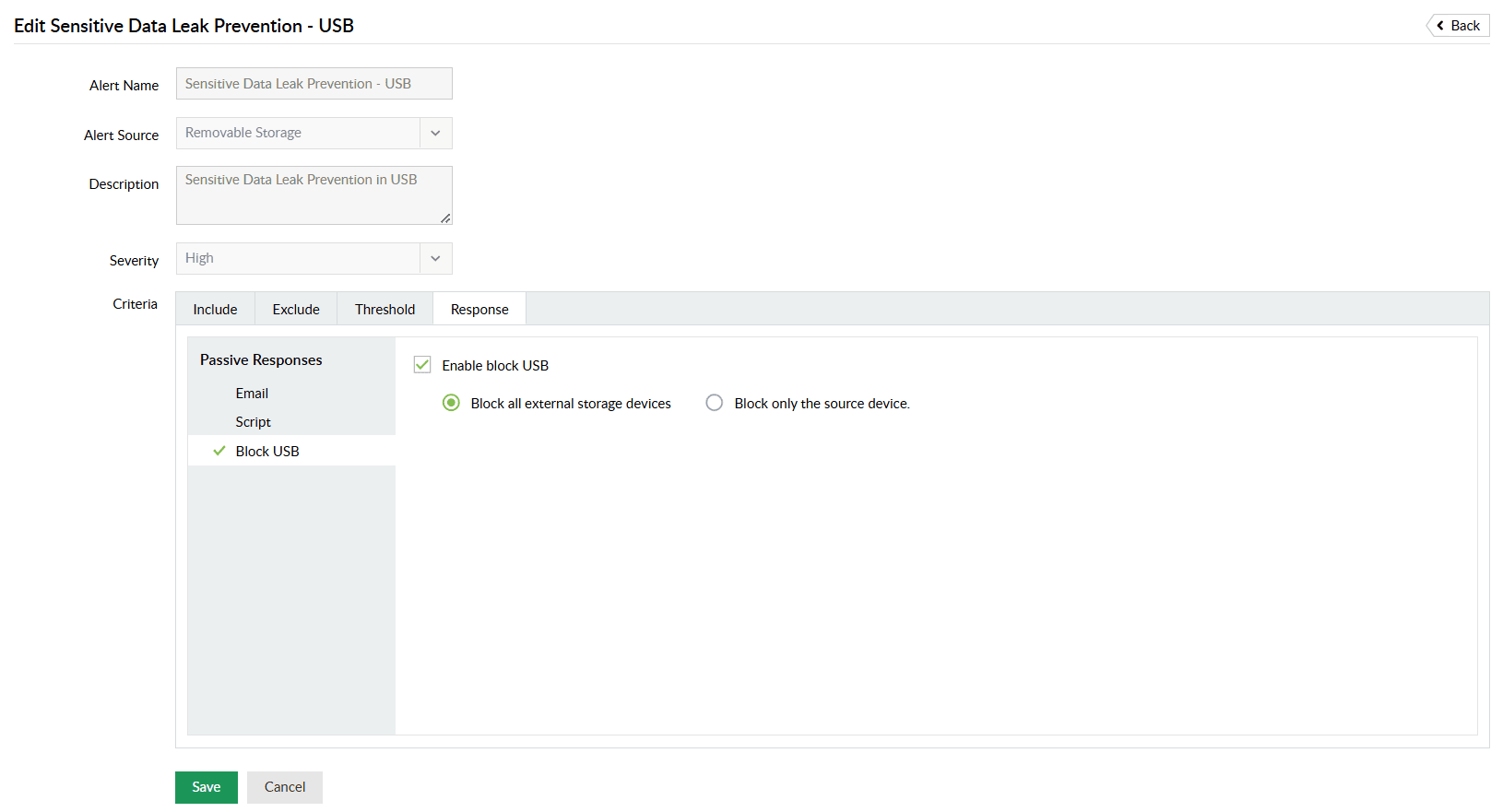
Block business-critical data from being copied to USB devices.
Generate reports on the usage of USB devices and stay compliant with a range of regulatory standards.
Monitor multiple external storage devices, including USB devices, printers, and cameras.
Monitor, track, and analyze your entire organization's removable device usage, including data transfers to and from USB devices.
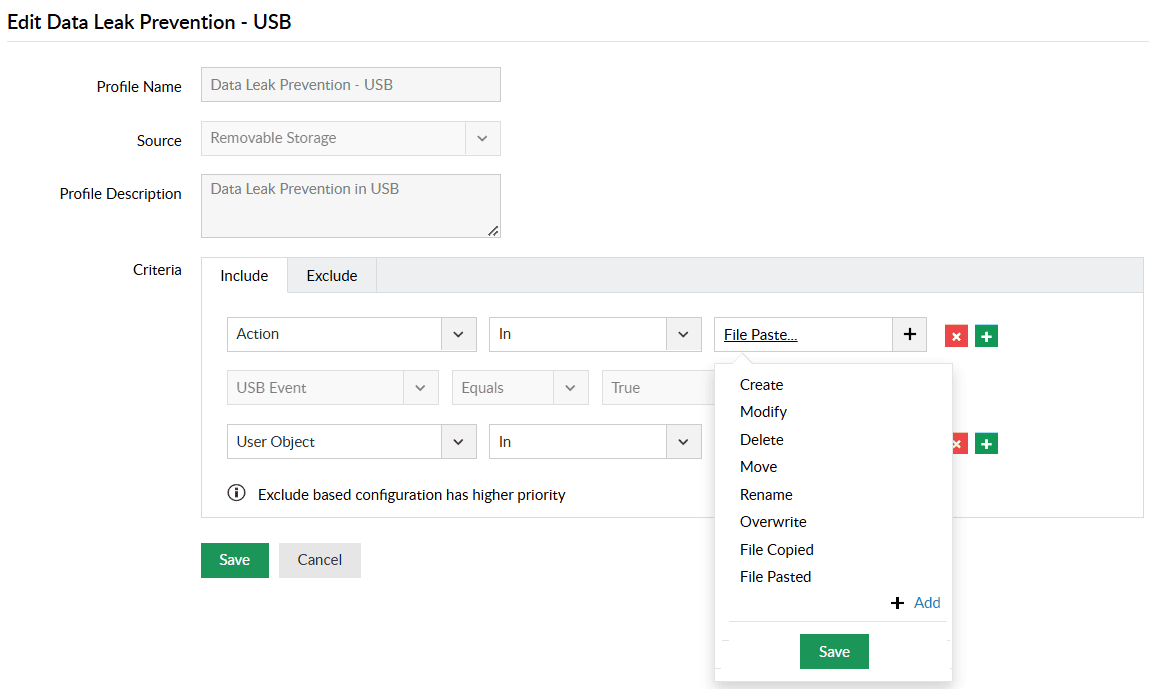
Monitor USB activities closely to identify and report when large files, certain file types, or files containing high-risk content are moved to USB devices.
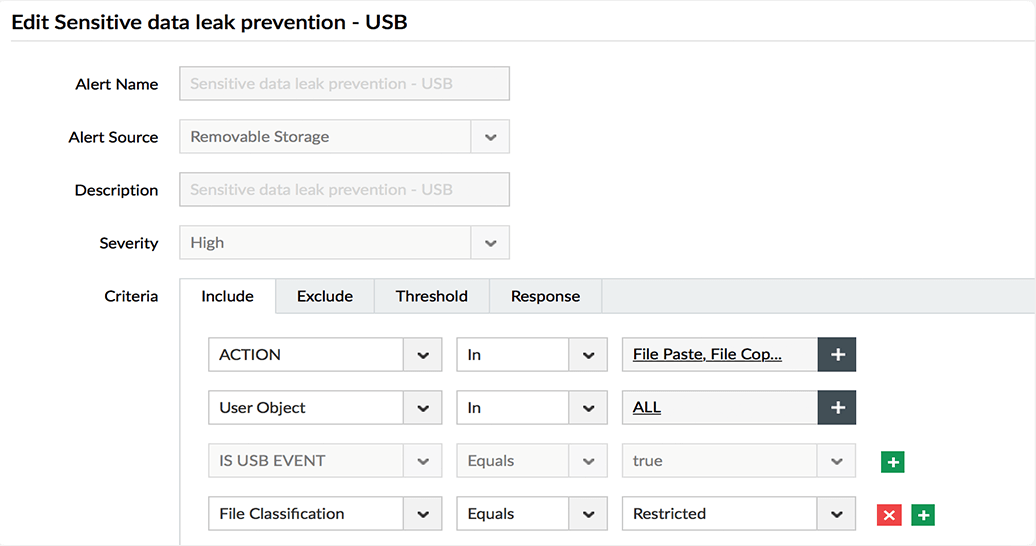
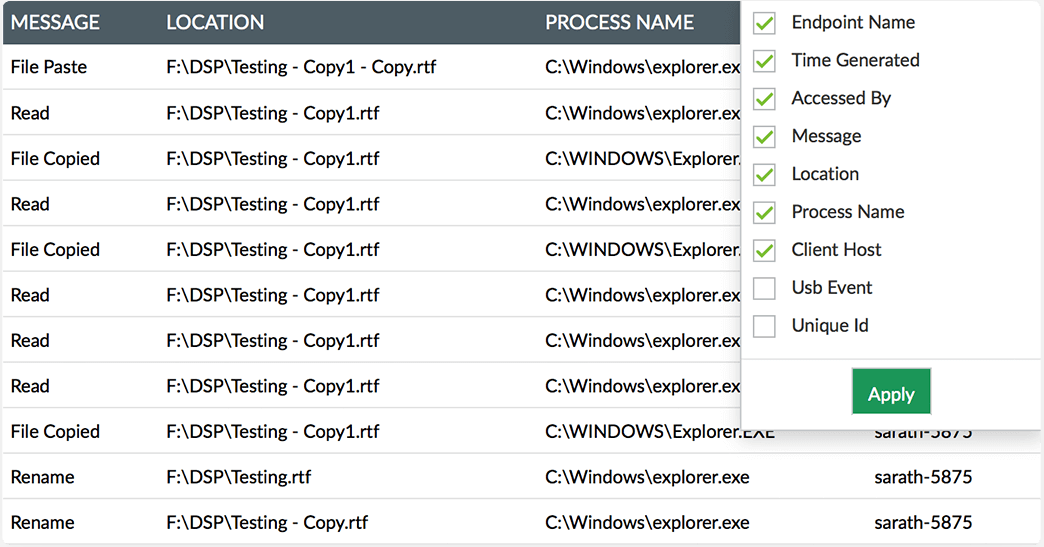
Identify the source, hostname, and time of all USB device events and perform forensic analysis as needed.



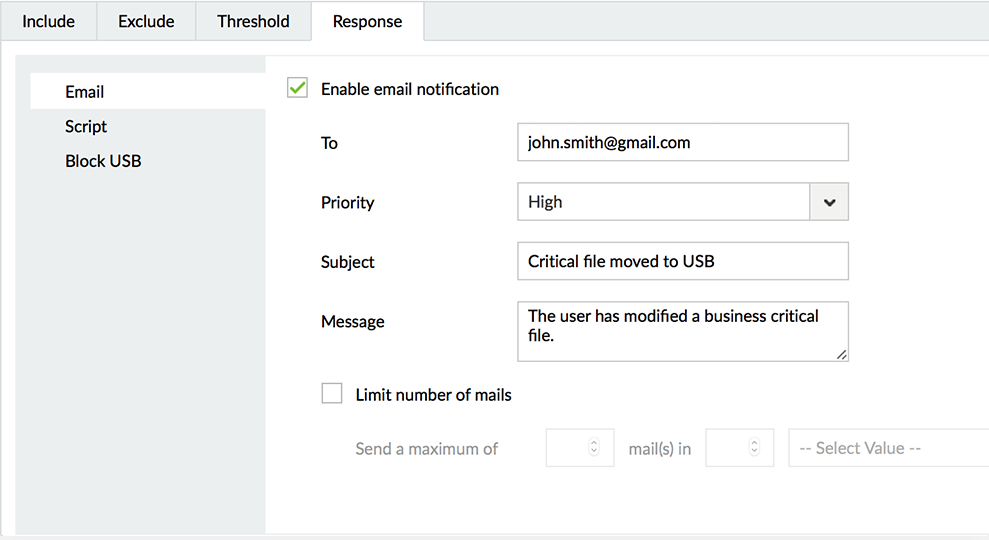
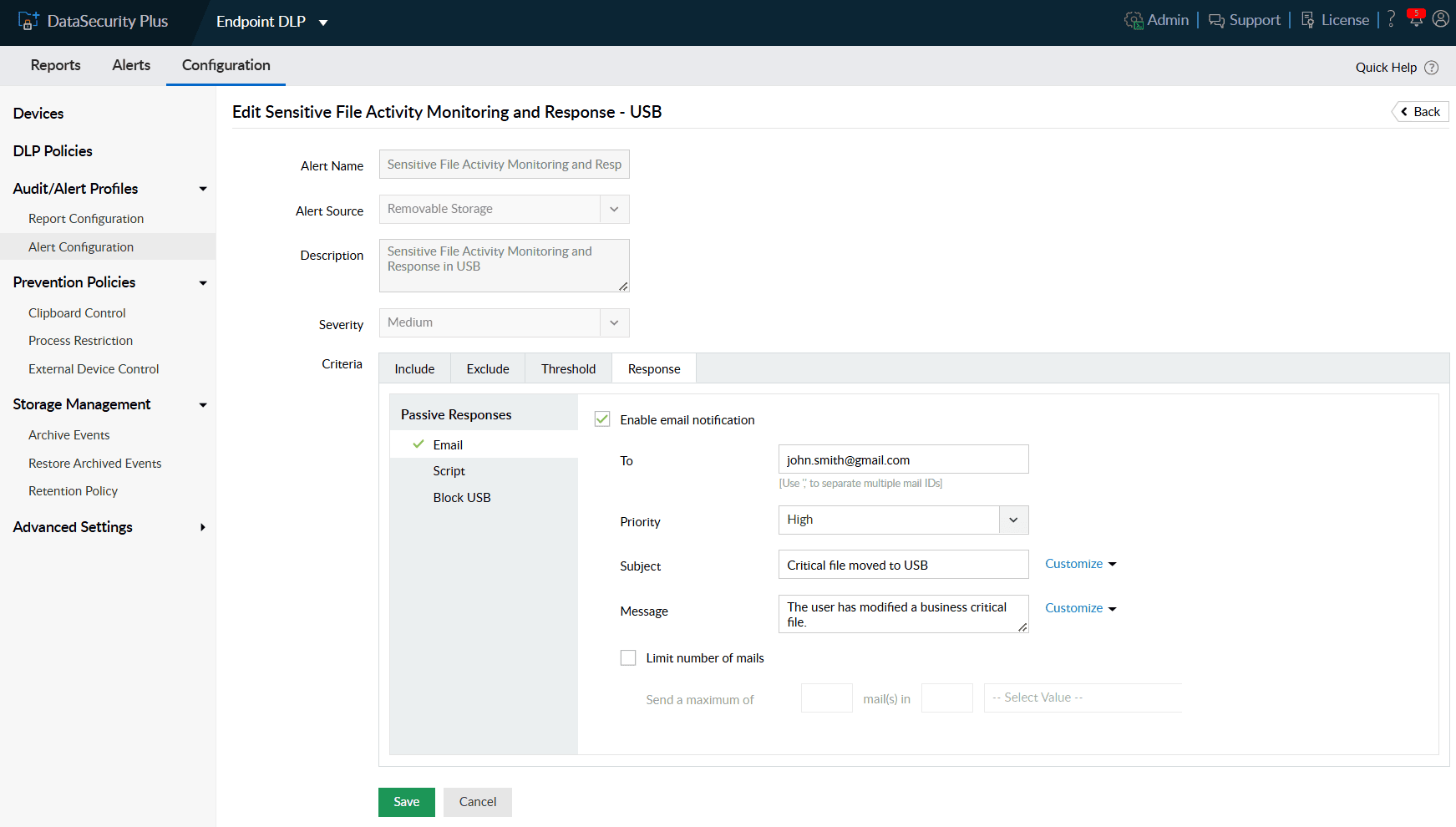
Receive real-time alerts when business-critical files are moved to external storage media, including mobile devices and USB devices.

Use predefined data leak prevention policies to secure your sensitive data against inadvertent loss by making USB devices read-only.

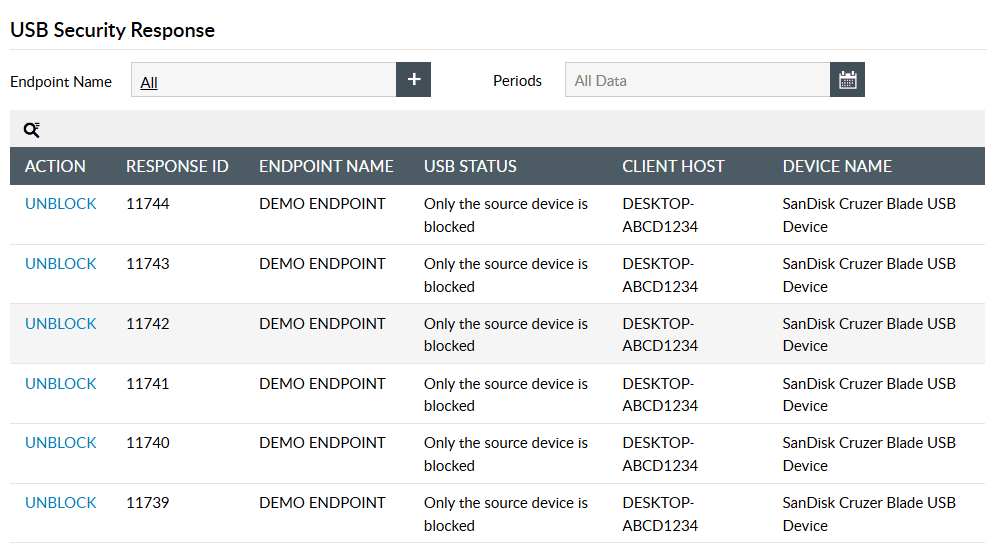
Quickly respond to malicious behavior by blocking users from moving sensitive data to USB devices, preventing potential data theft.

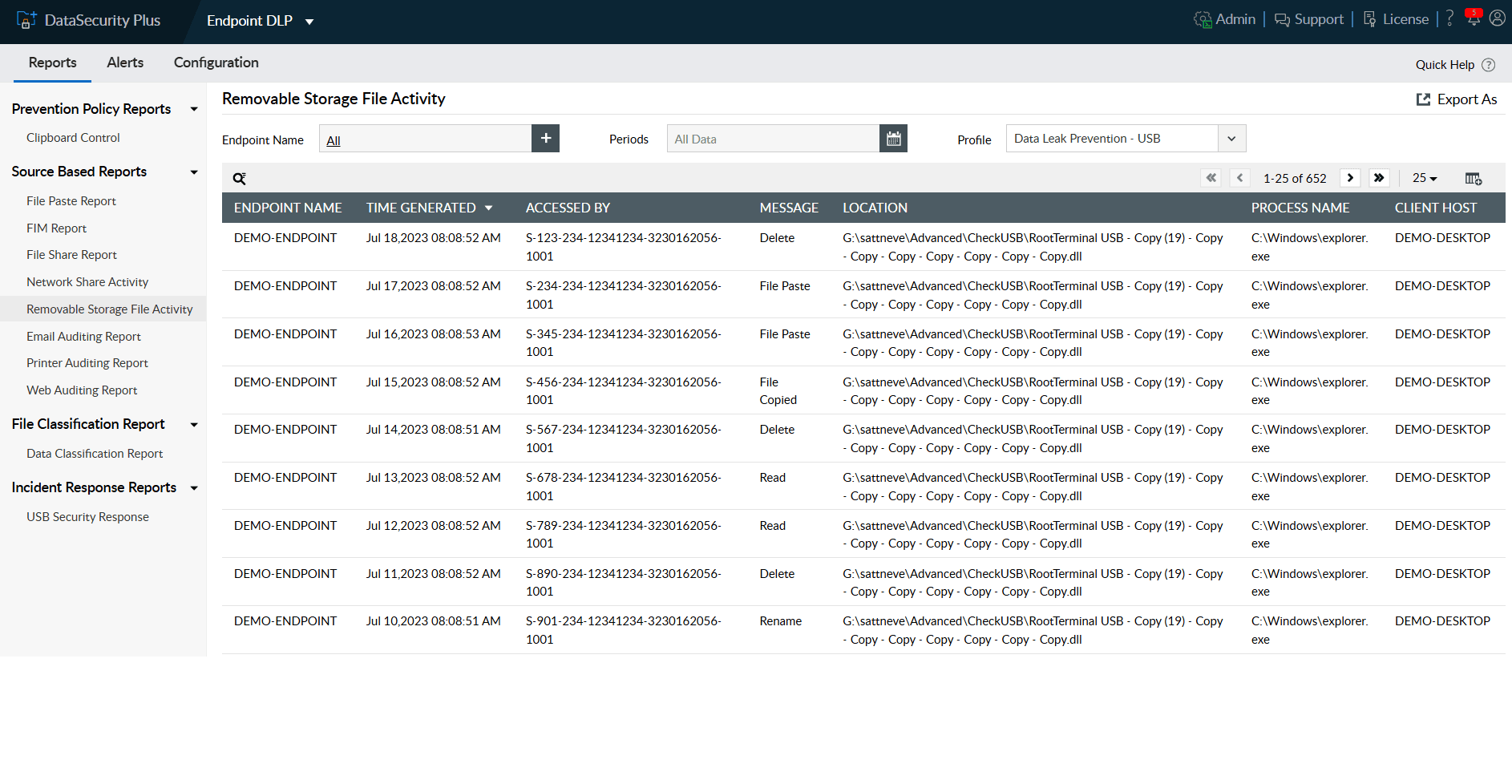
Leverage our USB activity monitoring tool to track peripheral device usage and gain actionable insights into all critical file transfers to and from these devices.
In the event of a security incident, quickly identify the source, event time, location, and more to perform forensic analysis as needed.

Receive instant alerts on file access anomalies on local drives, network shares, and USB devices and maintain detailed audit trails of all file modifications

Block USB ports indefinitely in response to suspicious user behavior, such as permission escalations or sudden spikes in file modifications.
Disable user accounts, terminate network sessions, or execute scripts tailored to your needs in response to malicious user activity.

Detect, disrupt, and prevent sensitive data leaks via endpoints, i.e., USBs, email.
Learn MoreAnalyze file content and context, and classify files based on vulnerability.
Learn MoreDetect and shut down ransomware attack right at inception with an automated threat response mechanism, and get notified with instant, user-defined alerts.
Learn MoreIdentify and respond to potential security threats, and safeguard critical data by monitoring file accesses and modifications in real time.
Learn MoreObtain detailed information on the four ws who accessed what, when, and form where for all files accesses and modifications.
Learn MoreIdentify overexposed files and files with inconsistent permissions, and find out who has access to modify sensitive files.
Learn More