-
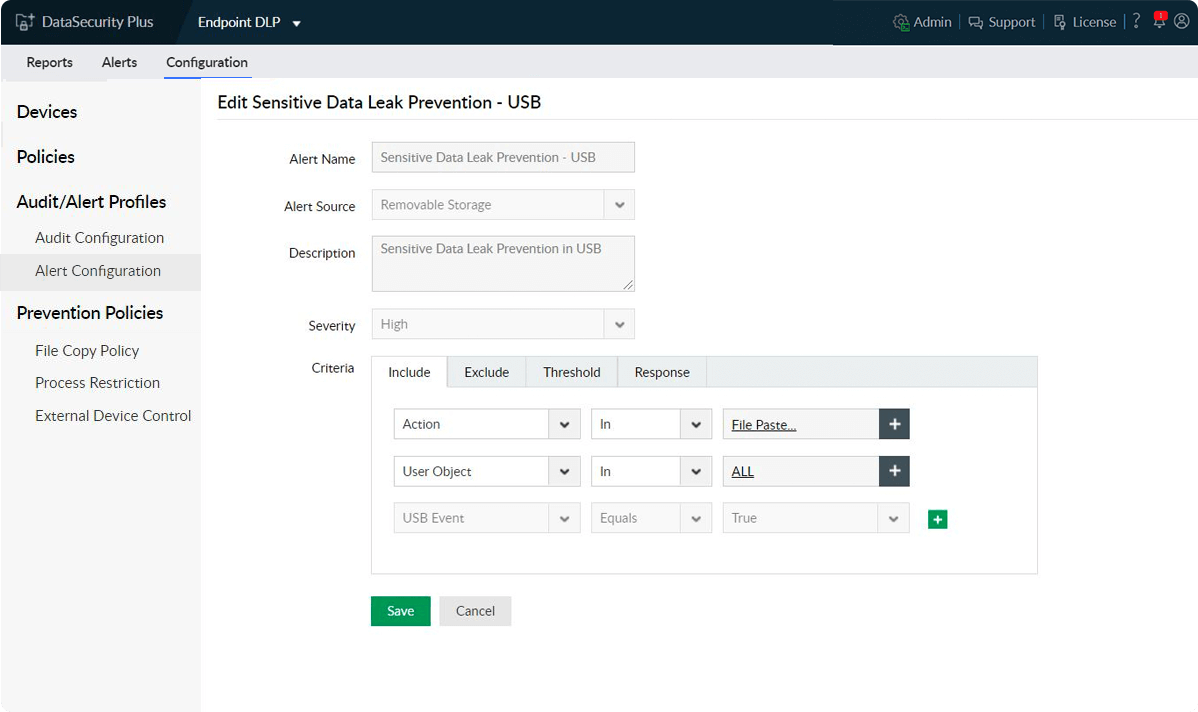
Prevent data theft via USBs
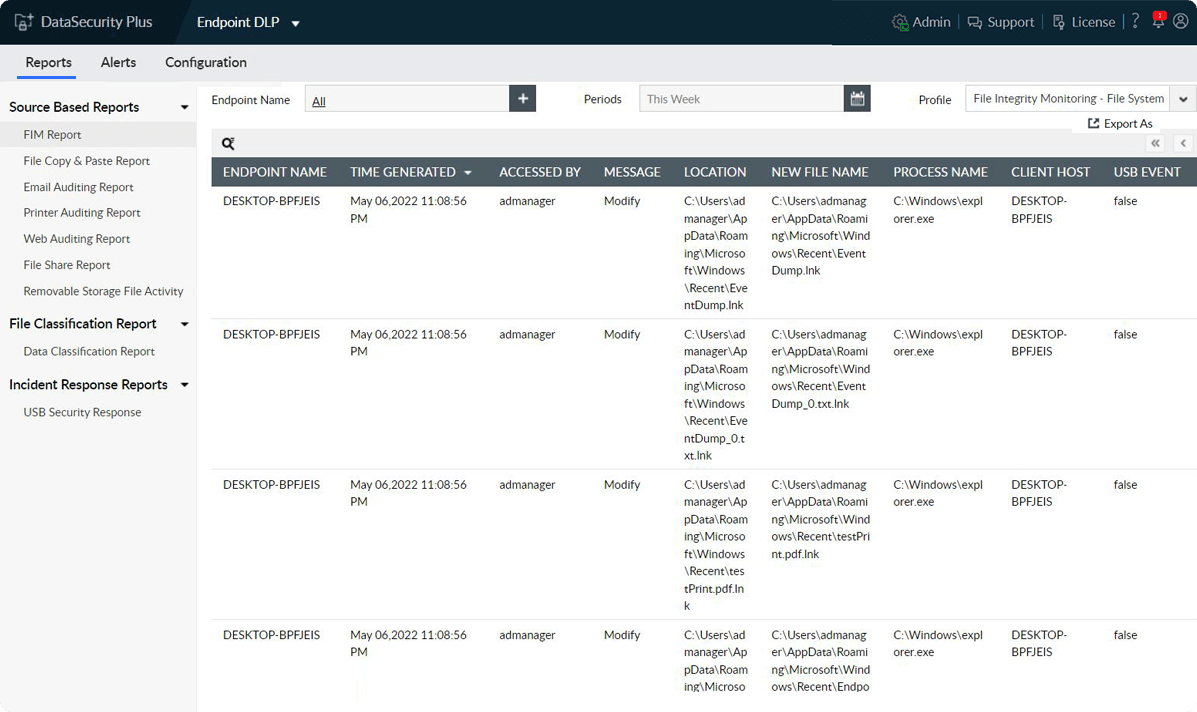
Control data movements via removable storage media by restricting the use of high-risk USBs, making USB sticks read-only, blocking file copy actions, and more.
-
Employ email DLP
Quickly detect and block emails in Outlook containing high-value business information as attachments from being sent.
-
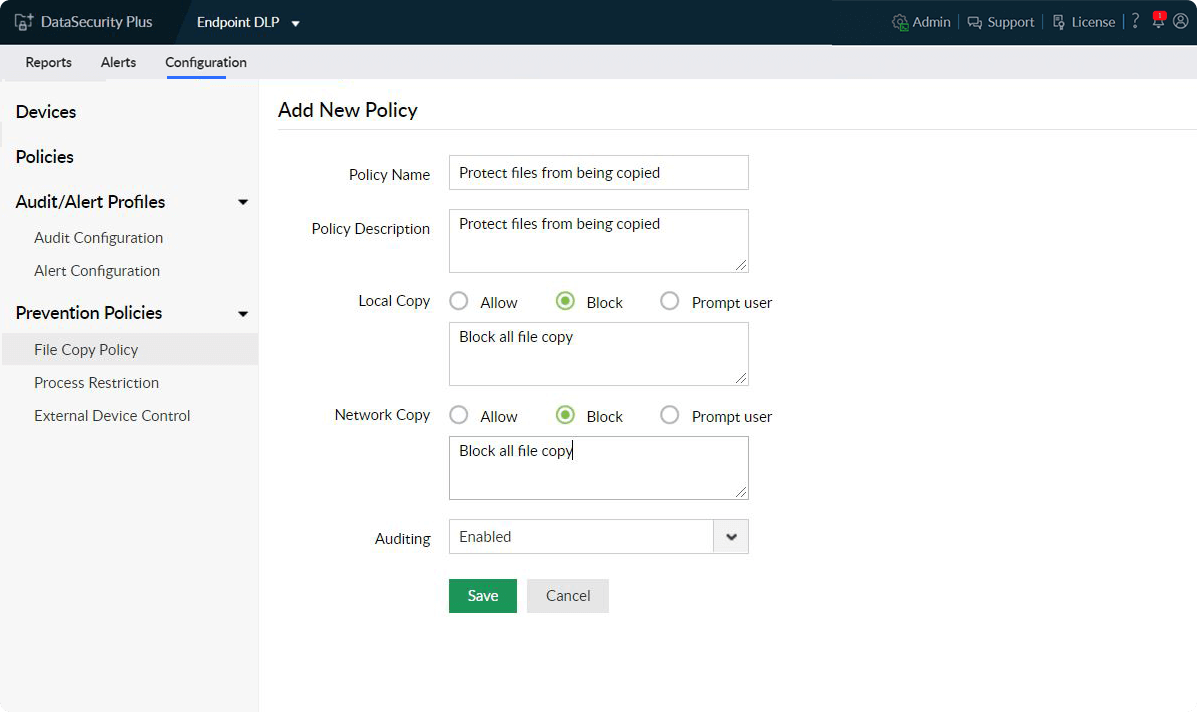
Use preconfigured DLP policies
Detect suspicious user behavior, potential malware intrusion, data leak attempts, etc., and initiate threat responses to manage security issues using our built-in DLP policies.
-
Deploy anti-data-theft measures
Block the use of Wi-Fi, Bluetooth, and CD/DVD drives; enforce application control; restrict the use of risky and malware-infested cloud applications; and more.
Control and keep track of your business-critical data with our data leak prevention solution.