-
Locate business-critical data
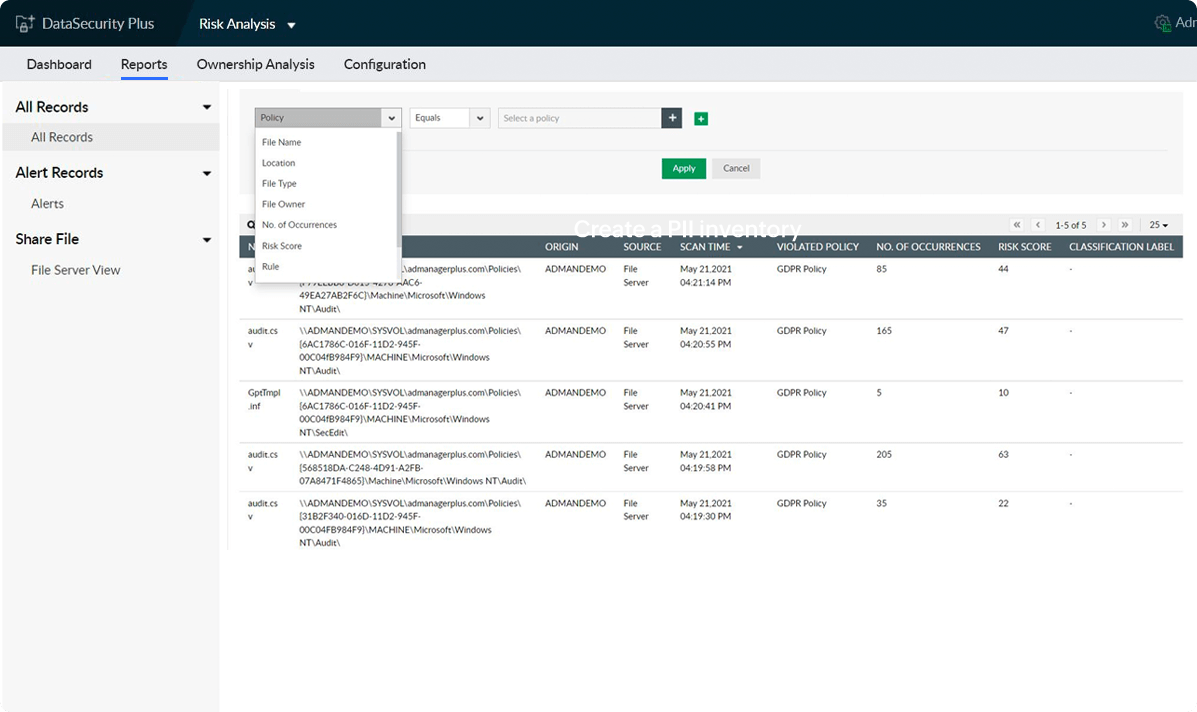
Scan through data repositories like Windows file servers and MS SQL database servers to find PII by matching key phrases or regular expression patterns.
-
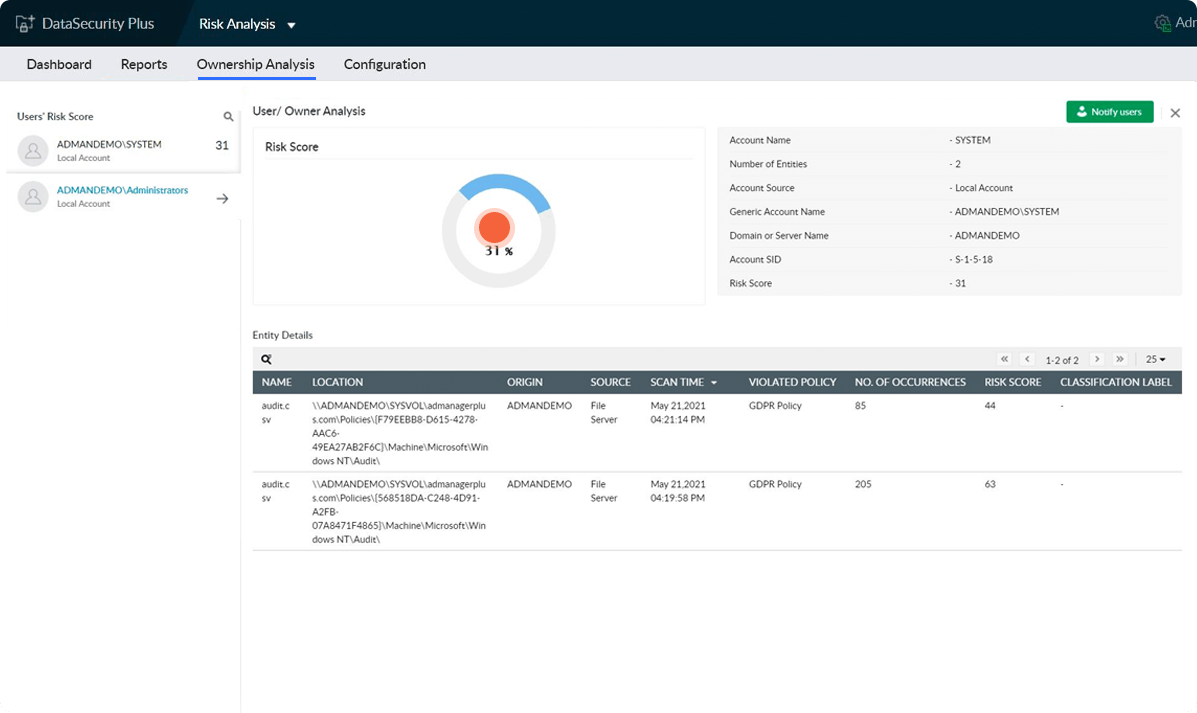
Analyze personal data discovered
Scrutinize various contextual details of files containing sensitive data like who owns them, who has access to them, what type of data they hold, their last modification times, etc.
-
Initiate data risk assessment
Calculate levels of risk associated with files by analyzing their content and contextual details. Use email notifications to alert data owners of the presence of vulnerable, sensitive data.
-
Comply with GDPR, CCPA, etc
Use our built-in data discovery policies and rules to locate compliance-specific sensitive data. Also, find organization-specific sensitive data by building custom data discovery rules.
Take control of the sensitive data your organization houses with our data discovery software.