Network Isolation in your Managed Network
IT Admins can detect and isolate devices that are found to be vulnerable. When a device is found to be non-compliant with companies' policies or infected with a ransomware, then such a device can be considered vulnerable. These devices need to be isolated from your network to prevent further manipulation of attack into your network.
Here is how Admins can achieve Network Isolation of devices using Endpoint Central.
Network Isolation of Ransomware Infected devices.
Network Isolation of Non-Compliant devices.
Ransomware Infected Devices:
Anti-ransomware detection policy aids in identification of devices that are infected with ransomware. When a device is found to be infected with ransomware, admins can quarantine that device to prevent further spread of the attack.
- Navigate to Anti-ransomware > Settings > Detection Policy in Endpoint Central console.
- Create a detection policy.
- The created policy can be:
an audit only process (where you can perceive data but no measures will be taken).
kill the process (find the process that manipulates the attack and kill that process).
Kill process and restore files (Kill the process and restore the modified files).
- Detection policy created is applicable to the entire managed network.
- Once the malware is identified and its processes are stopped, the next step is to quarantine this device from the managed network to prevent the spread of this attack. To achieve this Network Isolation of devices, Admins can execute scripts from Endpoint Central server with registry path values. HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\AdventNet\DesktopCentral\DCAgent\EDR\Isolate
- Upon deployment of scripts, the respective device will be isolated / quarantined from your network.
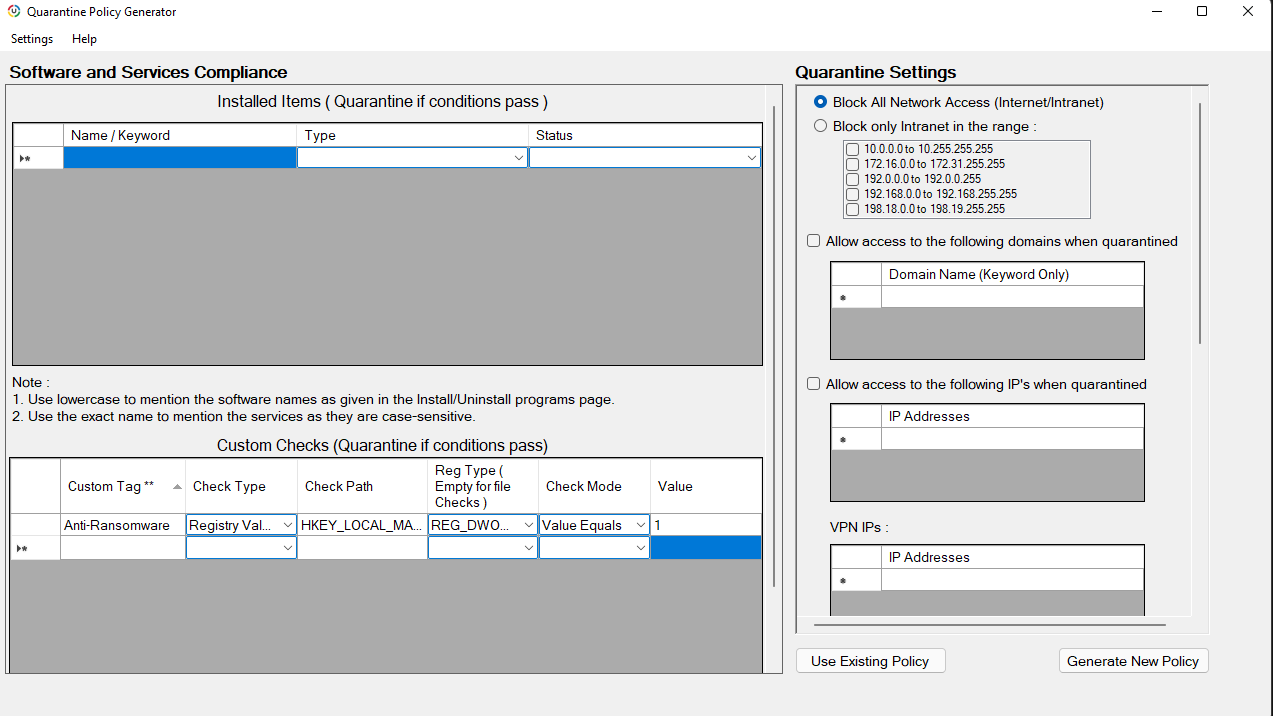
- To know more about Network isolation and leveraging Network access control, visit this page.
Non-Compliant devices:
With The Centre for Internet Security (CIS) Compliance policy, Admins can detect devices that fail to correlate with companies' policies. When a device is found to fail with most rules framed by the company, then such a device can be considered to be vulnerable. These devices are vulnerable to attacks and may infiltrate your managed network. In order to prevent such risks, IT Admins can now detect and quarantine these devices from the managed network.
To achieve Network Isolation of Non-Compliant devices:
- Navigate to Threats & Patches in Endpoint Central console.
- Under Threats & Patches, open the Compliance tab where you will find Create policy.
- Create a CIS policy and deploy it to target groups to gain insights on Compliance statuses of devices.
- Devices are categorized based on the number of rules in compliant with the policy. When a device fails most rules (90% and more), then such a device is considered to be vulnerable. Learn more about CIS policy offered by Endpoint Central here.
- When a device is found to be vulnerable in accordance with CIS policy, the next step is to isolate that device from the network. Admins can isolate/quarantine that device from the managed network by executing scripts from Endpoint Central server with registry path HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\AdventNet\DesktopCentral\DCAgent\ComplianceResources\Settings\SystemCompliancePercentage
- Upon deployment of scripts, the respective device will be isolated / quarantined from your network.
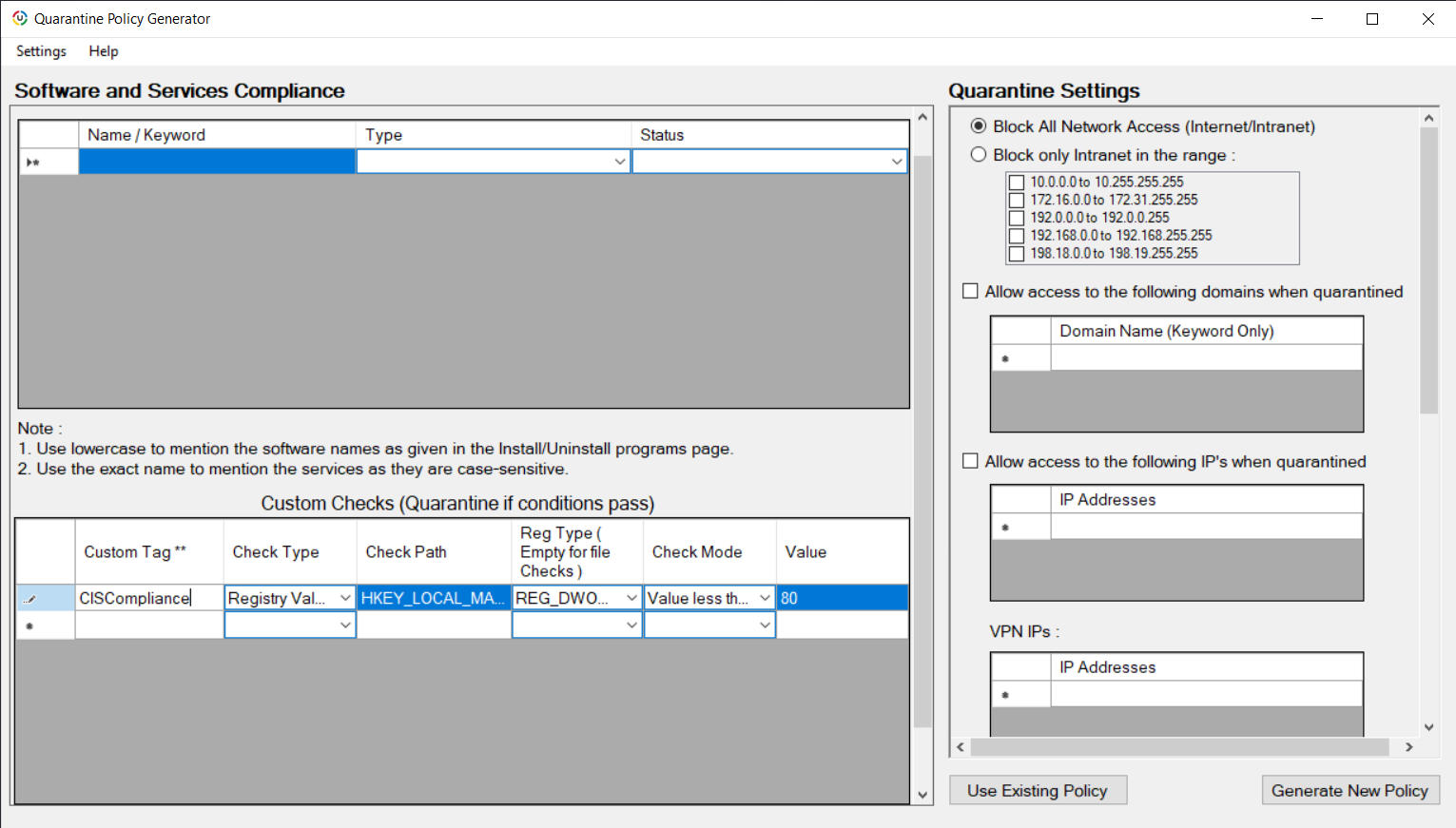
- To know more about Network isolation and leveraging Network access control, visit this page.
Admins can fix the issue manually or apply fixes automatically from the central console. Once the device is fixed, Admins can include that device to their managed network.
We respect your security and privacy concerns, hence no Personally Identifiable Information (PII) or browsing data is collected or logged by default.