Configuring TSIG keys
TSIG (Transaction Signature)
TSIG is a security protocol used in the Domain Name System (DNS) to provide authenticated and secure communications between DNS servers and between DNS servers and clients. TSIG uses shared secret keys and cryptographic signatures to validate that the DNS messages are authentic and have not been tampered with. It's primarily used for
- Securing Zone Transfers: Ensuring that AXFR zone transfers occur only between authorized servers.
- Securing Dynamic Updates: Authenticating requests to update DNS records dynamically, especially in Dynamic DNS (DDNS) environments.
- Authenticating DNS Queries and Responses: Verifying the authenticity of both the query and the response in DNS transactions.
TSIG adds an additional layer of security to DNS operations that is not provided by standard DNS, which by itself has no mechanism for authenticating the source or integrity of DNS data.
TSIG Key Templates in DDI Central
The Key Templates are saved under the TSIG Key Templates tab on the Config page with the following fields as shown below:
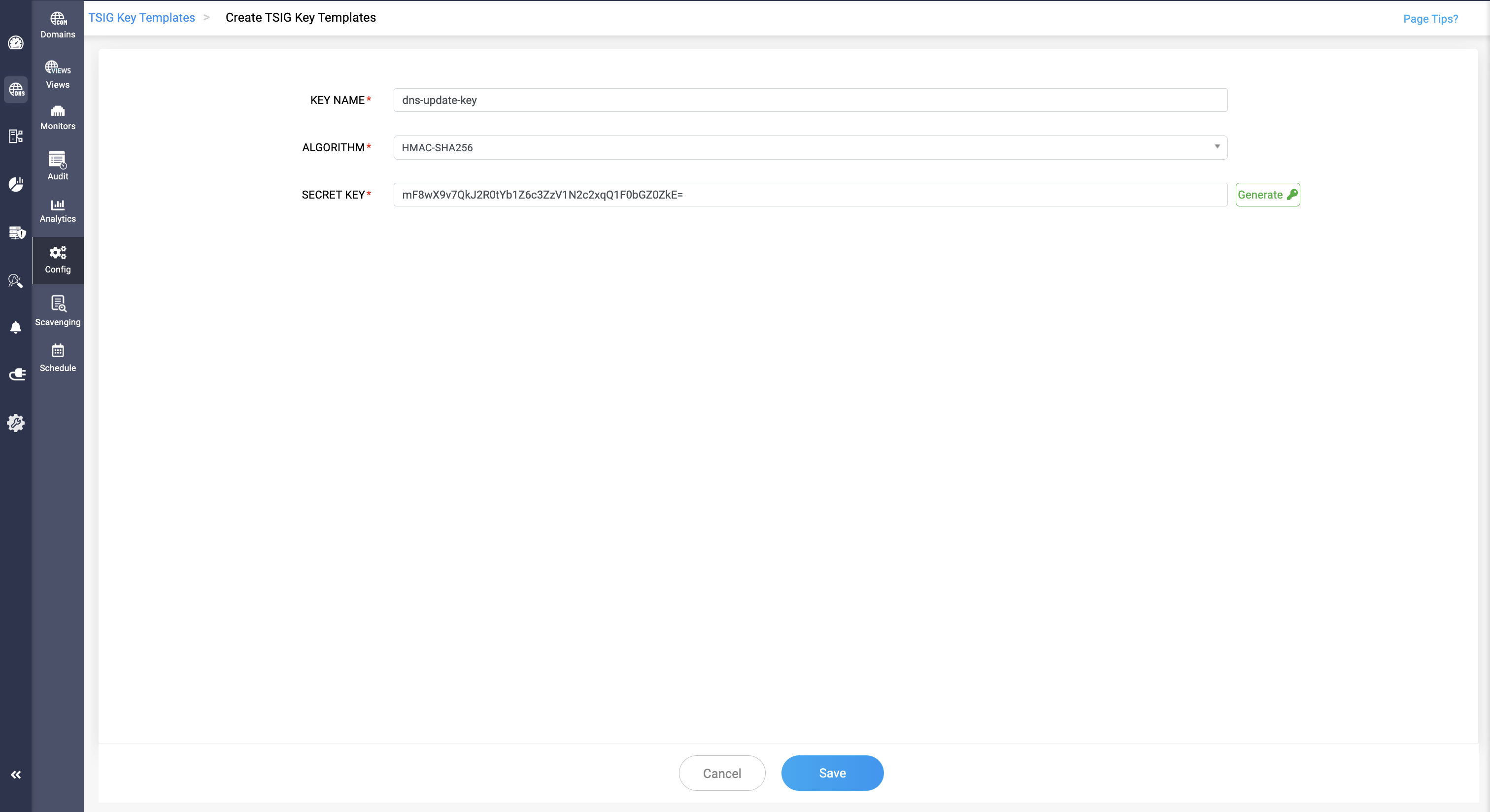
Key Name
The Key Name is mainly used to identify the key across the primary and secondary name servers. Ensure a unique name is assigned to the key.
Algorithm
TSIG Algorithm serves essentially as a cryptographic hash function that executes HMAC operations to generate the TSIG key value. Currently, CloudDNS supports the following algorithms HMAC MD5, HMAC SHA1, HMAC SHA224, HMAC SHA256, HMAC SHA384, and HMAC SHA512 to generate the TSIG key.
Secret Key
The secret key value is an encoded base64 string with a maximum value of 255 characters that acts as a shared signature to provide transaction-level authentication for the name servers during zone transfer operations.