- Free Edition
- What's New?
- Key Highlights
- Suggested Reading
- All Capabilities
-
Log Management
- Event Log Management
- Syslog Management
- Log Collection
- Agent-less Log Collection
- Agent Based Log collection
- Windows Log Analysis
- Event Log Auditing
- Remote Log Management
- Cloud Log Management
- Security Log Management
- Server Log Management
- Linux Auditing and Reporting
- Auditing Syslog Devices
- Windows Registry Auditing
- Privileged User Activity Auditing
-
Application Log Management
- Application Log Monitoring
- Web Server Auditing
- Database Activity Monitoring
- Database Auditing
- IIS Log Analyzer
- Apache Log Analyzer
- SQL Database Auditing
- VMware Log Analyzer
- Hyper V Event Log Auditing
- MySQL Log Analyzer
- DHCP Server Auditing
- Oracle Database Auditing
- SQL Database Auditing
- IIS FTP Log Analyzer
- IIS Web Log Analyzer
- IIS Viewer
- IIS Log Parser
- Apache Log Viewer
- Apache Log Parser
- Oracle Database Auditing
-
IT Compliance Auditing
- ISO 27001 Compliance
- HIPAA Compliance
- PCI DSS Compliance
- SOX Compliance
- GDPR Compliance
- FISMA Compliance Audit
- GLBA Compliance Audit
- CCPA Compliance Audit
- Cyber Essentials Compliance Audit
- GPG Compliance Audit
- ISLP Compliance Audit
- FERPA Compliance Audit
- NERC Compliance Audit Reports
- PDPA Compliance Audit reports
- CMMC Compliance Audit
- Reports for New Regulatory Compliance
- Customizing Compliance Reports
-
Security Monitoring
- Threat Intelligence
- STIX/TAXII Feed Processor
- Threat Whitelisting
- Real-Time Event Correlation
- Log Forensics
- Incident Management System
- Automated Incident Response
- Linux File Integrity Monitoring
- Detecting Threats in Windows
- External Threat Mitigation
- Malwarebytes Threat Reports
- FireEye Threat Intelligence
- Application Log Management
- Security Information and Event Management (SIEM)
- Real-Time Event Alerts
- Privileged User Activity Auditing
-
Network Device Monitoring
- Network Device Monitoring
- Router Log Auditing
- Switch Log Monitoring
- Firewall Log Analyzer
- Cisco Logs Analyzer
- VPN Log Analyzer
- IDS/IPS Log Monitoring
- Solaris Device Auditing
- Monitoring User Activity in Routers
- Monitoring Router Traffic
- Arista Switch Log Monitoring
- Firewall Traffic Monitoring
- Windows Firewall Auditing
- SonicWall Log Analyzer
- H3C Firewall Auditing
- Barracuda Device Auditing
- Palo Alto Networks Firewall Auditing
- Juniper Device Auditing
- Fortinet Device Auditing
- pfSense Firewall Log Analyzer
- NetScreen Log Analysis
- WatchGuard Traffic Monitoring
- Check Point Device Auditing
- Sophos Log Monitoring
- Huawei Device Monitoring
- HP Log Analysis
- F5 Logs Monitoring
- Fortinet Log Analyzer
- Endpoint Log Management
- System and User Monitoring Reports
-
Log Management
- Product Resources
- Related Products
- Log360 (On-Premise | Cloud) Comprehensive SIEM and UEBA
- ADManager Plus Active Directory Management & Reporting
- ADAudit Plus Real-time Active Directory Auditing and UBA
- ADSelfService Plus Identity security with MFA, SSO, and SSPR
- DataSecurity Plus File server auditing & data discovery
- Exchange Reporter Plus Exchange Server Auditing & Reporting
- M365 Manager Plus Microsoft 365 Management & Reporting Tool
- RecoveryManager Plus Enterprise backup and recovery tool
- SharePoint Manager Plus SharePoint Reporting and Auditing
- AD360 Integrated Identity & Access Management
- AD Free Tools Active Directory FREE Tools
EventLog Analyzer is a comprehensive application log monitoring and reporting tool that collects, analyzes, and correlates any application logs and provides actionable insights about network events. You can use the solution's application reports to identify anomalous user activities, troubleshoot application crashes, and detect security threats.
The solution collects and monitors web server application logs from IIS and Apache, databases including MySQL, Microsoft SQL server, Oracle server, IBM Db2, PostgreSQL, DHCP applications, and more. Further, with its custom log parser, EventLog Analyzer can parse and analyze any custom or in-house application log data. The solution also comes with a powerful correlation engine which helps detect security attack trails across network devices, servers, and applications.
Here's how EventLog Analyzer helps you proactively monitor application logs
Web application monitoring
EventLog Analyzer is a powerful solution for monitoring web server logs, including IIS server logs, Apache server logs, and DHCP server logs. This application's log analysis and reporting tool provides real-time alerts for DoS, cross-site scripting, and similar attacks targeting the IIS and Apache web servers for prompt mitigation of web application security attacks. It performs effective web server application log analysis and provides detailed reports on HTTP errors occurring on the web server, security attacks, malicious URL requests, and much more.
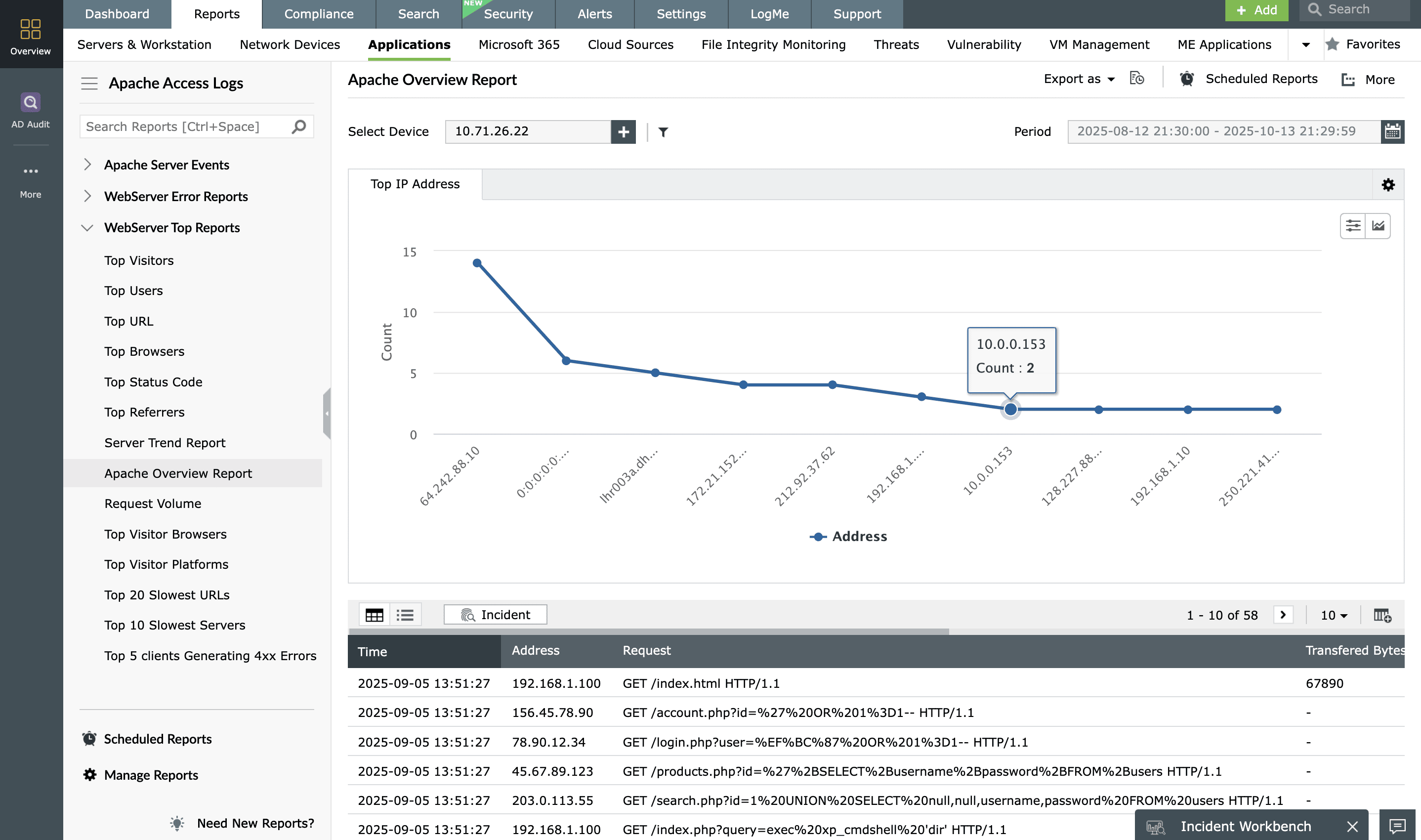
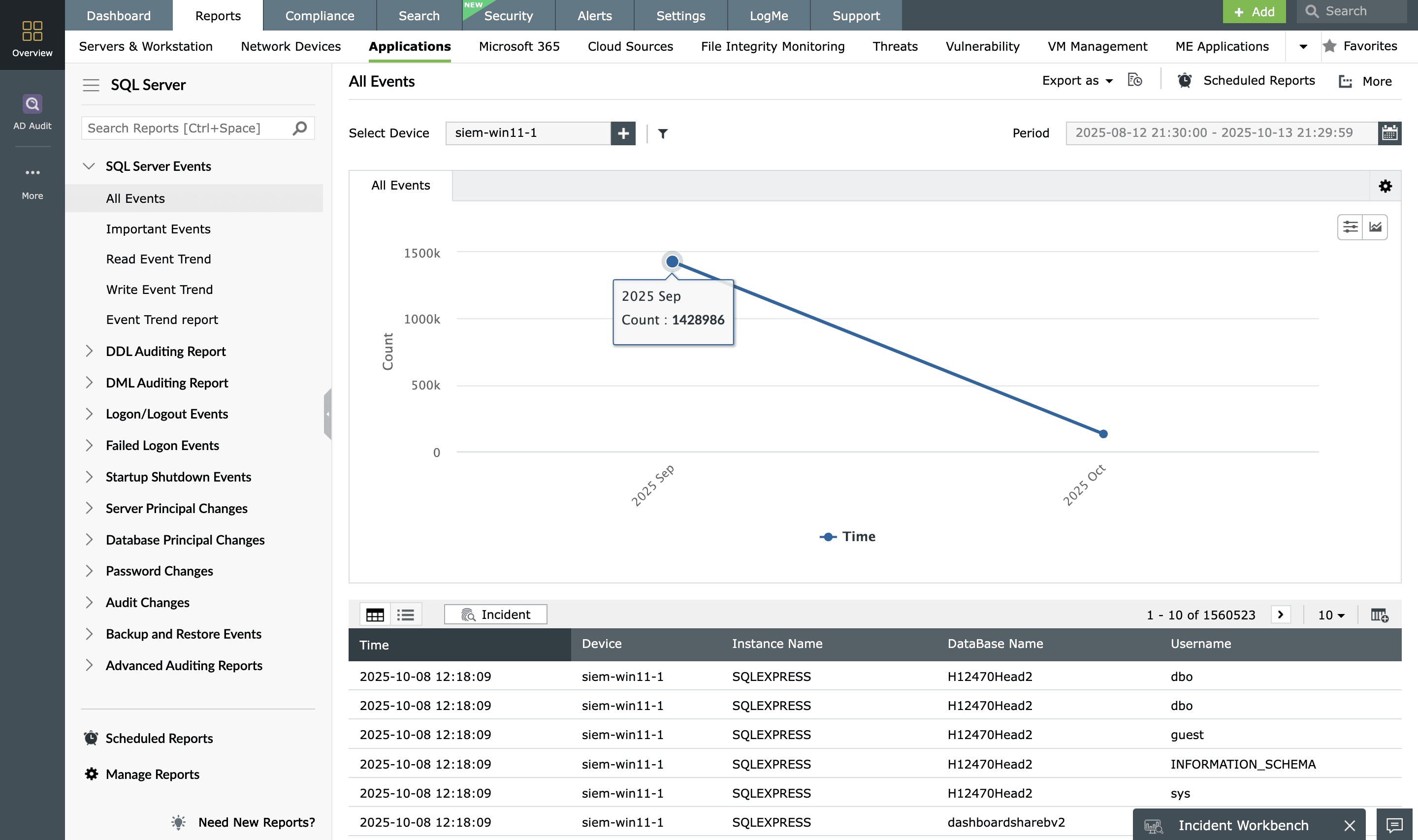
Database activity monitoring
EventLog Analyzer streamlines the process of database auditing and helps monitor database applications such as MS SQL, MySQL, Oracle, IBM DB2, and PostgreSQL. The solution maintains a detailed record of data definition language (DDL) and data manipulation language (DML) changes and users' access to the database, including who accessed the database, what actions were performed, and the timestamp of each activity. The alert profiles ensure you are notified of events that could pose a threat to database security such as privilege abuse, SQL injection, DoS, mass data deletion, and unauthorized backup activity.
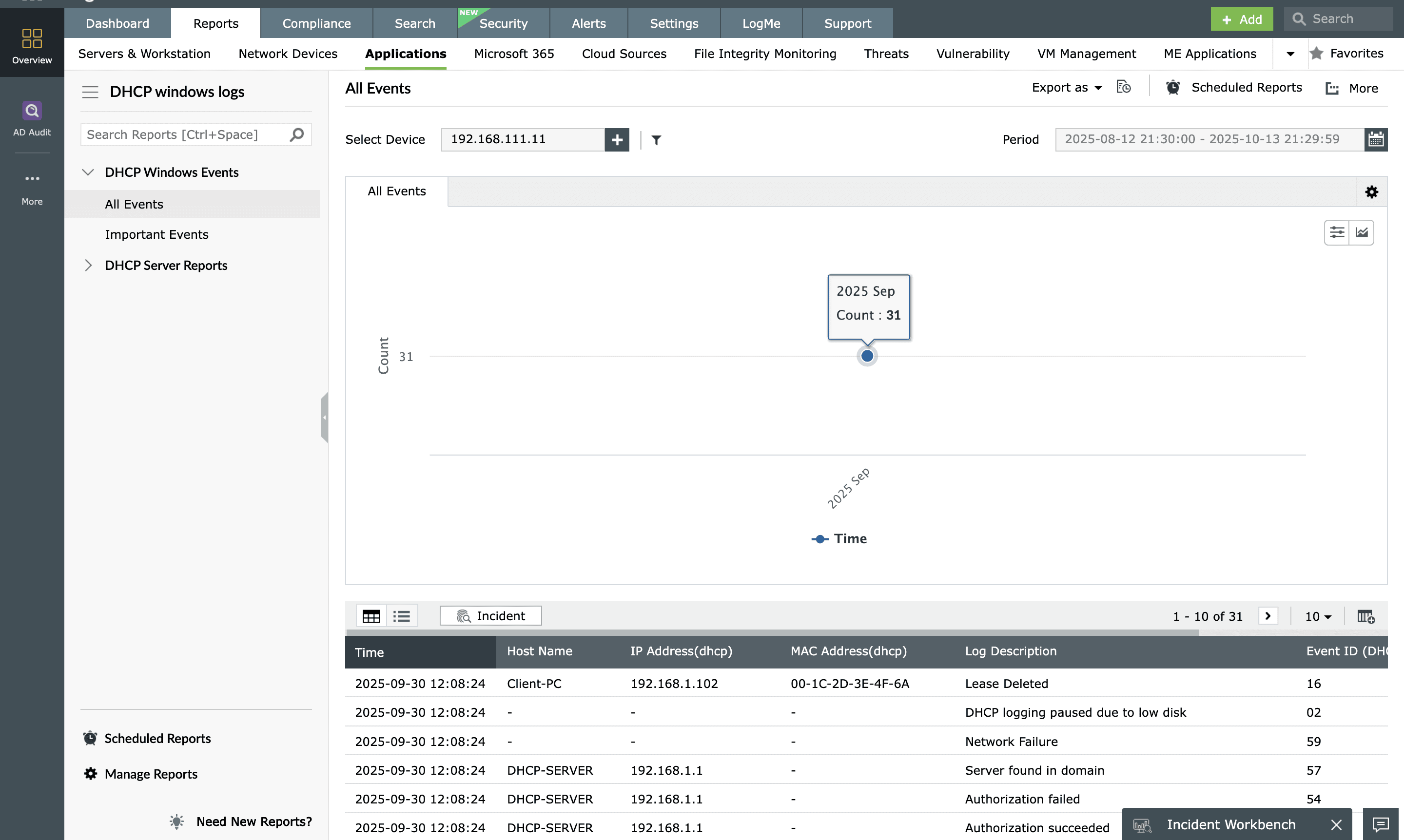
DHCP server monitoring
EventLog Analyzer simplifies DHCP server log analysis for Windows and Linux systems. It helps you gain deep insights into DHCP usage, top clients, and error frequency to enhance network monitoring and management. DHCP Linux Logs Reports of EventLog Analyzer provides comprehensive in-built reports such as top MAC address, top gateway used and negative acknowledgements to track and monitor the logs generated by Linux DHCP. You can easily track and monitor all DHCP server events through these exhaustive reports, staying informed about DHCP changes and ensuring network stability.
Print server monitoring
With EventLog Analyzer, managing print server security and monitoring becomes easier and more efficient. The solution helps manage print server logs by offering comprehensive tracking and monitoring of every printed document within your printer environment. The software provides out-of-the-box reports, eliminating the need for additional configuration, and presents important log statistics in intuitive graphs. It aids in generating detailed reports on user access and usage frequency to print servers, documents printed, printer activity trends, and more.
Other solutions offered by EventLog Analyzer
Windows event log monitoring
Automatically discover Windows event logs and enhance your security monitoring and incident response capabilities.
IDS/IPS log monitoring
Centrally collect and monitor IDS/IPS logs to detect anomalies and cyberattacks at the network intrusion stage itself.
SNMP monitoring
Easily track and analyze SNMP traps based on the severity level and identify suspicious events in real time.
VPN log monitoring
Keep track of VPN connections established within your network and analyze trends in login patterns.
5 reasons to choose EventLog Analyzer as your application log monitoring solution
1. Centralized log management
Get a consolidated view of application log data gathered from various sources and store it in a centralized location for efficient analysis.
2. Advanced log analysis
Uncover meaningful insights from your application logs and identify security incidents promptly with the advanced log analysis feature.
3. Real-time alerting and notifications
Mitigate application security attacks with real-time alerting, which sends instant alerts for any anomalies found in your applications.
4. Log forensic analysis
Conduct in-depth log forensic analysis to backtrack attacks and identify the root cause of incidents.
5. IT compliance reporting
Generate IT compliance reports and audit trails for regulatory mandates such as the GDPR, PCI DSS, FISMA, HIPAA, CCPA, and more.
Frequently asked questions
Application logs are files that store information about events that happen within an application. Application logs contain information about:
- User activity such as logins, logouts, page views, and search queries.
- Application errors such as exceptions and crashes.
- Security events such as failed login attempts and suspicious traffic.
- Performance metrics such as response times and throughput.
Application log monitoring is the process of collecting and analyzing logs generated by various applications, servers, databases, operating systems, and other components in your IT infrastructure. By analyzing these application logs, you can gain valuable insights into the user behavior, system events, security threats, and application performance, such as response times and resource utilization.
EventLog Analyzer's real-time log monitoring feature enhances your security posture by detecting critical security events and anomalies in application logs. It analyzes log entries for patterns, signatures, and anomalies that indicate potential security attacks. The software also incorporates advanced threat intelligence to promptly detect and respond to security threats in real time.
Some of the best practices for application logging are:
- Clearly define which events to log such as errors, performance metrics, user actions, or security events.
- Choose appropriate logging levels (like debug, info, warning, error, critical) to categorize log messages based on their severity.
- Don't log any sensitive information like user credentials or credit card details.
- Use structured log formatting to parse and analyze logs.
- Store logs in a central location and periodically review logs.
Using an application log analysis and reporting tool like EventLog Analyzer automates collecting, storing, and analyzing logs from all applications and other network components in your network. It also detects sophisticated attack vectors and bolsters your organization's security defenses.