

Endpoint Central lists all the end-of-life, remote desktop sharing and peer-to-peer software present in your managed computers under Threats & Patches → Threats → High Risk Software. It is important to understand the risks associated with these software and inspect the necessity of these software and uninstall them (if they are peer-to-peer or remote desktop sharing softwares) if they are not required for business for any related tasks in your enterprise. If they are critical for your business related tasks and you do not want them to see under this view, you can add them to exceptions.
Applies to:
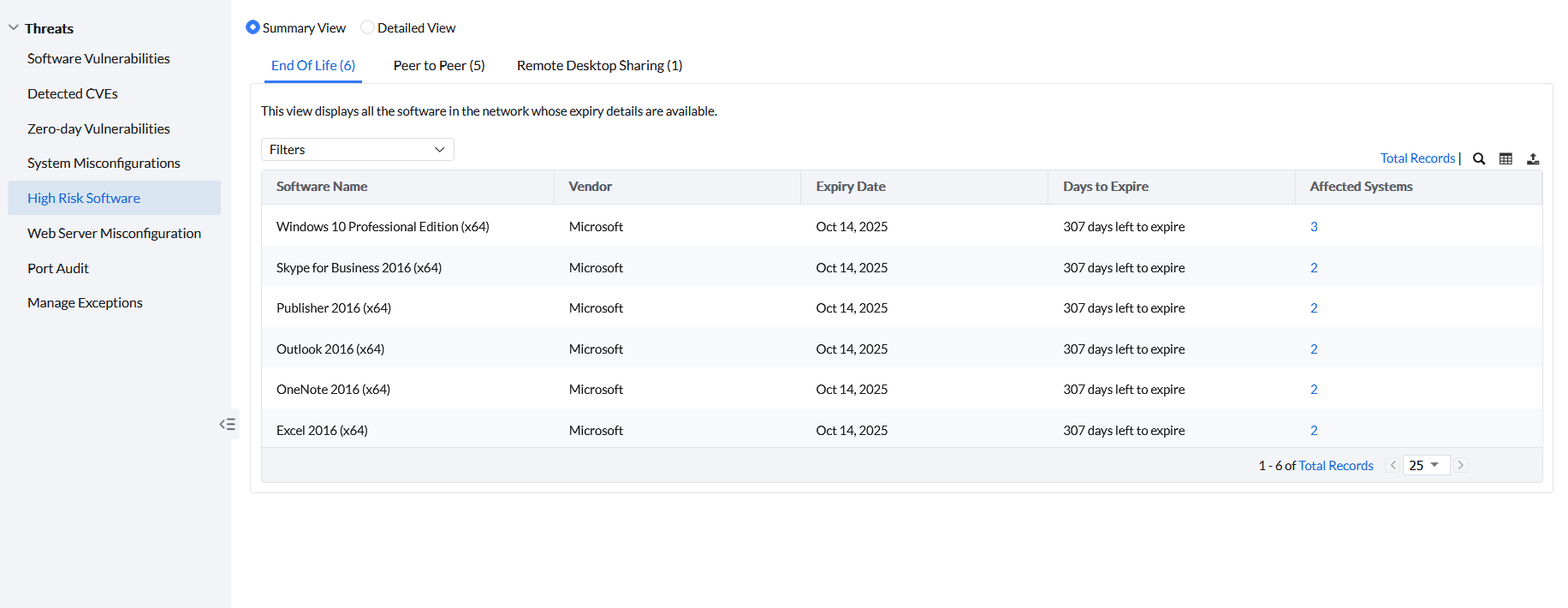
Patching may eliminate software vulnerabilities in applications and Operating Systems. But, how can you protect legacy applications and OSes that are no longer supported by the vendor? These End-of-Life software doesn't receive security updates and will be left with security gaps. Therefore, you must inspect the dependency of business critical resources and applications on EOL software and their importance to decide whether they're required or not. Under High Risk Software, click on End of Life; you can see all the End-of-Life software listed that are present across managed computers. You can see the name of the software listed along with its Vendor, Expiry Date, Days to Expiry and Affected Systems. By clicking on the system count in the Affected Systems, you can see the individual systems where that specific EOL software has been installed.
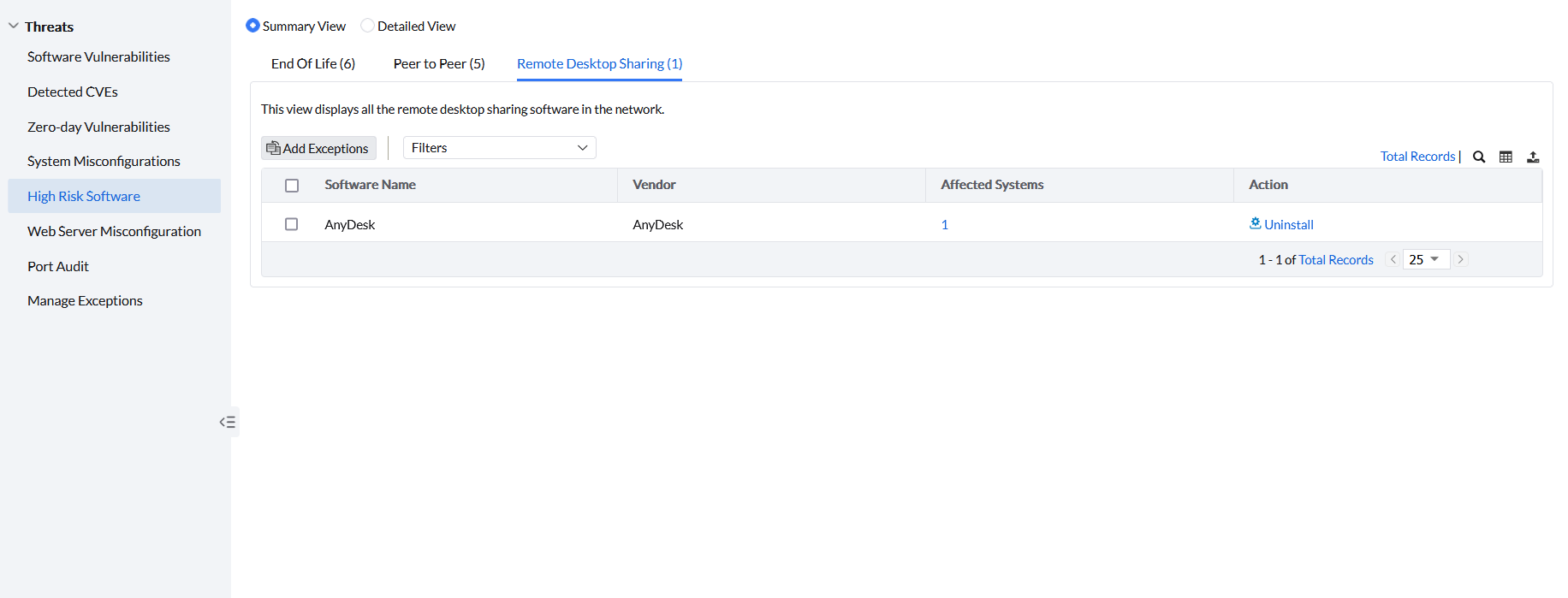
Employees might use remote desktop sharing software to connect to the work computer or a remote desktop server remotely from their home or public network. Unsecure connections might lead to exposure of the firewall port to the public, which increases the chances of getting infected with malware, ransomware, or data theft. This arises security concerns, such as whether the user is using a secure connection or not while remotely connecting to the system in the enterprise network. Therefore, it is advisable to eliminate Remote Desktop Sharing software from your network systems. Under High Risk Software, click on Remote Desktop Sharing; you can see all the software listed that that uses remote desktop sharing that are installed across managed computers. You can see the name of the software listed along with its Vendor and Affected Systems. By clicking on the system count in the Affected Systems, you can see the individual systems where that specific remote desktop sharing software has been installed. Under the Action column, click on Uninstall to uninstall that software. If you want to remove them from this view, click on Add Exceptions.
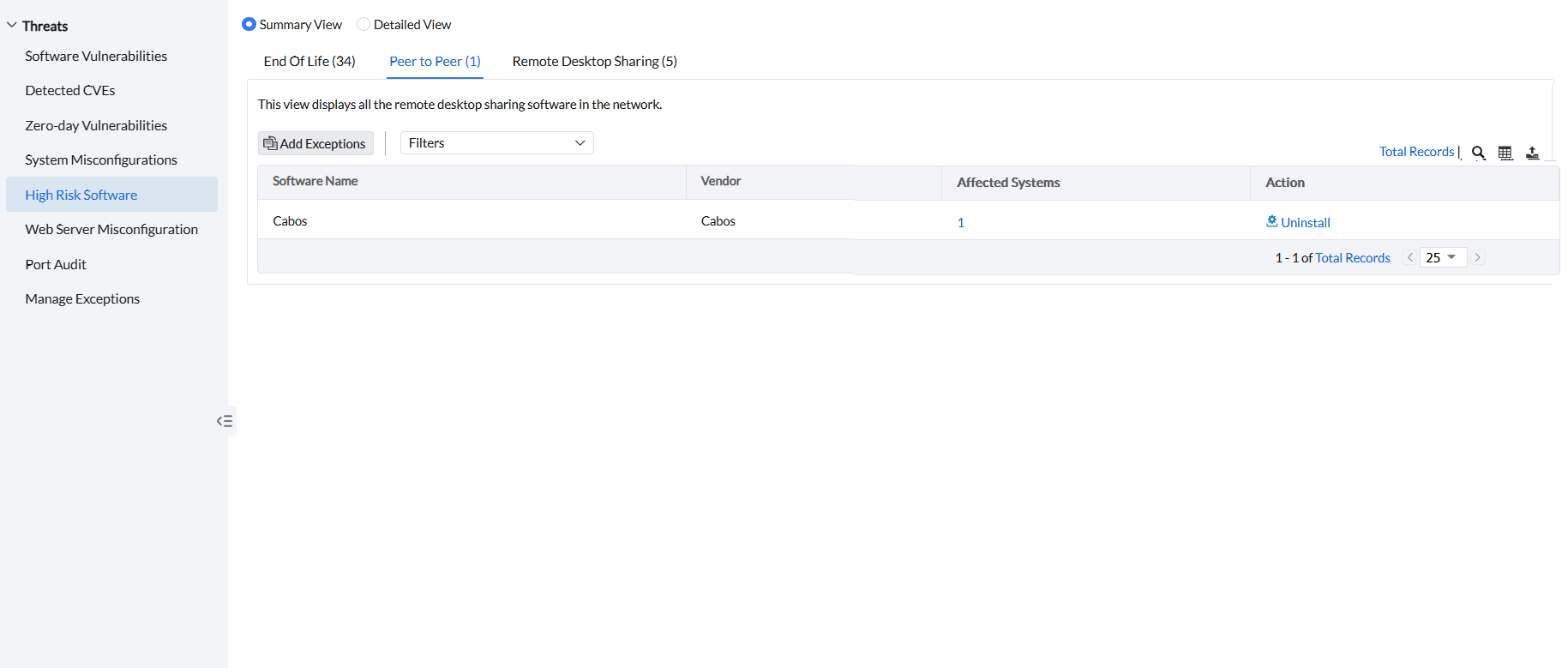
Employees might use peer to peer software to share and receive files to and from other computers on the internet. These software could pose a threat to network security as it opens certain ports to facilitate file sharing, and it is difficult to verify whether the source of the file is free from malware and viruses. Also, the directories that are shared can be accessed by anyone on the internet. This might also increase the chances of leakage of corporate data and personal information. So it is advised to uninstall these peer to peer software from your network systems if they are not required for any business critical tasks. Under High Risk Software, click on Peer to Peer; you can see all the peer to peer software listed that are installed across managed computers. You can see the name of the software listed along with its Vendor and Affected Systems. By clicking on the system count in the Affected Systems, you can see the individual systems where that specific peer to peer software has been installed. Under the Action column, click on Uninstall to uninstall that software. If you want to remove them from this view, click on Add Exceptions.
Note: If the software uninstallation has failed in any computer, you can see that computer listed under Attention Required view. To view those computers, click on Threats & Patches → Systems → Attention Required and under this section click on Software Uninstallation Failed, select the computers where the uninstallation has failed and click on Uninstall to retry the software uninstallation.
If you have any further questions, please refer to our Frequently Asked Questions section for more information.