Firewall Analyzer's integrated compliance management function automates your firewall compliance audits with its out-of-the-box firewall security standards reports on the following regulatory mandates
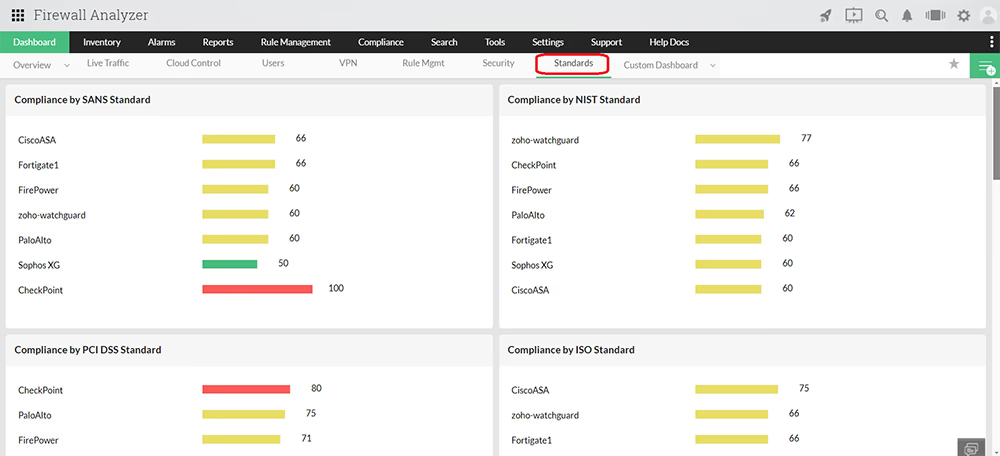
To know more on compliance management, get a personalized demo.
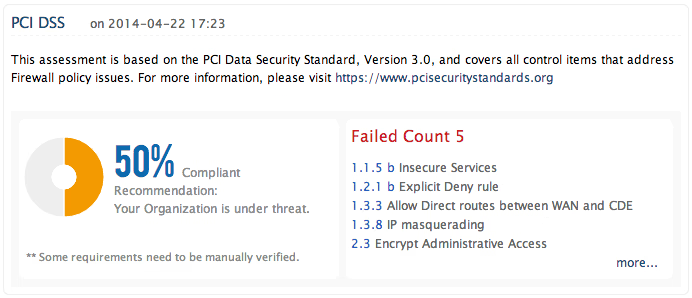
Request DemoPayment Card Industry Data Security Standard guidelines were developed to enhance the cardholder data security in organizations that process or transmit customer credit card data. The requirements of this compliance mandate includes
Firewall Analyzer helps you to meet PCI compliance requirements by installing and maintaining firewall configurations that allow you to build a secure network. It also provides you out-of-the-box reports and real-time alerts that ensures the security of cardholder data. The solution also helps you to review and audit the firewall configurations periodically and archives the firewall logs for conducting audit trails at an ease.
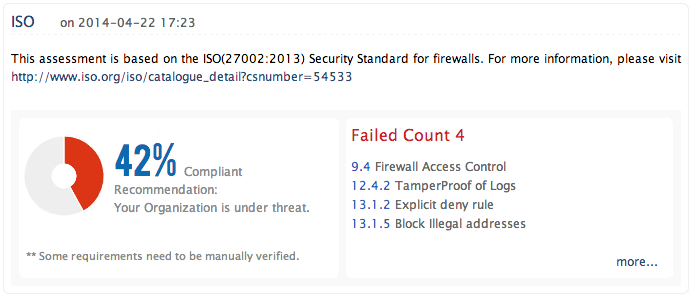
ISO 27001:2013 is a comprehensive internationally recognized information security standard that ensures the protection of organization's business sensitive information.It provides information security control measures for organizations that helps protecting their information assets against threats to confidentiality, integrity and availability.
Firewall Analyzer helps in complying to ISO 27001:2013 standard by meeting its requirements that are concerned with the implementation and maintenance of firewall device.With its off-the-shelf comprehensive reports on Firewall Access control, Configuration and Policy changes & Network Traffic it ensures the protection of your business sensitive information
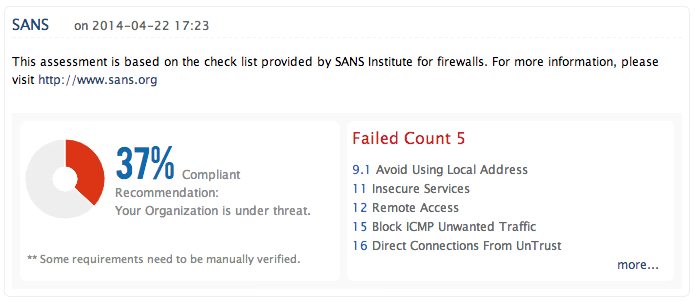
SANS Institute provides a general checklist of security considerations that are to be used while auditing a firewall. These widely accepted checklist for firewall auditing helps preventing unauthorized traffic to your secure network and avoids unintentional data loss or access to confidential data by outsiders.
Firewall Analyzer helps you to compare your organization's firewall configuration status with that of the SANS checklist and ensures security round the clock. The solution also automates your periodical firewall audits thus improving your operational efficiency.
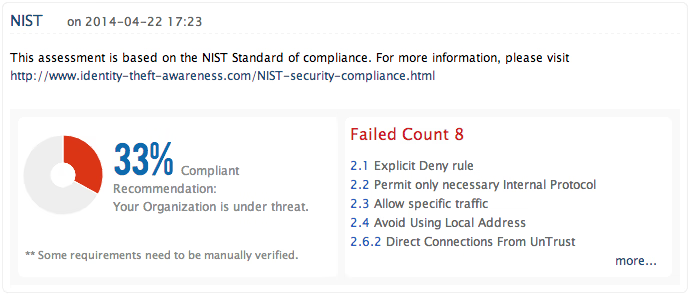
National Institute of Standards and Technology (NIST) provides a set of guidelines on information security controls for Federal Agencies and other organizations that helps protecting their network from security breaches.
Firewall Analyzer helps meeting NIST guideline requirements with its instant reports on inbound and outbound network traffic monitoring, firewall policy/configuration reviewing, Remote Firewall Management Access and more
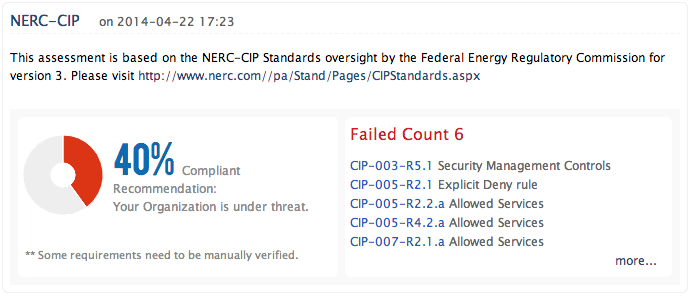
North American Electric Reliability Corporation (NERC) has designed its Critical Infrastructure Protection (CIP) standards to secure assets and business sensitive information from external threat.
With its comprehensive report templates and Alert mechanisms, Firewall Analyzer helps meeting NERC CIP's requirements on
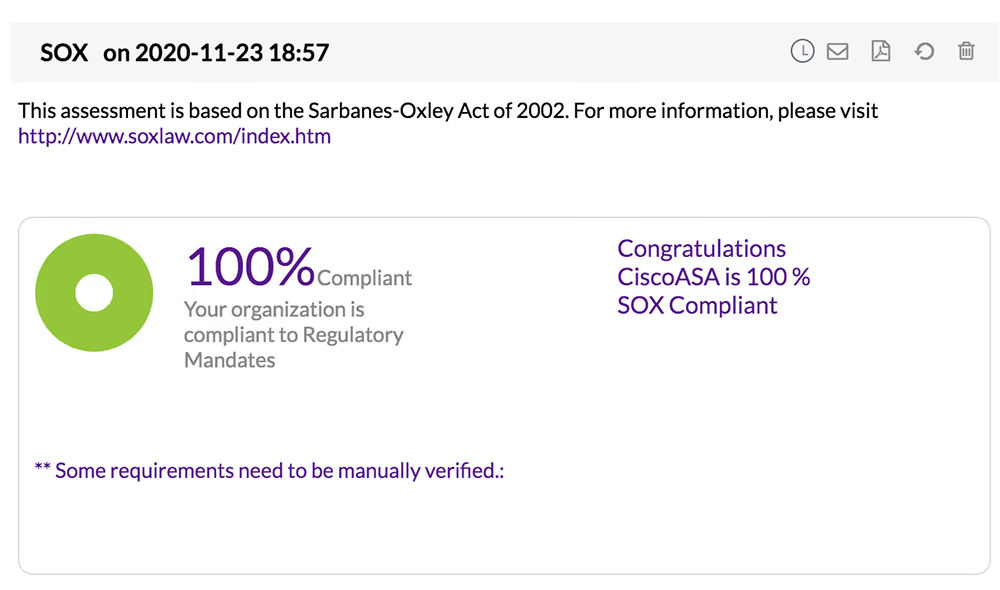
The Sarbanes-Oxley (SOX) protects shareholders and the general public from fraudulent practices in enterprises and accounting errors. It aims to improve the accuracy of corporate disclosures. This policy was incorporated to keep a check on how enterprises manage their internal controls. In a network security environment, this translates to a policy where all the data stored should be enabled with access controls, proper and error-free installations of backup procedures, scrutiny of configuration changes and data security.
Refer Compliance tab help page to get help on this topic.
Refer Firewall security audit and configuration analysis page for more details about firewall security audit and configuration analysis report.
To know more about security standards compliance, refer Firewall Security Standards page.
Featured links
Manage your firewall rules for optimum performance. Anomaly free, properly ordered rules make your firewall secured. Audit the firewall security and manage the rule/config changes to strengthen the security.
Get a slew of security and traffic reports to asses the network security posture. Analyze the reports and take measures to prevent future security incidents. Monitor the Internet usage of enterprise users.
Unlock the wealth of network security information hidden in the firewall logs. Analyze the logs to find the security threats faced by the network. Also, get the Internet traffic pattern for capacity planning.
With live bandwidth monitoring, you can identify the abnormal sudden shhot up of bandwidth use. Take remedial measures to contain the sudden surge in bandwidth consumption.
Take instant remedial actions, when you get notified in real-time for network security incidents. Check and restrict Internet usage if banwidth exceeds specified threshold.
MSSPs can host multiple tenants, with exclusive segmented and secured access to their respective data. Scalable to address their needs. Manages firewalls deployed around the globe.