As a network security administrator, monitoring and analyzing your Cisco firewall logs in real time is of utmost importance. For a secure network, you need to:
However, doing these tasks manually by exporting logs is extremely cumbersome and hence the need for a Cisco syslog analyzer tool.
Firewall Analyzer can analyze, report, and archive logs received from Cisco firewalls. Once the Cisco firewall is configured to direct log streams to the Firewall Analyzer server, Firewall Analyzer starts to generate in-depth Cisco log reports (Log Analyzer Cisco).
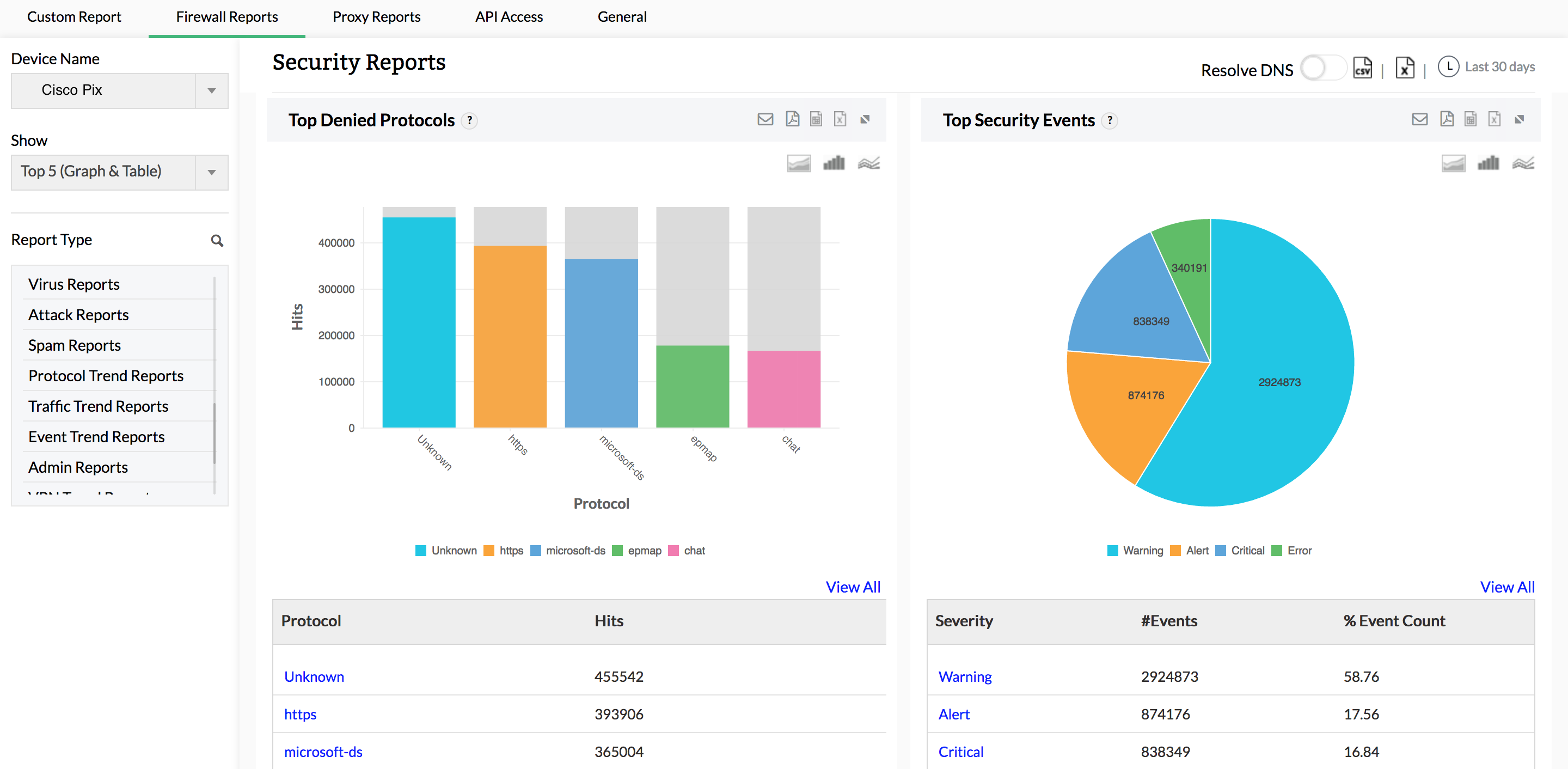
This Cisco firewall syslog analyzer generates reports on possible security threats and provides in-depth information on virus attacks in your network. Monitor failed logins, denied hosts, denied protocols, spam generators, spam receivers, and rules allowing spam. View comprehensive details on raw logs related to viruses to help pinpoint the origin of any specific attack.
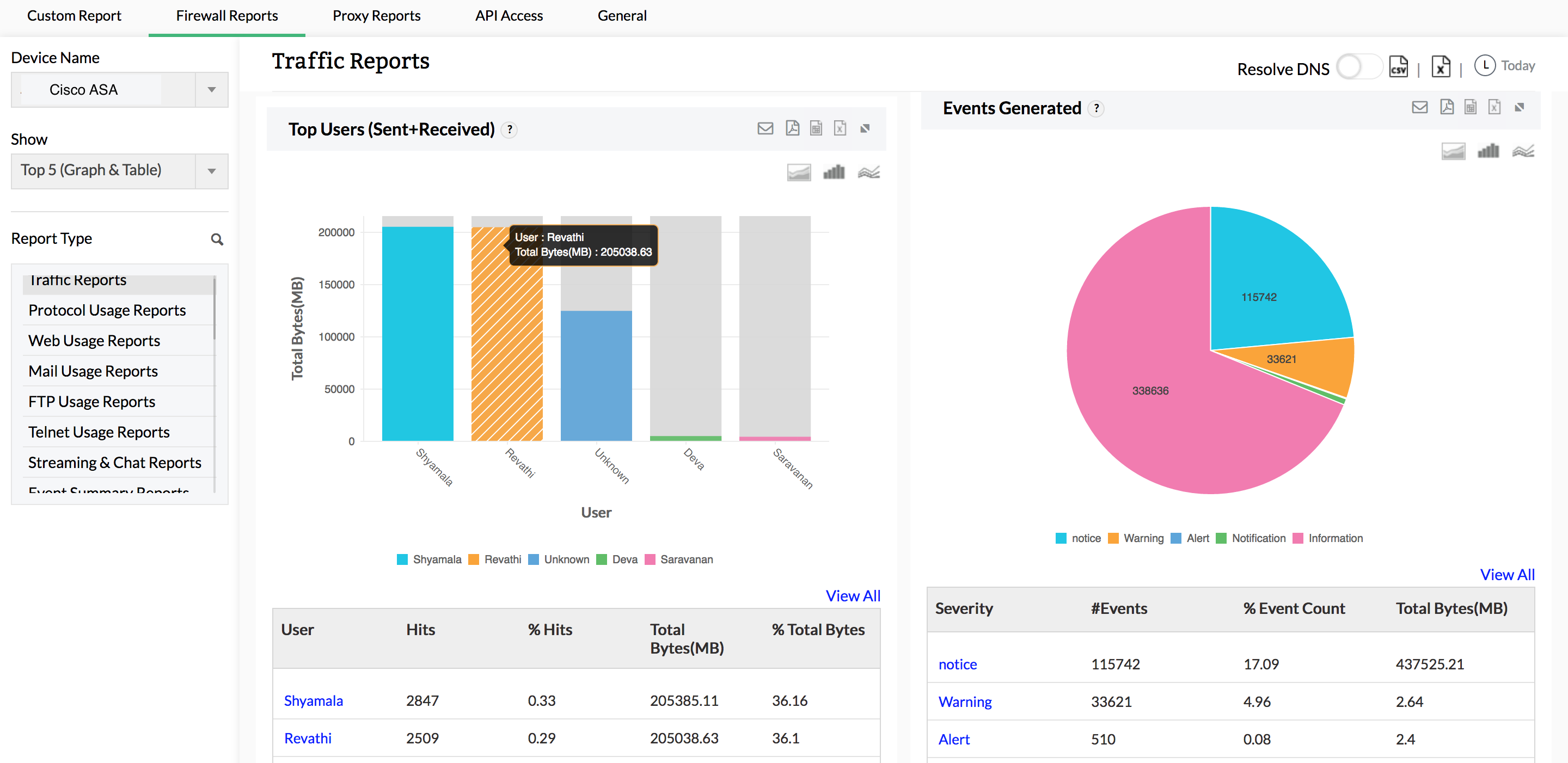
Firewall Analyzer provides a unique way to analyze the traffic in your network. This Cisco log viewer measures network traffic by analyzing logs, and churns out different traffic reports for web usage, mail usage, FTP usage, Telnet usage, intranet usage, internet usage, URLs visited, inbound traffic, and outbound traffic. As a security administrator, you can visualize behavior patterns for network traffic from these reports, and optimize bandwidth accordingly.
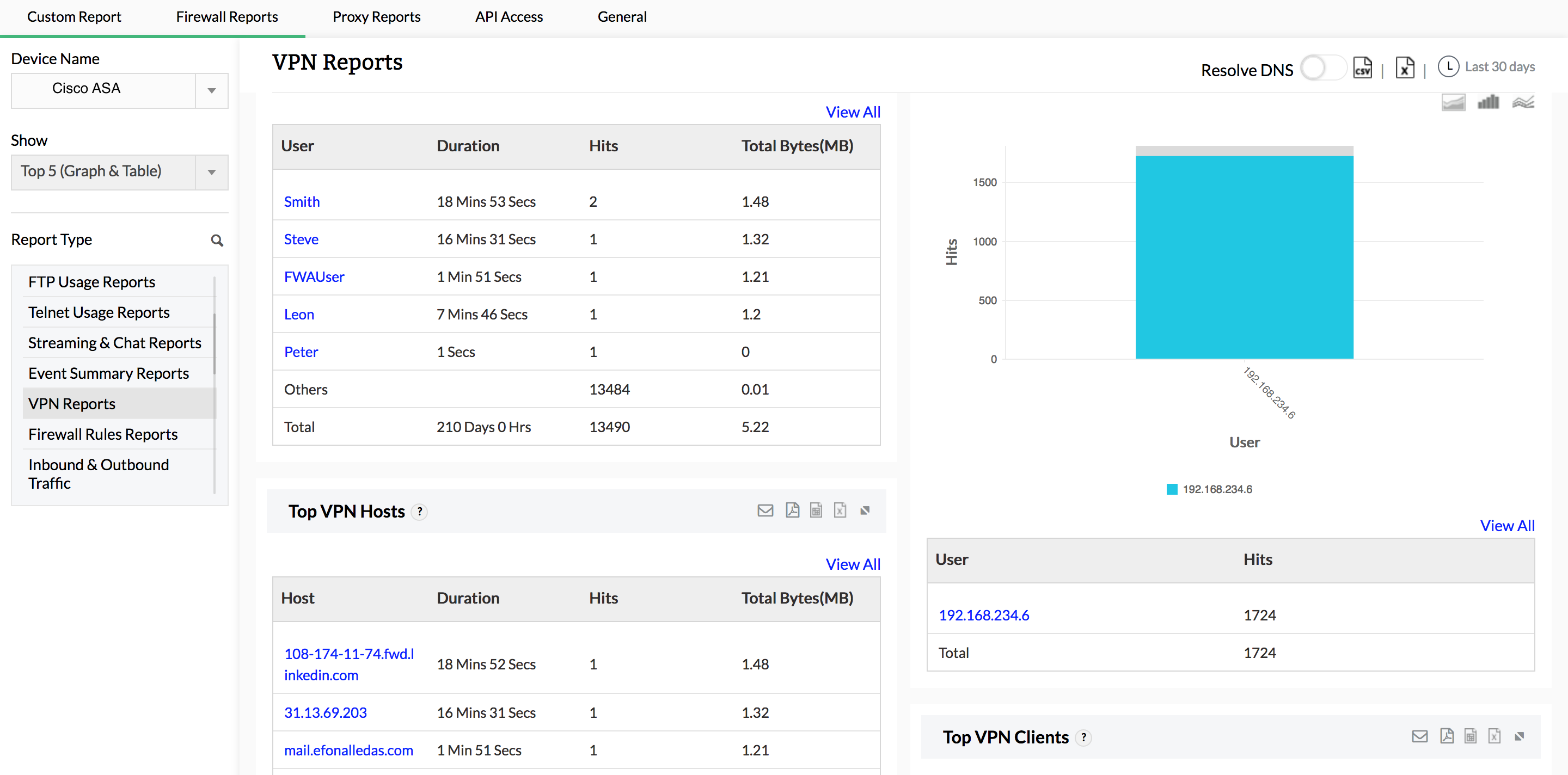
Get complete visibility on VPN hosts and protocols, as well as bandwidth used by VPN users during peak and off-peak hours. These reports provide information on the active users connected to your VPN, along with all failed VPN login attempts. Information on failed VPN logins is useful for identifying unauthorized login attempts.
Apart from exhaustive firewall reports on network security, Firewall Analyzer offers a comprehensive alarm management module. Alarms are generated for anomalous security and bandwidth events. Any alarm that is generated is recorded in Firewall Analyzer, and these alarms can be sent to stakeholders in real time via email and SMS. Alarms can also trigger scripts to mitigate security events the very moment an attack is detected.