Do not let unauthorized devices compromise your network security. With OpUtils' Rogue Detection module offering comprehensive user device tracking capabilities, safeguard your network from malicious devices.
Here is how OpUtils' user device tracker simplifies network security:
Enable comprehensive visibility with enhanced discovery
Modern networks are distributed and complex, and it can be tedious to manually account for the connected devices. To simplify this, OpUtils' Rogue Detection module enables network admins to gain complete visibility with:
Network discovery:
OpUtils' user device tracking capability provides a powerful network scanning feature. This scans all the monitored IP devices, such as routers and switch ports, enabling your organization to identify and track all the connected devices within your network. This ensures that no corner of the network goes unnoticed.
AD-based discovery:
By monitoring AD, OpUtils' user device tracker brings a new level of insights into user activities and device interactions. By syncing with AD, OpUtils automatically discovers and allowlists all the devices associated with AD.
Imports of allowlisted devices:
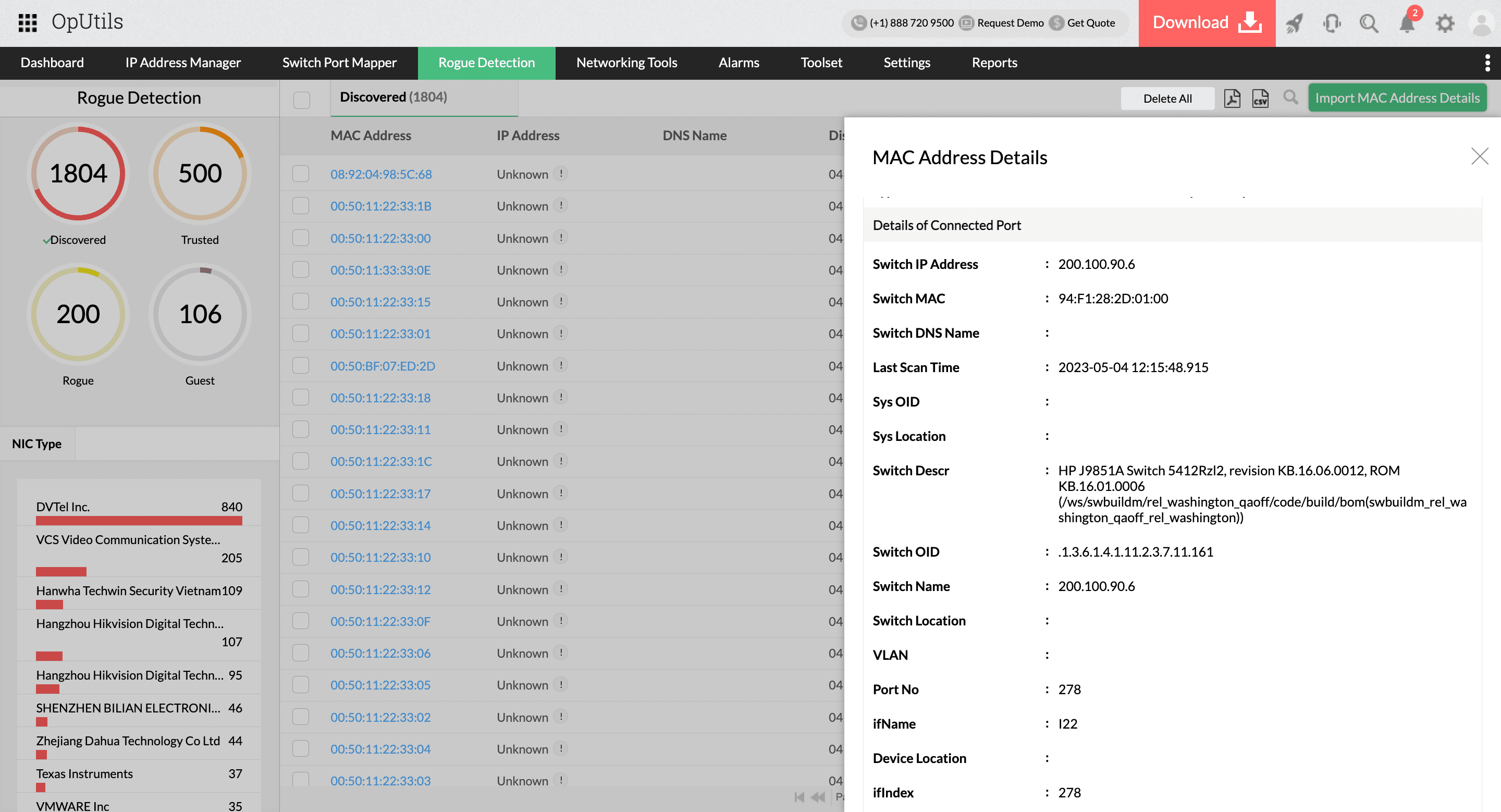
OpUtils lets network admins import allowlisted devices through the Import MAC Address Details option, streamlining the network visibility process. By incorporating trusted devices into the system, organizations can focus their attention on potential threats rather than benign elements.
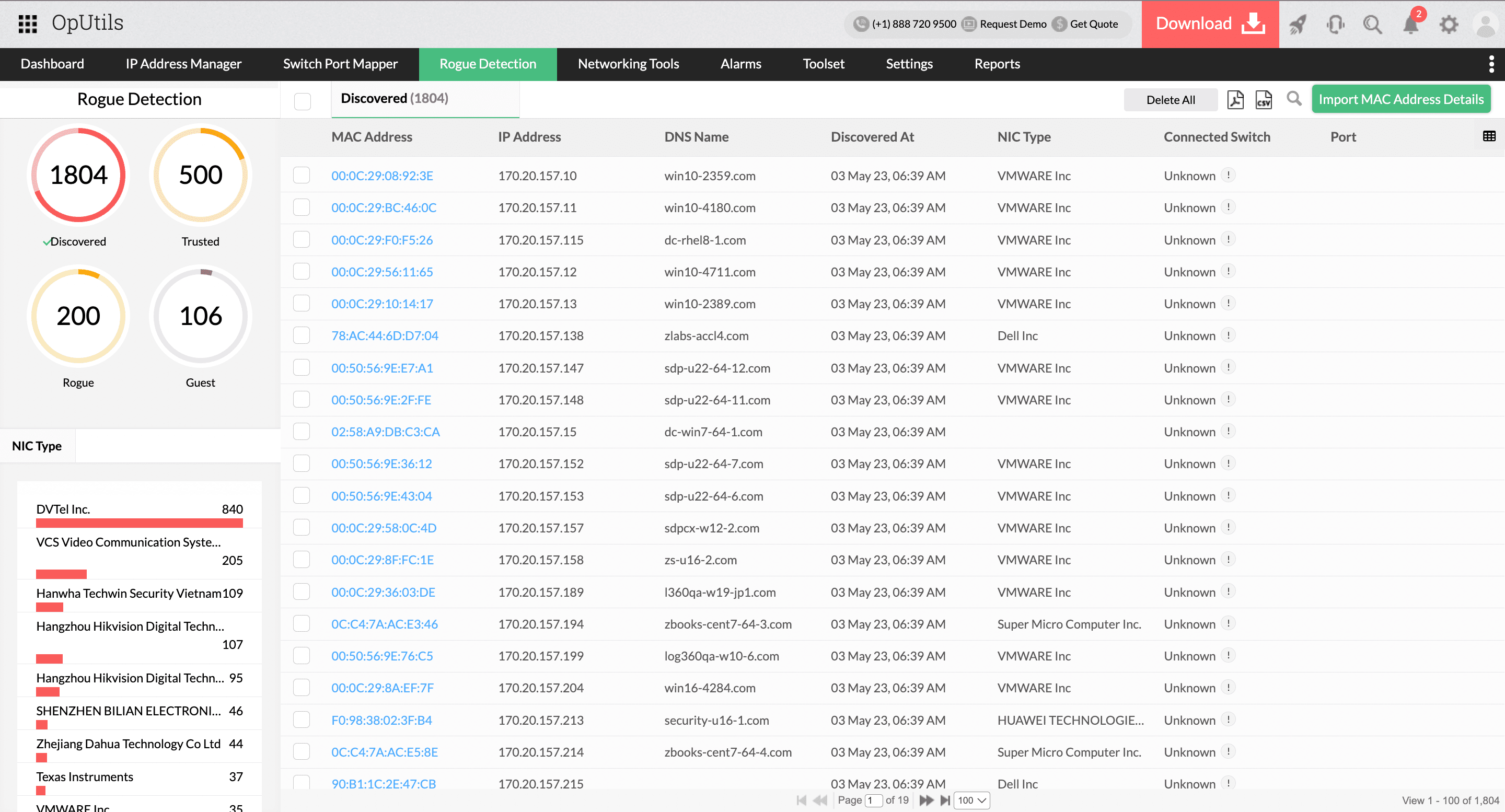
Inspect user details with an AD integration
OpUtils goes beyond simple device detection by integrating with AD. This integration delivers detailed user information, facilitating a more comprehensive understanding of network dynamics. Also, it enables network admins to scrutinize user behavior, enhancing their ability to identify and respond to potential security risks.
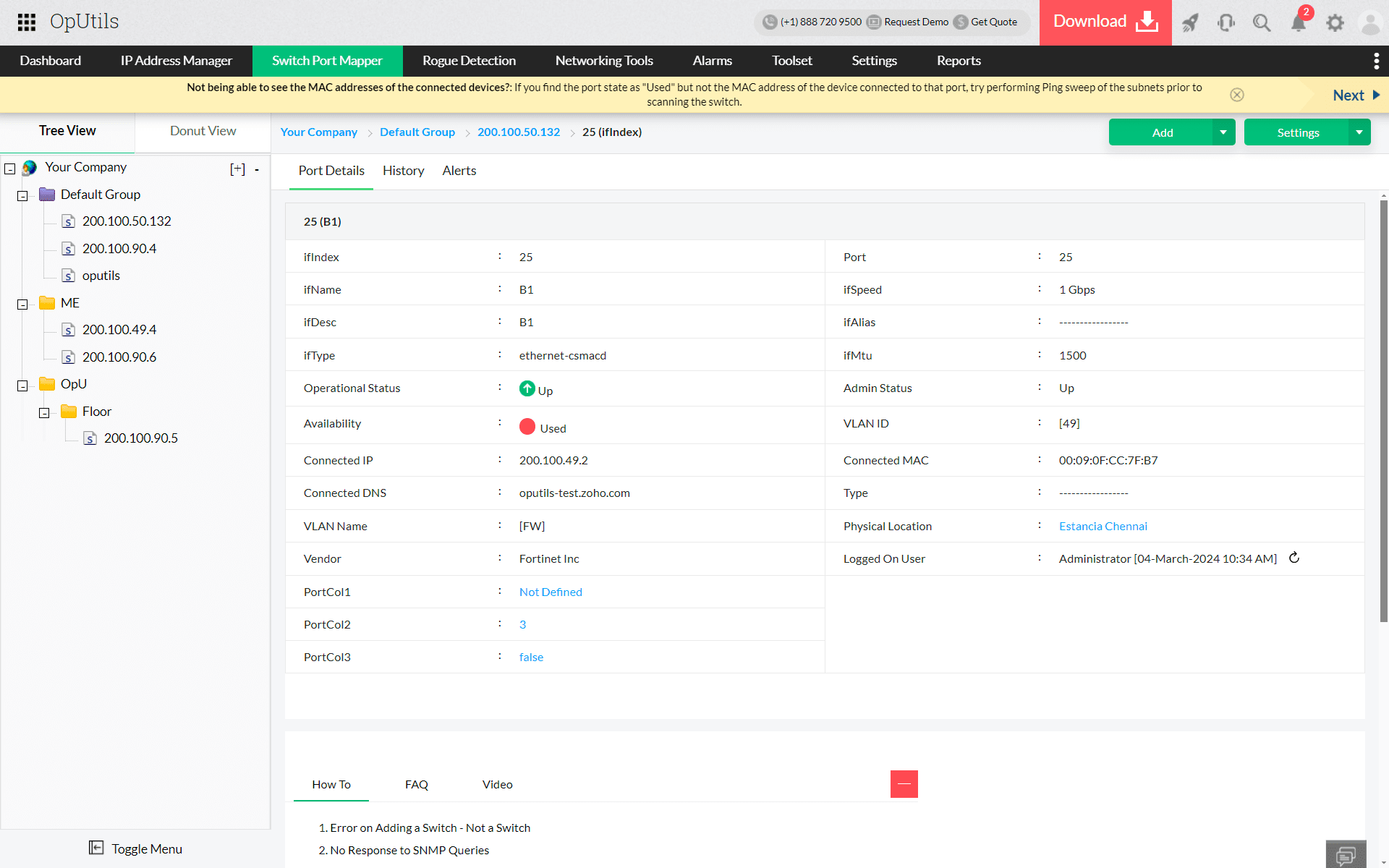
Locate users in the network with diverse tools
OpUtils offers a comprehensive suite of IPAM capabilities for efficiently locating users within the network. From IP address scanning to subnet monitoring, these capabilities facilitate rapid responses to incidents.
Network admins can use OpUtils' set of over 30 network tools to trace the origin and destination of network traffic, monitor the availability of critical devices, trace data packets, drill down to system details, and remotely reset system details.
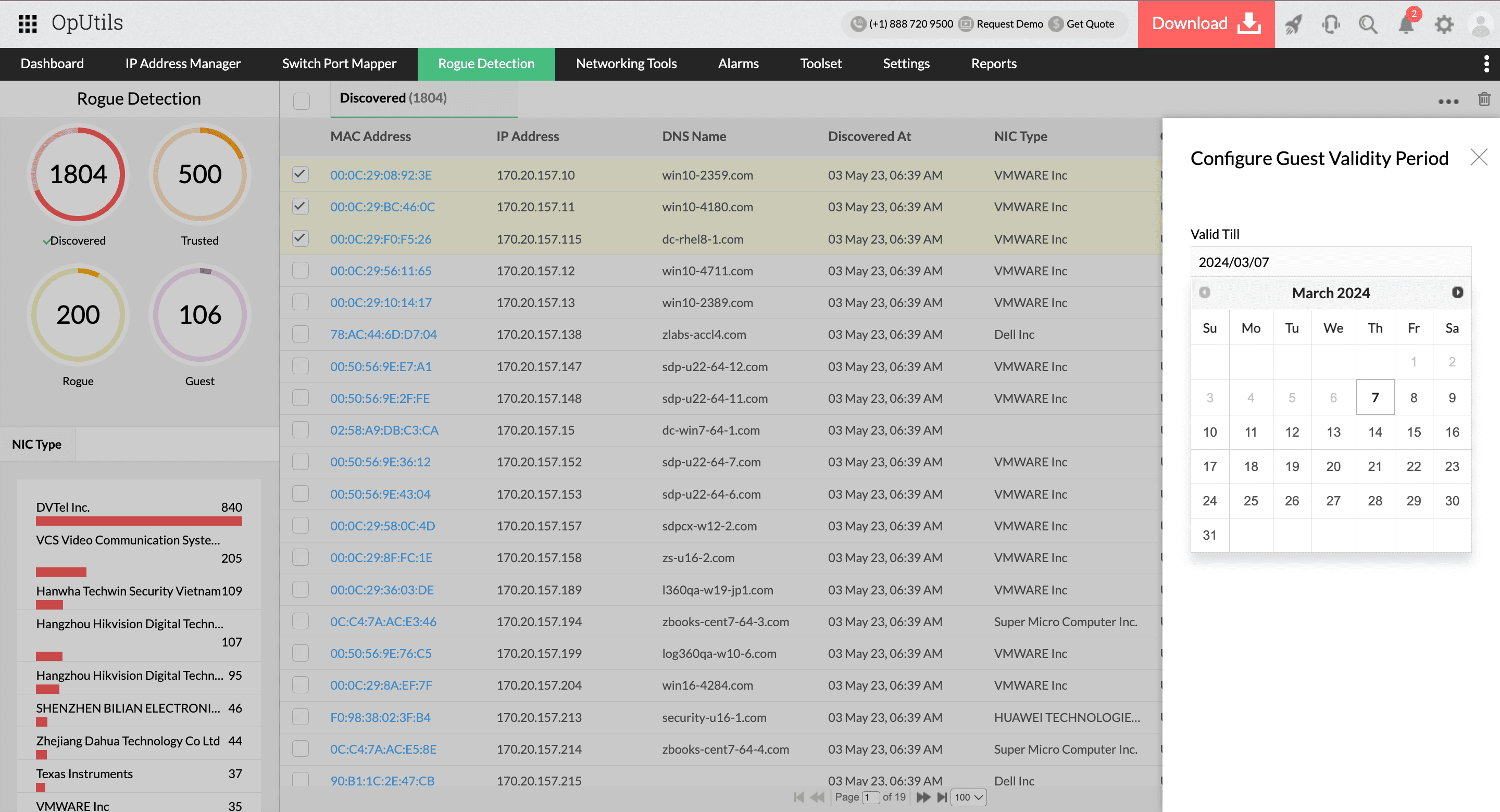
Track and tag for efficient management
OpUtils introduces the concept of tagging devices as Trusted, Guest, or Rogue, enabling administrators to categorize devices into different watch lists and monitor devices exhibiting suspicious behavior. Whether it's a guest device or a potential rogue element, the watch lists feature ensures proactive monitoring and swift responses.
Secure your network by blocking unauthorized access remotely
OpUtils provides a centralized view of switch port utilization, allowing administrators to visualize network connectivity. This feature aids in identifying potential bottlenecks, anomalies, and unauthorized devices connected to the network.
OpUtils takes network security to the next level by allowing administrators to remotely block unauthorized access. With a few clicks, suspicious devices can be isolated, preventing potential threats from spreading. This minimizes the impact on the network.
Simplify user device tracking with OpUtils
Get started for free and secure your network from unauthorized access.
Try OpUtils for free today