What is SharpUp?
SharpUp is a C# port of various PowerUp functionalities. It is essentially a tool created for security professionals, specifically those working in the area of cybersecurity and penetration testing. Its primary purpose is to help identify weaknesses or vulnerabilities within Windows operating systems. These weaknesses and vulnerabilities could potentially be exploited by someone with malicious intent to gain unauthorized access or higher levels of control over a system.
When you run SharpUp on a Windows system, it acts like a detective, looking for any loopholes or security gaps. These gaps might include outdated software, misconfigured permissions, or other oversights in the system setup that could allow an attacker to elevate their access rights — from a regular user to the privileges of an administrator.
In what way is SharpUp a hacktool?
The primary function of SharpUp is to look for weaknesses and vulnerabilities within your network to fix them and enhance your defenses. However, the same tool in the wrong hands can be used to exploit these vulnerabilities to gain unauthorized access to the network.
- Exploitation of vulnerabilities:
The tool can identify and take advantage of security weaknesses in a system to carry out unauthorized actions, such as gaining access to confidential data, installing malware, or creating a backdoor for future access
- Privilege escalation:
The tool allows users to gain higher-level privileges on a system without authorization upon finding the vulnerabilities in the network. This helps the threat actor gain higher privileges—say from a regular user to an administrator role—to gain full control over the system.
Attack Summary
- Environment: Windows-based network environment
- Vulnerability exploited: Misconfigured service permissions and outdated software vulnerabilities.
- Objective: To escalate privileges from a standard user account to an administrative level.
- MITRE ATT&CK phase: Privilege Escalation (Tactic ID: TA0004)
How is SharpUp used for privilege escalation
SharpUp scans for various misconfigurations and weaknesses that could be exploited for privilege escalation, such as:
- Unnecessary local administrative privileges for user accounts.
- Weak service account passwords.
- Misconfigured file and folder permissions.
These weaknesses are then exploited to gain higher privileges.
Here’s what a privilege escalation attack using SharpUp may look like.
1. Initial compromise
The attacker first needs access to the target system. This could be achieved through various methods, such as phishing, exploiting a known vulnerability, or using compromised credentials. The goal at this stage is to gain a foothold on the system with any level of user access.
2. Reconnaissance
With initial access secured, the attacker then proceeds to gather information about the system and its environment. This could involve manual commands to check system settings and configurations or using other reconnaissance tools to map out the network. However, the use of SharpUp specifically for privilege escalation comes in at a later stage.
3. Deployment of SharpUp
Once the attacker has a basic understanding of the system, they will deploy SharpUp to the compromised system. This could be done by transferring the SharpUp executable to the system via various methods, such as file sharing, email attachments, or utilizing existing vulnerabilities to download the tool directly to the system.
4. Execution of SharpUp
SharpUp is then executed on the system. It will look something like this:
.\SharpUp.exe .\SharpUp.exe audit will run all vulnerability checks, regardless of their integrity level or group membership. .\SharpUp.exe [check] invokes the individual vulnerability check that is to be run. It can be one of the following:
- AlwaysInstallElevated
- CachedGPPPassword
- DomainGPPPassword
- HijackablePaths
- McAfeeSitelistFiles
- ModifiableScheduledTask
- ModifiableServiceBinaries
- ModifiableServiceRegistryKeys
- ModifiableServices
- ProcessDLLHijack
- RegistryAutoLogons
- RegistryAutoruns
- TokenPrivileges
- UnattendedInstallFiles
- UnquotedServicePath
It would look something like this: .\SharpUp.exe HijackablePaths
Being a tool designed for checking various known privilege escalation vectors on Windows systems, SharpUp scans for common misconfigurations, vulnerabilities, or other weaknesses that can be exploited to gain higher privileges. This step is crucial as it helps the attacker identify the easiest and most effective way to escalate their privileges on the target system.
5. Exploiting identified vulnerabilities
Based on the vulnerabilities or misconfigurations identified by SharpUp, the attacker selects the most promising ones to exploit. This could involve taking advantage of misconfigured service permissions, exploiting known vulnerabilities in outdated software, or leveraging weak registry permissions. The specific exploit used will depend on what SharpUp uncovers during its scan.
6. Privilege escalation
Successful exploitation of the identified vulnerabilities allows the attacker to escalate their privileges. With elevated privileges, the attacker can perform a wide range of malicious activities—from installing backdoors for persistent access, exfiltrating sensitive data, deploying malware or ransomware, to moving laterally within the network—to compromise additional systems.
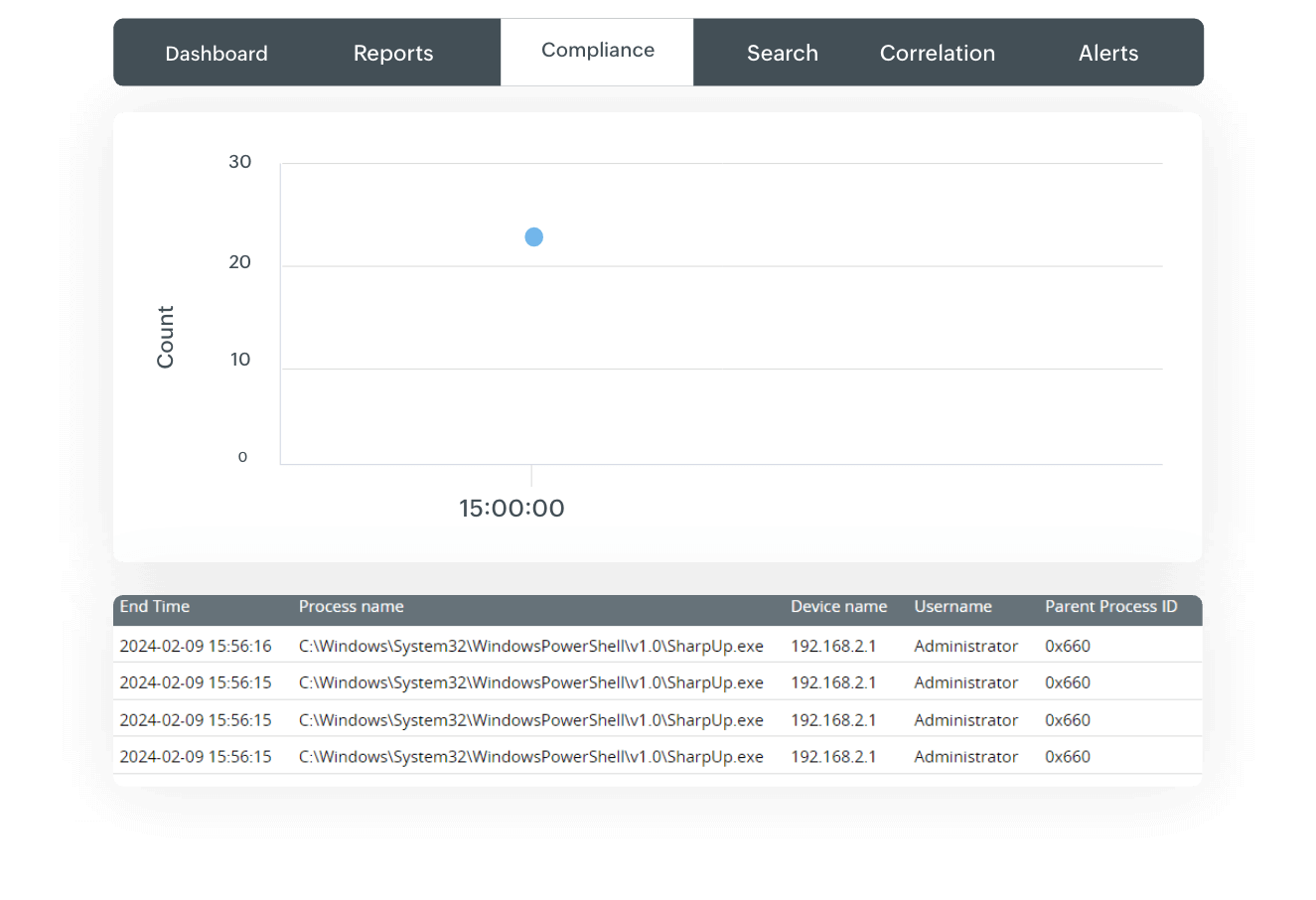
How Log360 helps in SharpUp hacktool detection
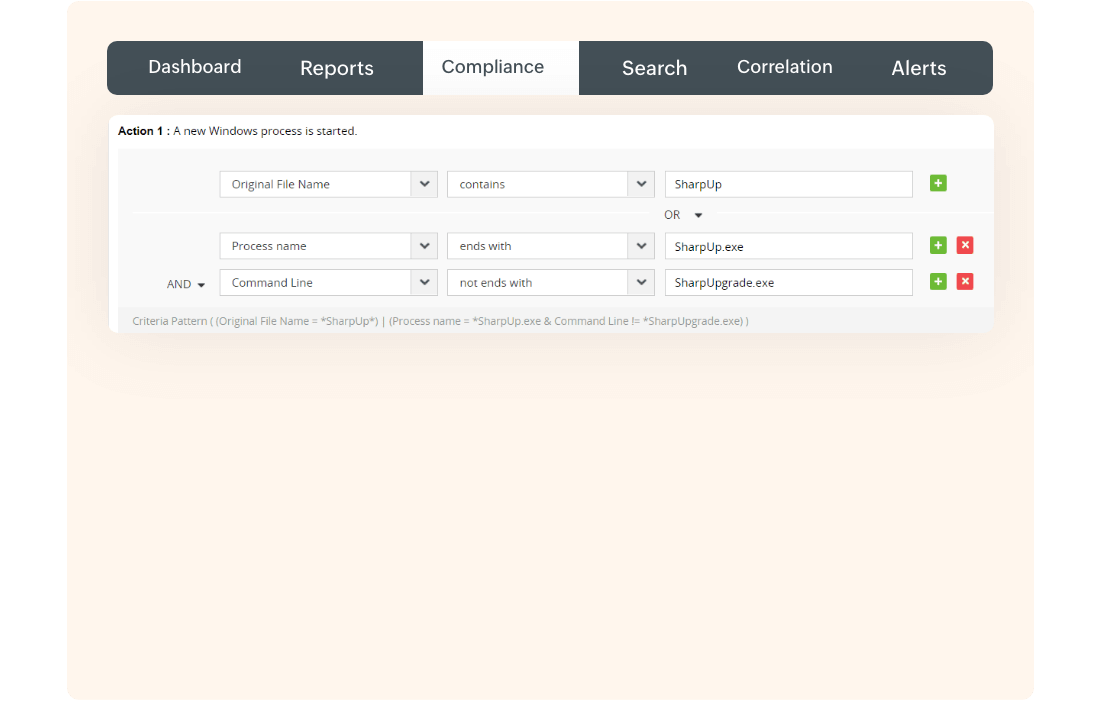
Log360 provides predefined correlation rules to detect the exploitation of any privilege escalation tools like SharpUp.
The SharpUp detection rule consists of certain criteria, such as if the original file name contains “SharpUp”, or if the process name ends with “SharpUp.exe” and the command line note does not end with “SharpUpgrade.exe”.
When an alert profile is created with this correlation rule, the solution will alert you whenever a privilege escalation attempt is underway using SharpUp.
What's next?
Detect privilege escalation attempts using SharpUp and other post-exploitation tools with Log360.
- What is SharpUp?
- In what way is SharpUp a hacktool?
- How is SharpUp used for privilege escalation
- How Log360 helps in SharpUp hacktool detection