Open port scanner with OpUtils
The rise in network attacks over the years has caused IT administrators to take network security practices more seriously. A port scanning attack is a common type of network attack used by hackers to infiltrate your network using vulnerable open ports. However, port scanning can also be an effective practice when leveraged by network adminstrators. It helps them perform network reconnaissance and identify malicious services running, enabling them to block unwanted traffic and secure network ports. Open port scanning is the process of identifying and analyzing open ports on a network using open port scanner tools.
In this page, we look into,
- Challenges in port scanning: The need for an integrated port scanner
- Features that make OpUtils' open port scanner tool stand out
- FAQs: More on open port scanning
Challenges in port scanning: The need for an integrated open port scanner
There are plenty of options available when it comes to choosing an open port scanner, be it a stand-alone tool, an online tool, or an integrated tool. However, using traditional stand-alone or online, open-source port scanner tools to manage and monitor millions of ports in your dynamic IT workspace is challenging and unfeasible. The following are the drawbacks of not having an integrated open port scanner:
Scalability:
As devices keep being added to your enterprise network, it can be hard to manage and monitor all the ports associated with those devices without a dynamic port scanning tool. Conventional open-source, stand-alone or online port scanning tools offer limited scan range and capabilities that do not scale with your growing network.
Centralization:
Enterprise networks are distributed across cross-subnets, remote sites, and multiple data centers. Unlike stand-alone or online open port scanners, integrated open port scanner tools can give you holistic visibility into your entire network by scanning ports across your network.
In-depth drill down and device inspection:
Using stand-alone or online open port scanner tools can provide you with insights on the services running on particular devices. However, they do not offer insights on the processes or hardware impact of the services running. This calls for a centralized, comprehensive network tool set that can help network administrators inspect, monitor, and diagnose several networking aspects of the inspected port. This increases your team's efficiency, and is less time-consuming.
Network reconnaissance security:
Collecting and analyzing data from port scanners, network scanners, and IP scanners can be tedious without centralized tools or tracking. Correlating data from different sources, i.e., stand-alone or point tools, can lead to errors which might impact the effectiveness of the network reconnaissance carried out.
Merging open port scanning tools with an IP address management (IPAM) inventory can give you more control and visibility over your network by correlating IPAM and port scanning data.
OpUtils' port scanner tool correlates data collected from the IPAM module and can help you get a complete overview of your organization's network. Here's how:
Features that make OpUtils' open port scanner tool stand out
With OpUtils, you can monitor a range of ports and the services running on them right from your centralized port scanning console. OpUtils' port scanner tool is built to tackle the scale and challenges involved in scanning ports in modern IT infrastructures and also offers other useful tools for pinging and querying your open ports. This provides:
Complete visibility
Get visibility into the status of your ports and services running on them.Open port security
Test your open ports to ensure port availability and security.Network diagnosis
Diagnose your complex network infrastructure with ease.A networking tool set
Get all the network monitoring tools you need in a single dashboard.Get visibility into the status of your ports and services running on them:
OpUtils' open port scanner tool will help you identify open, closed, and filtered ports.
| Open | A port is open if its port number (TCP or UDP) is configured to accept data packets. |
| Closed | A port is closed if its application or service is not actively listening. |
Discover and track multiple ports and services across a range of IP addresses with ease. OpUtils' open port scanner tool allows you to monitor open ports in real time. Track all the services running on your ports and turn them off when necessary. With OpUtils' open port scanner, you can also check if your open ports are working efficiently by monitoring their response time.
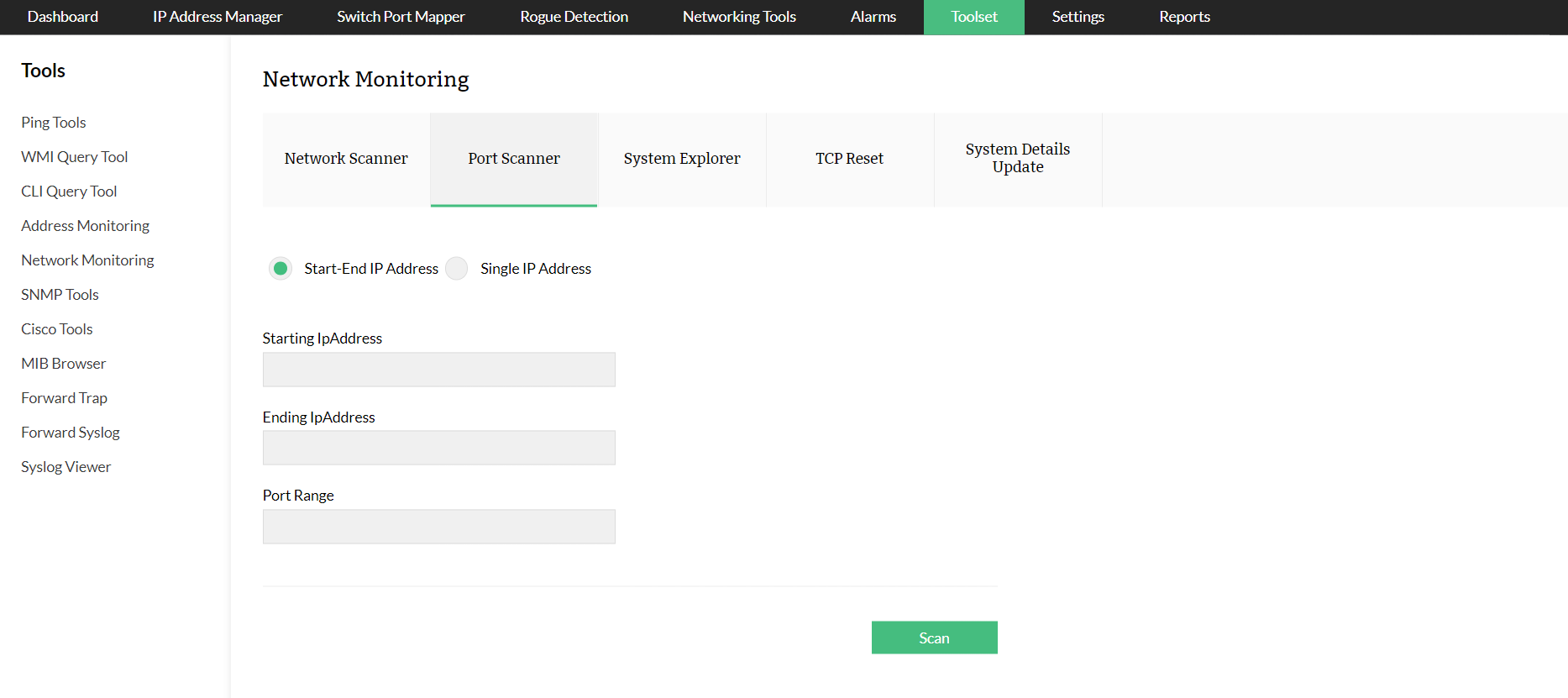
You can scan a single port or a range of ports together with OpUtils' open port scanner.
How to scan a single open port:
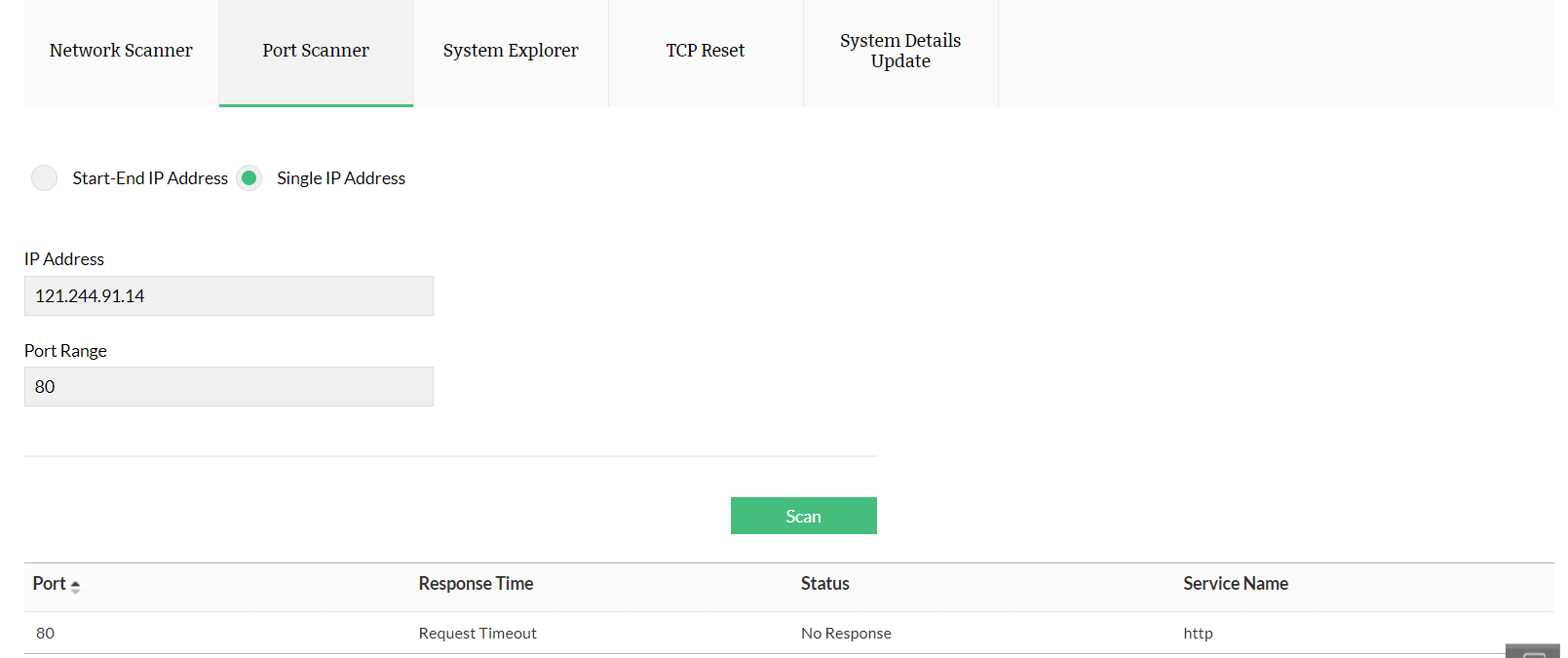
To scan an open port, enter your IP address and port range, and click Scan.
How to scan multiple open ports:
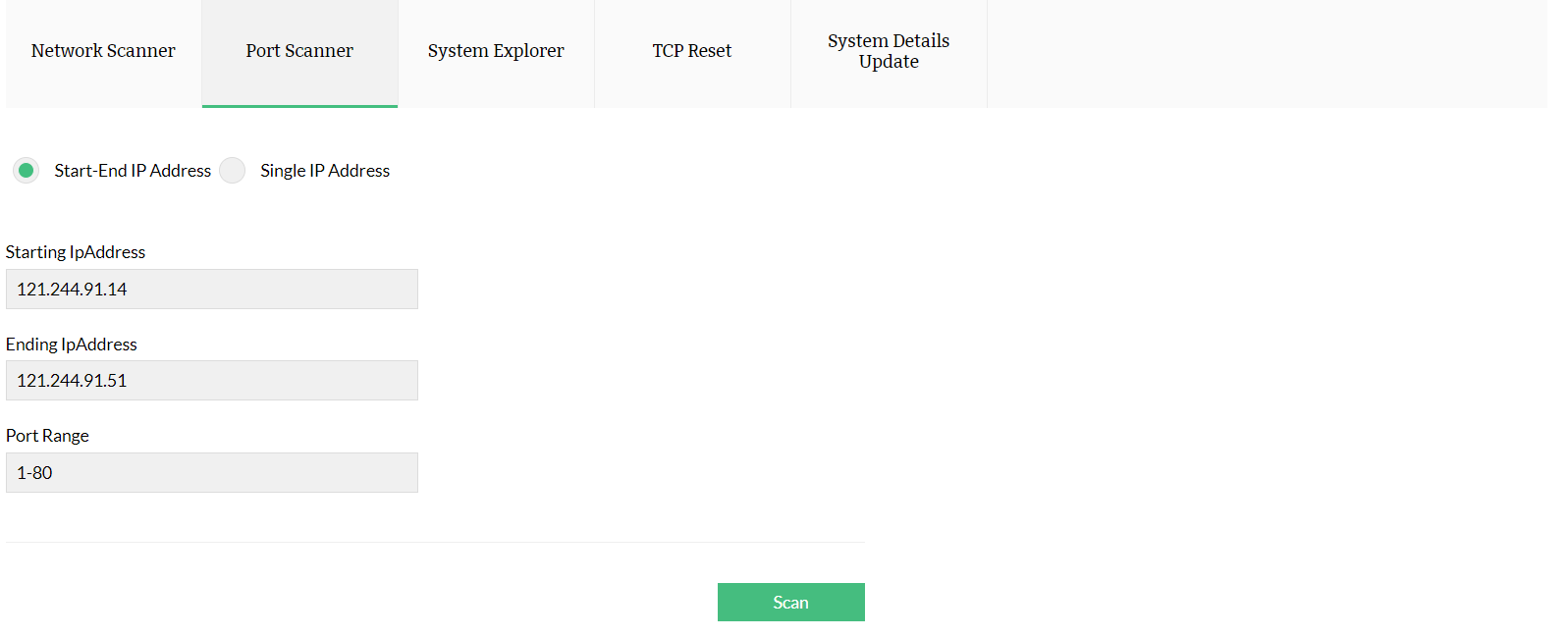
To scan multiple ports together, enter your IP address or range, and enter your port range (this can be done separating port numbers with a hyphen). You can also enter multiple port numbers by separating them with a comma. When you're ready, click Scan.
Test your open ports to ensure port availability and security:
Open ports must be tested to ensure that they are listening and not posing a security risk.
After you discover your ports in the OpUtils console and scan them, OpUtils will give you a consolidated, tabular view of all the ports that are listening, filtered, and not listening in real time. With the help of this feature, you can monitor your ports to ensure port availability constantly.
Diagnose your complex network infrastructure with ease:
OpUtils provides you a network scanner tool along with an open port scanner to diagnose and detect all the active hosts in your organization's network.
Obtain maximum visibility into your network node's IP addresses, ping statuses, response times, SNMP statuses, SNMP response times, OS types, MAC addresses, DNS forward lookups, DNS reverse lookups, and DNS status
Perform TCP reset operations with OpUtils and close all suspicious connections. Keep track of all the open ports that are actively listening, their IP addresses, and the port numbers of servers and clients. Organize your ports by deleting the ones that you don't need.
OpUtils also offers a management information base browser for SNMP devices, which provides valuable insight into your network by enabling you to query SNMP-enabled devices. Get visibility into SNMP traps, syslog messages, and Windows event logs with the help of OpUtils' syslog viewer.
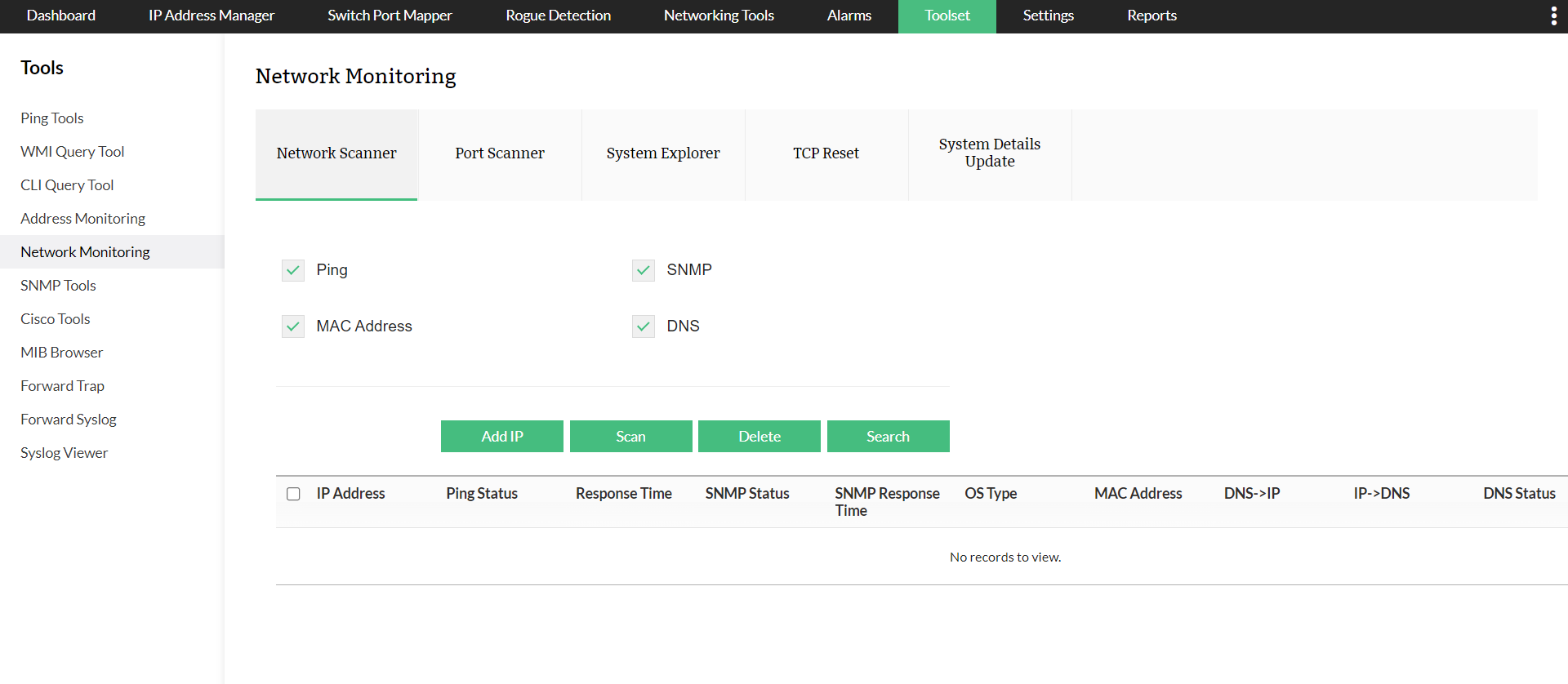
All networking tool sets in a single dashboard:
Manage all your networking tools without the hassle of switching between different tools.
