Remove Admin Rights
Organizations are well aware of the importance of establishing the principle of least privilege (POLP) in today's security landscape. However, they still remain reluctant to accept it. The hesitation is due to the plethora of complexities that results from this security concept. Striking the right balance between security and productivity becomes crucial, and organizations often need to juggle between multiple external tools to achieve this. ManageEngine Application Control Plus' Endpoint Privilege Management feature ensures that businesses face zero glitches with POLP, as it includes all the required capabilities.
There are two aspects that are key to establishing least privilege:
Fortifying security
This is the removal of unnecessary administrator rights, and maintaining authorized individuals as standard users unless absolutely required.
Maintaining productivity
This is providing an alternate means to allow standard users to execute out of the ordinary tasks without elevating their entire account or compromising admin credentials.
To learn about admin rights before figuring out ways to minimize their presence, head to the common queries section given below.
How to remove local admin rights using Application Control Plus?
In Application Control Plus, the Endpoint Privilege Management feature enables you to centrally remove all admin accounts you deem unnecessary, and elevate only application-specific privileges when required. You are saved from the hassle of using multiple tools to establish POLP. Here is how you can leverage the Remove Admin Rights to eliminate a huge section of your attack surface:
Discover
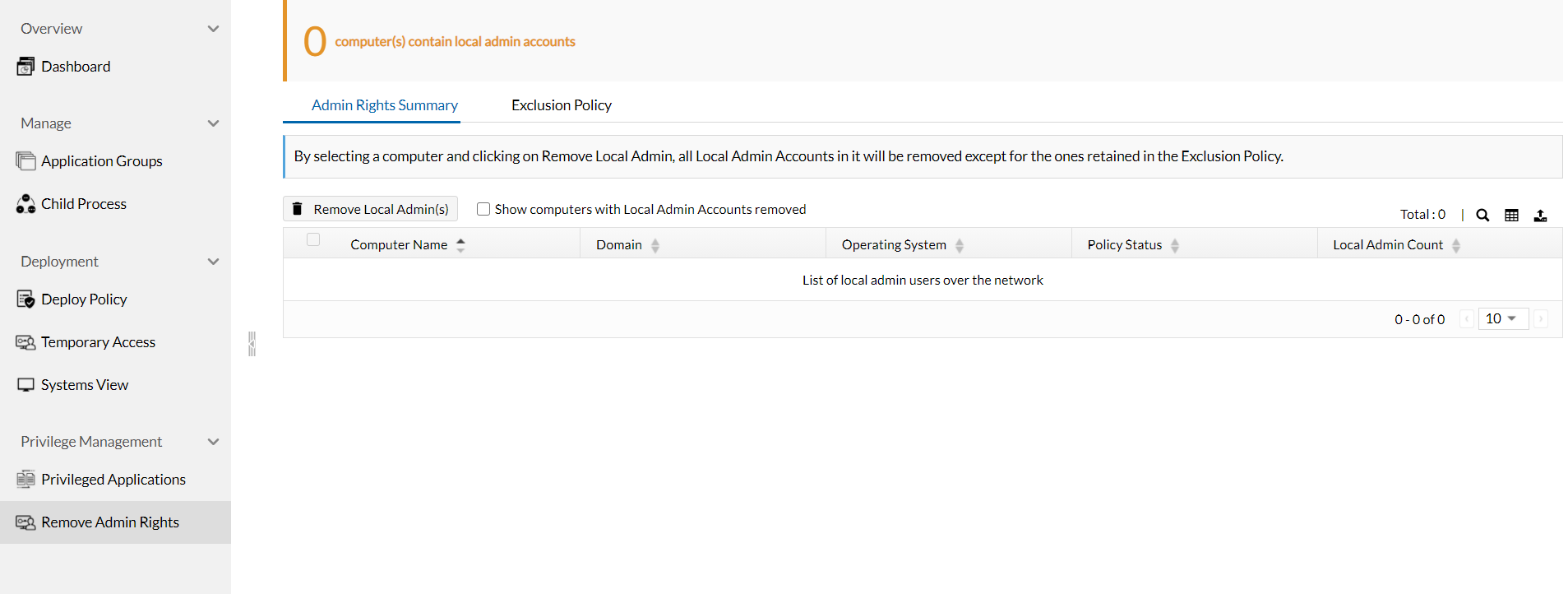
Identifying the gaps in your network is crucial. With a large amounts of endpoints, it is practically impossible for admins to manually track all the local admin accounts created in them. The Admin Rights Summary tab displays the list of local admin accounts that correspond to the discovered computers. Clicking on Count displays details about the accounts.
Analyze
Once we have a detailed account of the distribution of rights, the sysadmin will have to analyze them to qualify them. It is best to keep the rights distributed as minimal as possible.
Remediate
To minimize errors that admins might find during policy deployment, remediation has been split into two parts:
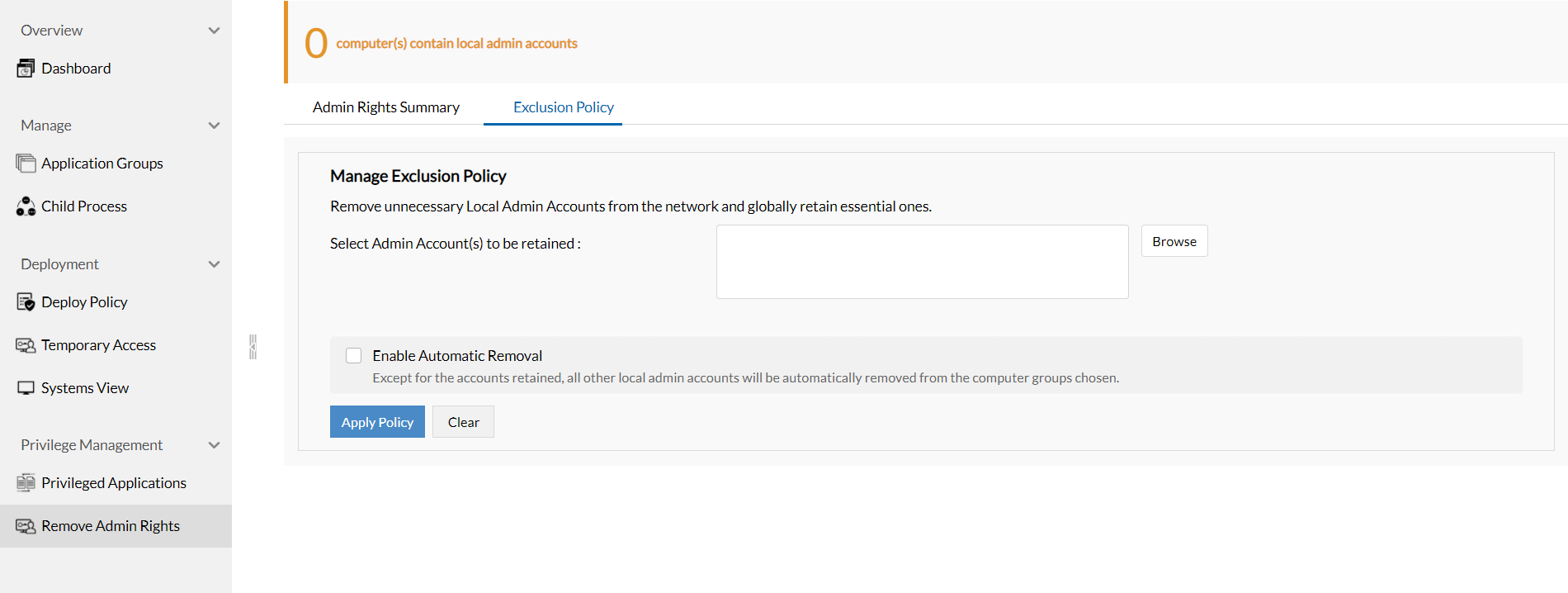
Exclusion Policy
Policies to retain certain admin accounts globally can be created from the Exclusion Policy tab. These admin accounts are retained in all the computers that they are present in. The sysadmin can choose to retain only their account, the built-in administrators account, or any other account depending on their needs.
Remove Local Admins
Once the exclusion policy is finalized, the sysadmin can remove the remaining unnecessary accounts either manually or automatically. Checking the Enable Automatic Removal box will immediately remove all other admin accounts from the computer groups selected.
To manually delete these accounts, return to the Admin Rights Summary tab, select the computers that you wish to modify, and click on the Remove Local Admin(s) button. All local admin accounts in the specified computers will be removed, except for the ones retained using the exclusion policy, if any.
Once all unnecessary local admin accounts are removed, the sysadmin can proceed to create a Privileged Application List. This list can then be associated with custom groups of users devices that will then enable select users to run these applications as administrators, even if they are granted only standard user privileges.
Benefits of removing local admin rights
Managing local admin rights by removing unnecessary accounts from computers might be the best thing for your network's security. Here's why:
- Phishing websites and emails targeting users are plentiful. Users often fall prey to these attacks, and end up accidentally installing viruses on their own devices. By removing local admin privileges, organizations can reduce these malware risks, as standard users do not have the privilege to install most software or malicious programs.
- Attackers who somehow gain access to a machine with a local administrator account can use it as a launching point to move laterally through the domain, making the entire network vulnerable. This can be avoided by eliminating privileged accounts that are not needed.
- Users lower in the hierarchy may lack technical skills and can create havoc in their machine's configurations and settings. Device misconfigurations can affect normal functioning, and also expose them to easily exploitable vulnerabilities. Removing admin rights is an effective way to prevent this.
- Most of the vulnerabilities that arise in applications need administrator level privileges to be exploited. According to a study, running Windows under an account without administrative rights mitigates 98 percent of the critical vulnerabilities affecting the Windows OS.
Other stellar features in this solution include Application Allowlisting, Application Blocklisting, Flexibility Regulator, and Just-in-time Access. These were developed to fulfill your application security needs. Try them all in your free , 30-day trial version of Application Control Plus.
Common Queries
What are local admin accounts?
User accounts in computers can be classified as standard user accounts and local admin user accounts. Local admin accounts enable users to accomplish management activities on their local computers, whereas standard user accounts grant minimal to no management privileges.
Here are a few capabilities that local admin accounts possess:
- Installing and uninstalling any software
- Adding or removing devices like printers
- Creating, deleting or modifying files, folders and other computer settings
- Creating accounts for other users on the computer
What are built-in administrator accounts?
Windows machines come with built-in administrator accounts. They can be used to set up other standard user and local admin accounts initially. These accounts also have privileges similar to the local admin account. However, unlike local admin accounts, they can never be deleted from the machine, only disabled.
