Firewall syslog analysis and other security device log analysis is vital when it comes to network security. Merely deploying multiple network security devices (firewalls, IDS, IPS, proxies, VPNs, and more) in itself will not secure your network. Instead, the security data generated from these tools should be thoroughly analyzed and used to identify anomalies within the data in real time. Syslog analytics can be broadly classified into the following:
Firewall Analyzer is a firewall Syslog analyzer software that helps reveal information about infiltration attempts at the perimeter of a network, meaning security administrators need to monitor these logs in real-time so that they can swiftly remediate threats once they're identified. Firewall Analyzer offers the following Syslog reports to help identify and prevent network security threats in real-time:
Security reports
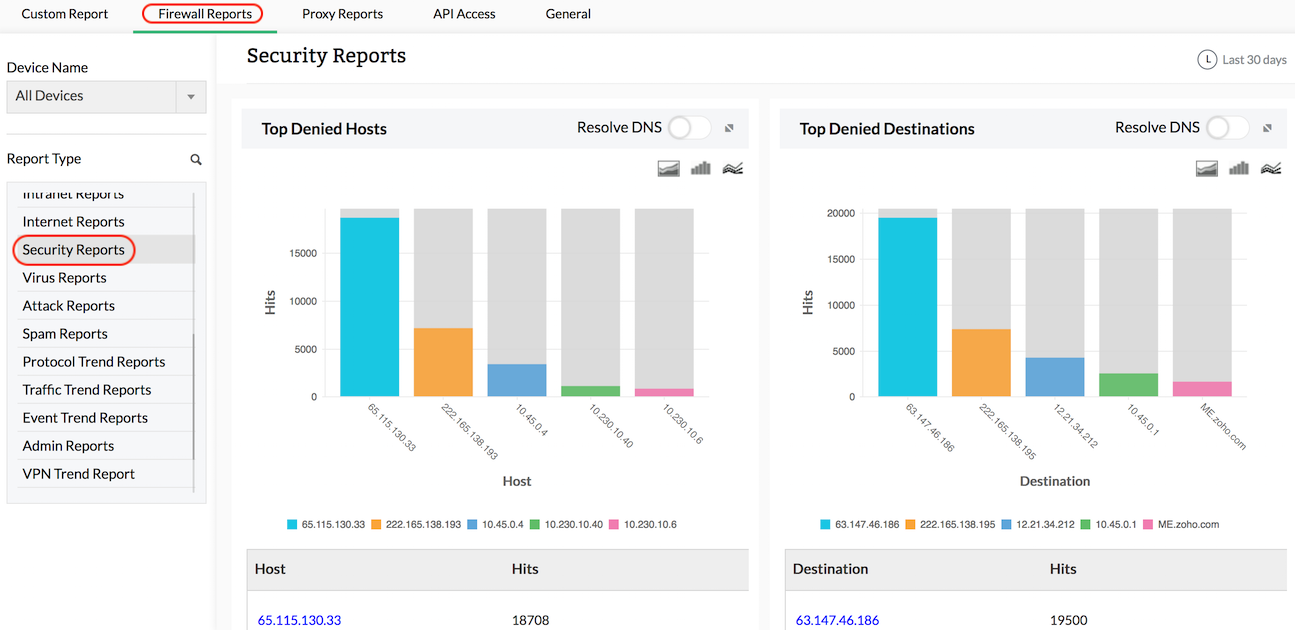
Get reports on possible security threats to the network including information on top denied hosts, denied protocols, and top security events generated. These help you determine if security policies across the network need to be revised.
Virus reports
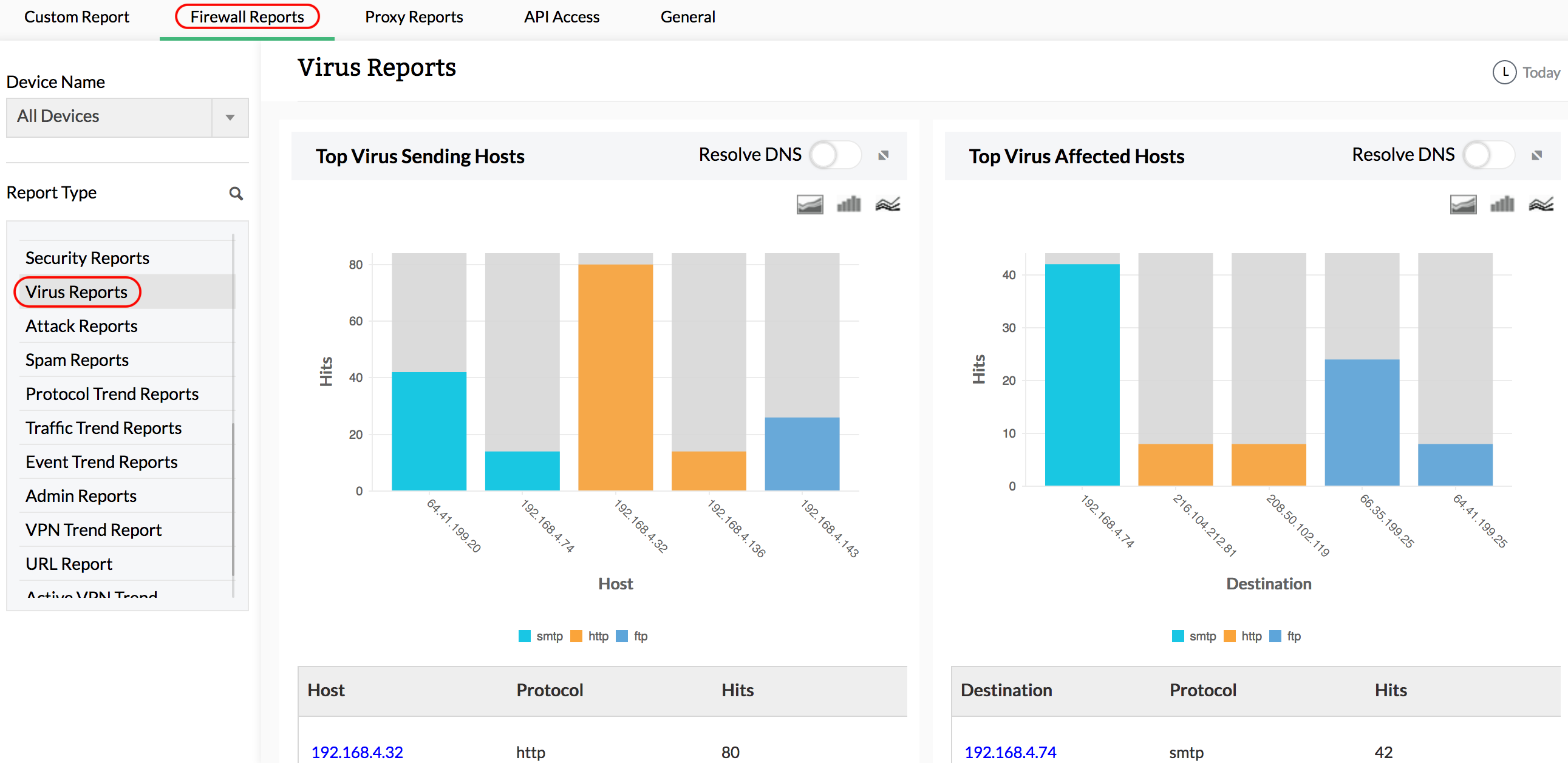
See in-depth information on virus attacks, hosts infected, severity of the attack, subtype, and more. You can view comprehensive details on virus-related raw logs that let you drill down to view details on the raw-log level for top viruses and top protocols used by viruses. The raw log messages make troubleshooting and problem resolution faster and more efficient.
Attack reports
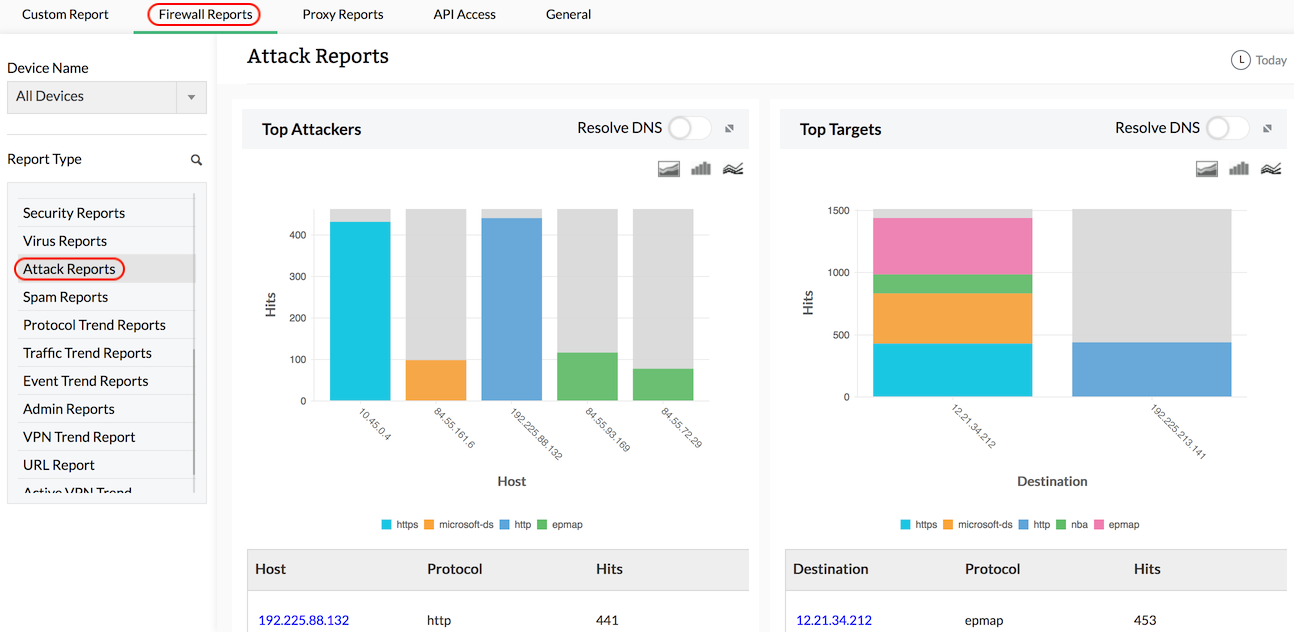
View detailed reports on possible network attacks including information on top attackers, top targets, and protocols used for the attack. These reports give you the insight you need to identify and counter network attacks.
Spam reports
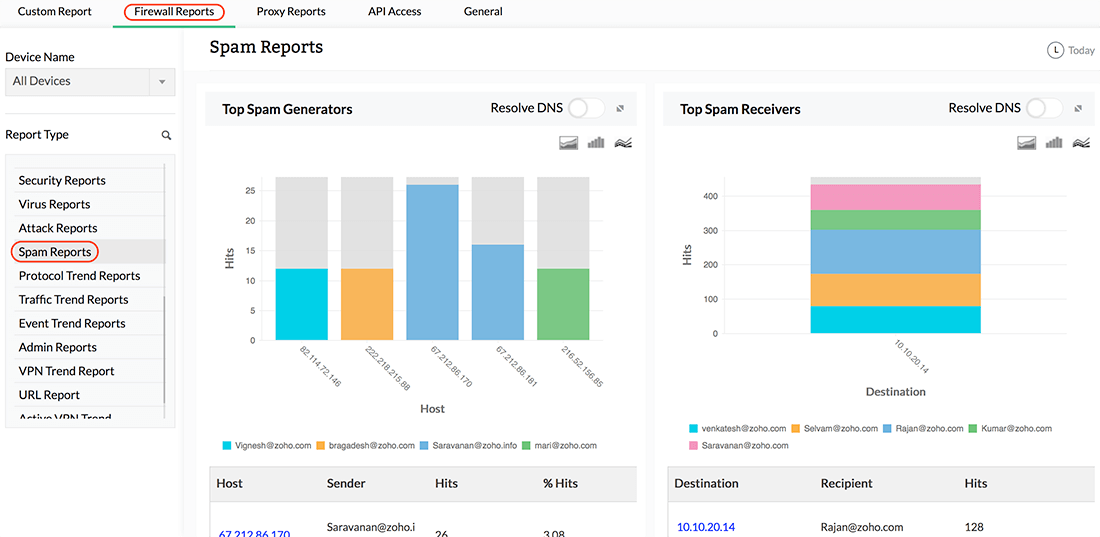
See information on the spam activity in your network, top spam generators, top spam receivers, and top rules allowing spam. These reports help the IT department control spam activity across the network.
VPN reports
Get drill down details on top VPN hosts, top protocols used by the VPN, and bandwidth used by the VPN during peak and off-peak hours. These reports help in identifying users connected to your VPN and the traffic consumed by them, along with all failed VPN login attempts. Information on the failed VPN logins is useful when somebody tries to compromise your VPN network. Repeated or abnormal failed connections may be an indication of an attack.
Proxy server reports
Collect and archive proxy server logs, analyze them, and generate useful corporate internet access information reports. As a proxy log analysis tool, Firewall Analyzer supports BlueCoat, Microsoft ISA, and Squid proxy logs and servers.
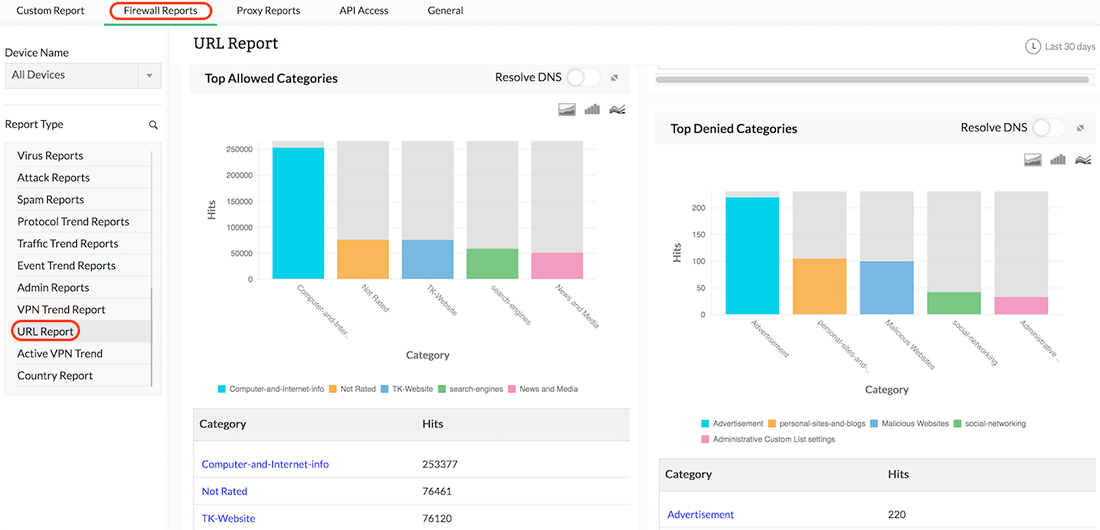
URL reports
Generate reports based on URL categories for each firewall, including allowed and denied URLs. Other categories of URLs include social networking and live streaming. This is useful for monitoring and tracking internal threats in the network.
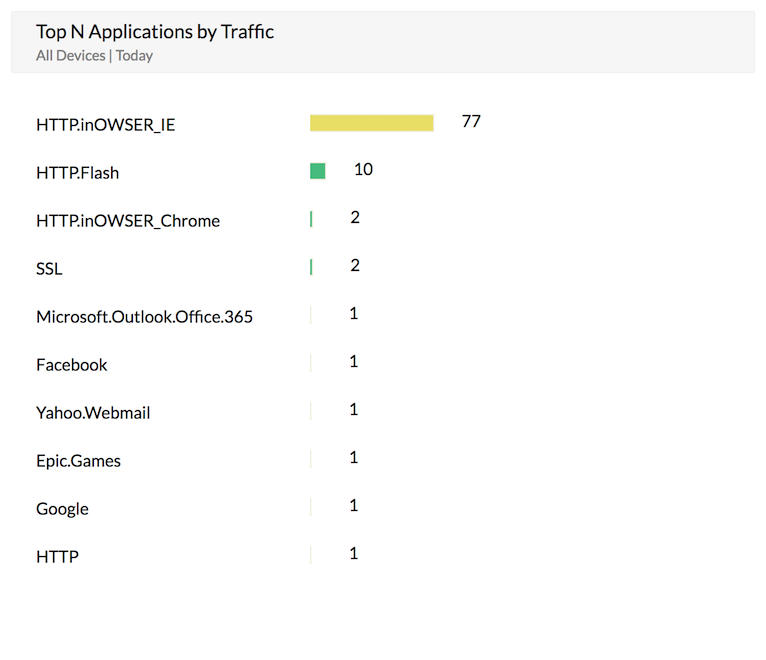
Application reports
Generate application reports for applications (like Skype and Yahoo Messenger) accessed through firewall devices. The application control service should be enabled by the user in the mentioned firewall devices. Firewall Analyzer uses the service provided by the device to get details about the applications and generates the report.
Traffic Syslog analysis helps understand the nature of traffic coming in and going out of the firewall; it also enables security administrators to plan their bandwidth requirements based on the bandwidth usage across firewalls. These detailed network traffic reports are based on syslog data and help identify any bandwidth anomalies. Firewall Analyzer's traffic reports help answer the following questions:
Firewall Analyzer is a firewall syslog analyzer tool. It generates the following reports:
As a security administrator, you can visualize the behavior patterns of the network traffic from these traffic analytics.
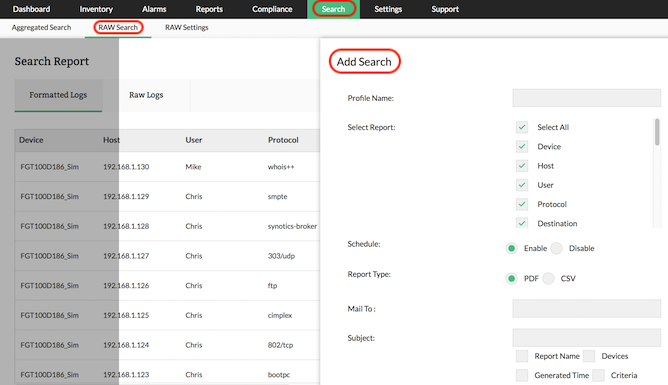
Firewall Analyzer is a firewall syslog analysis tool. It enables network administrators to search the raw logs of a firewall to pinpoint the exact log entry that caused the security activity. The advanced search results are based on raw firewall logs and can be converted into report profiles. The advanced search comes in handy during forensic analysis. Archived logs can be imported, and security incident analysis can be carried out by searching the raw logs.
Firewall Analyzer is an effective syslog analysis software that offers many features to help collect, analyze, and report on firewall syslogs. Its robust syslog analysis features allows it to function both as a windows syslog analyzer software and Linux syslog analysis tool. It provides syslog-based reports for most major firewall devices, including Cisco, FortiGate, WatchGuard, and Check Point. Download a free, 30-day trial of Firewall Analyzer, and secure your network now!
Featured links
Get a slew of security and traffic reports to asses the network security posture. Analyze the reports and take measures to prevent future security incidents. Monitor the Internet usage of enterprise users.
Integrated compliance management system automates your firewall compliance audits. Ready made reports available for the major regulatory mandates such as PCI-DSS, ISO 27001, NIST, NERC-CIP, and SANS.
Manage your firewall rules for optimum performance. Anomaly free, properly ordered rules make your firewall secured. Audit the firewall security and manage the rule/config changes to strengthen the security.
With live bandwidth monitoring, you can identify the abnormal sudden shhot up of bandwidth use. Take remedial measures to contain the sudden surge in bandwidth consumption.
Take instant remedial actions, when you get notified in real-time for network security incidents. Check and restrict Internet usage if banwidth exceeds specified threshold.
MSSPs can host multiple tenants, with exclusive segmented and secured access to their respective data. Scalable to address their needs. Manages firewalls deployed around the globe.