Firewall monitoring
- Firewall log monitoring
- Firewall rule monitoring
- Firewall configuration monitoring
- Firewall alert monitoring
Why is firewall monitoring important?
A firewall is a piece of hardware or software that controls what enters and exits a network. The efficiency of a firewall depends on a couple of things:
- The firewall’s processing speed
- The rules governing the firewall
However, the problem is that security admins face the challenge of balancing speed and security. Given these constraints, hackers primarily exploit the following loopholes to get into systems.
- Old or unused firewall rules
- Errors caused by internal users
- Unencrypted data
- Shadow IT
Most firewalls have a "deny all" rule, but for all practical purposes this rule can't stay on top. Rules have to be written according to specific network requirements. For example, if a company allows their employees to work from home, employees must be allowed to access the company's server through a VPN, and that means rewriting the firewall rules.
Firewalls typically have rules for inbound and outbound traffic. When deciding whether certain information is allowed to be sent and received or should be discarded, the firewall bases its decision on the rules that have been created.
This filtering stops most malicious information from reaching computers. However, network dynamics can change and destinations that are safe now might become malicious in the future. Hackers could infiltrate your network if you simply set the rules and forget about your firewall entirely.
Human error plays a critical role in security breaches, and trusted but unaware internal users are to blame. Cybercriminals are experts at hijacking identities by exploiting human error. They can get into an employee's system through malware or phishing attacks; some hackers steal credentials by gleaning data from social networks.
Aside from unintentional internal threats, malicious employees who intend to steal or damage corporate resources are also a great risk to network security. Even so, the biggest risk of all often comes from well-meaning IT admins, whose complete access to company infrastructure can turn a small mistake into a catastrophe.
The network traffic that passes through a host’s network interface usually contains username-password pairs, as well as other system information that would be useful to a hacker. In a network where data is transmitted without encryption, an intruder with physical access to the network can plug in a packet analyzer—also known as a packet sniffer—to monitor network traffic and obtain necessary information to access other hosts in the network.
Shadow IT refers to information technology projects that are managed outside the IT department. Most shadow IT services use the cloud to run below the IT department's radar. Although shadow IT might present short-term gains, it presents a serious security threat to the network.
In conclusion, hackers will look for any openings in the firewall and will exploit any vulnerabilities that exist. This is why it’s important to use a firewall monitoring software which continuously monitors not only your firewall but also everything related to your firewall.
How Firewall Analyzer acts as a firewall monitoring tool
Firewall monitoring goes over all the internal users, rules, data passing through interfaces, shadow IT-enabled cloud services, and nearly anything else that has a touch point with the firewall(Thus acting as a firewall monitor tool). Firewall Analyzer offers the following monitoring reports to keep your firewall secure.
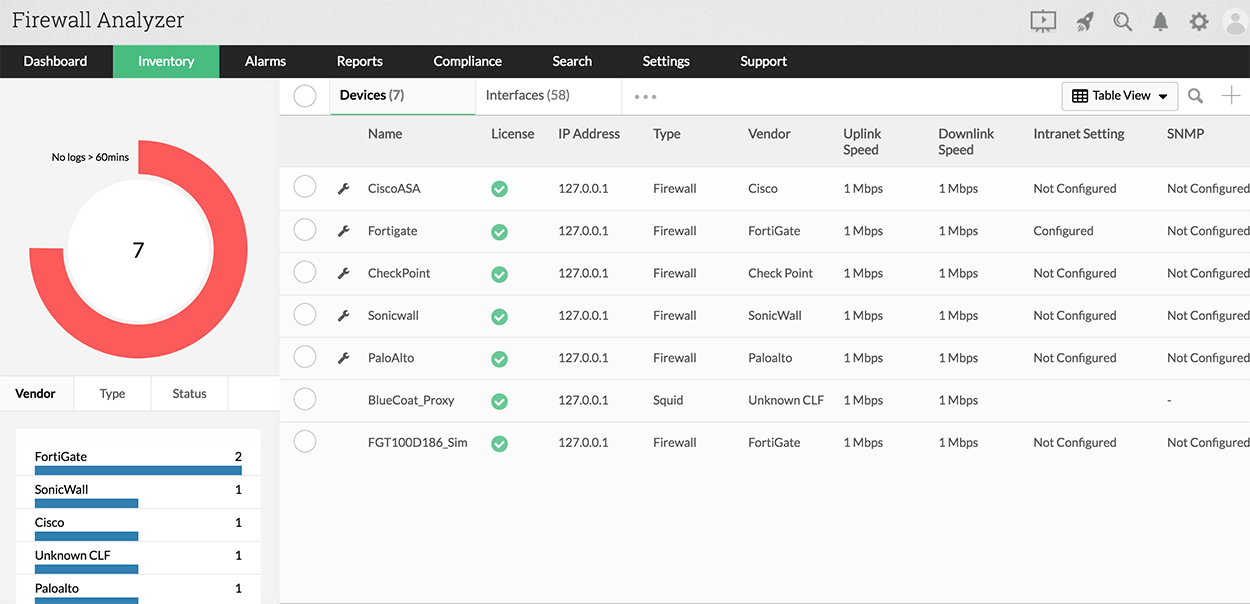
- Firewall Analyzer shows the activity status of all configured firewall devices. It also displays the vendor name, device type, and status of the firewall device.
You also get a complete picture of everything that’s happening on the firewall. Firewall Analyzer provides in-depth reports on:
- Firewall devices, including high-level summaries.
- The traffic in and out of a firewall device (Firewall bandwidth monitor).
- The top 10 host IPs, destination IPs, protocol groups, internal servers, external sites, and conversations.
- Traffic accessing allowed sites and attempting to access denied sites.
- The applications running on devices connected to the firewall (Firewall monitor).
- Firewall rule usage trends, including top allowed rules and top denied rules triggered.
- Security stats, attacks (including DDoS and virus attacks), denied host IPs, denied destination IPs, and denied user logons.
- The VPNs connected to a firewall device.
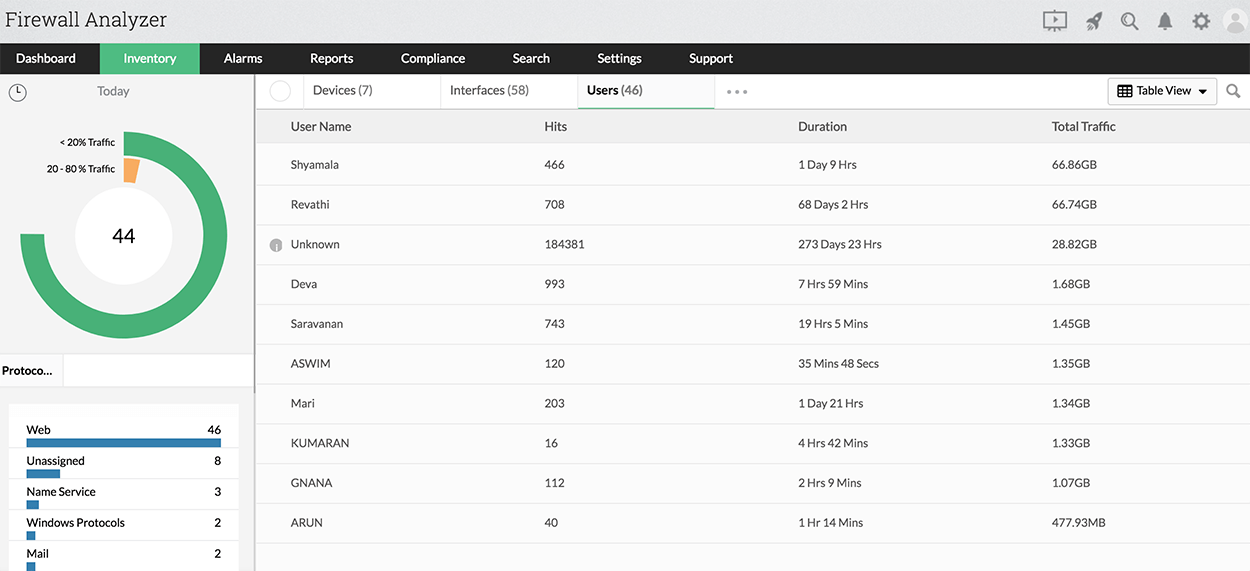
You also get a comprehensive view of all the users generating traffic via the firewall devices (Thus enabling efficient firewall network monitoring). Firewall Analyzer offers in-depth reports on:
- Total bandwidth consumed by users.
- Top 10 applications used by users.
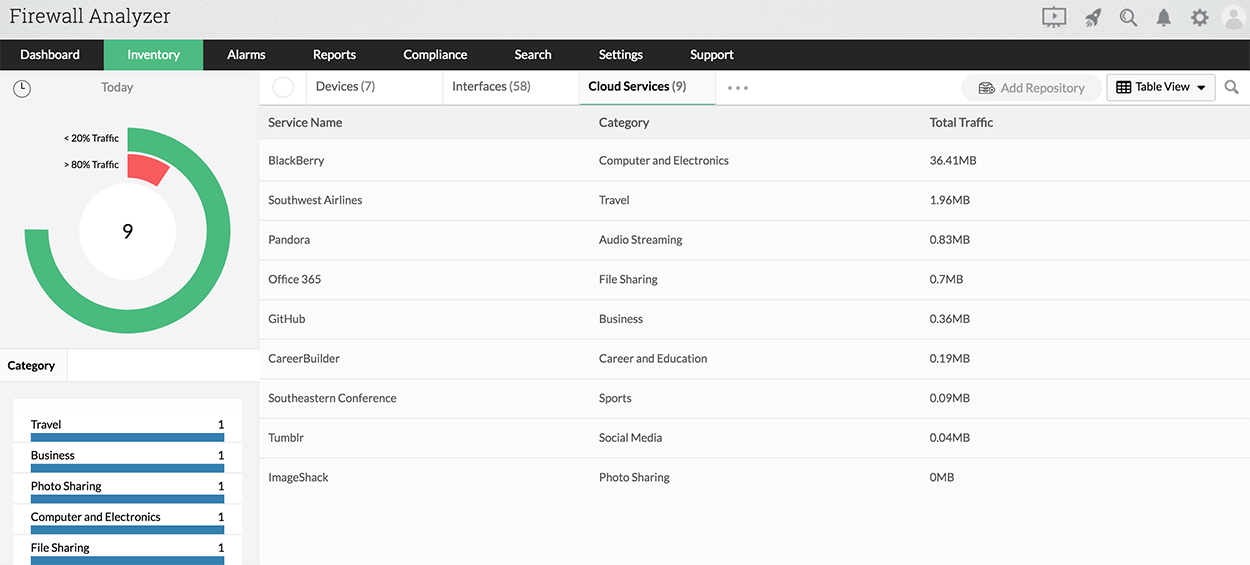
- Top 10 cloud services used by users.
- Top 10 rules used by users.
- URLs allowed for users.
- URLs blocked for users.
- Conversations users have participated in.
- Protocol and URL details for users.
- VPN details of any specific user.
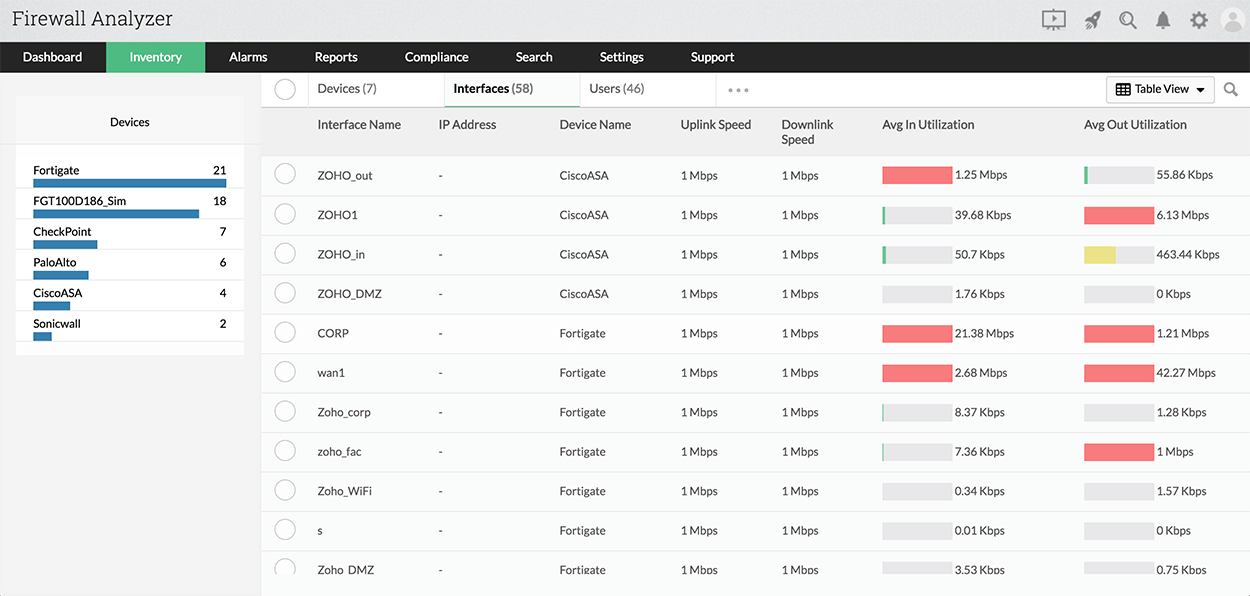
You also get live traffic reports on all the interfaces under the configured firewall devices.
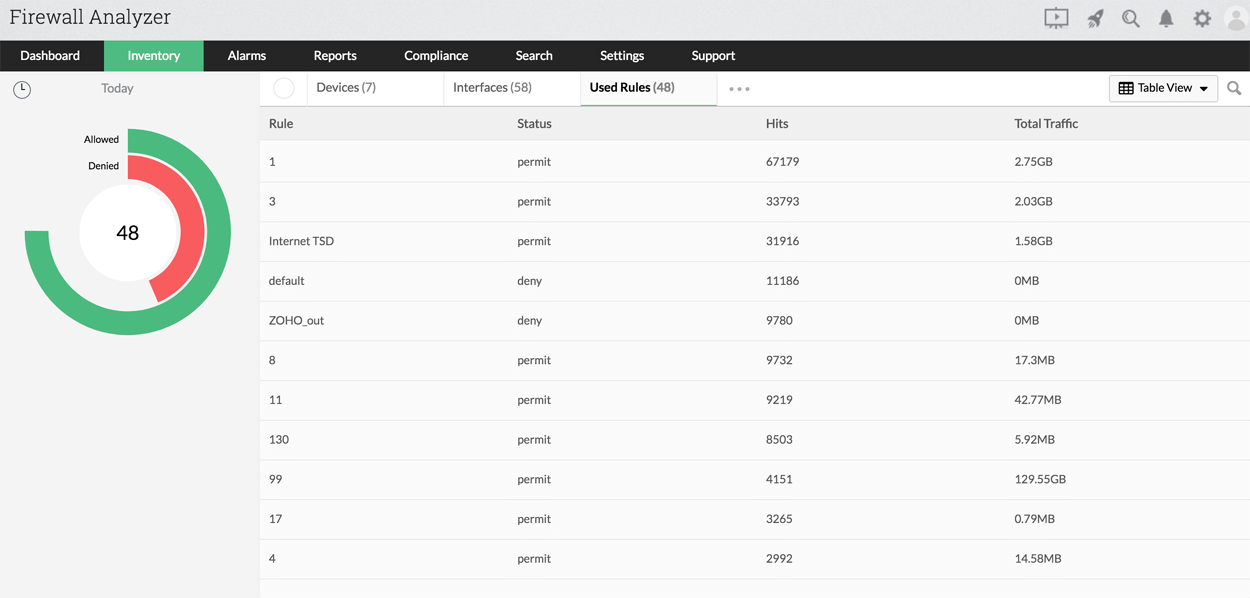
You get a complete picture of all the allowed rules, denied rules, and used rules under the firewall devices. Firewall Analyzer also comes with in-depth reports on:
- Rule usage and rule descriptions.
- Usage trends for a specific rule.
Firewall Analyzer reports on:
- Bandwidth usage.
- Connected users, hosts, and applications.
With these detailed real-time reports, you can not only monitor firewall traffic but also monitor firewall activity in depth using firewall logs on your network 24x7.
Featured links
Thank you for your feedback!