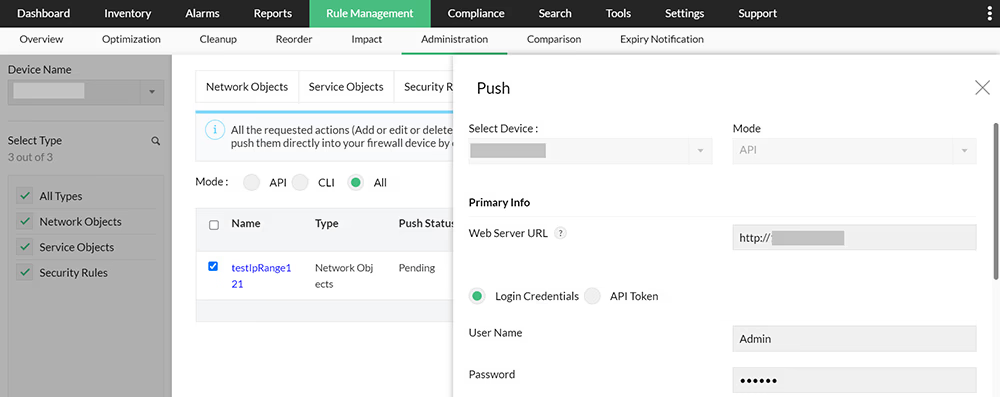
Firewall Analyzer is a firewall administration software, that helps in administering firewall rules and policies into multiple firewalls. The firewall rule automation ensures that firewall rules are pushed into the device seamlessly, avoiding errors and oversight. This firewall administration tool is capable of making the following changes.
Refer the 'Firewall Rule Administration' page for more details.
Firewall Analyzer is an efficient firewall rule and policy management tool that helps you gain visibility on all firewall rules, optimize firewall rules, and remove rule anomalies. It provides rule management reports for most major firewall devicesincluding Cisco, FortiGate, WatchGuard, and Check Point.
Firewall Analyzer is policy analysis and configuration reporting software that helps with firewall security policy management (Firewall Management). It offers API or CLI-based rule management, and helps security admins track policy changes, optimize firewall performance, and meet compliance standards. Below are the key features of Firewall Analyzer that help security admins manage firewall policies.
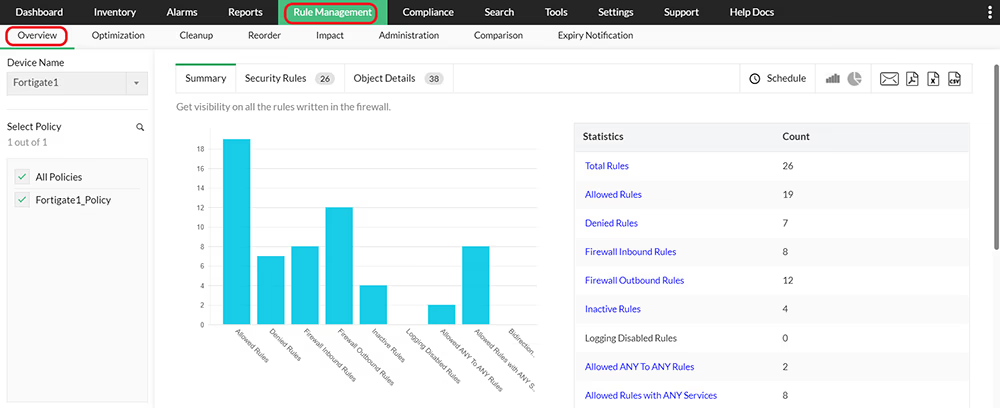
Manually documenting all firewall rules and reviewing them on a regular basis is a time-consuming task. To solve this issue, Firewall Analyzer fetches the entire set of rules written in the firewall. To simplify review, you can also filter rules based on the following criteria:
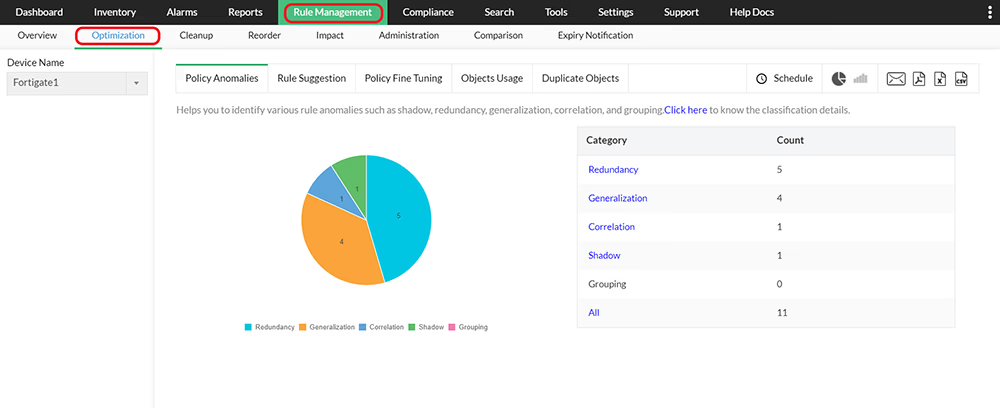
Firewall Analyzer helps identify redundancy, generalization, correlation, and grouping anomalies, as well as shadow rules, for faster firewall rule analysis. These anomalies negatively impact firewall performance, and removing them helps optimize firewall rule efficiency.
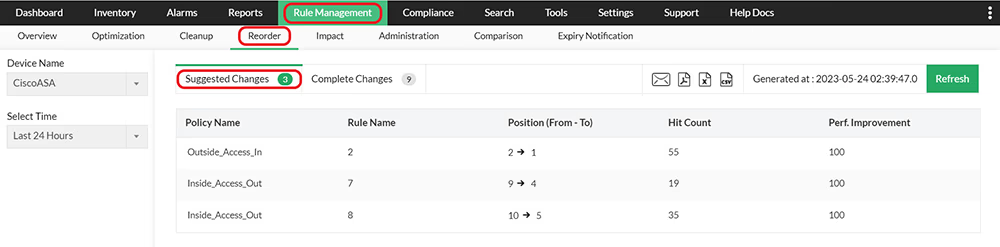
Firewall Analyzer analyzes various rule interactions and anomalies to provide suggestions on rule position. By correlating the number of rule hits with rule complexity and anomalies, it can estimate the performance improvement for a suggested change. With the help of this report, you get an understanding of how to organize firewall rules to maximize speed.
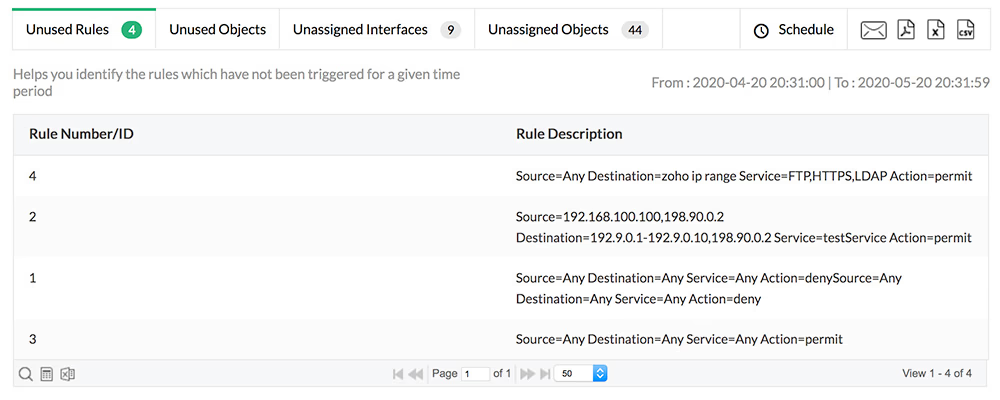
Firewall Analyzer provides a detailed list of all unused firewall rules, objects, and interfaces. The Rule Cleanup feature provides a high-level overview of which unused rules, objects, and interfaces can be removed or deactivated.
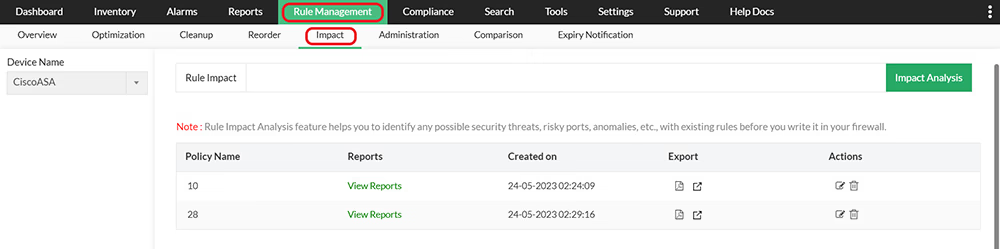
Firewall Analyzer's Rule Impact feature lets you perform in-depth impact analysis for a proposed new rule, allowing you to determine if the new rule is going to impact the existing rule set negatively. With these reports, you can identify threats, understand risks, remove anomalies, and optimize the proposed new rule.
Firewall rule management is the process of periodically reviewing and optimizing firewall rules. This process involves the following:
Firewalls provide protection from external threats by shielding your network and preventing malicious internet traffic. With a stable set of rules and policies in place, you can keep your company safe from hackers. But keeping track of firewall security policies is a challenge in itself; small organizations can have hundreds of rules to manage, while larger ones may have thousands. Many of these rules date back more than five to ten years, and there's often a lack of continuity in defining new rules as most are inherited from their predecessors. This mismanagement of rules severely affects firewall performance, leaving your network vulnerable to security breaches.
Download a 30-day free trialand secure your network now!
Refer Configure Firewall Rulespage to know how to configure firewall rules.
Featured links
Get a slew of security and traffic reports to asses the network security posture. Analyze the reports and take measures to prevent future security incidents. Monitor the Internet usage of enterprise users.
Integrated compliance management system automates your firewall compliance audits. Ready made reports available for the major regulatory mandates such as PCI-DSS, ISO 27001, NIST, NERC-CIP, and SANS.
Unlock the wealth of network security information hidden in the firewall logs. Analyze the logs to find the security threats faced by the network. Also, get the Internet traffic pattern for capacity planning.
With live bandwidth monitoring, you can identify the abnormal sudden shhot up of bandwidth use. Take remedial measures to contain the sudden surge in bandwidth consumption.
Take instant remedial actions, when you get notified in real-time for network security incidents. Check and restrict Internet usage if banwidth exceeds specified threshold.
MSSPs can host multiple tenants, with exclusive segmented and secured access to their respective data. Scalable to address their needs. Manages firewalls deployed around the globe.