- Overview
- Features
- Benefits
- FAQs
- Next step
Features
Identity threat detection and responseAnalyze the threat environment using identity risk assessment
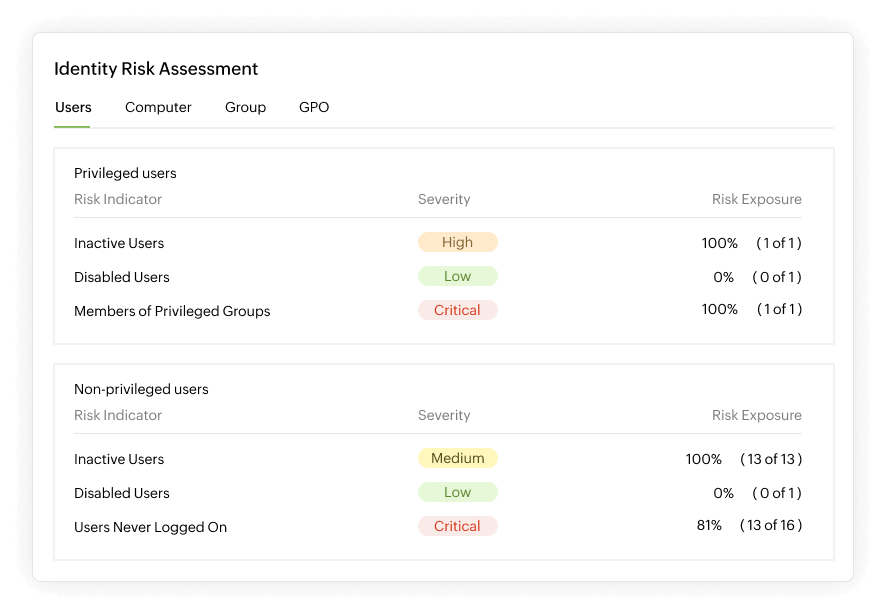
AD360 offers a comprehensive Identity Risk Assessment, providing a detailed perspective on the threat landscape within your Active Directory (AD) environment and the factors influencing its health and performance. The tool meticulously scrutinizes your AD network, identifies potential vulnerabilities, assesses their impact, and provides insights into potential harm. Moreover, it offers proactive measures to eliminate these risks and fortify your AD network. This report serves as a valuable resource for organizations seeking a thorough evaluation of their AD, revealing existing security threats, highlighting areas needing attention, outlining deficient policies, and shedding light on their overall security posture.
- Comprehensively evaluate the threat landscape in Active Directory (AD) environment
- Gain a detailed perspective on factors influencing AD health and performance
- Identify and assess potential vulnerabilities and their impact
- Take proactive steps to eliminate identified risks and strengthen the AD network
Leverage identity threat intelligence and analytics
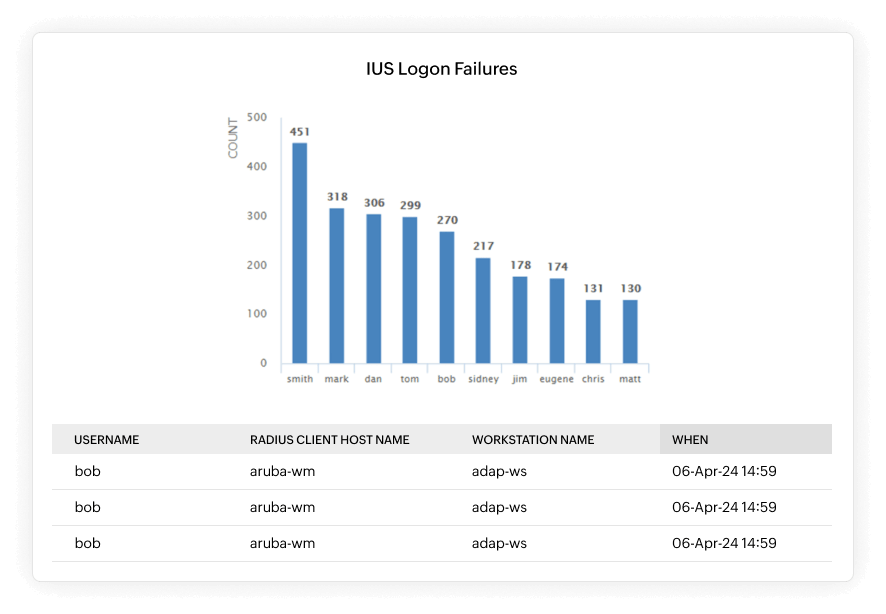
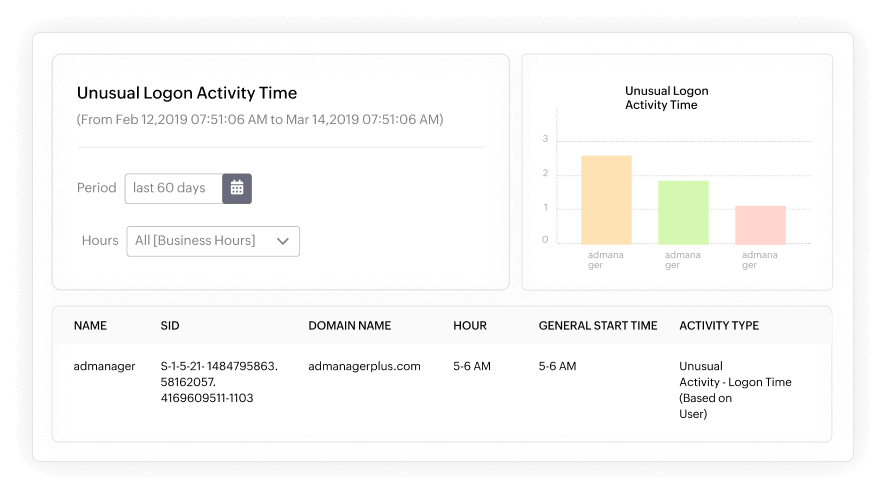
Uncover potential security threats by identifying suspicious user activities, such as events occurring at unusually high volumes and unconventional times. Investigate the source and reasons behind failed logon attempts, focusing on user accounts with the highest percentages of login failures. Establish a proactive defense system by defining alert profiles based on metrics like user activity count and time. Create rules that compare current data with previously generated data, triggering alerts whenever real-time data deviates from established patterns. This ensures swift detection of any anomalies in user behavior. In addition, monitor and respond to potential breaches by tracking file deletions, unauthorized alterations, and anomalous spikes in file access attempts. Utilize a diverse set of reports on anomalous file activities to gain insights and take timely action against any irregularities in your system.
- Establish a proactive defense system by defining alert profiles using metrics like user activity count and time
- Investigate the source and reasons behind failed logon attempts
- Prioritize user accounts with the highest percentages of login failures
- Create rules comparing current data with historical patterns and trigger alerts when real-time data deviates from established norms
- Track file deletions, unauthorized alterations, and anomalous spikes in file access attempts
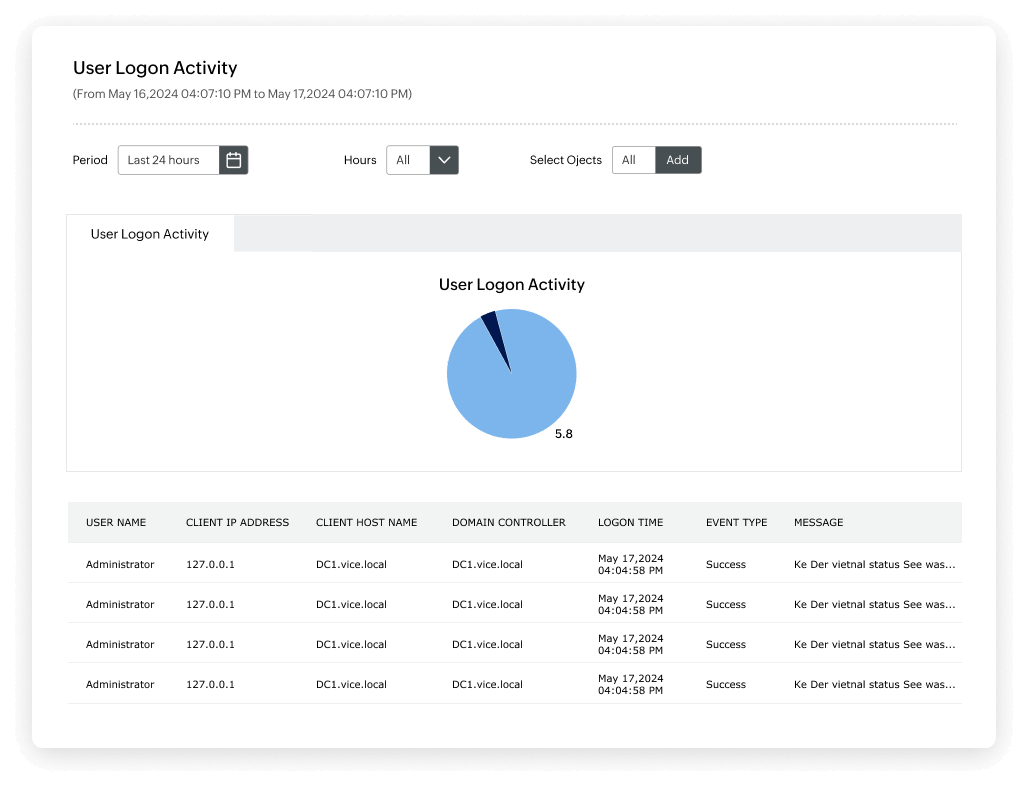
Automate UBA-powered threat response for enhanced security incidents management
Gain access to an automated threat response system to handle security incidents effectively. This includes the ability to disconnect sessions of rogue users, shutdown infected systems, and implement other appropriate response measures. The feature utilizes machine learning capabilities to identify anomalous user login behavior, encompassing sudden spikes in logon failures, unusual login times, and instances where a user employs remote access for the first time. Threat detection is enhanced by monitoring abrupt deviations in typical user behavior, such as the emergence of new processes on a server or an unusual surge in account lockouts. Threat intelligence is also refined by updating users' baseline behavior daily, minimizing both false positives and true negatives in the security alert system. Alert system administrators by receiving proactive notifications to detect early signs of privilege abuse, such as unusual timings or volumes of user management activities. Attain a comprehensive overview of all anomalous activities performed by users within your organization on a daily basis. This multifaceted approach ensures a robust defense against potential security threats and facilitates proactive response strategies.
- Effectively handle security incidents with automated response measures
- Disconnects sessions of rogue users, shuts down infected systems, and more
- Utilizes machine learning to identify anomalous user login behavior
- Detects early signs of privilege abuse, such as unusual timings or volumes of user management activities
Advance security event threat detection and analysis
Implement a comprehensive security strategy by auditing privileged user logons, logoffs, and resource access. Utilize machine learning (ML)-based user and entity behavior analytics to proactively identify unusual user activities and potential user-based threats. Enhance security further by monitoring user activities and employing signature-based MITRE ATT&CK techniques to detect and thwart attempts at privilege escalation or misuse. Utilize a security analytics dashboard and incident timeline to investigate suspicious authentication failures on critical systems, enabling the early detection and prevention of brute force or unauthorized network access attempts. Extend security measures to monitor access to databases and sensitive data on file servers. Utilize file integrity monitoring and column integrity monitoring to gain visibility into unauthorized data access, ensuring a robust defense against potential security threats.
- Audit privileged user logons, logoffs, and resource access
- Monitor user activities and employ signature-based MITRE ATT&CK techniques
- Monitor access to databases and sensitive data on file servers
- Utilize file integrity monitoring and column integrity monitoring
Benefits of identity-first security
Proactive identity-security measures
AD360's Identity risk assessment provides a detailed perspective, revealing security threats and deficiencies, allowing organizations to proactively fortify their AD network.
Swift threat detection
Anomaly detection and UBA features of AD360 swiftly identify potential security threats, ensuring a proactive defense system, swift detection of anomalies in user behavior, and timely response to potential breaches.
ML-based analytics
Security event threat detection implements a comprehensive strategy, utilizing ML-based analytics and signature-based techniques to identify unusual user activities, ensuring a robust defense against security breaches.
Comprehensive security coverage
Log360 not only covers security event threat detection but also encompasses network threat detection and endpoint threat detection, providing a comprehensive solution for identifying and preventing security threats across various vectors.
FAQs
How does AD360 monitor and detect security events and threats?
AD360 uses auditing to monitor privileged user logons, logoffs, and resource access. It employs MITRE ATT&CK capabilities for user activity monitoring and threat detection. Additionally, AD360 monitors database and sensitive file server access, utilizing file integrity and column integrity monitoring for overall security enhancement.
Can AD360 detect and prevent brute force attempts?
Yes, AD360 utilizes machine learning, MITRE ATT&CK techniques, and incident timelines to investigate and prevent brute force or unauthorized network access attempts.
Does AD360 automatically respond to security incidents?
Yes, AD360 uses automated measures, including disconnecting rogue user sessions, shutting down infected systems, and more. Machine learning is employed to identify anomalous user logins and detect early signs of privilege abuse, such as unusual timings or volumes of user management activities.
How does AD360 handle deviations in user activity metrics to enhance security?
AD360 establishes a defense system by defining alert profiles based on user activity metrics. It investigates failed logon attempts, prioritizes high-risk user accounts, and sets rules for comparing current data with historical patterns. Alerts are triggered for deviations, tracking file deletions, unauthorized alterations, and anomalous file access spikes.
How does Log360 handle ticketing and integration with external help desk tools during incident response?
Log360 automates ticket generation when an alert is triggered, assigning tickets to the appropriate security administrator. Additionally, organizations can integrate Log360 with external help desk tools to automatically create tickets and facilitate seamless collaboration in resolving security incidents.