Network segmentation in IPAM
Earlier, as organizations expanded, a single, flat network was increasingly difficult to manage as it put significant strain on routers, switches, firewalls, and other network components. Such networks frequently faced the risk of cyberattacks and unauthorized access, leading to significant downtime. Not just that, these straightforward networks also faced performance issues due to increased traffic flow, especially with the north-south movement. With all these challenges in place, the need for a more structured network approach arose.
This led to the adoption of network segmentation, where the large, flat network was divided into manageable sub-networks or internal networks, thereby improving overall security, performance, and network management. Before understanding how to monitor the network segments effectively, let's understand what network segmentation is and its importance with a use case.
What is network segmentation and why is it important?
Network segmentation is the process of dividing a larger network into manageable, interconnected network segments. Each segment is separated by network devices like firewalls, routers, and switches. This process helps enhance the security, performance, and capacity planning as each network segment is managed as an independent entity. Network teams implement specific policies within each segment depending upon the network's requirement, thereby limiting the chances of security threats spreading across the entire network.
Use Case:
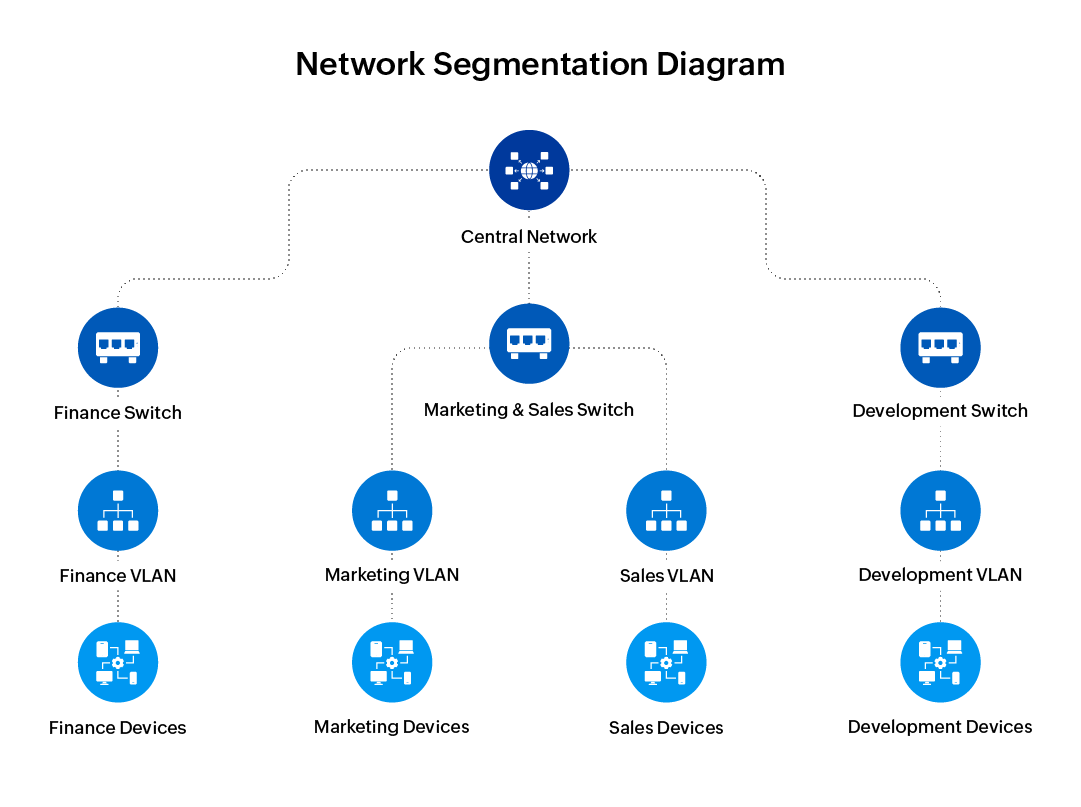
Let's consider a medium-sized enterprise network with different teams like finance, marketing, sales, development, etc. The organization aims to enhance its security and performance due to frequent security incidents, especially involving sensitive financial and HR data.
The solution to this could be to implement network segments where separate switches can be used for different departments to segregate the traffic physically. Additionally, implementing separate subnets and VLANs will segment the physical infrastructure.
This approach ensures that a breach in one segment of the network doesn't affect the others, and network congestion is minimized by confining departmental traffic within specific segments.
Types of network segmentation
Implementing network segments can be done in various methods depending on the operational requirements and security needs. Here are some of the types of network segmentation.
Physical segmentation:
Physical segmentation, also known as perimeter based segmentation, involves using network devices to segment a large network into sub-networks. Each segment has its own set of hardware and is deployed in organizations that require high security. This type of segmentation ensures less contamination in cases of a security breach. However, physical segmentation is expensive and is hard to manage.
Logical segmentation:
Logical segmentation, also known as virtual LAN segmentation, employs software to segment a physical network into several virtual network segments. These segments are logically apart, and any security policy update or configuration change can be implemented to individual segments. They are more cost-effective and easy to manage but are easily compromised when compared to physical segmentation.
However, the segmented network is further divided at application or workload level to create more finer security zones. They are a part of Zero Trust security principle and use SDNs to create micro-segments. Let's understand the difference between network segmentation and micro-segmentation in simple terms.
Difference between network segmentation and micro-segmentation
| Network segmentation | Micro-segmentation |
|---|---|
| Employs broad policies. | Uses granular policies and are a part of the Zero Trust security principle. |
| Controls north-south traffic. | Manages east-west traffic |
| Enforces policies based on IP addresses and network parameters. | Employs identity-based parameters, such as individual workloads. |
| Achieved using VLANs, access control lists (ACLs), and firewall rules. | Utilized through software-defined networking (SDN) technologies and network virtualization platforms. |
How is network segmentation implemented in IP-based networks?
Network segmentation in IP-based networks is done in the following ways.
- Creating subnets: You can segment a large IP network by creating smaller subnets (sub-networks), each with its own range of IP addresses.
- Creating VLANs: You can logically segment a network using a software within a physical infrastructure to create virtual local area networks. This ensures that traffic remains confined within its designated VLAN.
Additionally, methods such as access control lists (ACLs), software-defined networking (SDN), firewall access control policies, and micro-segmentation can be employed according to specific needs to effectively enhance network segmentation.
Why is monitoring network segments important?
Though there are several benefits of network segmentation, it is important to monitor the network segments proactively. Below are some of the reasons:
- Fortified security: Network segments help you physically and logically segment a network. Proactive monitoring will help you detect unauthorized access attempts, unusual network traffic patterns, and any potential security breaches. Monitoring the segments from time to time helps the administrators detect such breaches early and resolve them before they escalate.
- Enhanced performance: Monitoring network segments helps you keep track of their performance, such as bandwidth usage, latency, packet loss, etc. Monitoring the performance helps the administrator understand network blind spots and performance bottlenecks.
- Quicker troubleshooting: Segment monitoring provides insights into the exact location of network issues, enabling administrators to isolate critical network segments quickly. This segregation effectively minimizes the impact of problems and substantially reduces network downtime.
- Improved capacity planning: Each network segment exhibits unique usage patterns. Understanding these patterns across various segments, administrators can enhance capacity planning. This enables anticipation of future growth, facilitates more efficient resource allocation, and ensures that the network infrastructure adequately meets operational demands.
- Better compliance: Monitoring and logging of network activities is essential to meet regulatory compliance. Monitoring the network segments from time to time will maintain audit trails and logs of the network activities, thereby maintaining compliance with these regulations.
In a nutshell, monitoring network segments enhances both performance and security. Deploying a tool for this purpose further improves visibility and provides detailed insights for better management and troubleshooting.
Why OpUtils is the right choice for monitoring your network segments?
OpUtils is a robust IP address management and switch port mapping software designed to help administrators monitor network segments efficiently. Below are some of the key features that enable effective monitoring and management of your network segments.
Subnet monitoring:
OpUtils offers comprehensive subnet monitoring, enabling efficient tracking of IP usage and quick identification of network issues. Its intuitive dashboard provides real-time insights into subnet availability and utilization, allowing for proactive management and rapid troubleshooting. With detailed reporting and alerts, you can ensure optimal utilization and security of your subnets. Additionally, OpUtils supports subnet grouping, allowing you to organize and manage related subnets more effectively.
Port monitoring:
OpUtils enhances switch port monitoring by integrating comprehensive VLAN management capabilities. When VLANs are configured on switch ports, OpUtils allows administrators to monitor these ports and gain valuable insights into the connected devices. This functionality ensures that you can manage network segmentation efficiently and maintain an organized and secure network infrastructure.
Scope monitoring:
OpUtils' DHCP monitoring offers detailed insights into IP allocation and utilization within DHCP scopes. The real-time IP scanner tool tracks reserved and leased IP counts within each scope. It helps prevent IP conflicts and ensures efficient IP address utilization within each segment. With real-time alerts and reports, OpUtils helps you manage IPs efficiently across the network.
Rogue detection:
OpUtils enhances network security by detecting and categorizing devices as trusted, rogue, or guest. This feature helps you identify and classify unauthorized devices in real-time. By monitoring, categorizing and managing device access, OpUtils ensures that your network remains secure from any unauthorized intrusions.
Wake-on-LAN:
Wake-on-LAN feature allows administrators to wake up multiple devices on the network at a given time, making it easier to perform updates, maintenance, or access systems outside of regular working hours. Administrators can create multiple groups, and different groups can be rebooted at different times. By utilizing scheduled wake-up tasks and automation, OpUtils ensures smooth network management and enhances operational efficiency.
Not just that, features such as the advanced IP scanner and port scanner allow for on-demand scanning of specific subnet groups or switches, aiding in the effective management of your network segments. This isn't the entire story of OpUtils. There's more - book a live demo with our product experts to explore how OpUtils can enhance your network segment management journey. Alternatively, seize the opportunity to experience OpUtils hands-on today by downloading a free 30-day trial.
Looking to enhance integrated IPAM?
Try OpUtils for free today