Das Auditing von Datenbank-Aktivitäten ist ein wichtiger Schritt, wenn Sie Ihre Datenbanken besser schützen möchten. Dazu gehört es, Schwachstellen aufzudecken, wie standardmäßige oder schwache Anmeldedaten, übermäßige Benutzer- und Gruppenberechtigungen und ungepatchte Datenbanken. Die Angreifer nutzen diese Schwachstellen aus, um ihre eigenen Ziele zu erreichen und z. B. Berechtigungen zu eskalieren sowie SQL-Injection- und DoS-Angriffe durchzuführen. Im Ergebnis wird es immer zwingender erforderlich, die Datenbankaktivitäten aus Gründen der Sicherheit und Compliance zu prüfen.
EventLog Analyzer ist eine umfassende Lösung für Protokollmanagement, Auditing und IT-Compliance-Verwaltung, die automatisch alle Arten von MySQL-Protokollen importiert, analysiert sowie Berichte zu diesen erstellt.
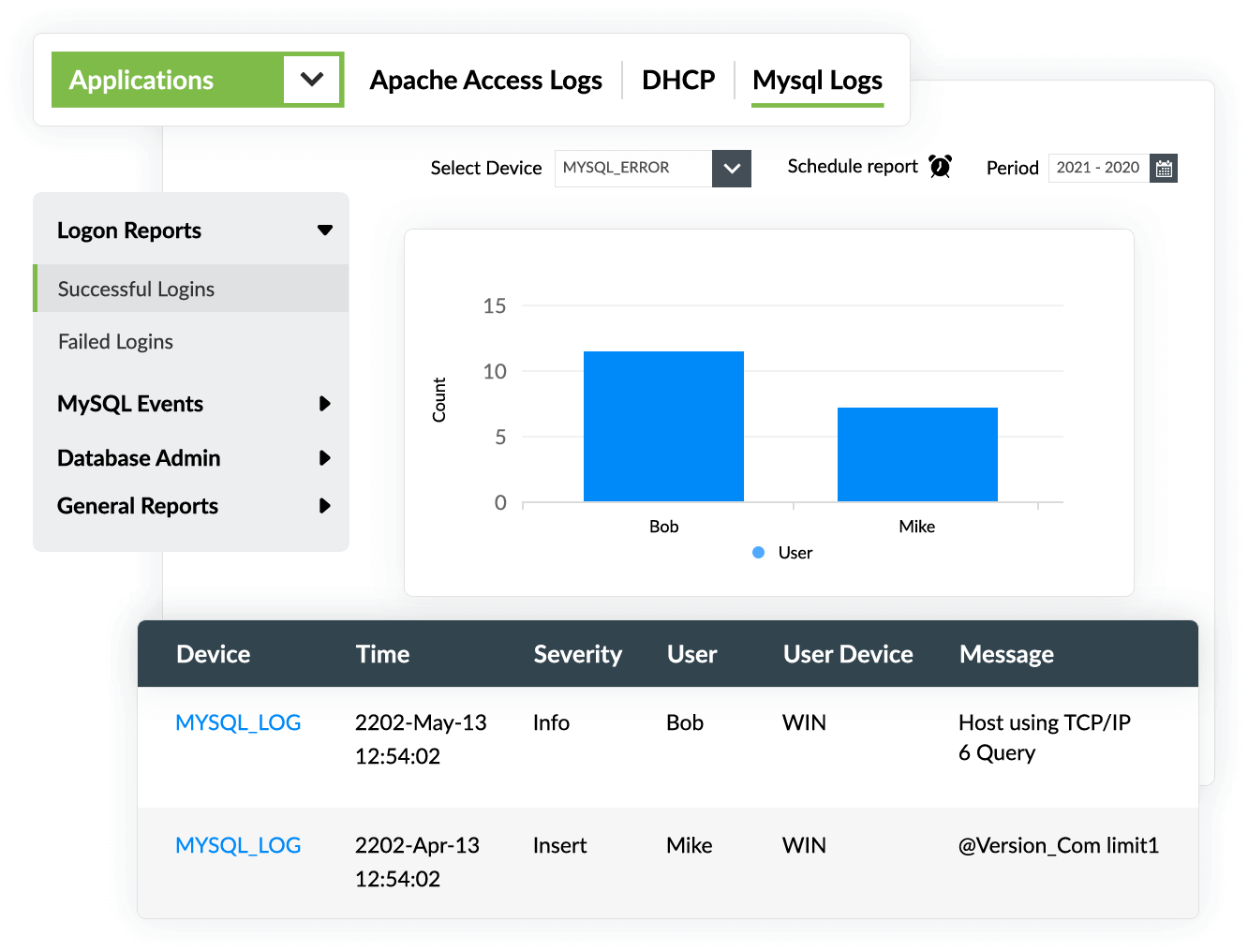
The first step in auditing MySQL databases is to collect their logs. EventLog Analyzer can automatically import and analyze logs from all server instances in the network.

The first step in auditing MySQL databases is to collect their logs. EventLog Analyzer can automatically import and analyze logs from all server instances in the network.
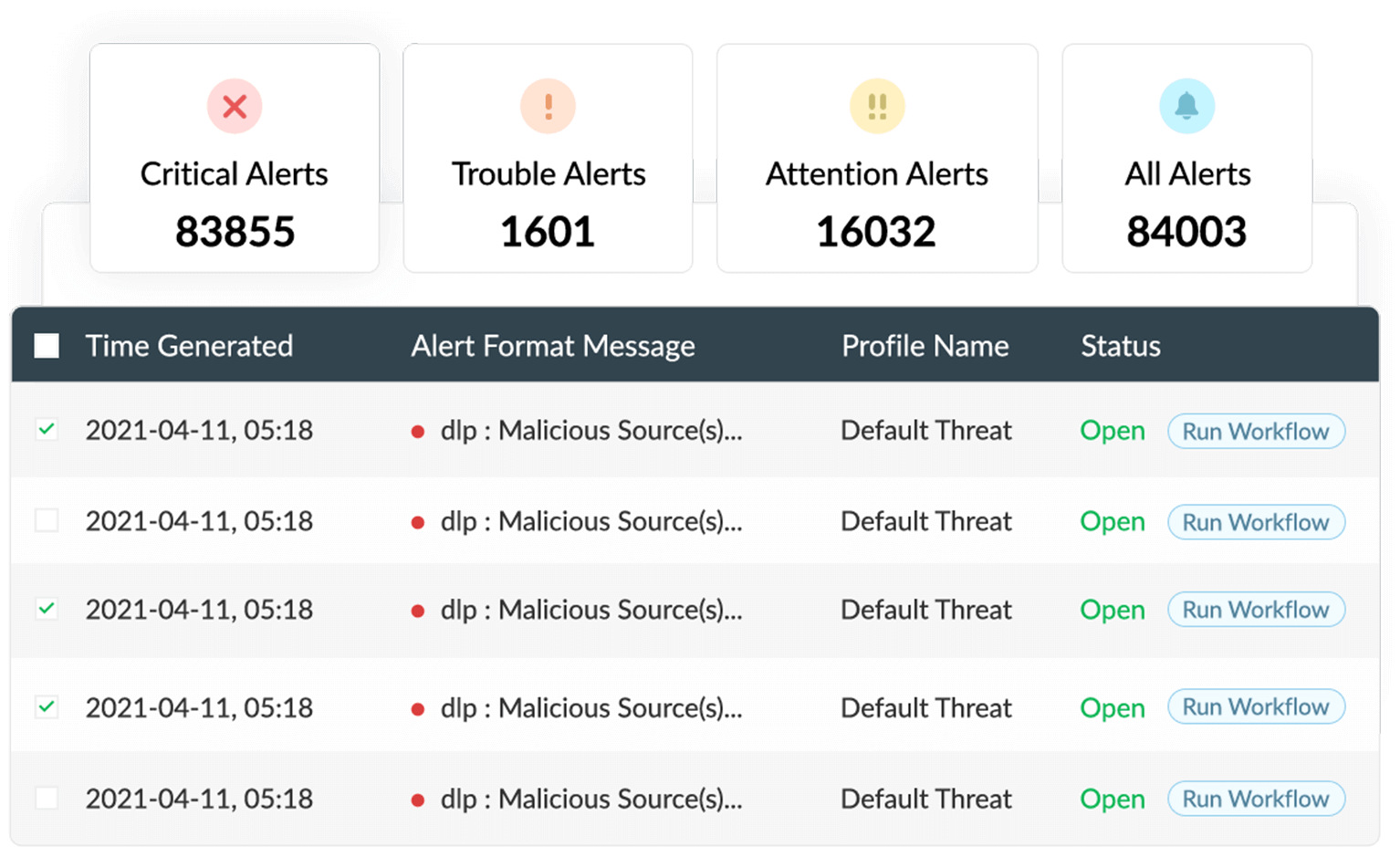
EventLog Analyzer provides real-time alerts on security incidents, such as privilege escalation, changes to audit policies, and repeated login failures. By monitoring these changes, you can ensure database security easily.
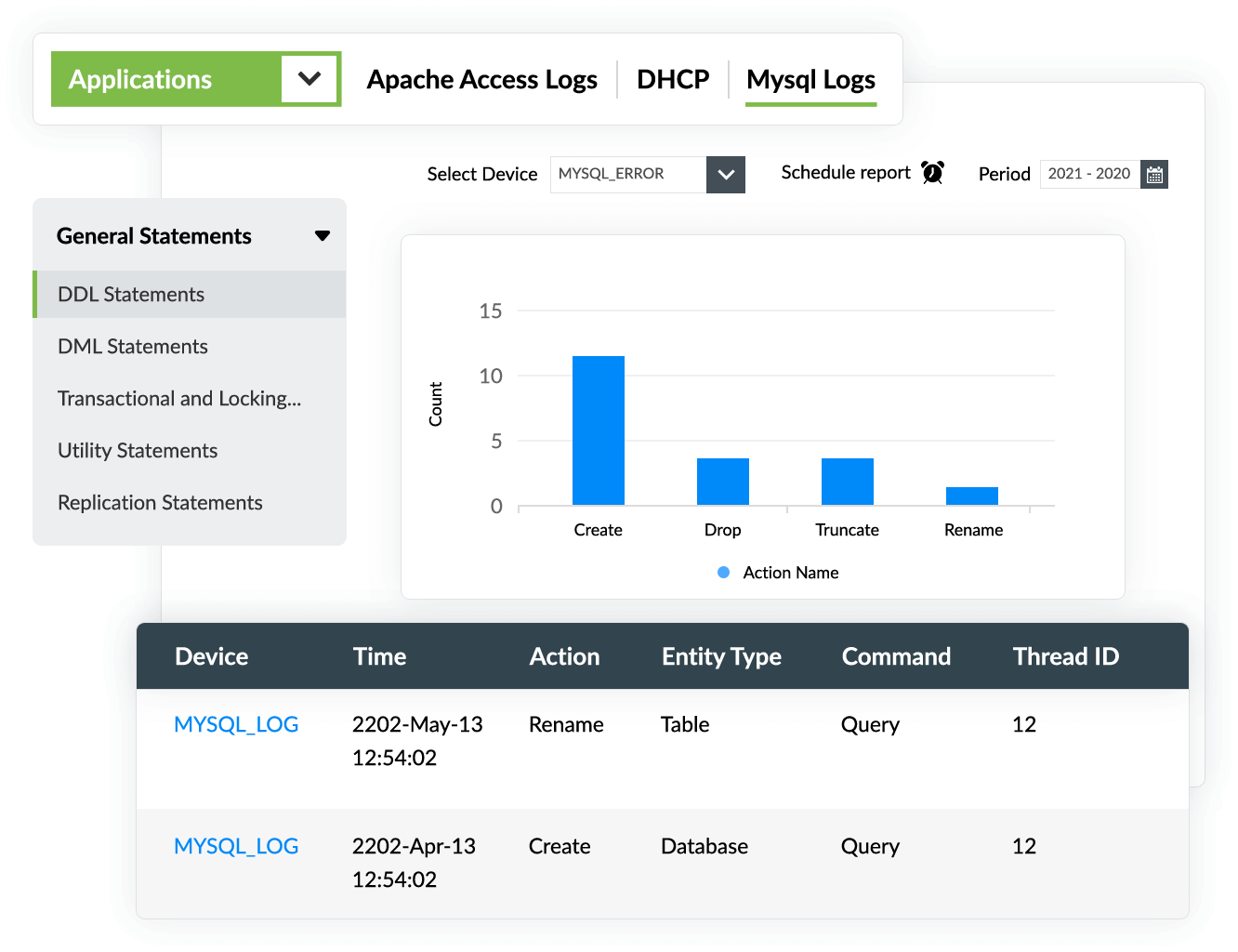
With EventLog Analyzer, you can monitor and investigate DDL actions, such as create, drop, truncate, and rename, that were executed in your database. Gain in-depth insights into each action, such as the time it occurred, who executed the command, and how frequently it was executed, with EventLog Analyzer's comprehensive reports.
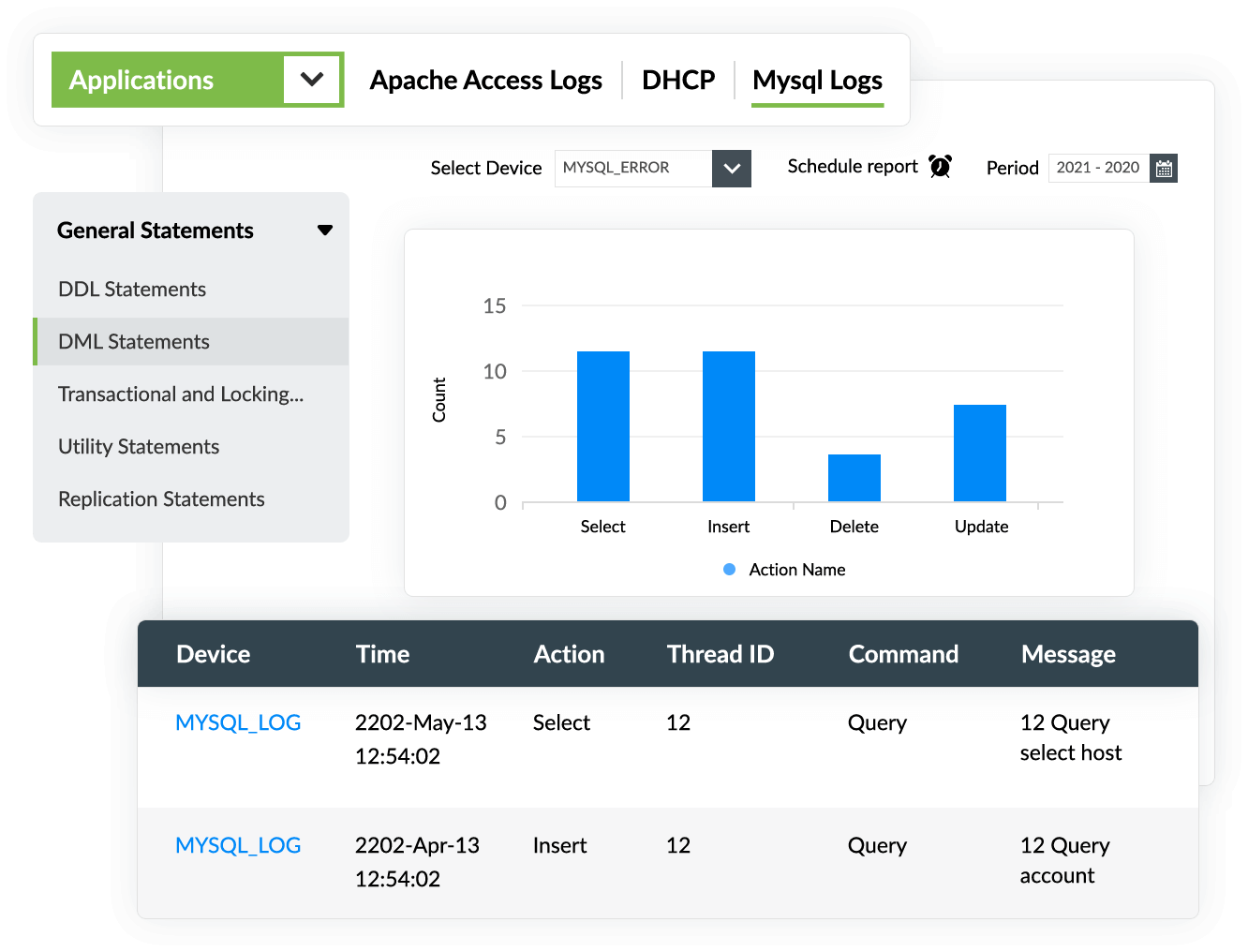
In addition to auditing DDL operations, EventLog Analyzer monitors and analyzes DML actions, such as select, insert, delete, and update, that were executed in your database. EventLog Analyzer's exhaustive reports detail the query executed, when it occurred, and the number of times it was executed.

In addition to auditing DDL operations, EventLog Analyzer monitors and analyzes DML actions, such as select, insert, delete, and update, that were executed in your database. EventLog Analyzer's exhaustive reports detail the query executed, when it occurred, and the number of times it was executed.
With EventLog Analyzer, you can securely collect and audit logs from your Microsoft SQL servers to detect security threats, prevent unauthorized access to confidential information, and comply with various data privacy regulations effortlessly.
Protect your Oracle Database servers from internal and external security threats by auditing their logs using EventLog Analyzer. Monitor database server changes, unauthorized user activities, unauthorized access to sensitive data, SQL injection, and DoS attack attempts.
Collect, parse, and analyze Apache web server logs efficiently with EventLog Analyzer. Enhance your network security with in-depth analytical reports and receive alerts immediately via email or SMS when a security threat is detected on your Apache server.
Mitigate security threats with EventLog Analyzer's comprehensive, graphical reports that provide in-depth information on user logins, error events, potential security attacks, unauthorized file operations, and more occurring on your IIS web servers and FTP servers.
Monitor security events on your perimeter network devices, such as routers, switches, firewalls, and IDS/IPS tools, using EventLog Analyzer. Secure your organization's network against security threats with real-time alerts and automated response workflows.
EventLog Analyzer raises alerts and executes response actions in real time when critical activities, such as changes to access permissions and confidential data, occur on your MySQL database servers.
EventLog Analyzer has over 30 predefined correlation rules for correlating and detecting attack patterns in logs from multiple devices across your organization's network.
EventLog Analyzer's powerful log search engine helps you search through thousands of raw MySQL log files to detect and mitigate security threats. It also performs forensic analysis on logs to find the root causes of security breaches.
Assign tickets to security administrators and efficiently respond to security incidents on your MySQL server using EventLog Analyzer's incident management system.
Fulfill the requirements of various data privacy regulations, such as the GDPR, HIPAA, the GLBA, the PDPA, and the CCPA, using EventLog Analyzer's audit-ready compliance reports.
MySQL log files are a security administrator's best friend. Whether it is an unintentional error, a security breach, or a system crash, logs can provide answers. MySQL has several log types that provide insights into different occurrences on the MySQL server. The error log and the query log are the most important ones that should be added to your monitoring list.
Manually examining these logs is time-consuming. EventLog Analyzer provides you with a reliable database monitoring system that simplifies your database management and auditing.
The major reason to continuously audit your MySQL database is to detect security threats in their early stages. Further, compliance regulations like HIPAA, SOX, and the PCI DSS require organizations to track access to sensitive information. Regulations such as the GDPR require organizations to report data breaches to authorities within a specific time frame.
To meet these compliance demands, an audit trail is crucial. Auditing user access to critical data speeds up the incident detection and incident response processes. Continuous auditing also allows organizations to identify the causes of their security and data integrity issues and to find ways to fix them.
In addition to collecting, parsing, and analyzing your MySQL database logs, EventLog Analyzer provides intuitive graphical dashboards and reports that provide details about the security events occurring in your MySQL database. You can easily investigate various events, such as login and logout events, server events, database access attempts, and changes to database schema.