The actions of insiders can either purposely or accidentally lead to a breach, so it is extremely critical to monitor your network for insider threats and remediate threats once identified (Insider threat detection). Organizations need a smart insider threat detection tool that can monitor and alert on various traffic and security anomalies.
Firewall Analyzer is an insider threat detection software that generates security and traffic reports to help identify internal threats to your network. Apart from generating reports, Firewall Analyzer can also trigger and record alerts for security and traffic anomalies. The following capabilities help IT admins identify and remediate insider threats.
The internet usage of employees can impact both the security and traffic infrastructure of a company. Employees consuming a large amount of data for personal use can not only disrupt bandwidth availability, but also result in malware and other security breaches, which threatens the entire network infrastructure.
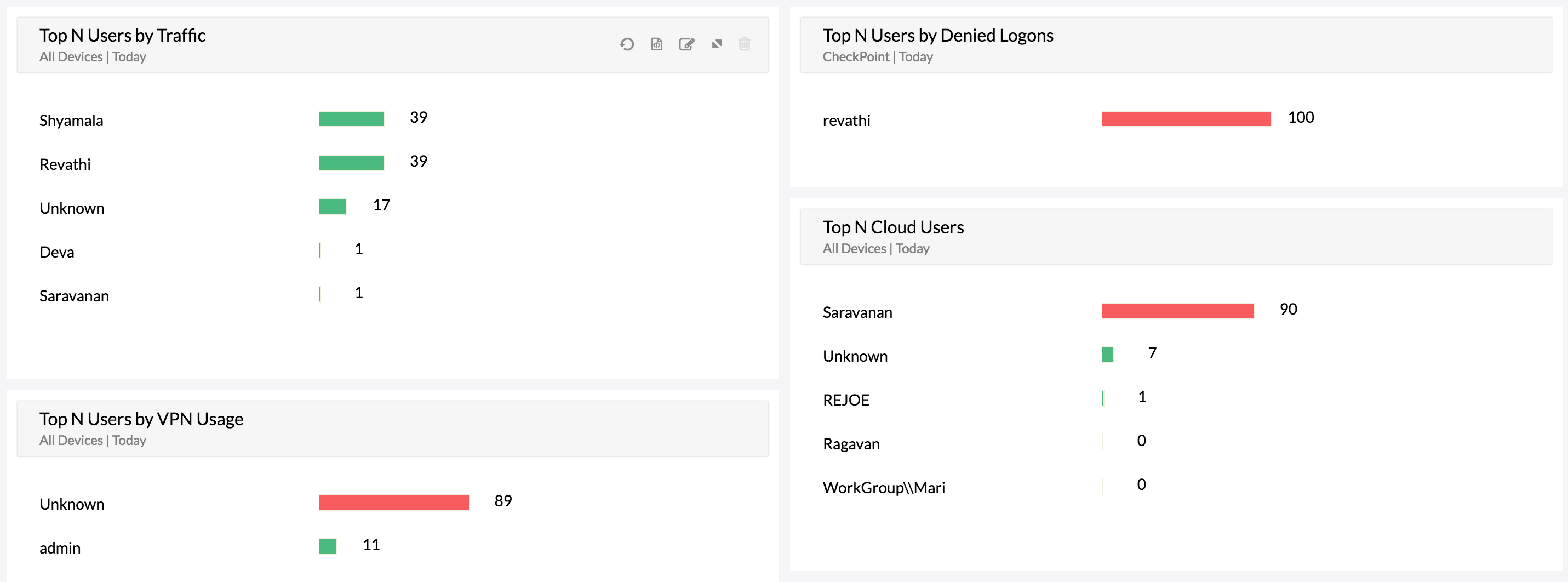
Firewall Analyzer monitors internal threats and provides you with the following insights:
With these insights, you can not only identify insider threats, but also remediate them by fine-tuning your firewall policies to restrict bandwidth guzzling websites or malicious ones.
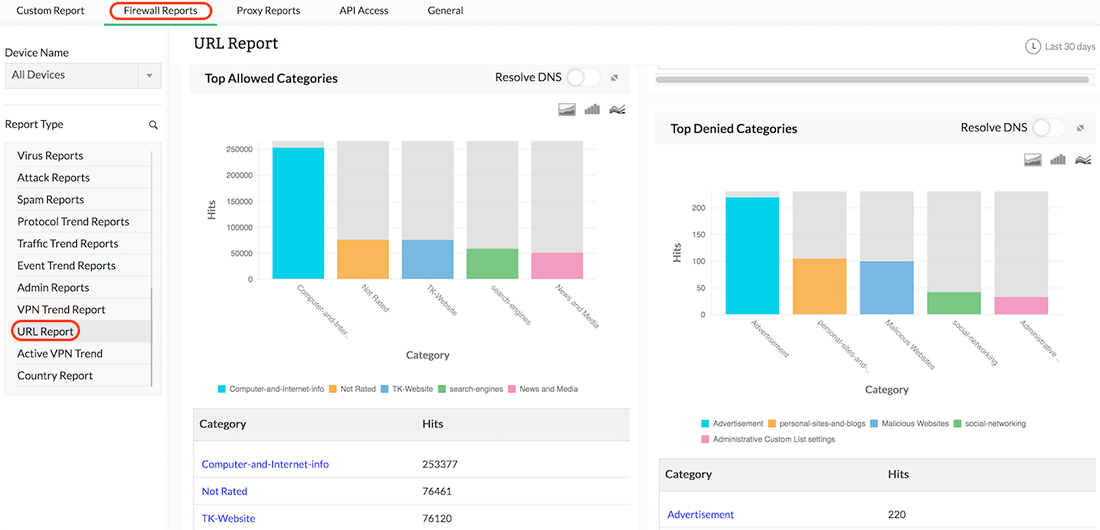
Firewall Analyzer monitors and records the URLs visited by employees and displays them as part of its web usage reports. These reports not only provide the bandwidth consumption for a specific URL, but also list the denied URLs employees have attempted to access. With this report, you can clearly identify URLs that are causing network issues and then push rules to block problematic URLswith Firewall Analyzer’s rule administration feature.
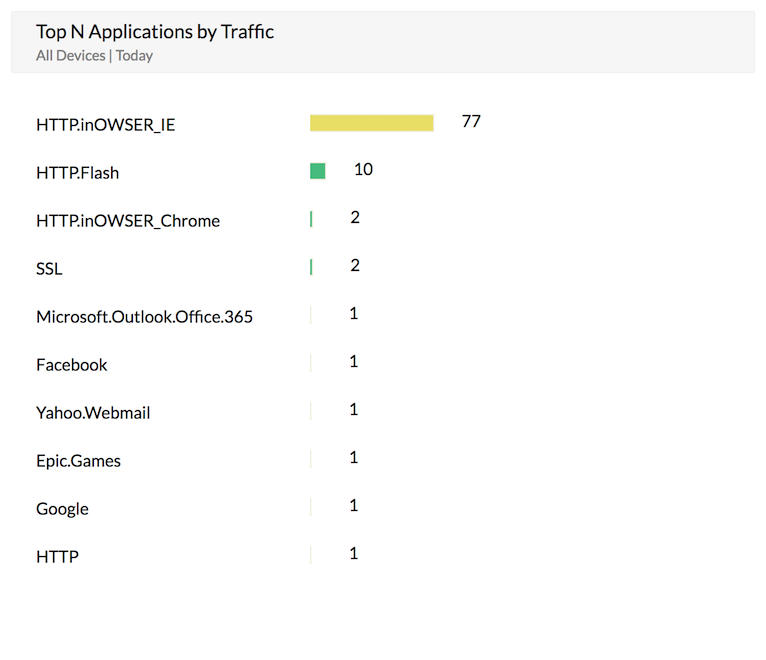
Shadow IT is not a new phenomenon, but the surge in the usage of third-party cloud applications has fueled a new wave of security complications. Most employees don't consider themselves an insider threat because, for the most part, they're just trying to improve their productivity. However, by signing up for cloud services and interacting with their phones using consumable APIs, employees may enable hackers to tap into the company network or extract sensitive data without raising suspicion.
Firewall Analyzer monitors and generates reports on all applications accessed through firewall devices. With these reports, security administrators can easily identify suspicious applications and also generate alerts when employees try to access a specific application.
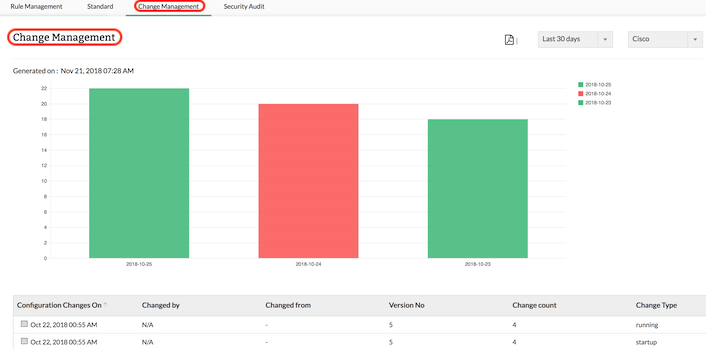
Firewalls are extremely critical for network security, and the heart of any firewall’s performance is its configuration. If your firewall configuration is not properly monitored and managed, your network may be left vulnerable to attacks. Firewall Analyzer fetches firewall configurations using the CLI or API from your firewall device (Threat detection firewall) and enables you to keep an eye on the changes being made to your network security infrastructure.
Administrators may commit an unintentional error or carry out an improper change while acting on a firewall configuration change request, leaving room for breaches.Firewall Analyzer ensures that all the configurations and subsequent changes made in your firewall device are captured periodically and stored in the database. The configuration change management reports help you find out precisely who made what changes to the firewall configuration, when, and why.
Setting bandwidth-based triggers and security-based triggers (Insider threat detection solutions) can be useful in identifying internal threats. With Firewall Analyzer’s alarm management feature, you can set traffic and security triggers . Once a firewall alert is triggered, the alarm can be sent directly to your email or phone (as anSMS). You can also further investigate and identify the source and type of threats to your network. Alarms are also displayed in Firewall Analyzer's UI.
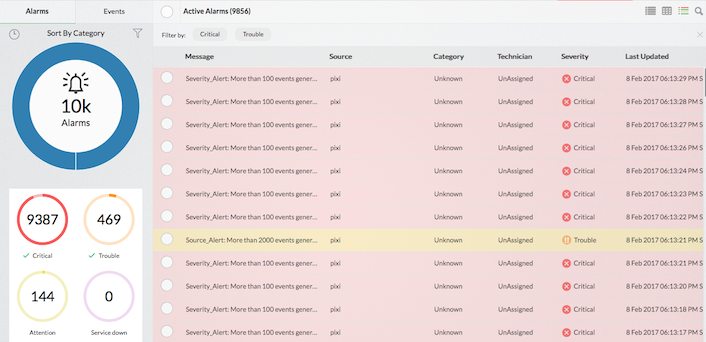
By monitoring key security metrics and getting notified about various bandwidth-based triggers (Insider threat detection systems), you can easily identify internal threats and remediate security issues using Firewall Analyzer . Download a 30-day free trial and secure your network now!
An insider threat is a network security risk that originates within the targeted organization. An insider may not just be a current employee; consultants, former employees, business partners, and even board members can be insiders. The following are the digital warning signs of an insider trying to breach the network.