

Endpoint Central regularly scans your network for vulnerabilities. Once vulnerabilities are detected, they are displayed in the web console. New vulnerabilities are being discovered constantly, therefore, it might get overwhelming to decide on which vulnerability to remediate first. Therefore vulnerabilities should be assessed and prioritized based on the risk it presents to your enterprise.
Applies to:
Endpoint Central helps you assess the risk posed by vulnerabilities and priortize them with the help of following parameters:
Vulnerabilities are classified into four severity levels ranging from low to critical based on its impact and exploitability.
Critical: Vulnerabilities in the this range are easily exploitable and can result in root-level compromise of servers, remote code execution, information disclosure, etc. These vulnerabilities inflict great damage to the organization, therefore should be prioritized and remediated first.
Important: Vulnerability that falls under this range are quite difficult to exploit but exploitation of them could result in significant data loss or downtime. Therefore, these vulnerabilities should be remediated once all the critical vulnerabilities are removed from your systems and servers.
Moderate: Vulnerabilities in the medium range requires social engineering, or an access to the local network to be exploited. Even when exploited, these vulnerabilities have very limited access and, to the maximum extent, can cause Denial-of-service (DoS).
Low: Vulnerabilities in the low range typically have tiny or no impact on an organization's business and may require local or physical system access to be exploited.
This parameter displays whether an exploit code is available for the vulnerability or not. Vulnerabilities for which the exploit code have been disclosed are at a high-risk of being exploited. Exploit-code-available vulnerabilities with critical severity levels must be prioritized and eliminated at first.
Endpoint Central lets you calculate the age of a vulnerability either from the date on which the vulnerability is published or from the date on which it is discovered in your network. Letting a vulnerability reside in your network for a longer time is an indication of weak security. Therefore, vulnerability age must be taken into consideration while prioritizing vulnerabilities.
You can also prioritize the vulnerability based on the availability of the patches. If a patch is available to mitigate the vulnerability, give priority to that vulnerability first and remediate it.
If the detected vulnerability is a zero-day, give top priority to it ahead of other vulnerabilities.
CVSS scores of vulnerabilities range from 0 to 10, with higher scores indicating greater severity of that vulnerability. Critical vulnerabilities (with CVSS scores above 9) should be given immediate attention, while low-severity vulnerabilities (with scores below 4) may not require urgent remediation.
To prioritize and remediate vulnerabilities based on severity, exploit status, patch availability and CVSS Scores:
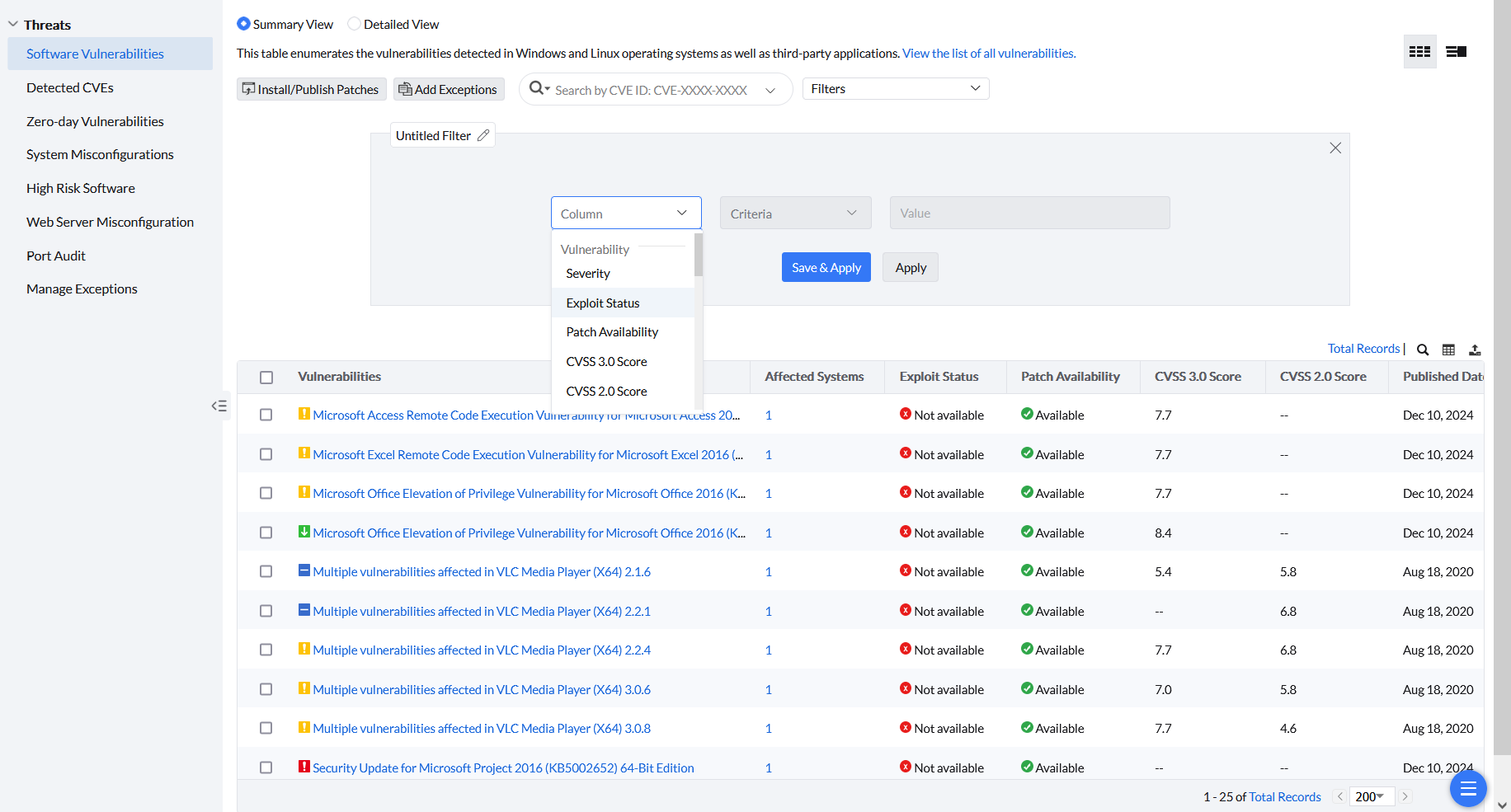
Click on Threats → Software Vulnerabilities.
By default, all the vulnerabilities present in your network will be displayed here. Click on Filters. You can filter vulnerabilities based on the severity, exploit status, patch availability and CVSS Scores and remediate them.
To filter specific vulnerabilities:
Click on Threats → Software Vulnerabilities.
In the Search by CVE ID field, specify the CVE IDs of the vulnerabilities you want to fix.
Now select the specific vulnerabilities and remediate them.
To prioritize vulnerabilities based on Vulnerability age and severity:
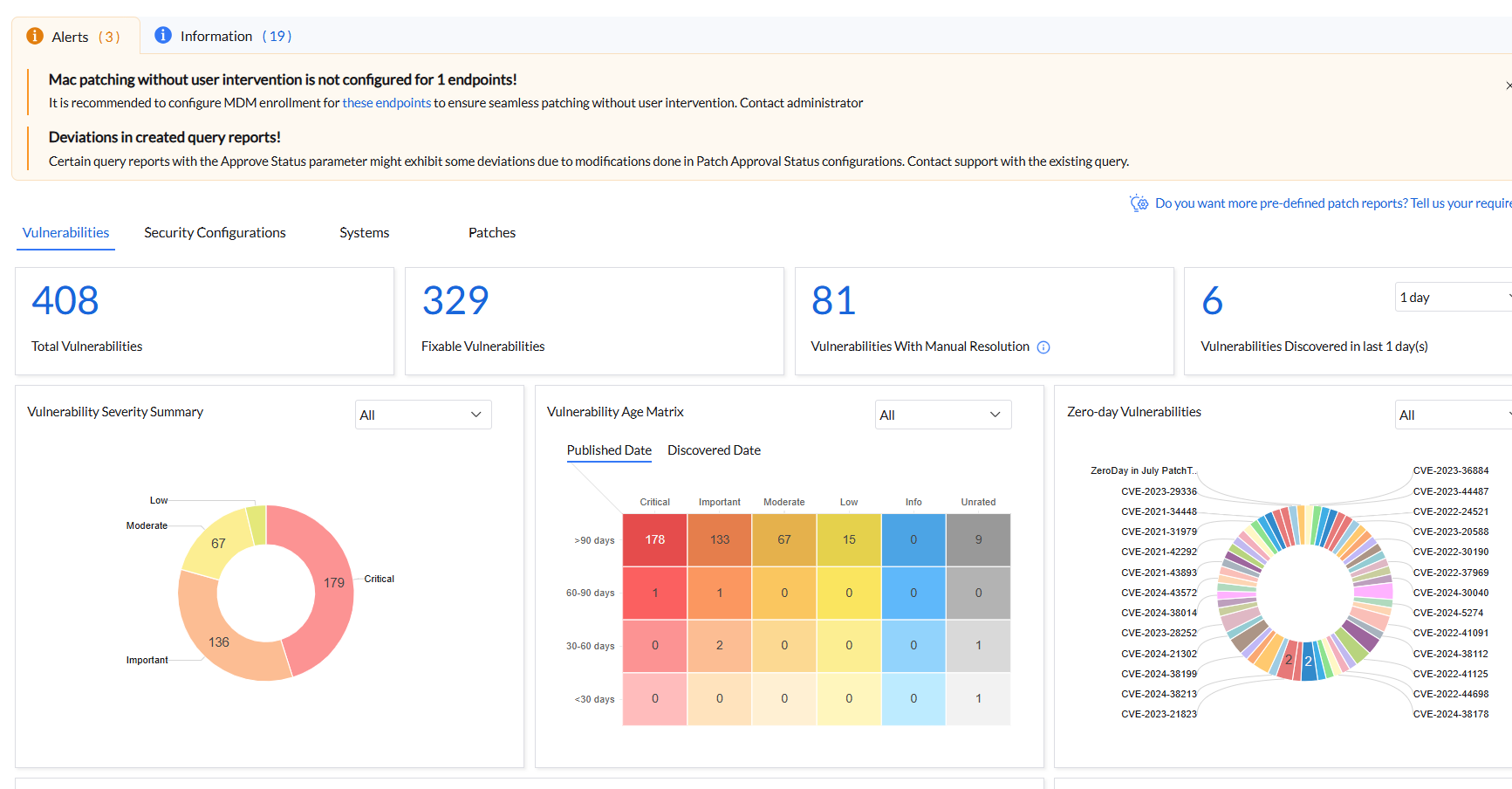
Click on Dashboard → Vulnerabilities → Vulnerability Age Matrix.
Vulnerability age matrix groups vulnerabilities based on both severity and age. You can choose to view the age of vulnerabilities either from published date or discovered date. Click on the age and severity level based on your priority to view a list of vulnerabilities that belong to that category.
Now select the vulnerabilities which you want to fix and remediate them.
Note: You can filter vulnerabilities based on
1. Vulnerability: Severity, Exploit Status, Patch Availability, CVSS 3.0 Score, CVSS 2.0 Score, CVE ID, Published Date, Discovered Date, Vulnerability Name, Operating System and Application
2. Computer: Computer Name, Platform, Domain Name, Branch Office, Custom Group, Operating System, Language and Agent Live Status
Zero-day Vulnerabilities will be listed in a separate section which can be accessed by clicking on Threats → Zero-day Vulnerabilities. To learn more about managing zero-day vulnerabilities, refer to this page.
If you have any further questions, please refer to our Frequently Asked Questions section for more information.