- Free Edition
- What's New?
- Key Highlights
- Suggested Reading
- All Capabilities
-
Log Management
- Event Log Management
- Syslog Management
- Log Collection
- Agent-less Log Collection
- Agent Based Log collection
- Windows Log Analysis
- Event Log Auditing
- Remote Log Management
- Cloud Log Management
- Security Log Management
- Server Log Management
- Linux Auditing and Reporting
- Auditing Syslog Devices
- Windows Registry Auditing
- Privileged User Activity Auditing
-
Application Log Management
- Application Log Monitoring
- Web Server Auditing
- Database Activity Monitoring
- Database Auditing
- IIS Log Analyzer
- Apache Log Analyzer
- SQL Database Auditing
- VMware Log Analyzer
- Hyper V Event Log Auditing
- MySQL Log Analyzer
- DHCP Server Auditing
- Oracle Database Auditing
- SQL Database Auditing
- IIS FTP Log Analyzer
- IIS Web Log Analyzer
- IIS Viewer
- IIS Log Parser
- Apache Log Viewer
- Apache Log Parser
- Oracle Database Auditing
-
IT Compliance Auditing
- ISO 27001 Compliance
- HIPAA Compliance
- PCI DSS Compliance
- SOX Compliance
- GDPR Compliance
- FISMA Compliance Audit
- GLBA Compliance Audit
- CCPA Compliance Audit
- Cyber Essentials Compliance Audit
- GPG Compliance Audit
- ISLP Compliance Audit
- FERPA Compliance Audit
- NERC Compliance Audit Reports
- PDPA Compliance Audit reports
- CMMC Compliance Audit
- Reports for New Regulatory Compliance
- Customizing Compliance Reports
-
Security Monitoring
- Threat Intelligence
- STIX/TAXII Feed Processor
- Threat Whitelisting
- Real-Time Event Correlation
- Log Forensics
- Incident Management System
- Automated Incident Response
- Linux File Integrity Monitoring
- Detecting Threats in Windows
- External Threat Mitigation
- Malwarebytes Threat Reports
- FireEye Threat Intelligence
- Application Log Management
- Security Information and Event Management (SIEM)
- Real-Time Event Alerts
- Privileged User Activity Auditing
-
Network Device Monitoring
- Network Device Monitoring
- Router Log Auditing
- Switch Log Monitoring
- Firewall Log Analyzer
- Cisco Logs Analyzer
- VPN Log Analyzer
- IDS/IPS Log Monitoring
- Solaris Device Auditing
- Monitoring User Activity in Routers
- Monitoring Router Traffic
- Arista Switch Log Monitoring
- Firewall Traffic Monitoring
- Windows Firewall Auditing
- SonicWall Log Analyzer
- H3C Firewall Auditing
- Barracuda Device Auditing
- Palo Alto Networks Firewall Auditing
- Juniper Device Auditing
- Fortinet Device Auditing
- pfSense Firewall Log Analyzer
- NetScreen Log Analysis
- WatchGuard Traffic Monitoring
- Check Point Device Auditing
- Sophos Log Monitoring
- Huawei Device Monitoring
- HP Log Analysis
- F5 Logs Monitoring
- Fortinet Log Analyzer
- Endpoint Log Management
- System and User Monitoring Reports
-
Log Management
- Product Resources
- Related Products
- Log360 (On-Premise | Cloud) Comprehensive SIEM and UEBA
- ADManager Plus Active Directory Management & Reporting
- ADAudit Plus Real-time Active Directory Auditing and UBA
- ADSelfService Plus Identity security with MFA, SSO, and SSPR
- DataSecurity Plus File server auditing & data discovery
- Exchange Reporter Plus Exchange Server Auditing & Reporting
- M365 Manager Plus Microsoft 365 Management & Reporting Tool
- RecoveryManager Plus Enterprise backup and recovery tool
- SharePoint Manager Plus SharePoint Reporting and Auditing
- AD360 Integrated Identity & Access Management
- AD Free Tools Active Directory FREE Tools
As a crucial component of network security, database auditing is essential for safeguarding sensitive corporate data, strengthening security measures, and ensuring compliance with regulatory requirements.
ManageEngine EventLog Analyzer aids in database auditing by seamlessly collecting and monitoring logs from various database servers. The solution delivers comprehensive reporting and analysis of database activity across platforms such as Microsft SQL, Oracle, MySQL, and IBM DB2 by correlating and investigating log data. It also provides user activity tracking, change management, server activity tracking, and detection of database security attacks like SQL injection.
Here's how EventLog Analyzer helps you proactively audit database servers
Simplified approach to effective database management
EventLog Analyzer is a comprehensive database log management solution that streamlines the collection of database logs from across your network. It simplifies log analysis by providing preconfigured reports for various database activities, including account management, user changes, server security, and more. Not only does it compile these reports, but it also keeps you informed in real-time about security events through instant alerts. EventLog Analyzer ensures the secure archiving of logs, adding an extra layer of protection.
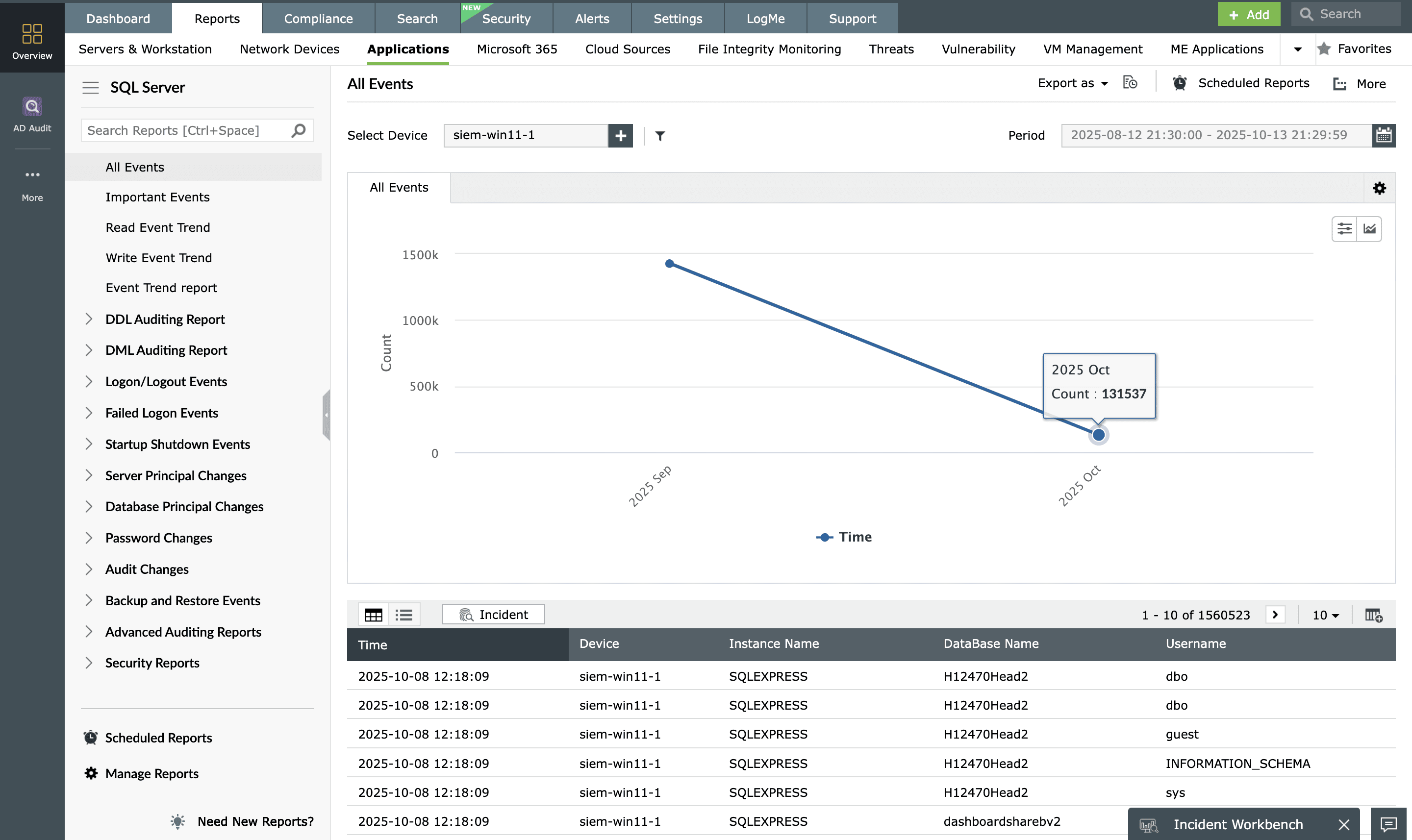
Strengthening security through user monitoring
EventLog Analyzer aids in monitoring database server logs. It provides real-time analysis of server activity, user logins, and changes to accounts and permissions. It establishes a robust security posture by tracking user actions within the system, including logon and logoff activity, user account validation, configuration changes, and more. The solution strengthens database security by promptly responding to critical events, providing a proactive defense against potential threats and vulnerabilities.
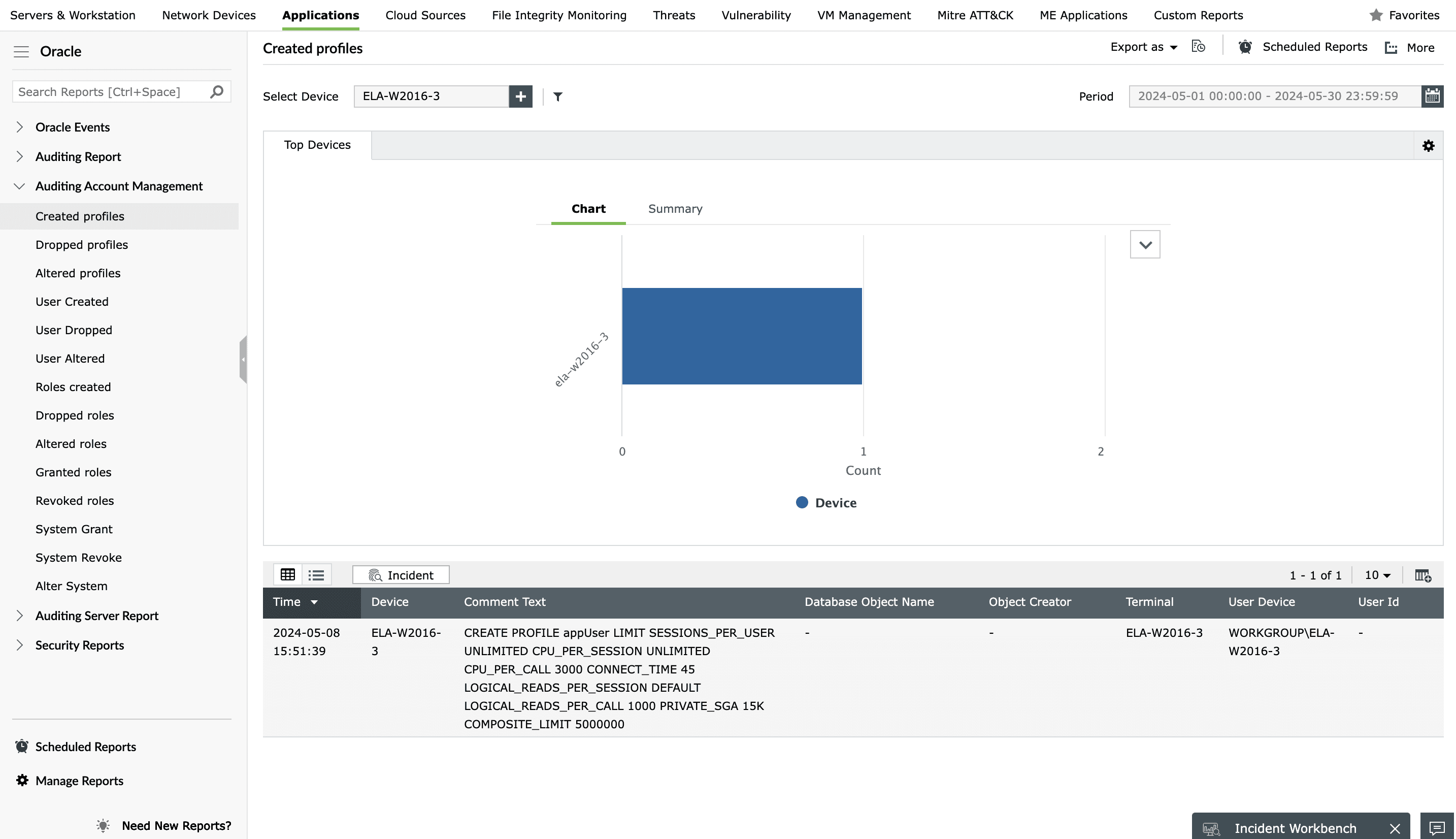
Effortless monitoring and auditing for regulatory compliance
EventLog Analyzer provides real-time monitoring to alert on prominent database attacks like SQL injection, maintains an audit trail for compliance and investigations, identifies complex attack patterns through correlation of events, and provides prebuilt reports for regulatory compliances, including HIPAA, PCI DSS, FISMA, and SOX.
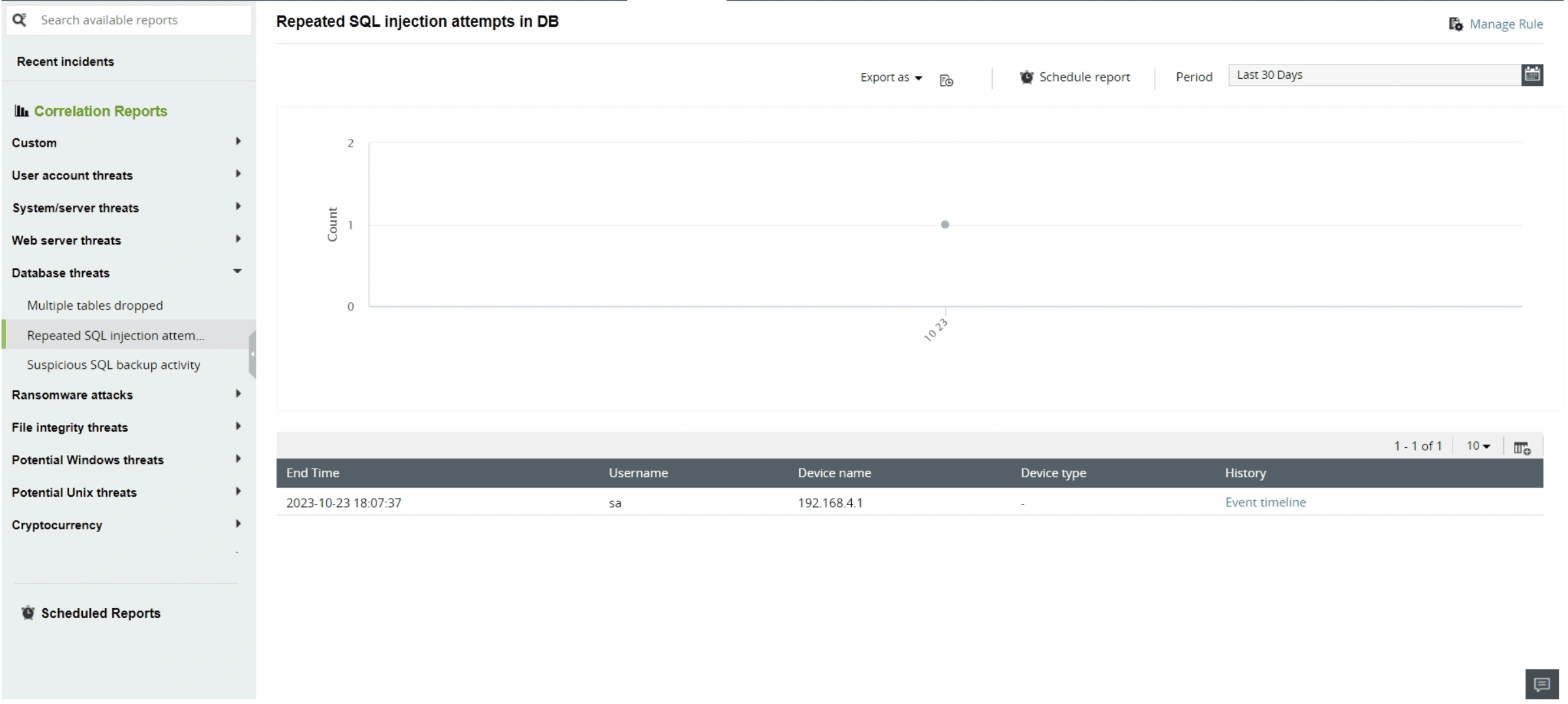
Evaluate database server operations
EventLog Analyzer offers in-depth analysis capabilities by providing reports specifically designed for database server log analysis. These reports provide insights into users who logged in the most or users who failed logons the most, enabling a more comprehensive understanding of database server activity. By utilizing these reports, you can derive valuable insights from your logs, identify patterns, and trends in server activities, and make data-driven decisions to enhance database security and performance. This deeper analysis helps to address issues proactively and optimize database operations for improved efficiency and security.
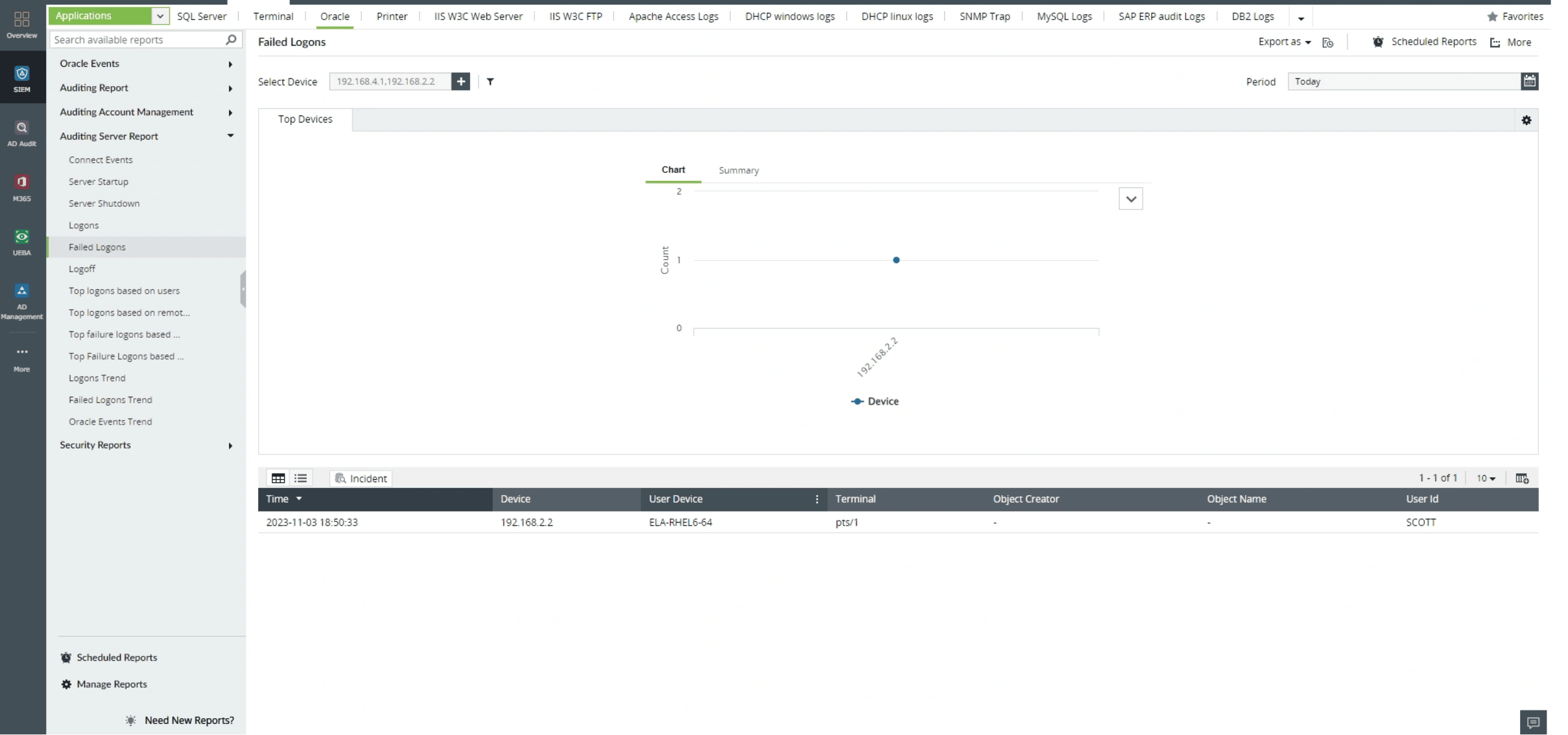
Real-time alerts for instant database security
Database activity monitoring is essential for maintaining data security. It enables comprehensive tracking and issues instant alerts about security events in the database, including crucial database transactions like change in DDL and DML statements. With this capability, you can identify and monitor who accesses the database and track the specific actions they perform, ensuring accountability and data integrity. By promptly detecting any suspicious or unauthorized activities, this monitoring contributes to enhanced security and compliance with regulatory standards.
Other solutions provided by EventLog Analyzer
Proactive database auditing
Proactively monitor database changes and activities such as database creation, modification and server activity, as well as server activities such as startups, shutdowns, and creation of server level objects.
Oracle database auditing
Efficiently audit Oracle database operations with detailed predefined reports and track structural changes, queries, and user modifications.
Log analysis
Enhance log analysis through centralized log collection, real-time monitoring, log correlation and facilitate custom alerting, compliance reporting, and user activity tracking for effective log analysis that are critical in security threat detection and troubleshooting.
Comprehensive user activity monitoring
Analyze user actions, track sessions, and set real-time alerts for unusual behavior. Access reports for privileged user oversight, data loss prevention, compliance reporting, and enable historical analysis for security incident investigations.
5 reasons to choose EventLog Analyzer as your database monitoring tool
1. Comprehensive user activity monitoring
Analyze user actions, track sessions, and set real-time alerts for unusual behavior. Access reports for privileged user oversight, data loss prevention, compliance reporting, and enable historical analysis for security incident investigations.
2. Enhanced forensic analysis
EventLog Analyzer enables detailed incident investigations through advanced historical analysis, providing a precise timeline for forensic examination of security incidents.
3. Elevate SQL server security
Identify intricate attack patterns within SQL servers, detecting potential threats like privilege abuse, credential theft, and SQL injection attempts.
4. In-depth privileged user monitoring
EventLog Analyzer delivers detailed insights into privileged user activity, generating graphical reports for both device-specific and user-centric events.
5. Advanced reporting and compliance
The tool includes advanced reporting capabilities with predefined templates for various regulatory standards such as HIPAA, PCI DSS, GDPR, FISMA, SOX, SOC 2 and others, streamlining compliance efforts and facilitating audit preparation.
Frequently asked questions
Database auditing is a process of monitoring and tracking activities, and granting access to a database to ensure data security, compliance with regulations, and the integrity of the information stored within the database. This practice involves recording and analyzing events and actions related to the database management system (DBMS) and the data it contains
To audit data in a database, set clear objectives, enable auditing (either through the database's native features or third-party tools), configure what to audit, and regularly review logs for unauthorized activities. Take necessary actions, secure audit data, generate compliance reports, and adapt the auditing configuration as the database evolves.
The purpose of a database audit is to safeguard data security, uphold regulatory compliance, and verify data integrity. It involves systematically tracking and recording actions related to a database and its management system. This process helps detect security breaches, unauthorized access, and data tampering, ensuring the protection and authenticity of data. Furthermore, it aids in demonstrating adherence to legal and industry standards, supports forensic investigations, and offers insights for optimizing database performance.
Within a SQL database management system, SQL database auditing involves monitoring and recording activities to:
- Enhance security: Helps prevent unauthorized access and data breaches by tracking SQL statements and commands.
- Maintain compliance: Ensures adherence to regulatory standards and industry-specific requirements.
- Establish accountability: Assigns responsibility for database actions to deter malicious activities and enforce data governance.
- Facilitate forensics: Provides a detailed history of SQL queries for investigations into security incidents.
To implement SQL database auditing, enable auditing, capture relevant data, store it in audit logs, regularly review logs, and take necessary actions. This can be accomplished using built-in DBMS features or third-party tools, depending on the complexity and requirements of the database environment.