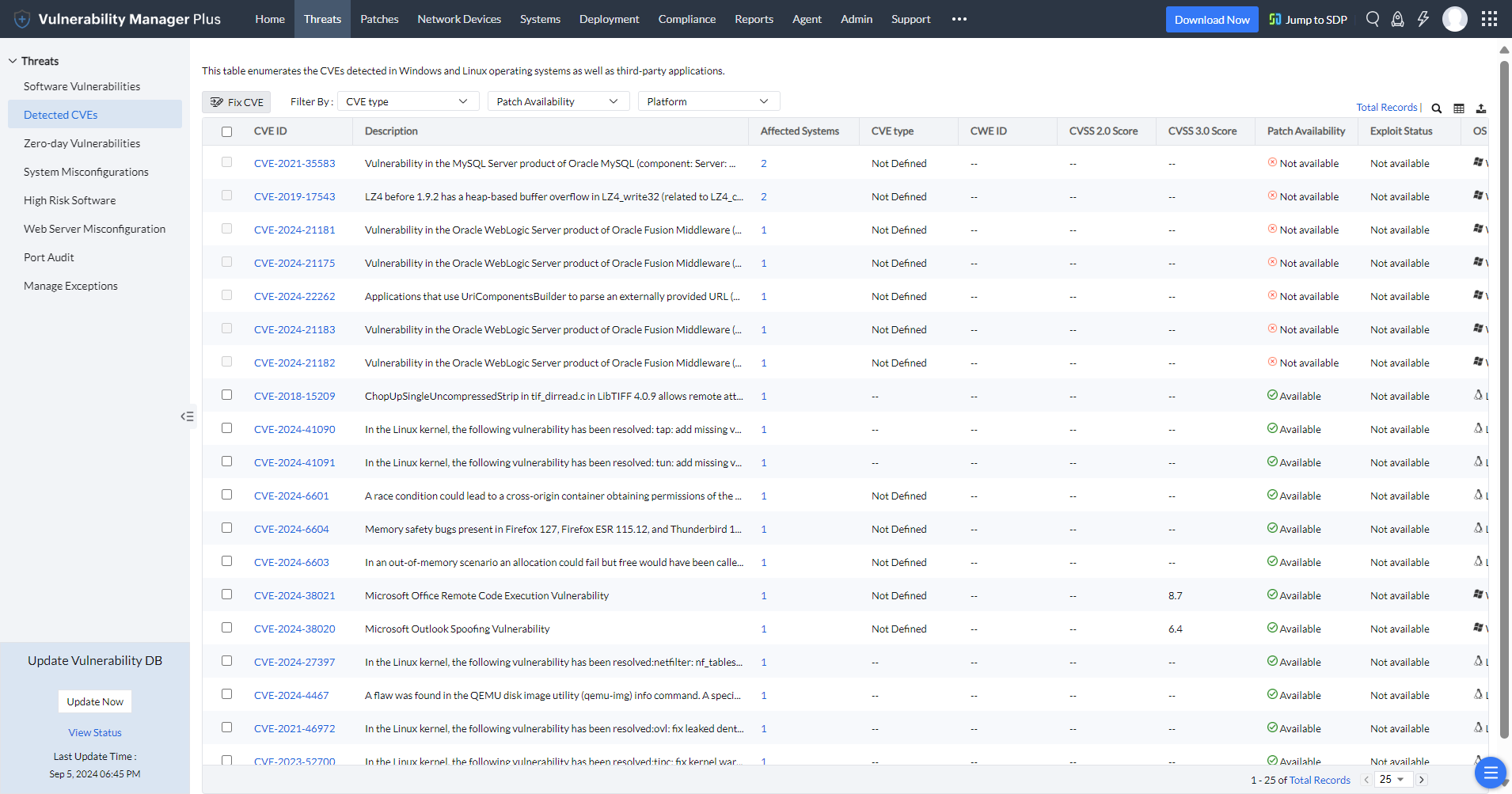
Vulnerability Manager Plus boasts a dedicated Detected CVEs view that lists all the CVEs affecting your network endpoints. All you have to do is select the desired CVEs then click Fix CVE to instantly create a patch deployment task in all the affected machines.
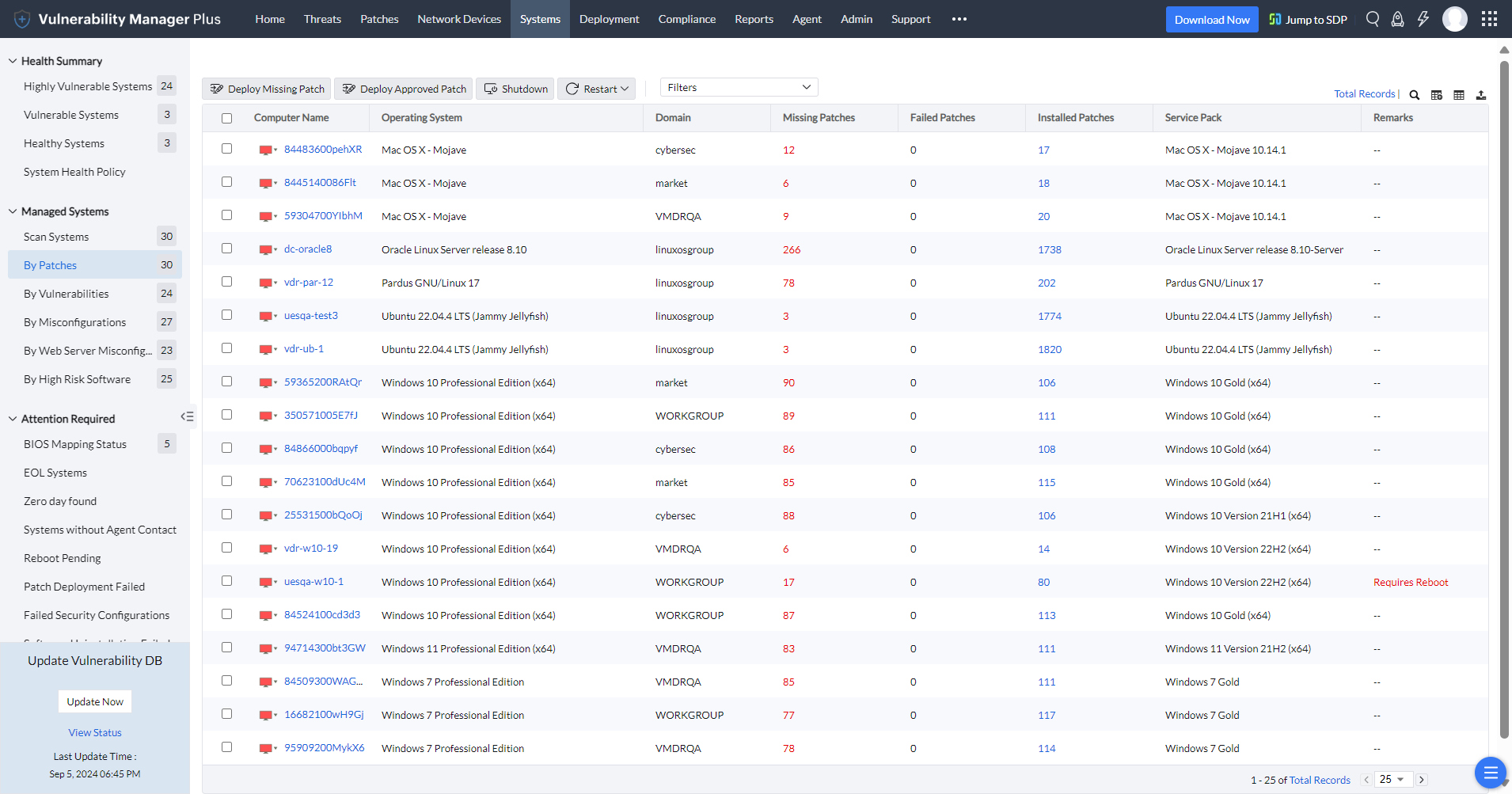
Clicking on a system takes you to a drilled-down view that clusters vulnerabilities of the system into three major categories:
Save yourself from the densely populated club of cybercasualties.
Schedule a demo.Free, 30-day trial.With vulnerabilities growing exponentially, regular vulnerability assessment is crucial to safeguard the network assets. While there are several vulnerability assessment tools available, the challenge lies in prioritizing and streamlining the assessment process.
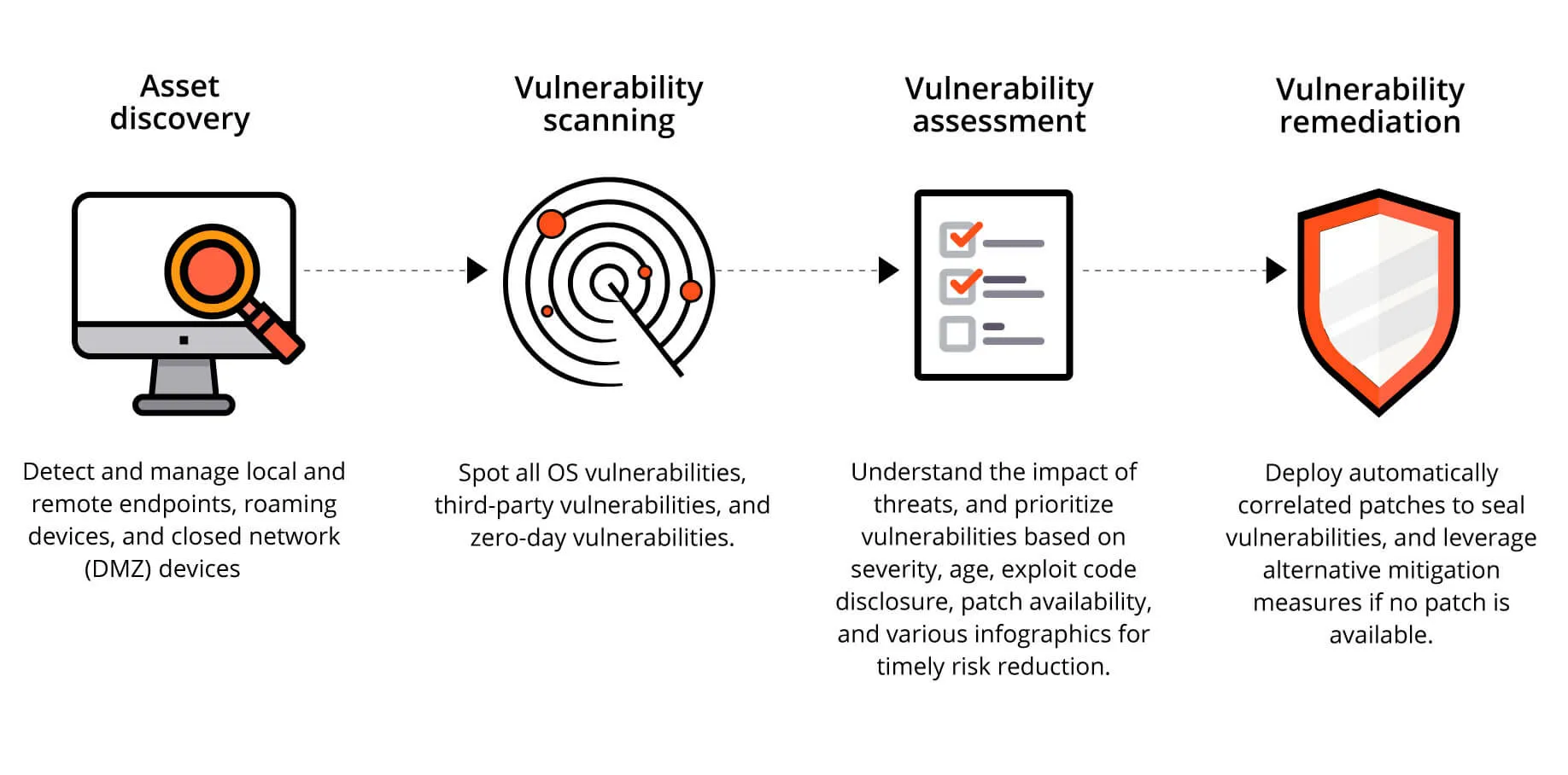
Here are the recommended steps to perform vulnerability assessment in your networks:
Before initiating the vulnerability assessment process, it is important to prioritize and choose the systems that should be scanned. Most organizations today have a BYOD policy that enables users to make use of their personal devices for business purposes. As a result, the number of systems utilizing the network resources also increases drastically. The security teams and admins must prioritize the business-critical systems (such as servers, POS devices, etc.) over others for vulnerability scanning. The other set of systems that are used internally can be further prioritized in the upcoming scanning cycles.
ManageEngine Vulnerability Manager Plus allows admins to prioritize scanning for the required systems by manually choosing them. Furthermore, admins can also initiate scanning for all of the systems at once, right from the console.
Once the systems are scanned and vulnerabilities detected, the next course of action is to prioritize the vulnerabilities for mitigation. As a thumb rule, the vulnerabilities with critical or high severity in business-critical or customer-facing systems should be mitigated first.
The pending set of vulnerabilities with lower severity ratings or systems that are used internally or are not actively connected to the internet can be mitigated in the subsequent cycles.
Upon successfully scanning, detecting, and prioritizing the vulnerabilities in the network, it is imperative to create a vulnerability assessment report. This will provide a holistic overview of the vulnerability status in the network to all the internal teams concerned.
Vulnerability Manager Plus' System Health Reports provide an overview of the network's current health status by listing the systems based on the number and severity of vulnerabilities in them. This ensures a clear visibility of the managed assets and assists in decision-making.
Once the vulnerability assessment report has been created and shared with the concerned internal teams, it is now time to remediate the vulnerabilities. Based on the type, the remediation steps might differ, starting from patch deployment, and registry changes to configuring servers, passwords, and open ports.
Vulnerability Manager Plus is the only vulnerability assessment tool you need to tackle the challenges that crop up during your vulnerability management process. See below for the four common scenarios IT admins often run into while managing vulnerabilities and how ManageEngine's vulnerability assessment tool helps address them:
Vulnerabilities posing unequal risk? Prioritize vulnerabilities by exploitability and impact, and remediate them, across an environment of any size, by deploying the latest patches in no time.
Too many vulnerabilities to patch? With built-in patching, you can automate your regular patching schedules to keep your endpoints up-to-date with security updates and non-security patches, clearing your IT staff's schedule so they can focus on what matters most.
Vulnerability Manager Plus offers a dedicated view to swiftly identify zero-day or publicly disclosed vulnerabilities and apply work-arounds to mitigate the flaw before fixes arrive. It also keeps you abreast of OSs and applications that have or are about to become obsolete, meaning they’ll no longer receive patches from the vendor.
Create custom groups to isolate high-availability servers and exclude less critical vulnerabilities from them to prevent downtime. Utilize the decline patch feature to deny problematic patches for production machines until vendors come up with a revised version of the patches.
To know more about the process of ManageEngine's vulnerability assessment tool, visit here
A vulnerability assessment is the process of identifying, quantifying, and prioritizing security vulnerabilities that have emerged in your enterprise network. The purpose of vulnerability assessment is to help enterprises identify and address vulnerabilities before they can be exploited by attackers.
The rise in vulnerabilities has been extremely high over the recent years. If these security vulnerabilities are not addressed properly, they can be exploited by cybercriminals and this might segue into a cyberattack. Sadly, no security team possess the resources or time to deal with every single vulnerability manually. Hence, a prioritization-focused solution is vital for enterprises to detect and remediate vulnerabilities. This is where a vulnerability assessment tool is required to perform spontaneous vulnerability analysis and this would help you see what's likely to be exploited and what's not, so you can immediately address the critical flaws at once.
Vulnerability assessment tools performs vulnerability scans on endpoints to identify potential security weaknesses. On performing vulnerability analysis, the tool determines the level of risk posed by the vulnerabilities. This helps in prioritizing the vulnerabilities that need to be addressed first.
You can enjoy a 30-day free trial on download of ManageEngine's vulnerability assessment tool. Also it is completely free for organizations with up to 25 devices.
Most vulnerability assessment tools provide common metrics such as severity ratings and Common Vulnerability Scoring System (CVSS) ratings to assess security vulnerabilities. However, to truly understand the risks posed by a vulnerability, you need to look beyond those basic metrics.
You should take the following checklist into consideration while performing a security vulnerability analysis:
If you're trusting your organization’s security to vulnerability assessment tools, make it a rule to see if your current solution helps you meet the above vulnerability assessment checklist.
When it comes to vulnerability assessment and analysis, it is recommended to group them based on their types for faster remediation. That being said, here's a look at the types of vulnerability assessment:
Choosing a vulnerability assessment tool can be a daunting task. But to choose the best vulnerability assessment tool, here are few factors to consider: functionality, scalability, ease of use, integration, and support. ManageEngine Vulnerability Manager Plus meets all these criteria and offers comprehensive vulnerability assessment, user-friendly interface, and a plethora of security features.