Firewall Rule Monitoring
Firewall Analyzer monitors and reports the Firewall rules / policies / ACLs usage. Firewall Analyzer fetches all the rules of the Firewalls and provides rule wise usage reports. With the help of the reports, you can analyze the usage and effectiveness of the Firewall rules and fine tune the Firewall rules for optimal performance.
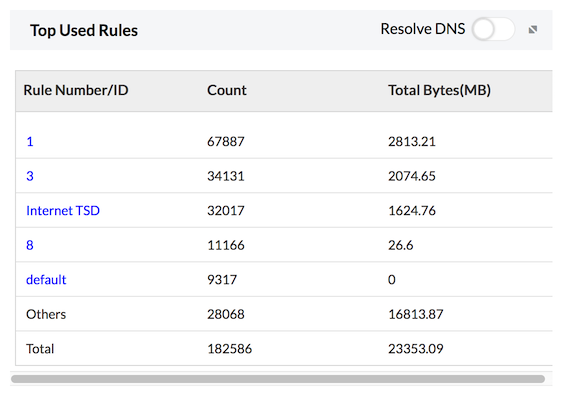
Top Used Rules
Top Used Rules report provides the list of rules/ policies/ ACLs used by the traffic of your enterprise network through the firewall. This list enables you to ascertain the Firewall rules which were heavily used and modify the heavily used rules to use them optimally. The number of events triggered the rule are listed for the specific rule.
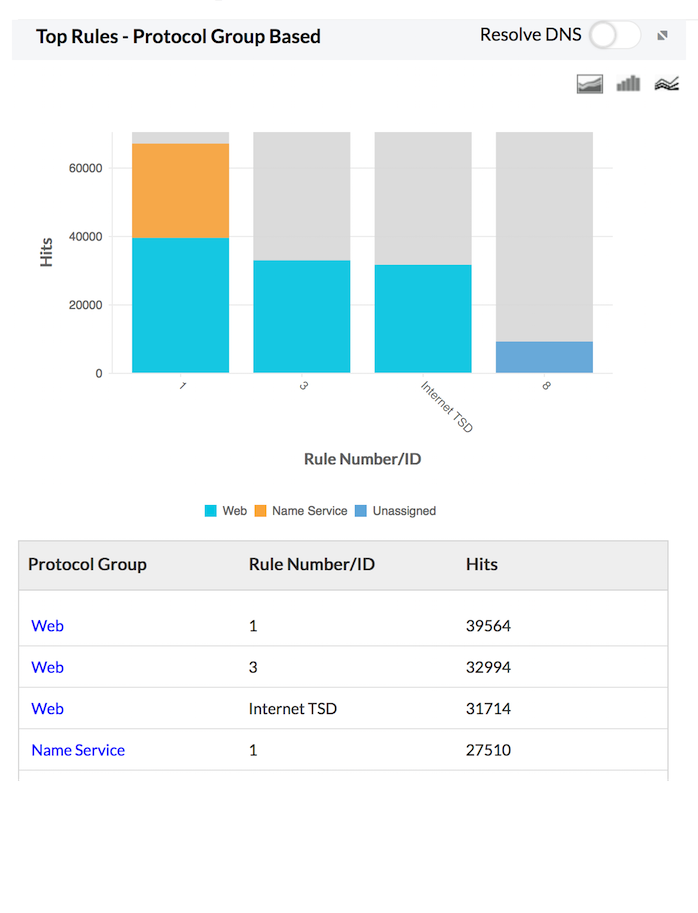
Top Rules - Protocol group based
Top Rules - Protocol Group Based report provides the number of events triggered for each rule based on protocol groups. The report is displayed as graphs and listed in table. This will give you an idea of the rules being used or over-used by each protocol group.
Request Demo
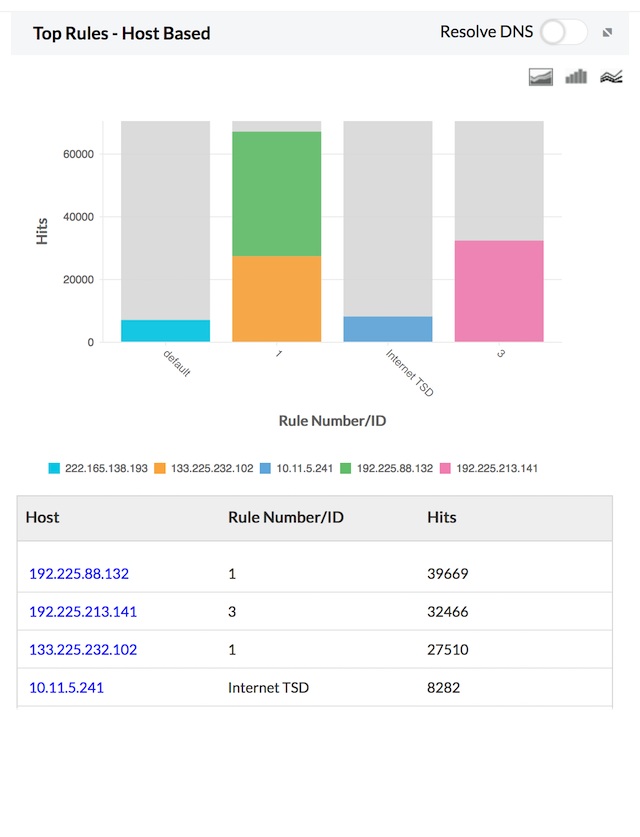
Top Rules - Host based
Top Rules - Host Based report provides the number of events triggered for each rule based on protocol groups. The report is displayed as graphs and listed in table. This will give you an idea of the rules being used or over-used by each protocol group.
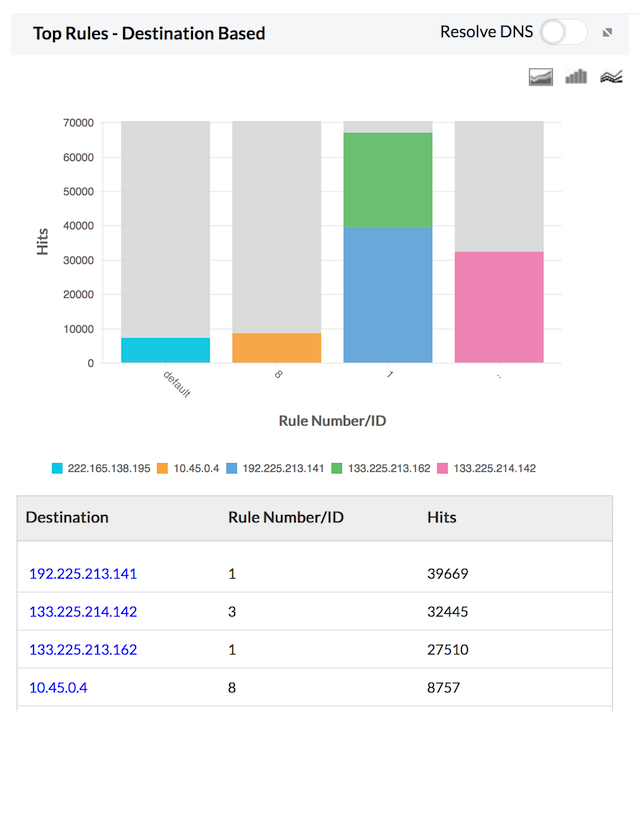
Top Rules - Destination based
Top Rules - Destination Based report provides the number of events triggered each rule based on destinations. The report is displayed as graphs and listed in table. This will give you an idea of the rules being used or over-used by each destination.
Firewall Unused Rules Monitoring
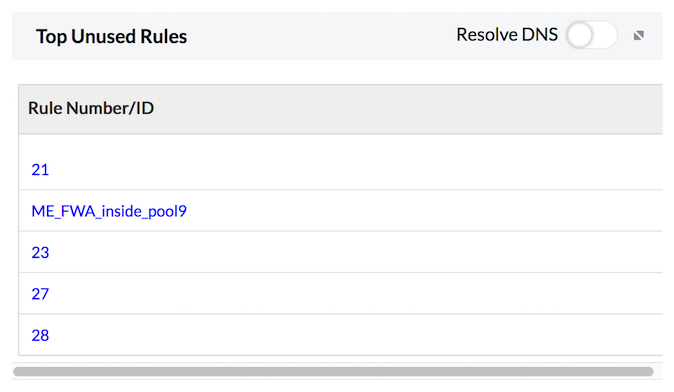
Top Unused Rules
Top Unused Rules report provides the list of rules/ policies/ ACLs not used by the traffic of your enterprise network through the firewall. This list enables you to modify or remove the unused rules or create new rules to use them optimally.
Refer Configure Firewall Rules page to know how to configure firewall rules.
Refer the following help documents:
Featured links
Firewall Reports
Get a slew of security and traffic reports to asses the network security posture. Analyze the reports and take measures to prevent future security incidents. Monitor the Internet usage of enterprise users.
Firewall Compliance Management
Integrated compliance management system automates your firewall compliance audits. Ready made reports available for the major regulatory mandates such as PCI-DSS, ISO 27001, NIST, NERC-CIP, and SANS.
Firewall Log Management
Unlock the wealth of network security information hidden in the firewall logs. Analyze the logs to find the security threats faced by the network. Also, get the Internet traffic pattern for capacity planning.
Real-time Bandwidth Monitoring
With live bandwidth monitoring, you can identify the abnormal sudden shhot up of bandwidth use. Take remedial measures to contain the sudden surge in bandwidth consumption.
Firewall Alerts
Take instant remedial actions, when you get notified in real-time for network security incidents. Check and restrict Internet usage if banwidth exceeds specified threshold.
Manage Firewall Service
MSSPs can host multiple tenants, with exclusive segmented and secured access to their respective data. Scalable to address their needs. Manages firewalls deployed around the globe.
Thank you for your feedback!