Both the cloud and on-premises version of ManageEngine ServiceDesk Plus are now compliant with HIPAA standards. This compliance, deemed by an independent, third-party audit organization, extends ServiceDesk Plus' ability to serve any business that handles patient healthcare and services. Here is a brief summary of what it means for ServiceDesk Plus to be HIPAA-compliant.
What is HIPAA?
The Health Insurance Portability and Accountability Act of 1996 (HIPAA) is a US federal law aimed at protecting sensitive patient health information from being disclosed without the patient?s consent or knowledge.
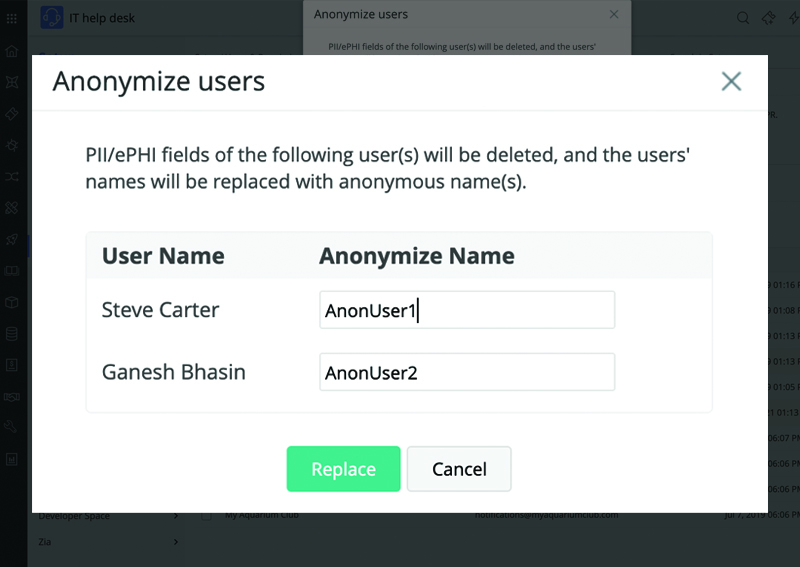
Organizations that handle individuals' protected health information (PHI), such as healthcare providers and any businesses that work with them, are required to adhere to the data privacy and security standards established by HIPAA. These organizations meet the definition of "covered entities" or "business associates" under HIPAA.
Covered entities
A covered entity (CE) is an organization that collects, transmits, or stores PHI regulated by HIPAA legislation. A few examples of CEs would be insurance companies, hospitals, healthcare providers, and community health information systems.
Business associates
A business associate (BA) is an organization that performs activities on behalf of a CE?specifically, those activities that include the disclosure or use of PHI. Every BA must agree to install safeguards like access controls to protect the integrity, confidentiality, and availability of PHI.
How is ServiceDesk Plus defined under HIPAA?
Both the cloud and on-premises version of ServiceDesk Plus are HIPAA compliant as a BA. The responsibility of Zoho, the parent company of ManageEngine, is that of a BA as defined in HIPAA. Further, Zoho is not involved in directly collecting ePHI from data subjects.
How are ITSM tools used in healthcare?
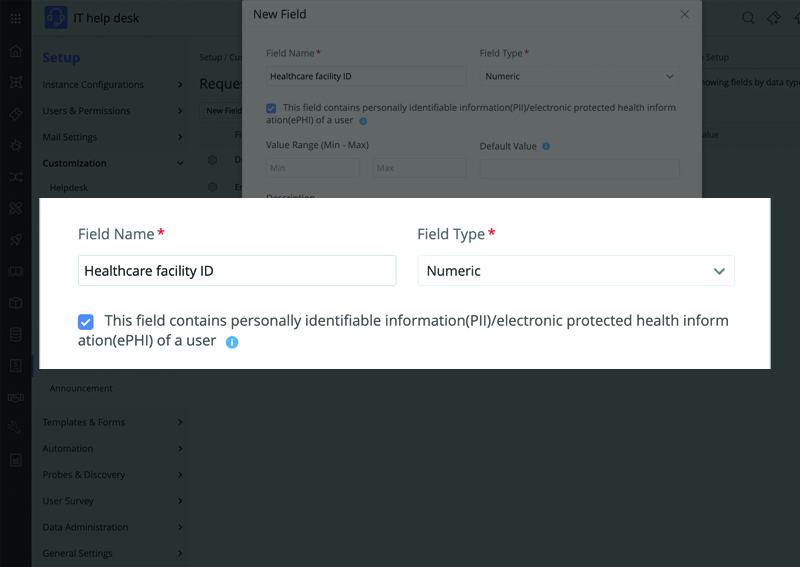
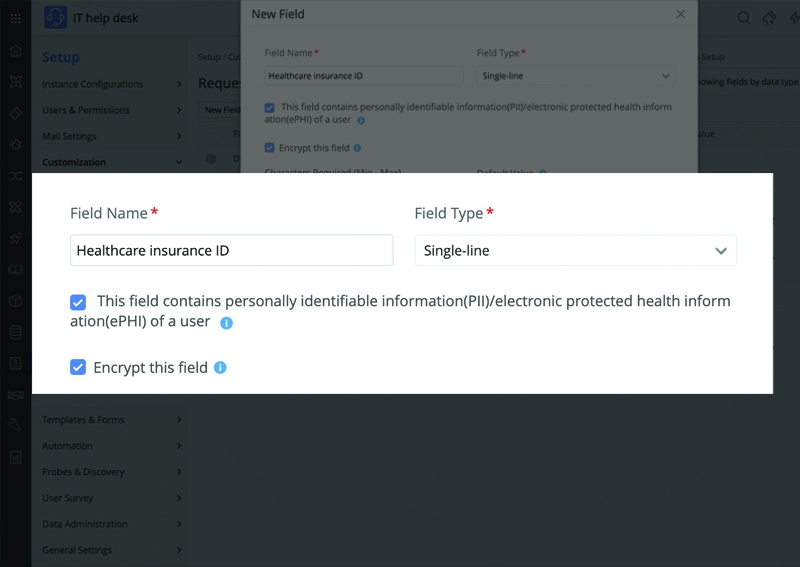
An IT service management (ITSM) solution used in healthcare comes under the purview of HIPAA since it could be used to record various ePHI, including healthcare provider addresses, health plan details, and critical asset information. Healthcare organizations should work with ITSM solutions that are compliant with HIPAA standards to avoid incurring civil penalties. The key areas where a HIPAA-compliant ITSM tool comes in handy are:
Request fulfillment & incident management
Now that most ITSM solutions offer enterprise service management capabilities, ITSM practices have been extended beyond IT. A ticketing system to track IT requests and incidents can now be used to track health insurance claims, health records like lab results, and more. The requests handled by the IT team, the finance team, or the diagnostics team can hold sensitive information such as the patient name or ID; if any unapproved eyes fall upon this information, it could be detrimental for all stakeholders.
Asset management
Since CEs such as healthcare providers use numerous hardware and software assets to store and transmit sensitive ePHI, an ITSM tool with an assets module is generally used as a single source of truth to track and manage all these resources. If someone were to obtain unauthorized access to the asset inventory, this could lead to tampering of asset information, or the intruder gaining illegal access to the systems holding sensitive patient records.
Maintenance
Automated backup systems and scheduled archival of service desk data facilitate quick restoration during failures and improve the performance of the ITSM tool. However, since backup data is often stored in a centralized location in a network drive, it could be prone to unwarranted access and unmonitored usage, leading to misuse of sensitive health records.
Integrations
ITSM tools are integrated with various third-party tools either natively or via APIs to establish a seamless collaborative environment. This could lead to the sharing of critical asset information with tools like an endpoint management system. Despite utilizing authenticated APIs, ITSM tools do not have control over who has access to the third-party tools, and this lack of access control could lead to a breach.
Change management
While the change management practice is designed to minimize risk during any modifications to IT infrastructure, IT personnel need to stay extra vigilant with changes that deal with IT assets holding any PHI. The compliance risk during a change process comes when stakeholders from various departments participate in the change planning process. In this case, any one of the stakeholders could become the unintended recipient of an automated notification containing sensitive information; they could even share the change plan with their team to keep them in the loop, enabling unaudited access. Sometimes, technicians save a local copy of the change implementation document and forget to delete it later, increasing the risk of misuse.