What is a Cloud Snooper?
Cloud Snooper is a sophisticated attack carried out on various Linux and Windows EC2 instances hosted by Amazon Web Services (AWS). It is a complex malware―a rootkit with a remote access Trojan (RAT)―which serves as a backdoor for controlling the compromised machines. The RAT enables attackers to freely communicate with the rootkit and exfiltrate sensitive data to their servers, bypassing firewall settings, thereby impacting data security in AWS. Cloud Snooper is considered unique because not only does it remain inconspicuous, but it can attack both Windows and Linux machines at the same time, demonstrating its multi-platform nature of attack propagation. The rootkit can be used to infect multiple Windows hosts using the infamous Gh0st RAT, which is capable of assuming complete control of Windows devices. It can also communicate with and control compromised machines on any platform, on any OS, behind any firewall boundary, bypassing cloud security controls.
How Cloud Snooper works
The Cloud Snooper rootkit can be installed on a Linux host by a brute-force attack on password-protected Secure Shell (SSH) or by the exploitation of any AWS misconfiguration. The Cloud Snooper rootkit has a component known as a communications handler, which facilitates communication between the malware and the attacker. The handler constantly inspects the HTTP and HTTPS traffic allowed by the firewall. If the source port in the packets is 1010, 2020, 6060, 7070, 8080, or 9999, the handler identifies it as a command from the attackers and redirects it to ports 2080 and 2053. These are the default ports at which the rootkit receives traffic and the rest of the traffic is allowed to pass through ports 80 and 443. In reverse communication, the handler collects data stolen by the malware from ports 2080 and 2053, disrupting data security and privacy. It then rewrites the source ports as 80 or 443, and sends it through the firewall back to the C2 servers of the attackers. So, when the firewalls in a cloud environment are misconfigured to consider only the destination ports to block or allow incoming traffic, attackers can easily leverage this security gap to execute a Cloud Snooper attack to sabotage sensitive data in the AWS cloud.
IoCs of a Cloud Snooper attack
Here are a few indicators of compromise (IoCs) for detecting cloud Snooper in your environment:
| Indicators | Values |
|---|---|
| Open ports on local hosts | 2080, 10443 (TCP); 2053 (UDP). |
| Inbound connections from the remote ports | 1010, 2020, 6060, 7070, 8080, 9999 |
| Domains | cloud.newsofnp.com, ssl.newsofnp.com |
| File names | /tmp/rrtserver-lock /proc/sys/rrootkit /tmp/rrtkernel.ko /usr/bin/snd_floppy |
| Kernel module | snd_floppy |
How to detect and defend against Cloud Snooper attack?
Collecting and analyzing logs from your cloud environment can help you detect these IoCs at an early stage and minimize damage. Cybersecurity solutions such as a security information and event management (SIEM) tool can detect and mitigate these attacks with real-time alerts, automatic remediation workflows, anomaly detection, and more.
ManageEngine Log360 is a SIEM solution that extensively audits cloud platforms like AWS along with firewalls, routers, switches, applications, file servers, web servers and much more, giving you complete visibility into both cloud and on-premises. It can help you detect and defend a Cloud Snooper attack in the following ways:
- SSH brute forcing is one way by which attackers can compromise Linux hosts to install the Cloud Snooper rootkit. Monitoring AWS Linux instances for multiple failed logons in an unusually short period can help you detect a potential brute-force attack. Figure 1 shows a detailed report on recent logon failure activities in AWS in Log360.
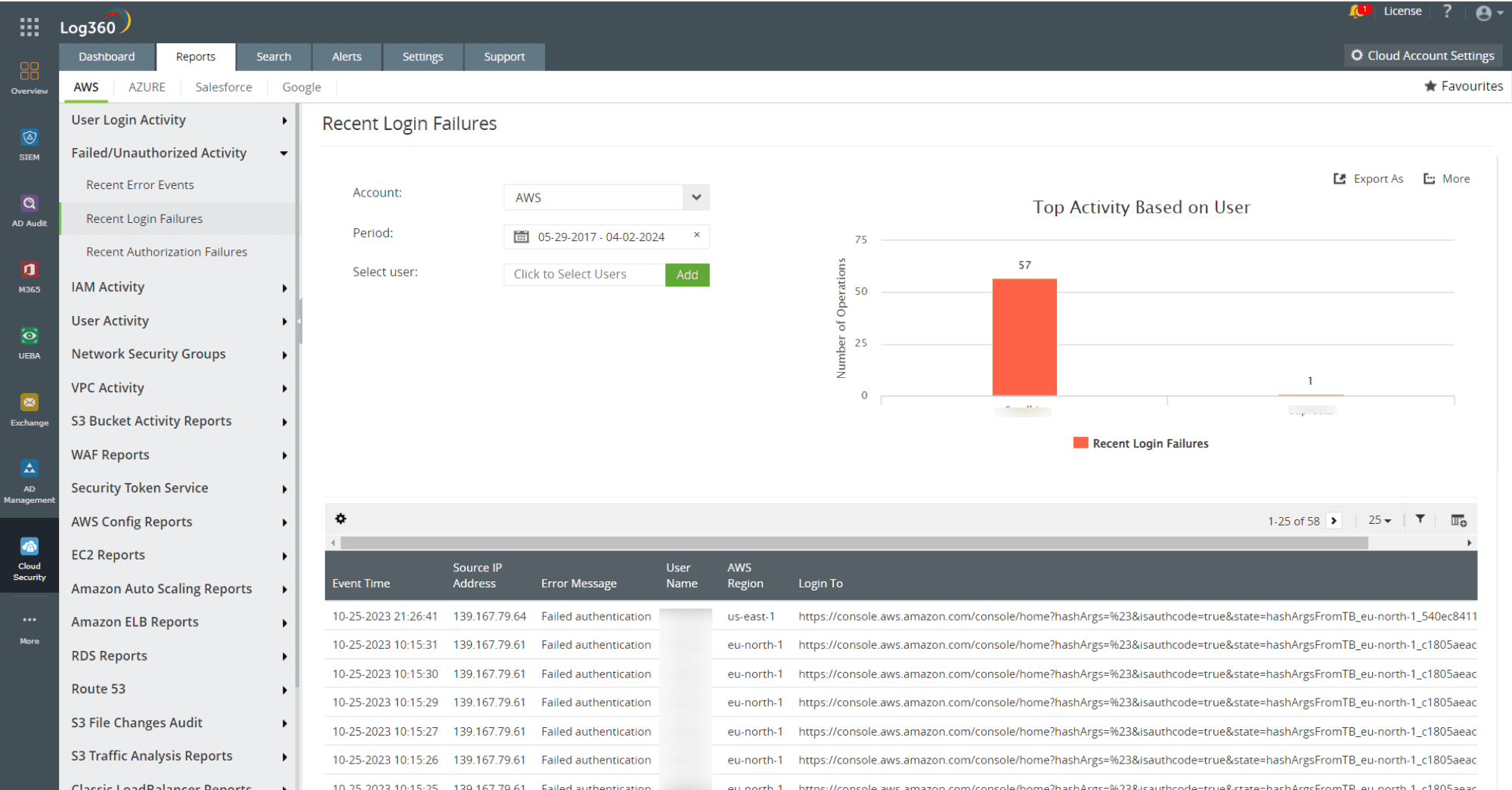
Figure 1: AWS login failure report in Log360
- The RAT in the Cloud Snooper rootkit creates a communication channel between the compromised host and the C2 server by misconfiguring the firewall to allow traffic from unintended ports. Tracking firewall configuration changes and allowed traffic settings can help you identify Cloud Snooper malware intrusion in your network. Figure 2 depicts the firewall denied traffic report in Log360 that can help you identify the IoCs of a Cloud Snooper attack like the malicious IP address, source port, and destination port.
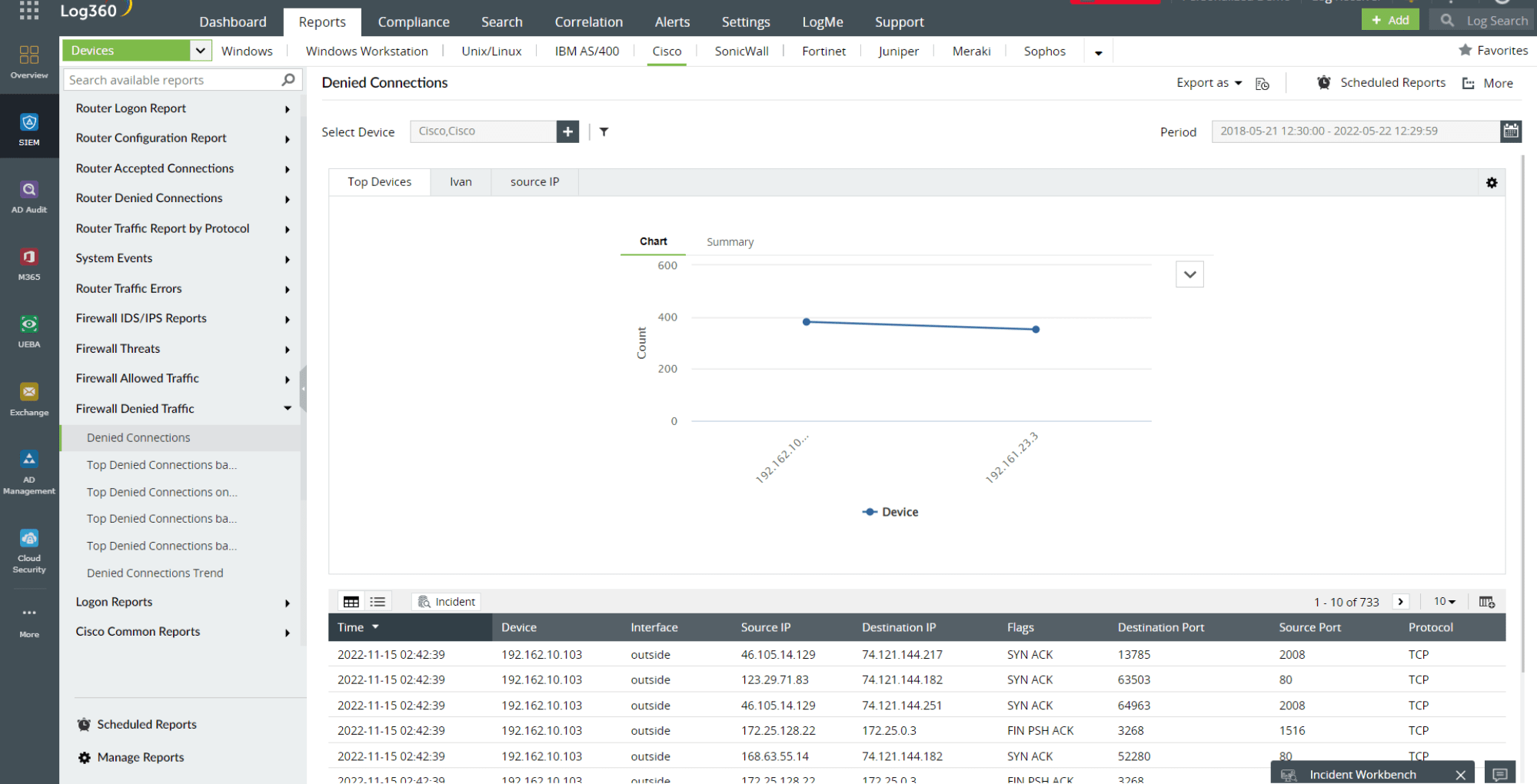
Figure 2: Firewall denied traffic report in Log360
- You can also leverage Log360's capabilities such as custom correlation, real-time alerting and incident workflows to identify the IoCs of Cloud Snooper attack, and prevent the attack from propagating further into the network. Figure 3 shows a custom correlation rule for detecting a Cloud Snooper attack in Log360.
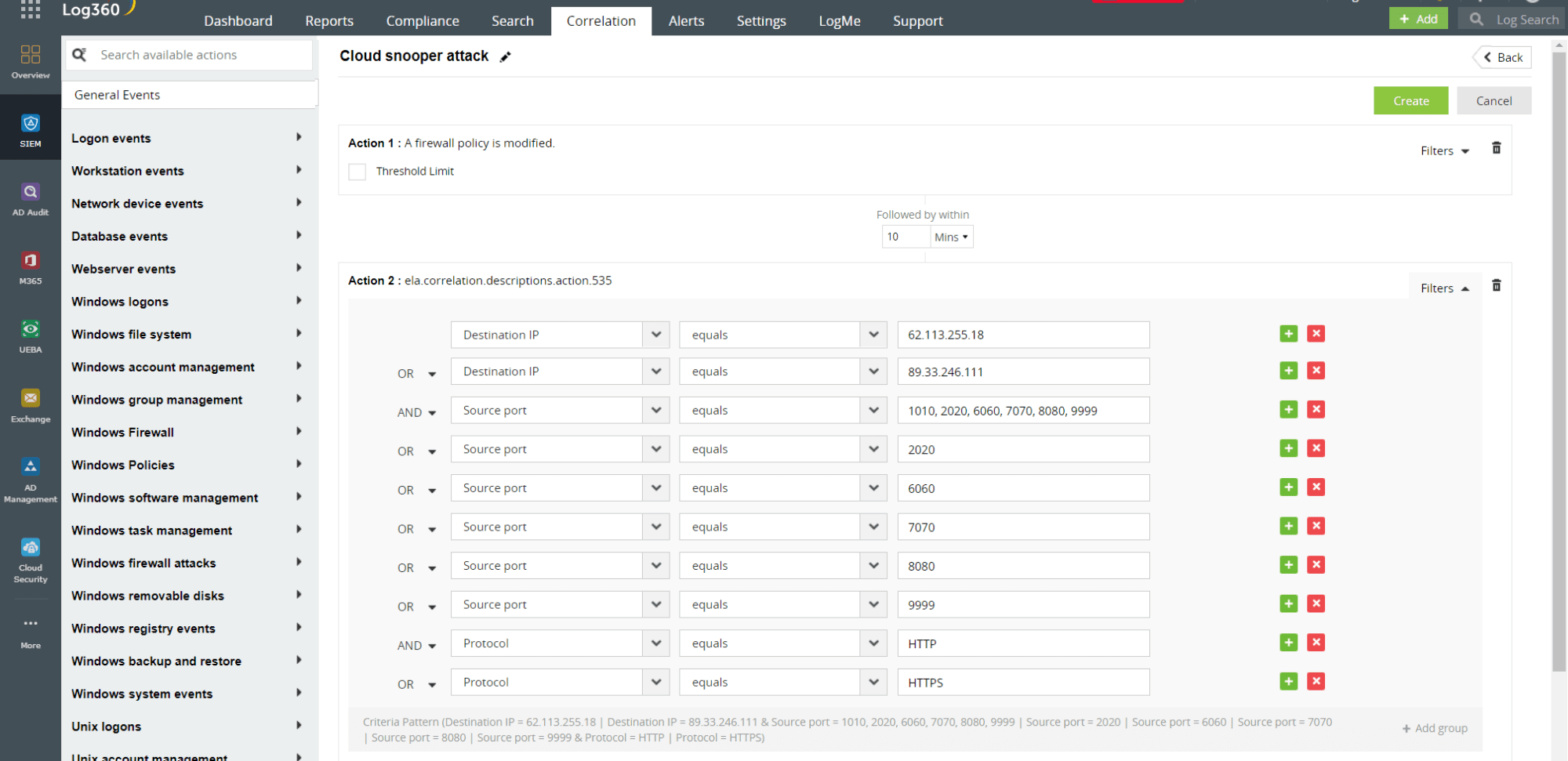
Figure 3: Custom correlation rule for Cloud Snooper attack in Log360
Log360 also offers a threat intelligence platform that brings in dynamic threat feeds for cloud security monitoring and an incident management module that helps prioritize and resolve security incidents. To learn more about Log360, sign up for a personalized demo or take advantage of the fully functional, free 30-day trial to explore it yourself.



