In a Firewall device, there could be numerous rules/access-list defined to secure the network from external attacks. Out of the rules/access-list configured, there could be certain rules which would be most used and certain which are least used or never used. Firewall Analyzer captures the most used rules in the Top Used Rules as they would be available in the logs generated by Firewall. But, to get the Unused Rules, one needs to configure the Firewall Analyzer to fetch the complete rules from the device. Once, Firewall Analyzer fetches the complete rules configured in the Firewall, it can provide the Unused Rules view.
To view Unused Firewall Rules, configure the Firewall Analyzer by following the steps given below:
Device Rule
After entering and saving the Device Credential values through the Firewall Analyzer GUI, the device, with details to fetch rules, is listed in the Device Rule table.
The details of the columns of the Device Rule table are:
| Device Rule | Description |
|---|---|
| Status | The status of fetching device rules/access control of the Firewall device |
| Devices Name | The names of the devices for which the rules will be fetched |
| Virtual FWs | For multi (vdom/context) Firewalls, this will display the number of vdoms/contexts associated to this specific device rule. Clicking on the count will show the details of the vdoms/contexts individually. Refer the screen shot below. |
| Security Audit | The configuration changes of the Firewall devices are reported. The report is available on clicking the link and the link text shows the time the configuration change report was generated. You can instantly fetch the current configuration change report by clicking the icon. |
| Config Changes | The configuration changes of the Firewall devices are reported. The report is available on clicking the link and the link text shows the time the configuration change report was generated. You can instantly fetch the current configuration change report by clicking the icon. |
| Last Update On | The time when the rules of the device were updated last. |
| On Demand |
|
| Status | Enable, disable notification |
| Edit | An icon to edit the details of the rules fetching info of the device. Click icon to edit the device info. |
Virtual Firewalls
Note: Click here to know more about on how to add Bulk Device Rules in Firewall Analyzer
In addition to individual device selection, Firewall Analyzer also allows bulk rule addition using Device Groups.
To add bulk device rules using a device group:
All firewall devices that belong to the selected device group(s) will be automatically associated with the chosen credential profile.
Select the option as per your requirement.
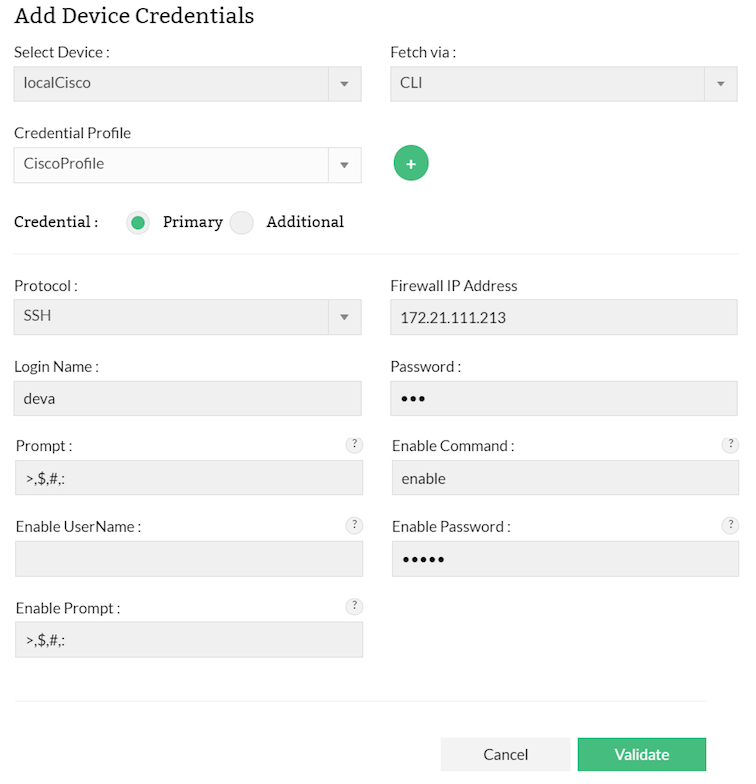
The Credentials tab
You can configure the individual device credentials to fetch the rules and configuration from the device or you can create a common profile of device credential which can be used for a group of devices to fetch rules.
| Note: |
Fetching the rules directly from the device is supported for the following devices only:
For the rest of the devices, please use the Fetch Rules/Config > From File option. |
Primary - deal with parameters that are necessary to establish communication with the device. Details such as Login Name, Password, Prompt, Enable UserName, Enable Password and Enable Prompt are classified as basic details.
|
Device Info |
Description |
|---|---|
| Protocol | Select the protocol (SSH, Telnet, SSH TFTP, Tlenet TFTP) in the Protocol drop down list. |
| Firewall IP Address | Enter IP address of the firewal for credential configure. See Note below. |
|
Login Name |
While establishing connection with a device, if the device asks for a Login Name, set a value for this parameter. This parameter is Optional. |
|
Password |
To set the Password for accessing the device. |
|
Prompt |
The prompt that appears after successful login. |
| Enable Command | The command to fetch the rule and configurations |
|
Enable UserName |
When entering into privileged mode, some devices require UserName to be entered. Provide the username if prompted; otherwise leave this field empty. |
|
Enable Password |
This is for entering into privileged mode to perform configuration operations like backup/upload. This parameter is mandatory. |
| Enable Prompt |
This is the prompt that will appear after going into enable mode. |
| Note: |
Both Primary and Additional credentials (Login Name and Password) of the Firewalls are encrypted and stored in the Firewall Analyzer. |
Additional - certain parameters usually take standard values. All such parameters have been classified under 'Secondary Info'. Port, login prompt, enable user prompt, password prompt, enable password prompt values are usually assigned with certain Standard Values by default. Such standard values have been filled for these parameters. Most of the devices would work well with these values and you need not edit these details unless you want to provide different set of details.
All the parameters are usually assigned with certain Standard Values by default. Such standard values have been filled for these parameters. Most of the devices would work well with these values and you need not edit these details unless you want to provide different set of details.
|
Device Info |
Description |
|---|---|
| Port (Telnet/SSH) |
Port number of Telnet/SSH - 23 (for Telnet) and 22 (for SSH) by default. |
|
Login Prompt |
The text/symbol that appears on the console to get the typed login name is referred as login prompt. For example, Login: |
|
Password Prompt |
The text displayed on the console when asking for password. For example, Password: |
|
Enable User Prompt |
The text displayed on the console when asking for Enable UserName. For example, UserName: |
|
Enable Password Prompt |
The text displayed on the console when asking for password. For example, Password: |
| Banner Prompt | The prompt that appears for the banner |
| Banner Input | The banner message |
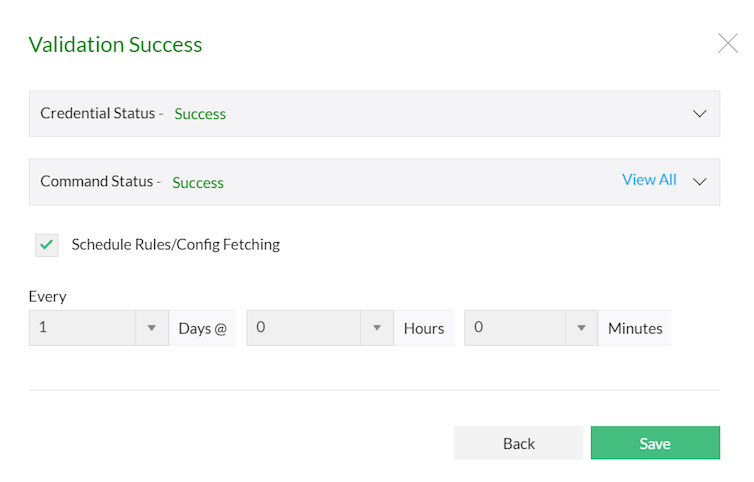
| Note: |
Generating Change Management Report is supported for the following devices:
|
| Note: |
Getting Rules/ Configuration Information from the individual virtual firewalls (vdom/context)
|
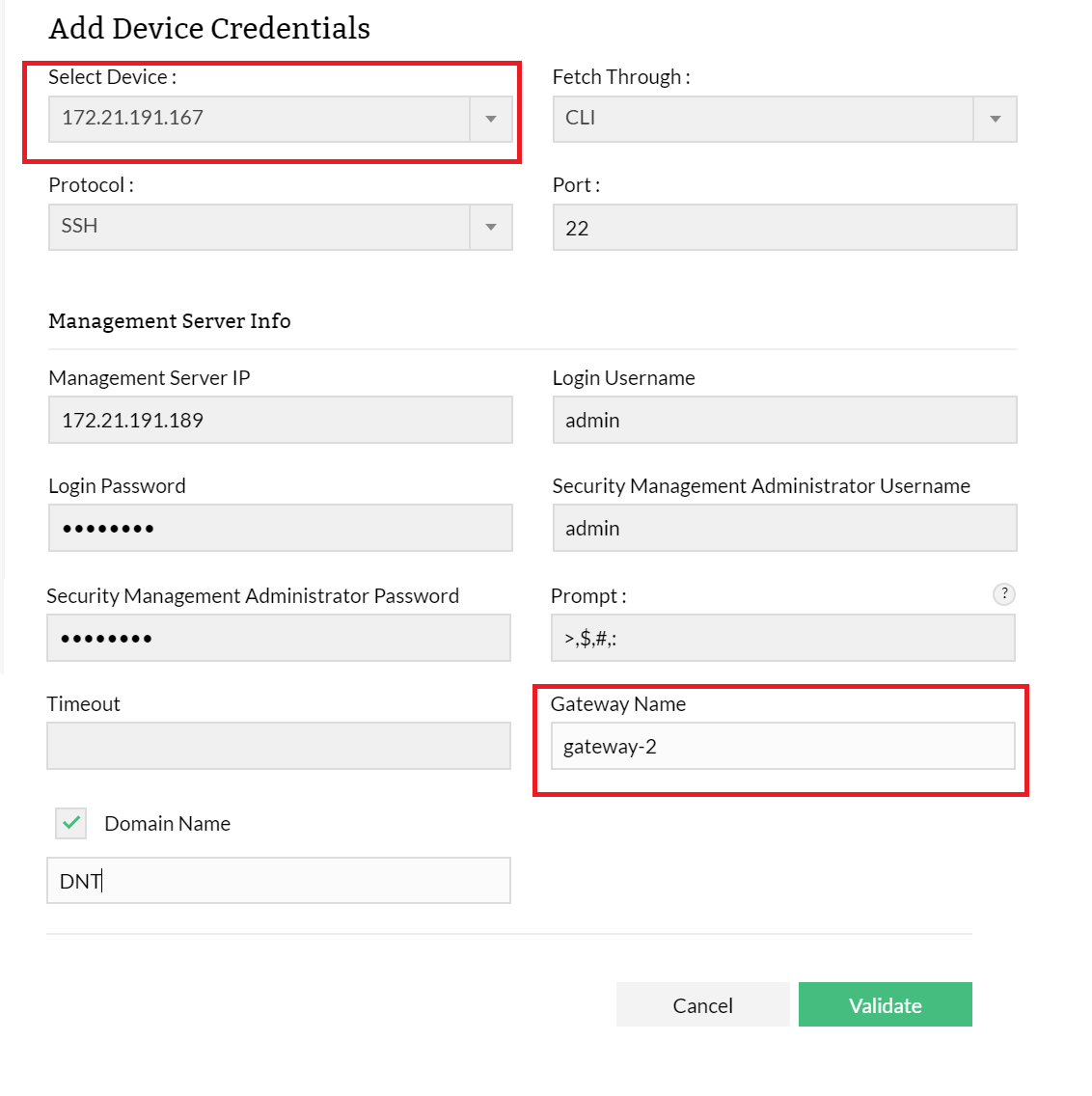
Select the option as CLI.
|
Device Info |
Description |
|---|---|
| Select Device |
Select the IP address or device name of the Check Point firewall device. |
| Fetch Through | Select CLI from the CLI, API, File drop down list. |
| Protocol | Select the SSH protocol (SSH, Telnet) in the Protocol drop down list. |
| Port | Select port 22 from the 22, 23 drop down list. |
|
Management Server Info |
Description |
|---|---|
| Management Server IP | Enter IP address of the Check Point firewal Management Server. |
|
Login Username |
While establishing connection with a device, if the device asks for a Login Username, enter the Username of the device. |
|
Login Password |
Enter the Login Password for accessing the device. |
| Security Management Administrator Username | While establishing connection with a Management Server of the Check Point device, if the device asks for a Security Management Administrator Username, enter the login name of the device. |
| Security Management Administrator Password | Enter the Security Management Administrator Password. |
|
Prompt |
The prompt that appears after successful login. |
| Timeout | The time allowed to login to the device successfully. |
|
Gateway Name |
Enter the Gateway Name. |
|
Domain Name |
Select the Domain Name check box. Enter the domain name. |



Only for Check Point Firewall
| Note: |
Rule File
Configuration File
|
| Note: |
Getting Rules/ Configuration Information from the individual virtual Firewalls (virtual domain) If you want to fetch the rules/configurations from the individual virtual Firewalls (virtual domain) separately, select the option 'Display Virtual Domains in the below resources list.' in Associate Profiles to Devices page. It lists both the virtual Firewalls (virtual domain) and the physical devices in the Select Device drop down list. |
| Note: |
Trouble Shooting: If the following message appears in the Compliance Reports field, enable Nipper. 'Unable to generate compliance report. Reason: failed to locate nipper. Click here to enable it' |
Primary - deal with parameters that are necessary to establish communication with the device. Details such as Login Name, Password, Prompt, Enable UserName, Enable Password and Enable Prompt are classified as basic details.
Primary Info
|
Device Info |
Description |
|---|---|
|
Web Server URL |
URL of the API management server of the firewall device. Example: https://192.168.90.10:4444 (protocol://firewallManagementIp:port) |
|
User Name |
Firewall web login username (We recommend admin credentials) |
| Password | Firewall web login password (We recommend admin credentials) |
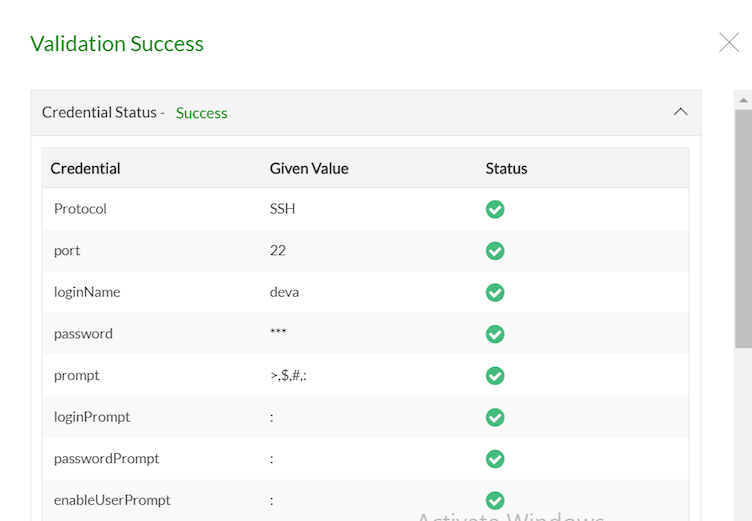
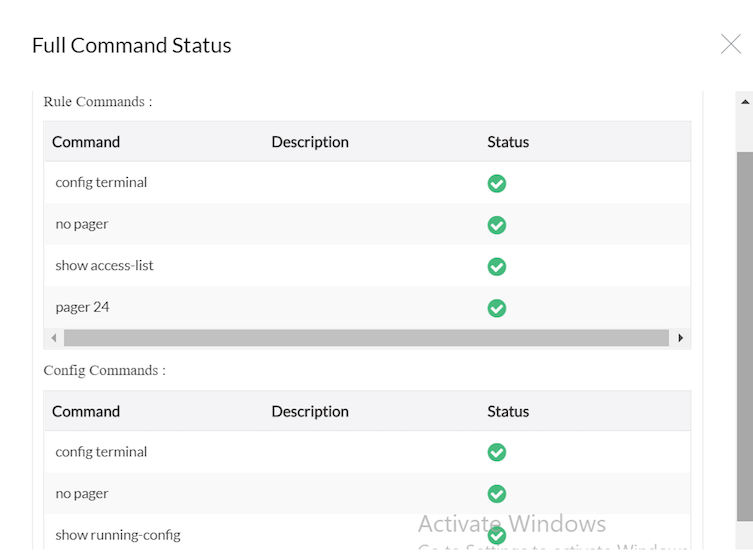
Device credentials and commands are validated and the results are displayed. Refer screen shots in fetch using CLI section.
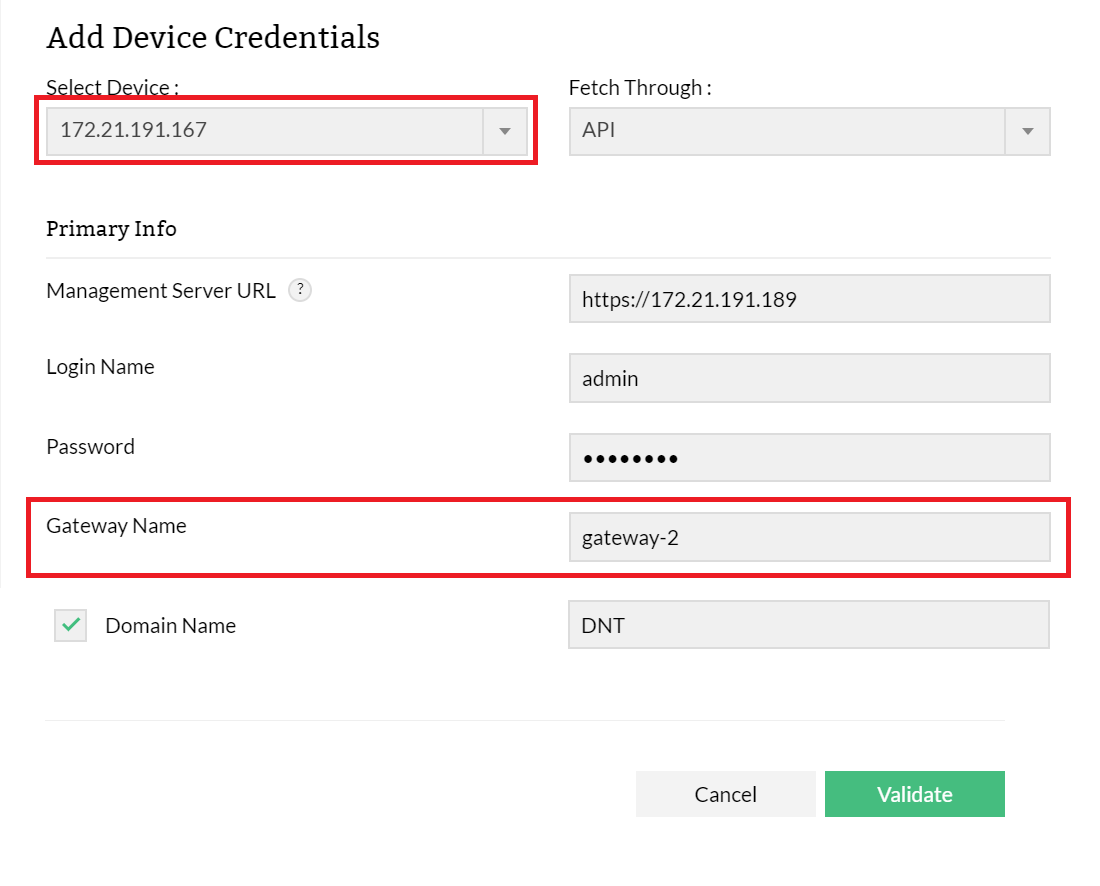
Select the option as API.
Primary Info - deal with parameters that are necessary to establish communication with the device.
Primary Info
|
Device Info |
Description |
|---|---|
|
Management Server URL |
URL of the API management server of the firewall device. Example: https://192.168.90.10:4444 (protocol://firewallManagementIp:port) |
|
Login Name |
Firewall web login username (We recommend admin credentials) |
| Password | Firewall web login password (We recommend admin credentials) |
| Gateway Name | Enter the Gateway Name. Check Point firewall version 80.10 or later with CEF log format cases, we have only option to get IP address value from syslog, in these cases using IP address we can't findout the gateway specific rules, so must provide Gateway Name value to get gateway specific rules. |
| Domain Name | Select the Domain Name check box. Enter the domain name. |
Device credentials and commands are validated and the results are displayed. Refer screen shots in fetch using CLI section.
Procedure to enable SSH option for Stormshield devices:
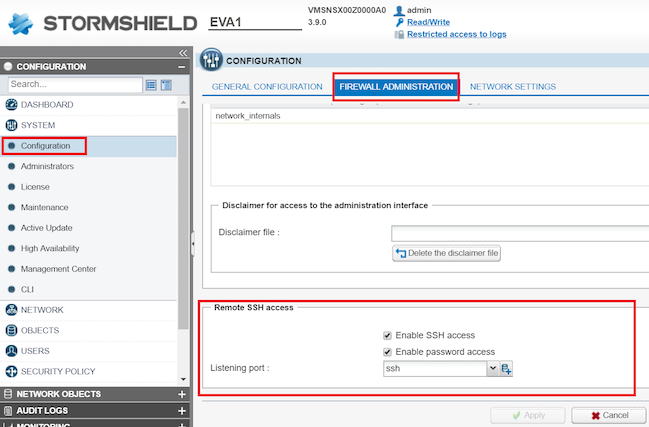
Supported version: Web API option available for Check Point R-80.10 or higher versions.
Refer screenshot below:
Open firewall command prompt (CLI), execute the below commands:
In the Compliance Report field, the following message appears: 'Unable to generate compliance report. Reason: Failed to locate Nipper. Click here to enable it'. What should I do?
Supported Platform:
Prerequisite:
The GNU/Linux platform requires Qt 4.5 to be installed. Your package manager system should automatically install this for you.
Steps:
After performing the above steps, go to Setting > Device Rule > Add Device Info, the option to generate compliance report for the device will be enabled.
The Device Group feature is used in Rule Management to generate Firewall Reports for a specific set of firewall devices. You can create a device group that includes devices from multiple vendors (cross-vendor devices are supported). However, if you wish to use the Rule Administration feature, it is limited to devices from a single vendor only. Cross-vendor device selection is not supported for Rule Administration.

Now your Device Group has been created.
Note:Additionally, you can select Device Groups to view Reports under Rule Management
Thank you for your feedback!