Endpoint Central's Device Control provides a robust layer of security by restricting the execution of unauthorized Devices. This document delves into the specifications of the agent processes and the core mechanisms behind Device Control, helping you understand how it safeguards your endpoints.
| Agent Process | Running Device Name | Digital Signature Name | Bandwidth Consumption (~) | CPU Consumption (~) | Memory Consumption (~) |
|---|---|---|---|---|---|
| Device Control Service | uesAgentService.exe | ZOHO Corporation Private Limited | N.A | 0 - 0.5% | 1 MB |
| Device Control Policy Processing | dcconfig.exe | ZOHO Corporation Private Limited | 5 KB | 0 - 1% | 6 MB |
| Device Audit | uesDevCtrlSummary.exe | ZOHO Corporation Private Limited | N.A. | 0-3% | 6 MB |
| File Audit Data Populator | uesFaDataPopulator.exe | ZOHO Corporation Private Limited | N.A. | 5-10% | 12 MB |
| File Shadow | uesFileShadow.exe | ZOHO Corporation Private Limited | N.A. | 0-1.4% | 1-1.5 MB |
| Component Upgrade | dcconfig.exe | ZOHO Corporation Private Limited | 7.5 MB | 0-1% | 1 MB |
| File Audit | uesFauser.exe | ZOHO Corporation Private Limited | N.A. | 0-1% | 2 MB |
After agent installation, a one-time scan is initiated. It identifies and gathers details about all connected devices. Once completed, the collected data is made available in the web console.
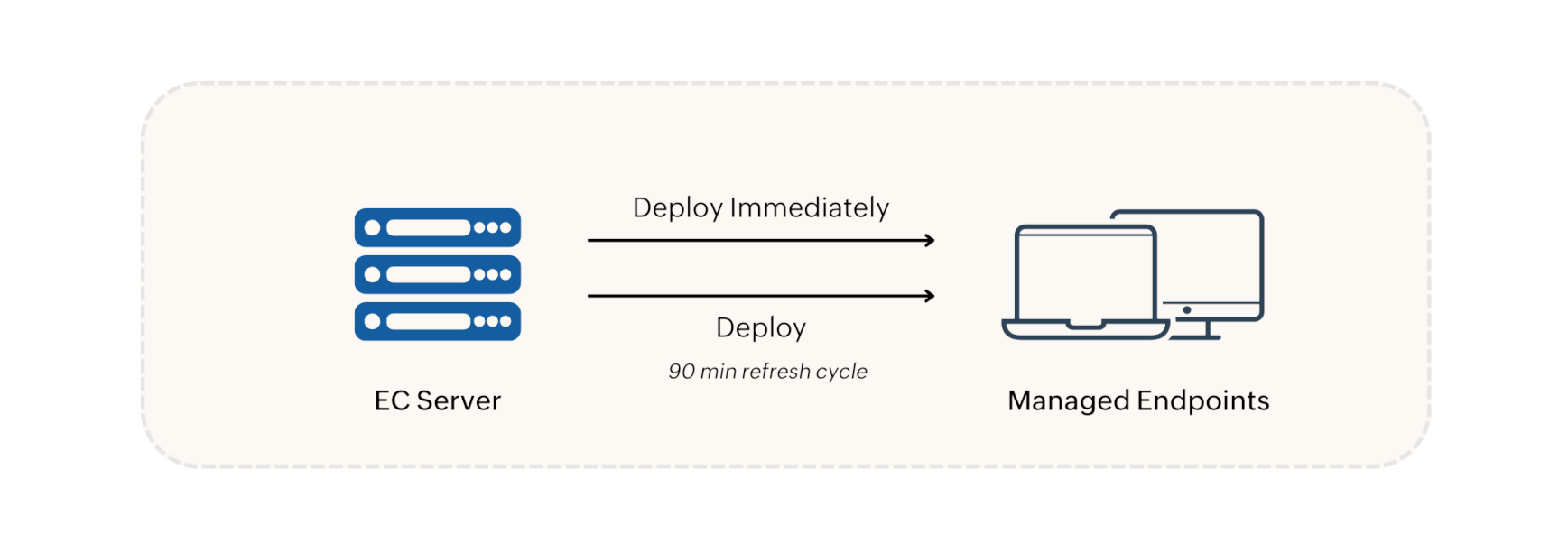
When an Device Control policy is created, it is deployed in the following two options:
Policy modifications, deletions, group changes, and unmanaged Device updates are synchronized with agent machines during refresh cycles. In environments with a Distribution Server, policies and configurations are replicated to the Distribution Server and then synchronized with agent machines during the 90-minute refresh cycle.
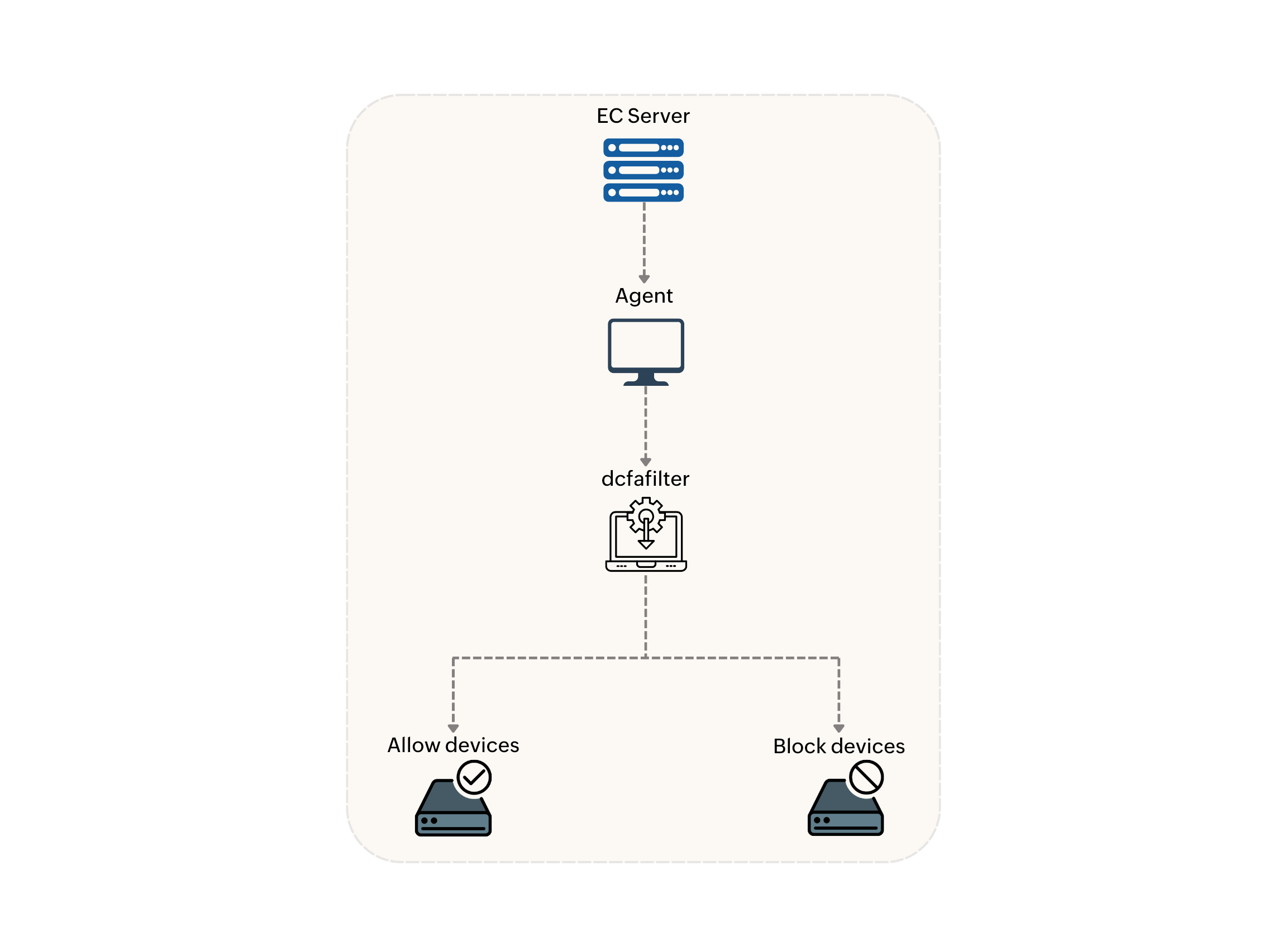
The Device Control policy will be received by the agent and enforced by the kernel mode driver named dcfafilter. This driver monitors device connections and ensures that only authorized devices can be accessed according to the deployed policy. Audited and blocked device events will be posted in the 90-minute refresh cycle.
When conflicting policies are applied to the same target group, The following is the order of precedence:
Note: Once a Device Control policy is successfully applied, any configurations made through Secure USB will be disabled on the machines. Removing the Device Control policy will not reinstate the previously configured Secure USB settings.
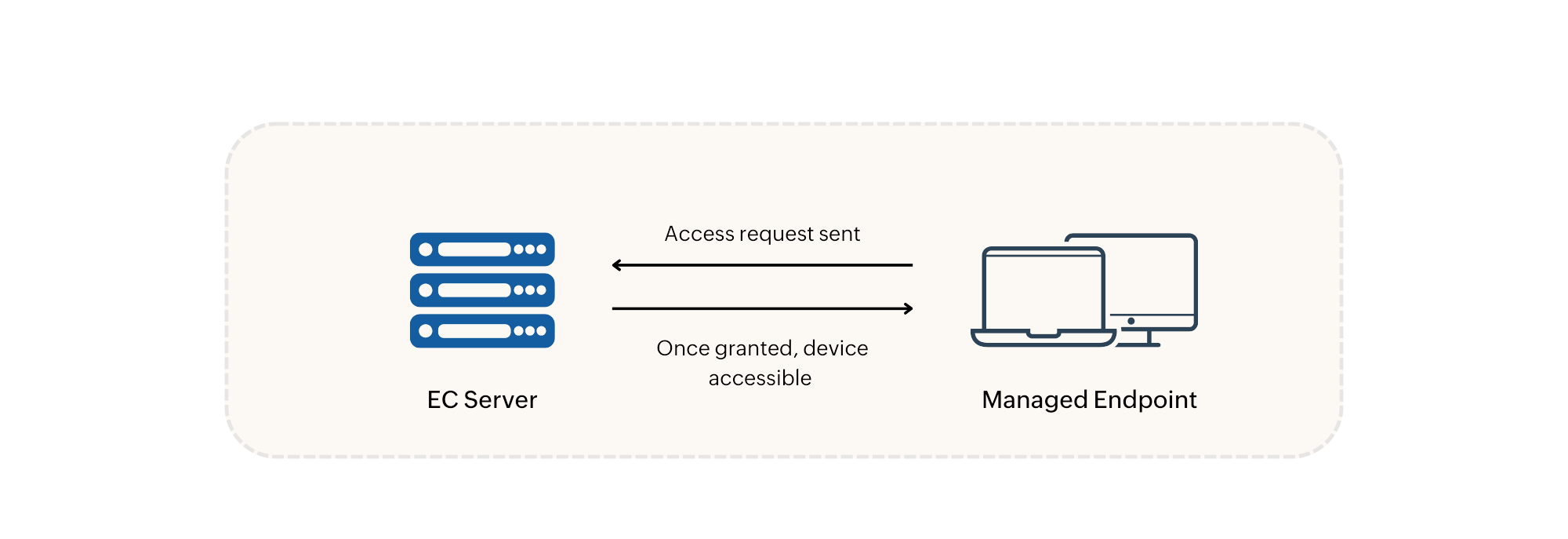
When a user requests access to an untrusted Device, a request is immediately sent to the server for administrator approval. Once approved, the device will be accessible to the user immediately.