As the internet has evolved multifold in the past years, a huge number of services and applications that make business operations easier have come into the picture. With a broad scope of use cases and traffic data being transferred to and from different sources, organizations should be monitoring their networks with strategies and tools. Security and risk management has become an increasingly important aspect of network management that organizations are finding competitive solutions for.
In large enterprises, complexity and the need for scalability in the network infrastructure tends to be more common. Tracking the flow of a huge amount of traffic to check for anomalies and prevent hacks is difficult with traditional, rule-based security systems.
Signature-based techniques can be considered analogous to capturing fingerprints. They monitor network traffic to find if a particular pattern matches the attack signature present in packet headers. Using this technique, network admins can predefine rules and indicators of compromise to describe what would precede a specific attack, such as the attack's behavior, harmful domains, or email subject lines.
The challenge with following this technique in today's IT environment is that it won't work for advanced internet worms such as Raspberry Robin, Stuxnet, or Code Red. Network admins can lay out new rules to combat attacks that they suspect, but most hackers can bypass the laid-out rules by disguising their attack as a file or folder that, when accessed, would evade the security system. Therefore, admins can't protect the network from zero-day attacks that have no signatures to be matched or attacks that utilize a link's weak authentication.
Additionally, with relevant knowledge on the attacks, the obtained information can be used to generate more false positives and keep sending alerts that can be harmful. This increases the workload for admins, forcing them to identify which traffic is authentic for security concerns and to keep the signatures updated to avoid attacks.
Organizations need a dynamic technology that knows how to differentiate abnormal behavior from normal behavior in the way hosts and servers interact with the network. This is where statistical methods like anomaly detection based on machine learning can come in handy. Network anomaly detection, in short, is based on classifying data by differentiating the unusual behaviors of applications or devices compared to what's deemed normal by the organization's network admin. Methods such as statistical theory and information theory have been predominantly used by network admins.
Machine learning has been adopted across various domains to detangle complex problems, and its use in real-time network traffic anomaly detection is no less powerful. Instead of matching the present signatures, machine learning adapts to recognize complex traffic patterns and analyzes the behavior linked to certain attacks that are unseen and likely to be harmful, providing intelligent decisions based on these insights. This way, whether it's a known or unknown attack, admins won't be caught off guard.
Using anomaly-based detection, network admins can flag behavior as "good" or "normal" as well as "suspicious" and get alerts on the specific activity that is different from normal traffic. Anomaly-based detection can be useful in finding attacks that won't align with the baseline behavior, such as a user logging in during non-business hours, rogue devices being added to the network, or when a flood of requests are establishing a connection with the network. Therefore, many zero-day intrusions can be detected and alerted on immediately to protect the security of the network.
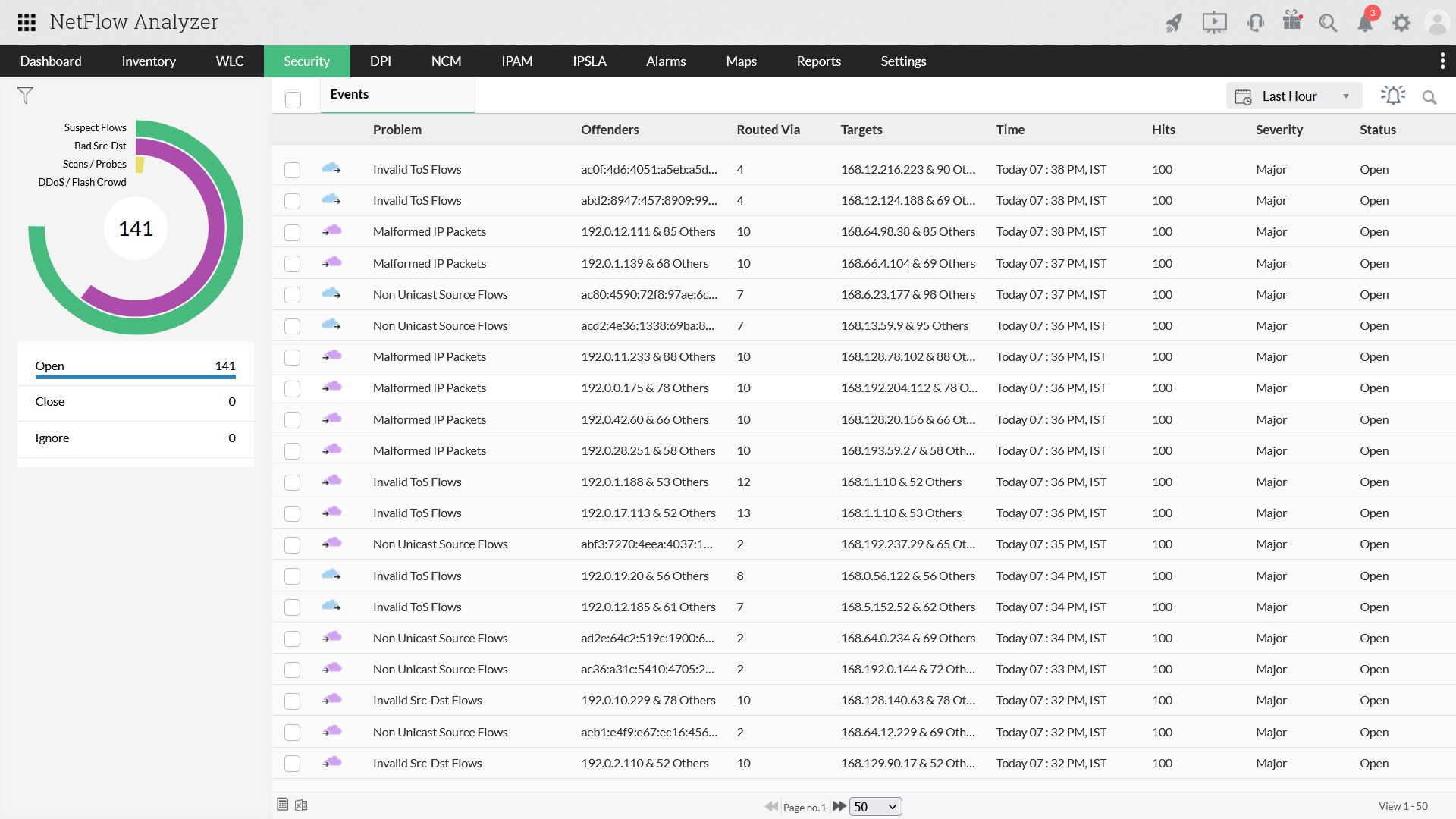
NetFlow Analyzer is a network traffic anomaly detection tool that provides full-fledged visibility into your network's elements, be it a data center or cloud infrastructure. Our flow-based behavior analysis tool is integrated with an advanced Security module that monitors suspicious traffic behavior and classifies it based on different classes like Suspicious Flows, Bad Src-Dst traffic, and DDoS/Flash crowd. With its Continuous Stream Mining Engine and the algorithm configured by you, you can keep an eye on abnormal traffic behavior.