What is the effect of bandwidth hogs in the network? In easy terms, a bandwidth hog happens when you have more traffic in the network than bandwidth and there are delays in network activities. This will directly affect the network performance and could cost an organization in millions! With that being the case, there is the need for an advanced traffic analysis tool, that intuitively identifies the sign of any activity that can lead to a bandwidth hog in the network.
NetFlow Analyzer provides an answer to this known challenge through a real-time alerting & reporting mechanism. Let's say there is slowness in the network during business hours due to users screening the live football match, NetFlow Analyzer will alert you once the utilization excess the threshold limit. It will notify any undesired activity happening in the network and help you identify the users and applications that are clogging the network.
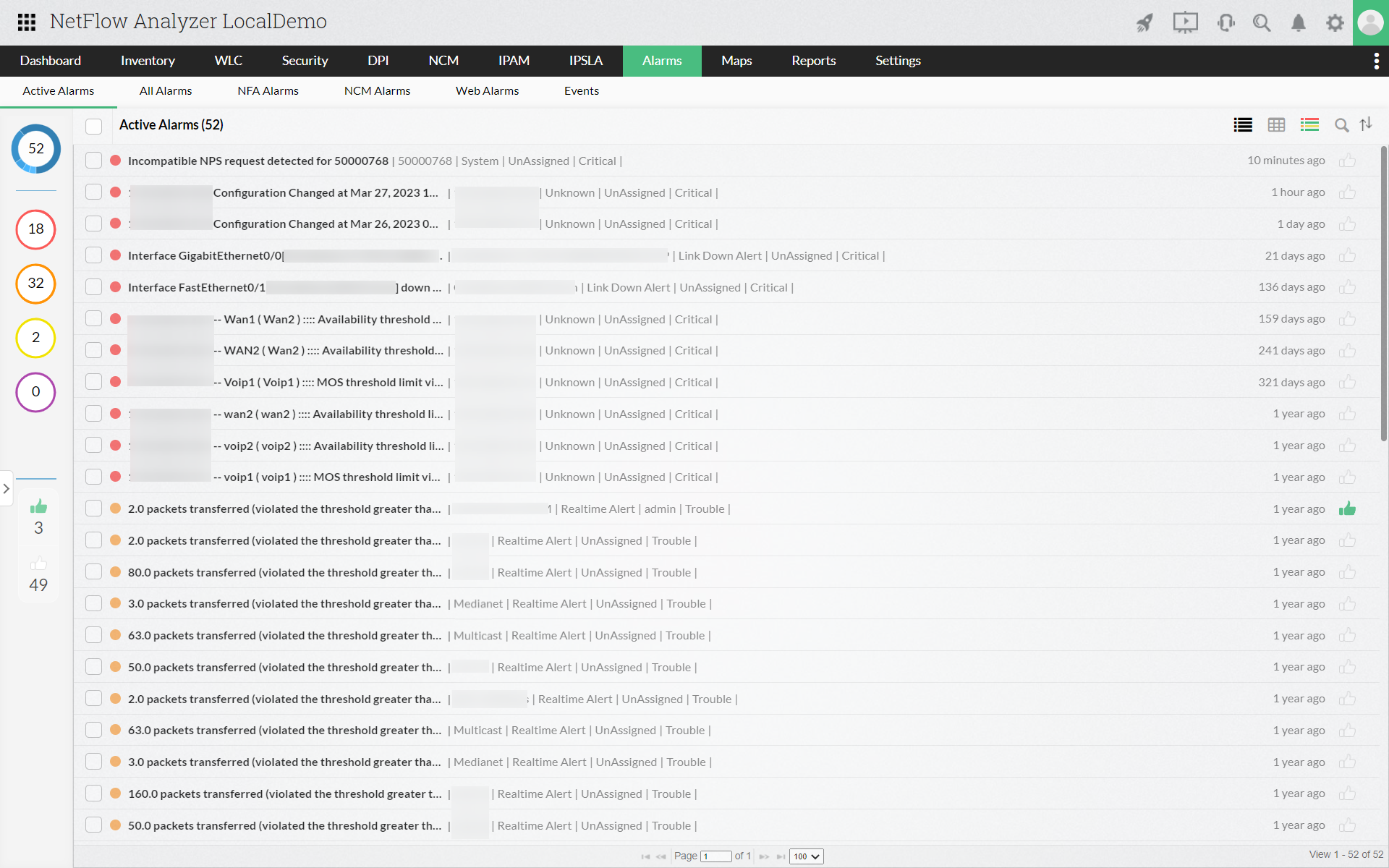
Configuring alert notification in NetFlow Analyzer will send an email or SMS when the utilization exceeds the threshold limit. It allows you to configure alerts based on severities such as Trouble, Attention and Critical. Once the alert is notified, you can drill down to root cause of the alarm.
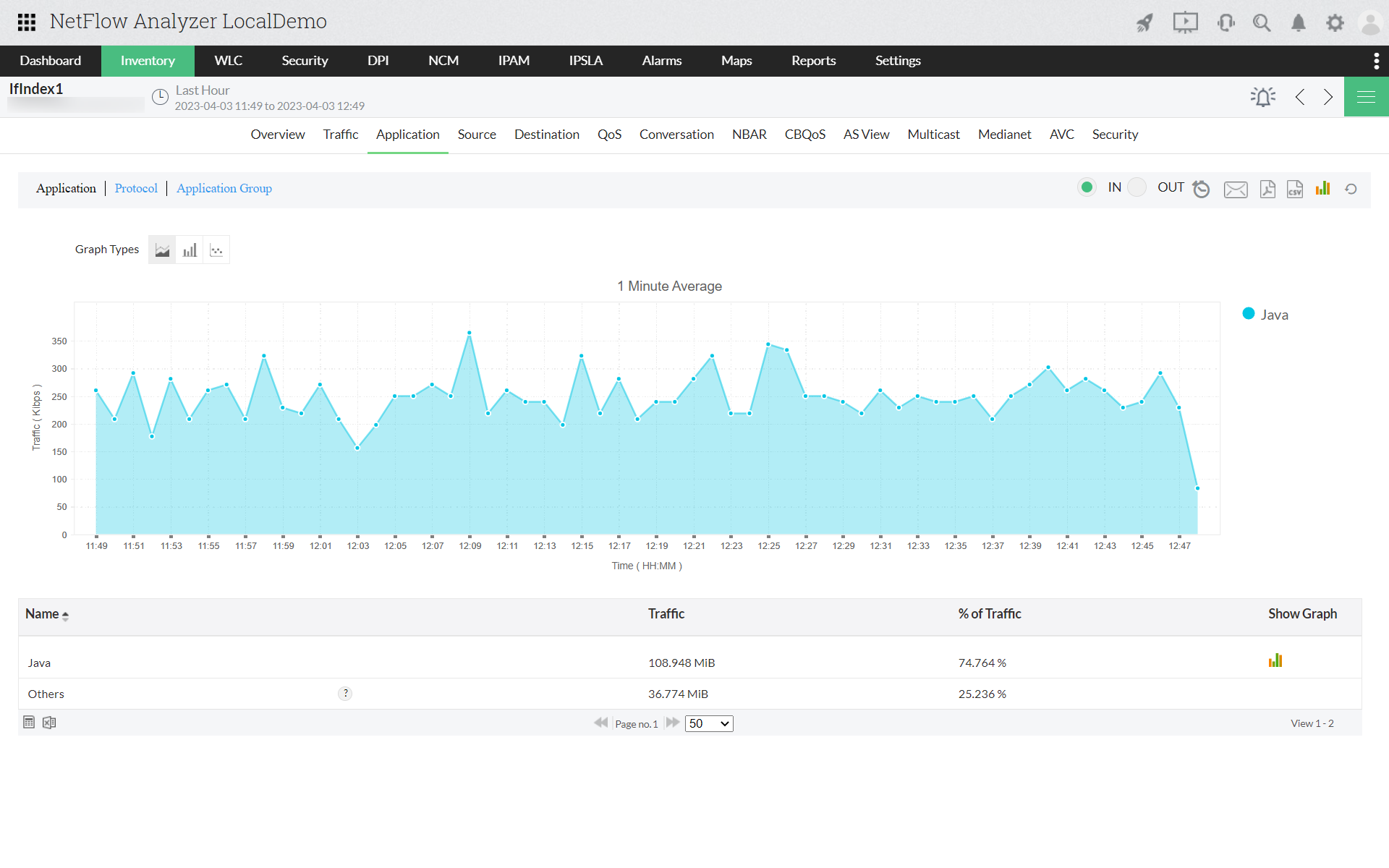
Drill down to bandwidth usage graph for the interface or device with high utilization and identify the top talkers causing the congestion in the network. You are one step closer once you pinpoint the top talkers such as top applications or protocols that are consuming the most bandwidth.
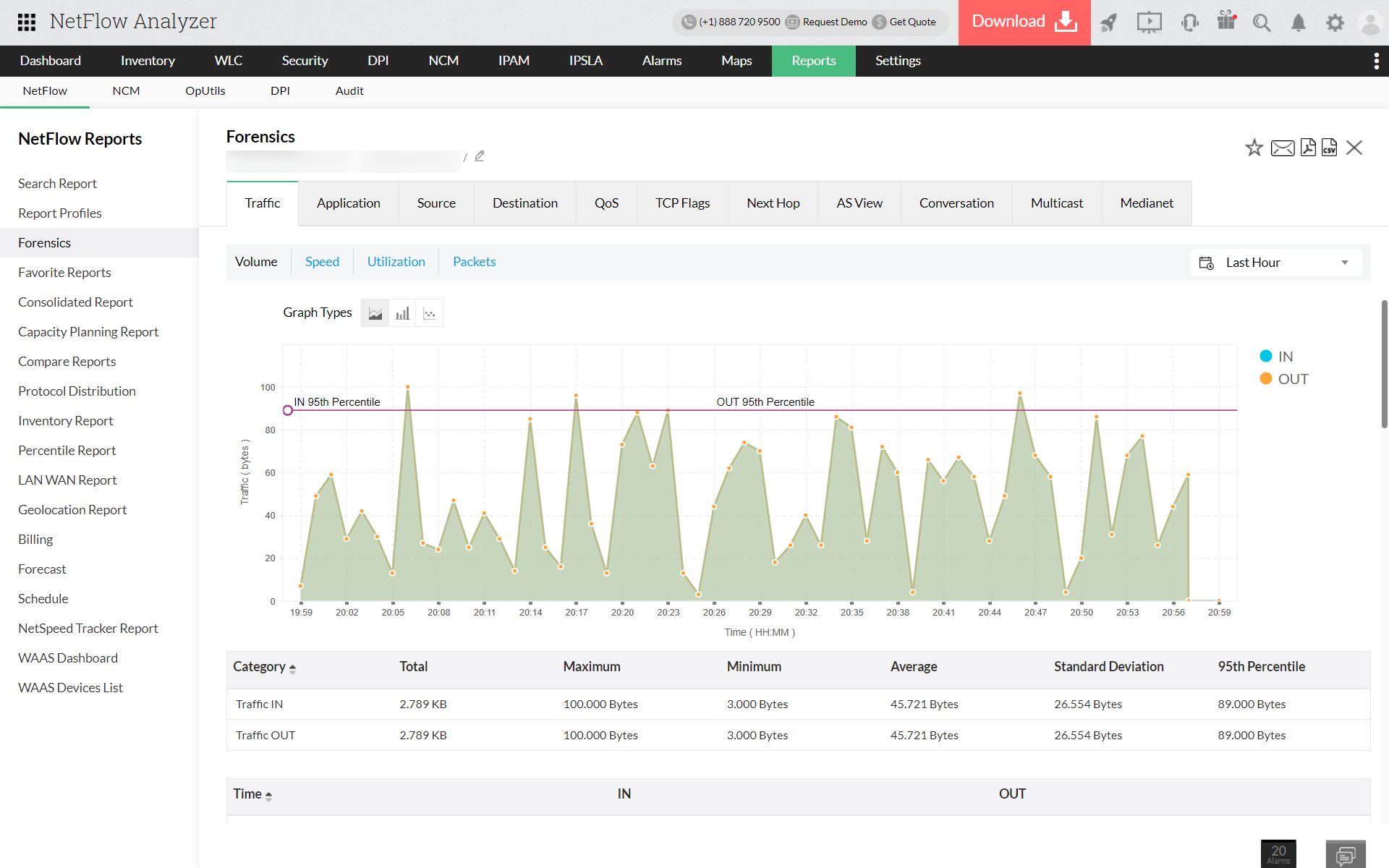
Generate Forensics report with defined criteria as the top consuming application and generate to view the complete conversation details.
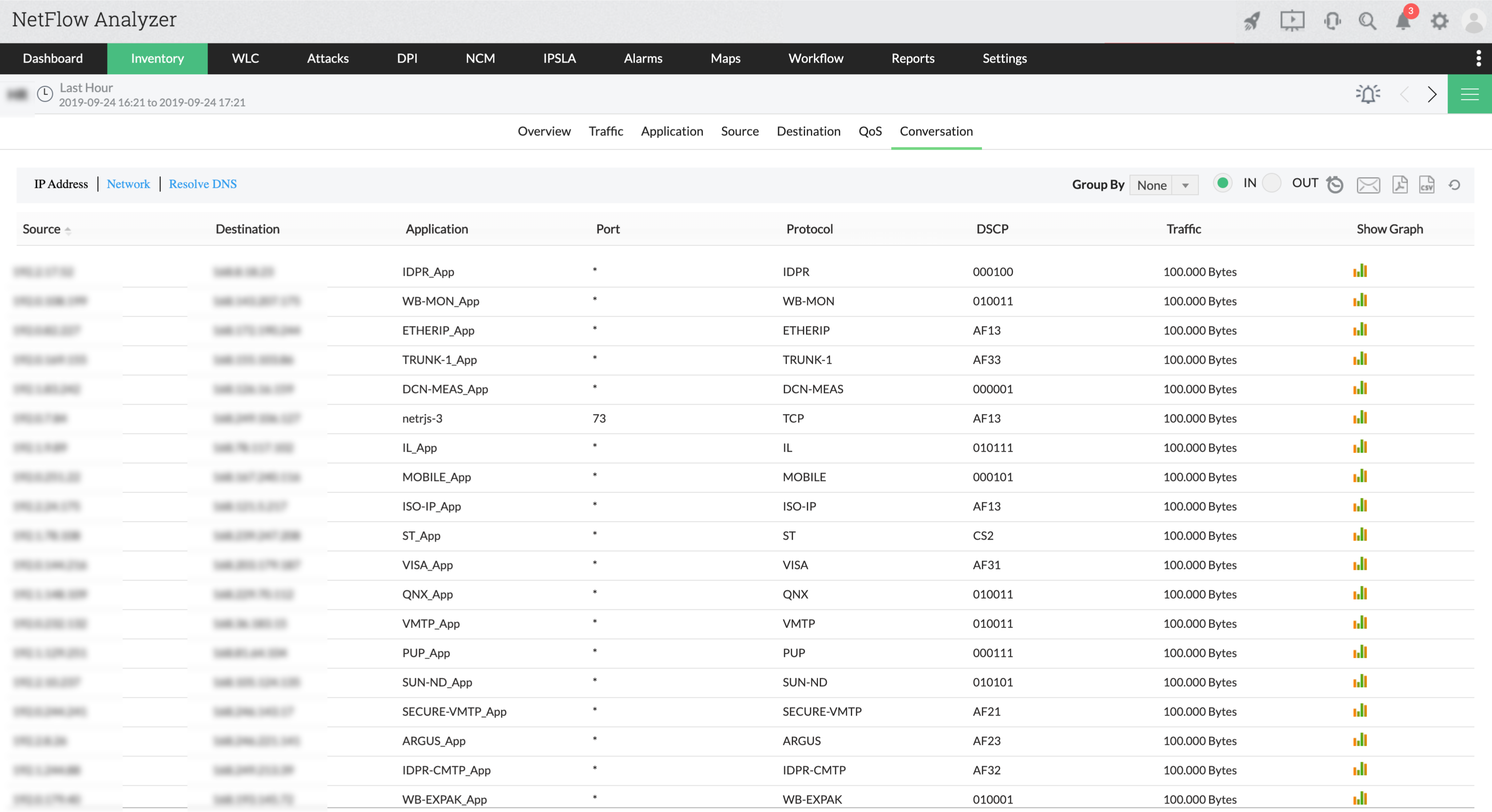
Reporting in NetFlow Analyzer helps you to drill down further to identify if it is an legitimate hog i.e business critical applications or users accessing the network or an external attack that is consuming most of the traffic.
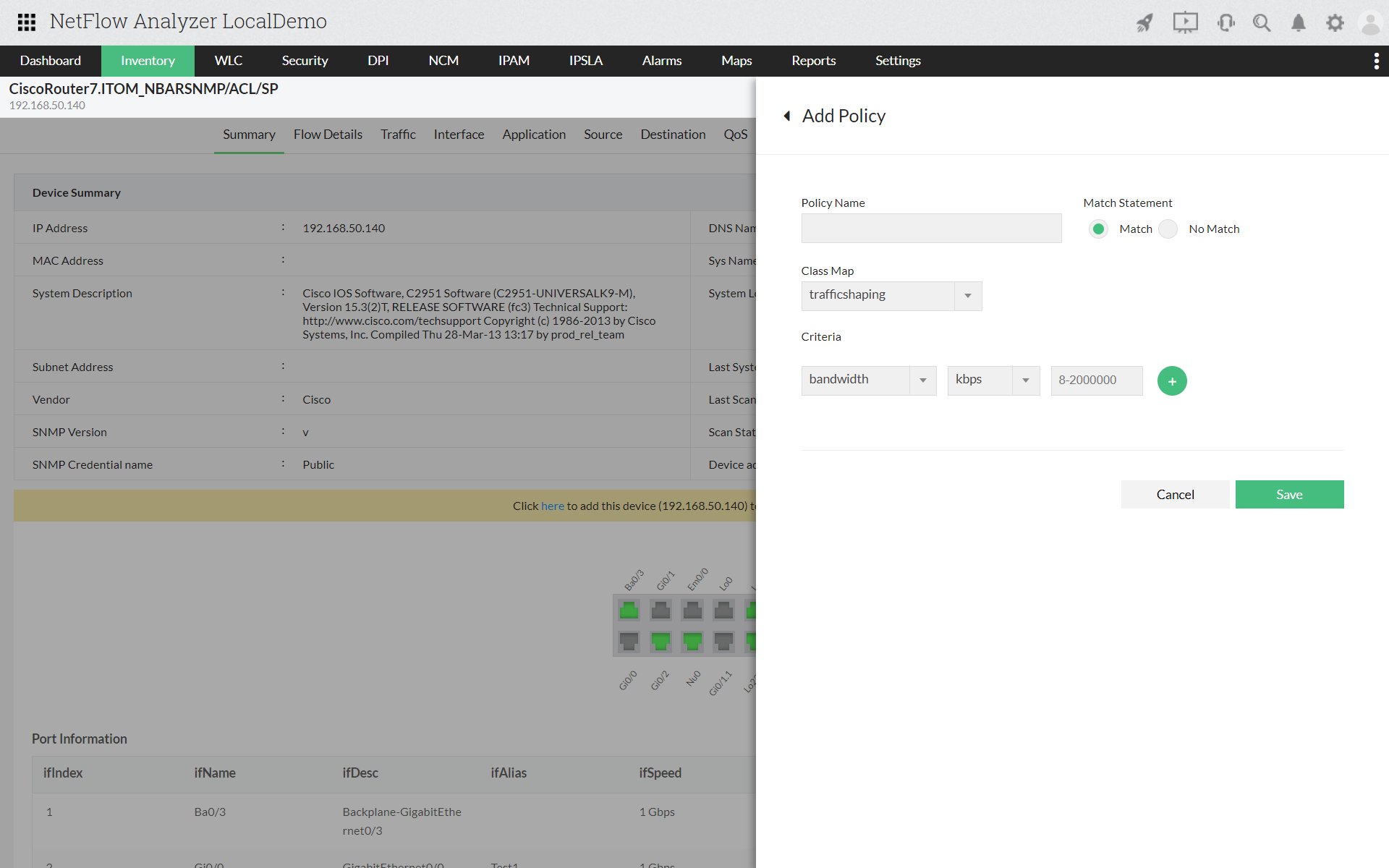
If you can see that a particular type of users are causing the bandwidth hogs in the network, you can take actions by redefining the QoS policies. You can apply ACL or edit the service policies for particular IP addresses in the network. It allows you to exercise bandwidth control, manage network traffic, and align bandwidth for business critical applications.
Learn more on network anomaly detection with network forensics!