Steps to configure SAML SSO for Wrike
About Wrike
Wrike is a cloud-based project management platform designed for both large enterprises and small- to medium-sized businesses. Wrike offers a comprehensive suite of tools, including Gantt charts, calendars, workload views, and custom dashboards, enabling teams to manage projects, deadlines, and workflows effectively.
The following steps will help you enable single sign-on (SSO) for Wrike from Identity360.
Prerequisites
- The MFA and SSO license for Identity360 is required to enable SSO for enterprise applications.
- Log in to Identity360 as an Admin or Super Admin.
- Navigate to Applications > Application Integration > Create New Application, and select Wrike from the applications displayed.
Note: You can also find Wrike from the search bar located at the top.
- Under the General Settings tab, enter the Application Name and Description.
- Under the Choose Capabilities tab, choose SSO and click Continue.
 General Settings of SSO configuration for Wrike.
General Settings of SSO configuration for Wrike.
- Under Integration Settings, navigate to the Single Sign On tab and click Metadata Details. Copy the Metadata value, which will be used later during the configuration of Wrike.
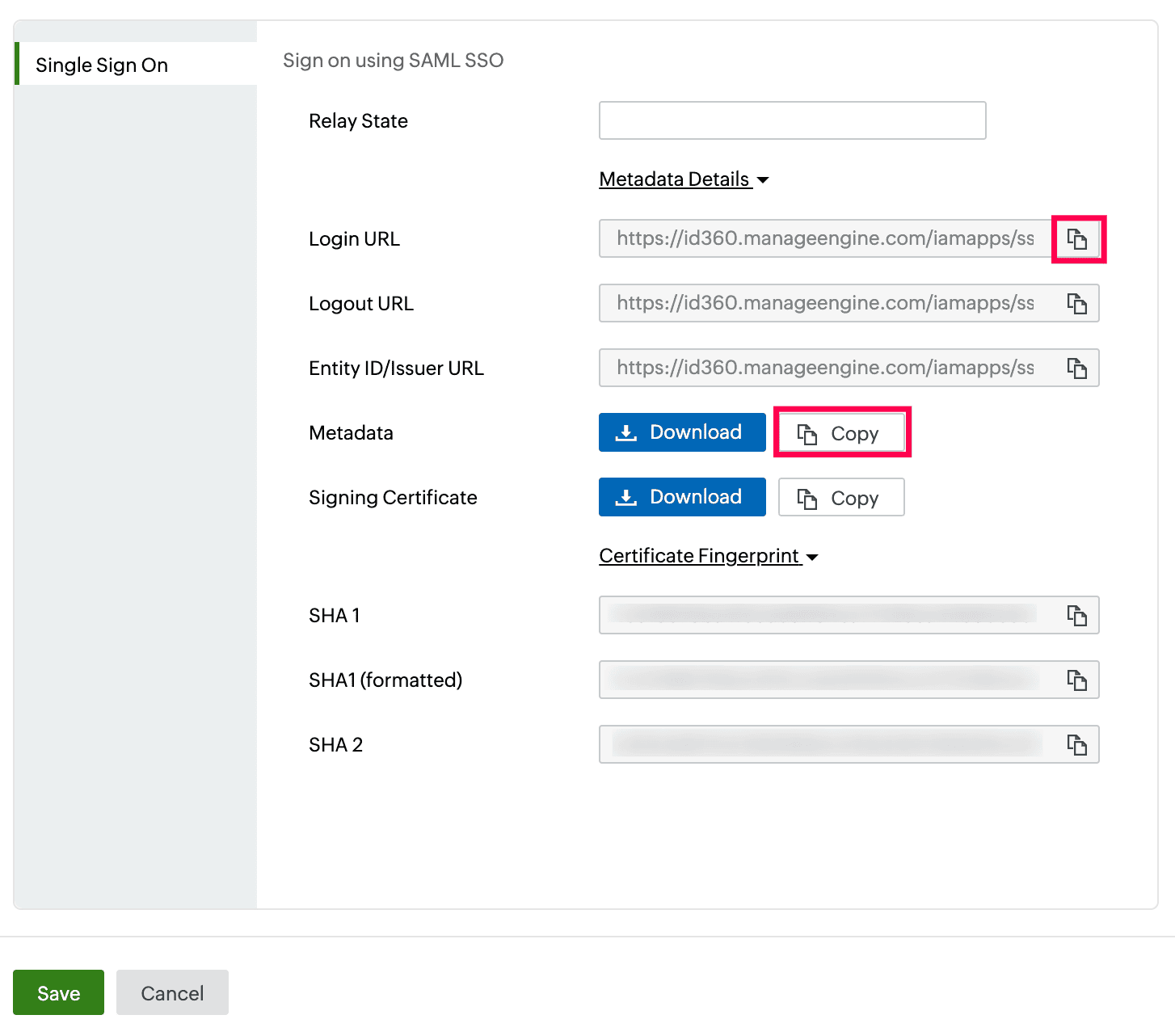 Integration Settings of SSO configuration for Wrike.
Integration Settings of SSO configuration for Wrike.
Wrike (service provider) configuration steps
- Log in to Wrike with admin privileges.
- Click your profile icon and click Settings.
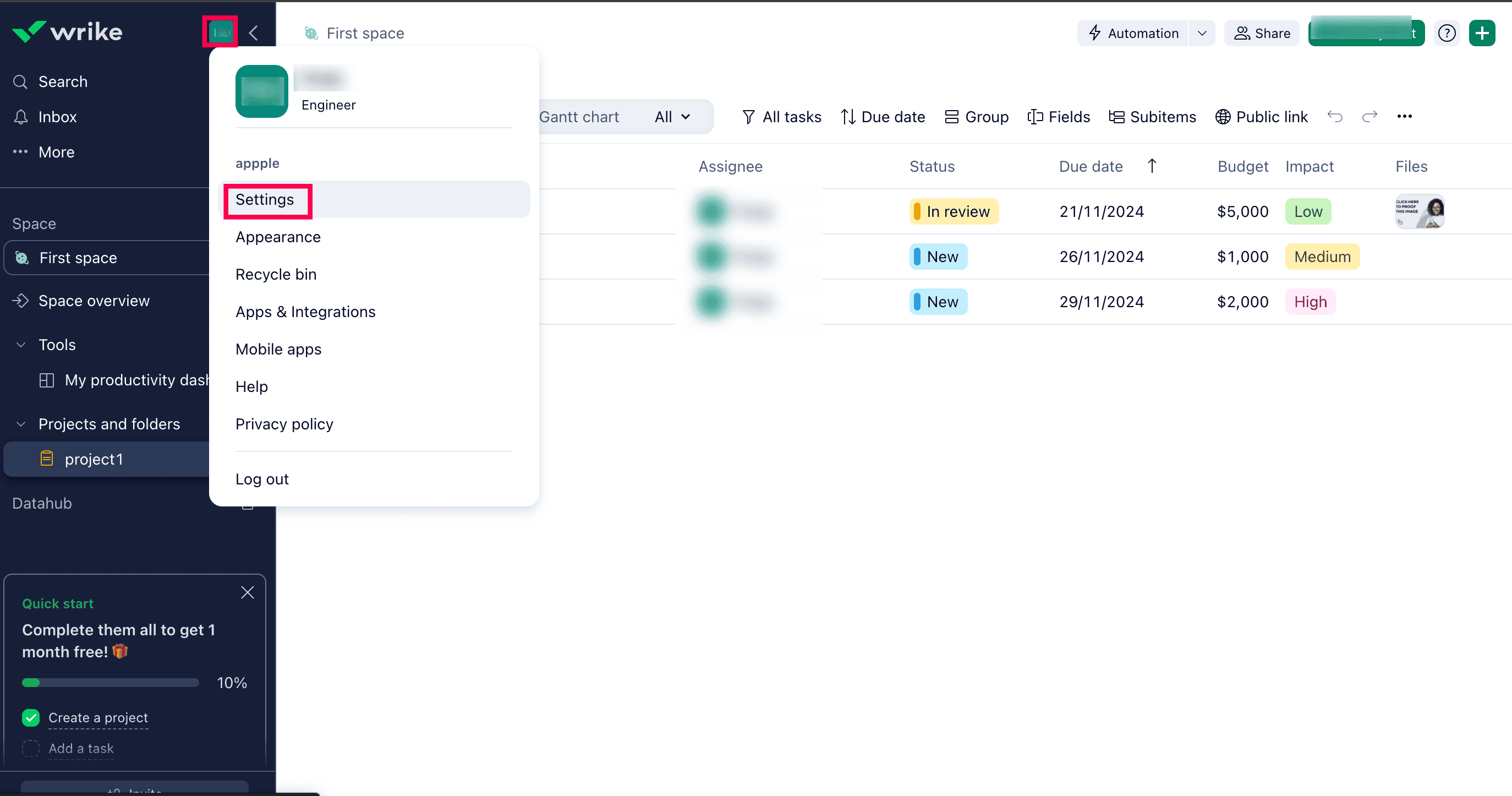 Portal view of Wrike.
Portal view of Wrike.
- Navigate to Security and click Setup SAML SSO.
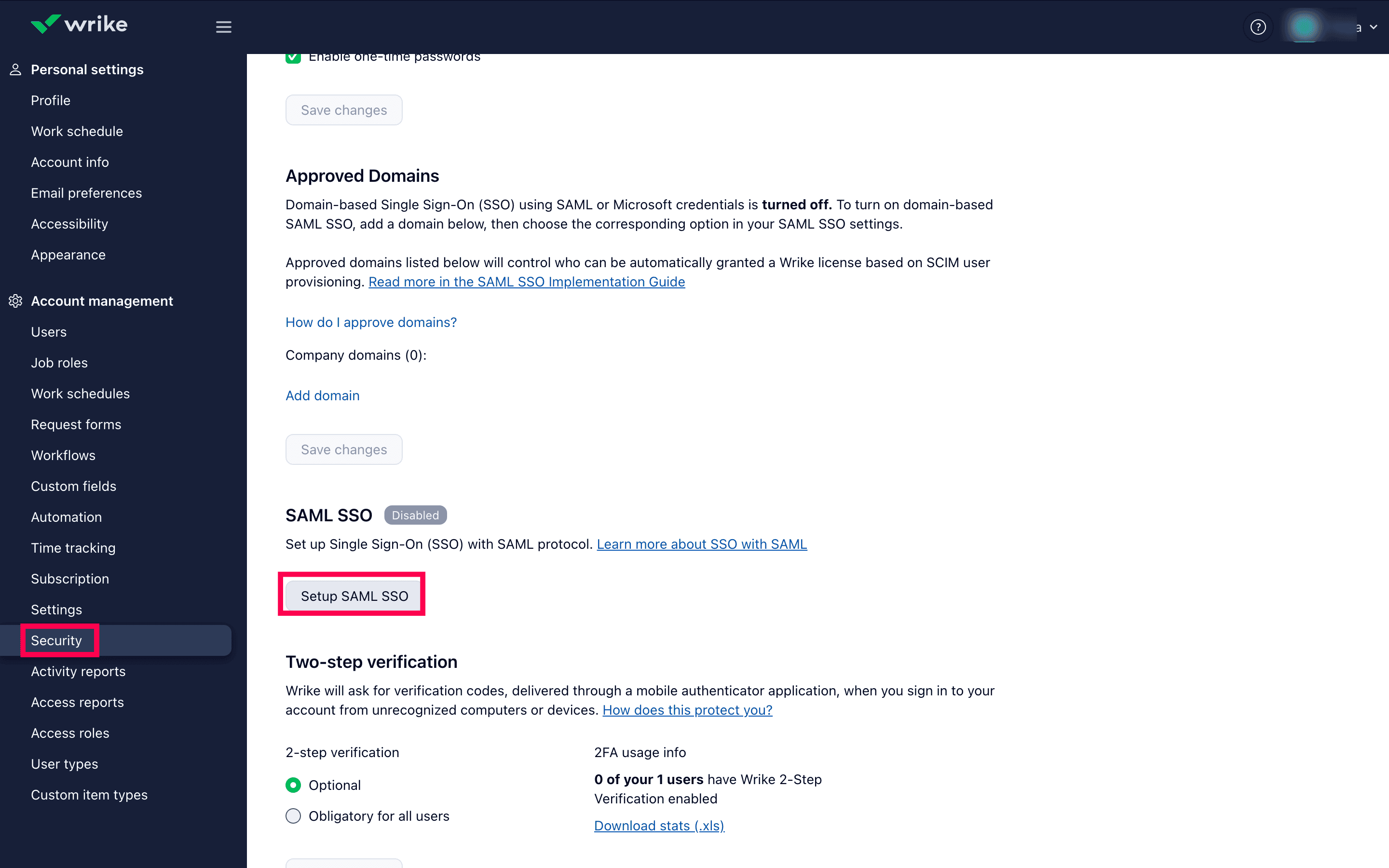 Security settings of Wrike.
Security settings of Wrike.
- From the Set up your Identity Provider section, choose the Other drop-down. Click Next.
 Identity provider selection for SSO setup for Wrike.
Identity provider selection for SSO setup for Wrike.
- From Wrike's metadata file section, click Next.
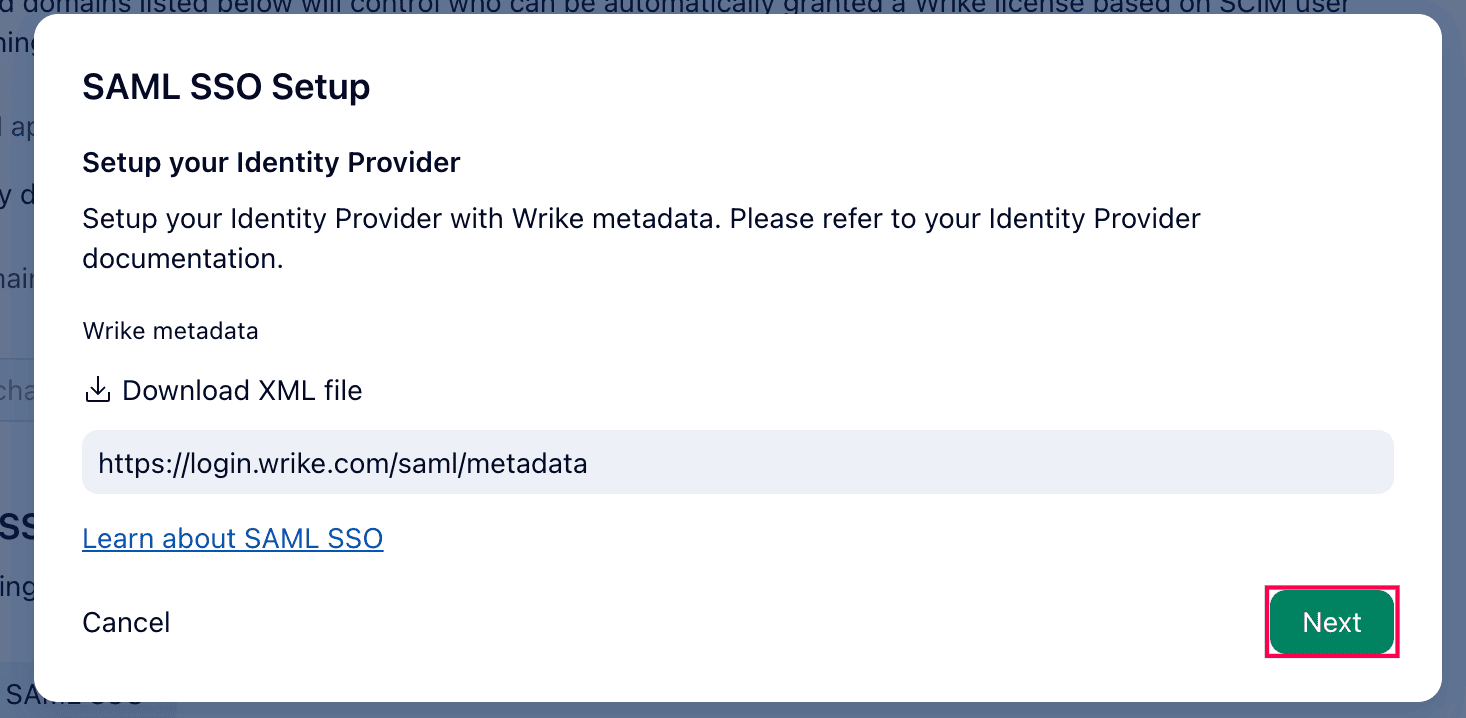 Wrike metadata.
Wrike metadata.
- Under the IDP metadata section, select the Enter XML radio button and paste the metadata value copied in step 6 of the prerequisites. Click Next.
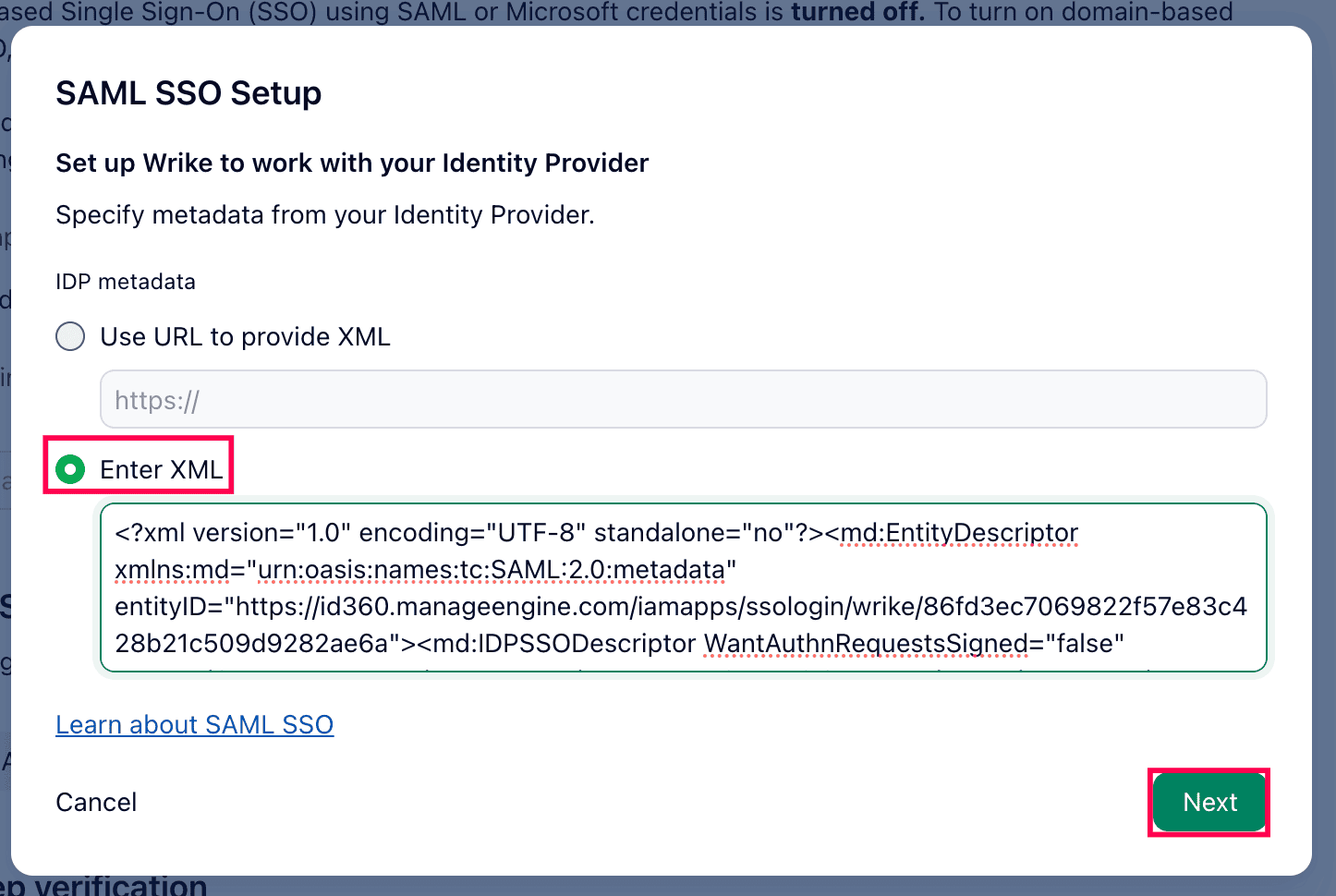 Identity provider metadata configuration in Wrike.
Identity provider metadata configuration in Wrike.
- Next, click Enable SAML settings.
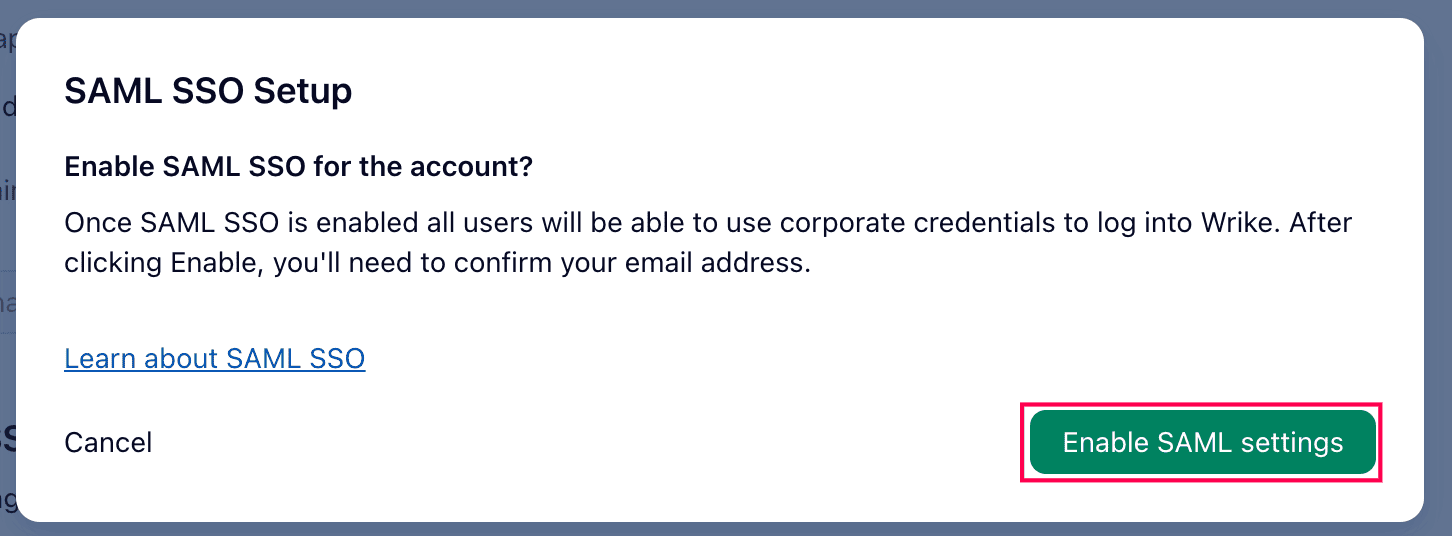 Enabling SAML settings in Wrike.
Enabling SAML settings in Wrike.
- An email will be sent to you with a code to confirm the implementation of SSO. Enter the code and click Confirm.
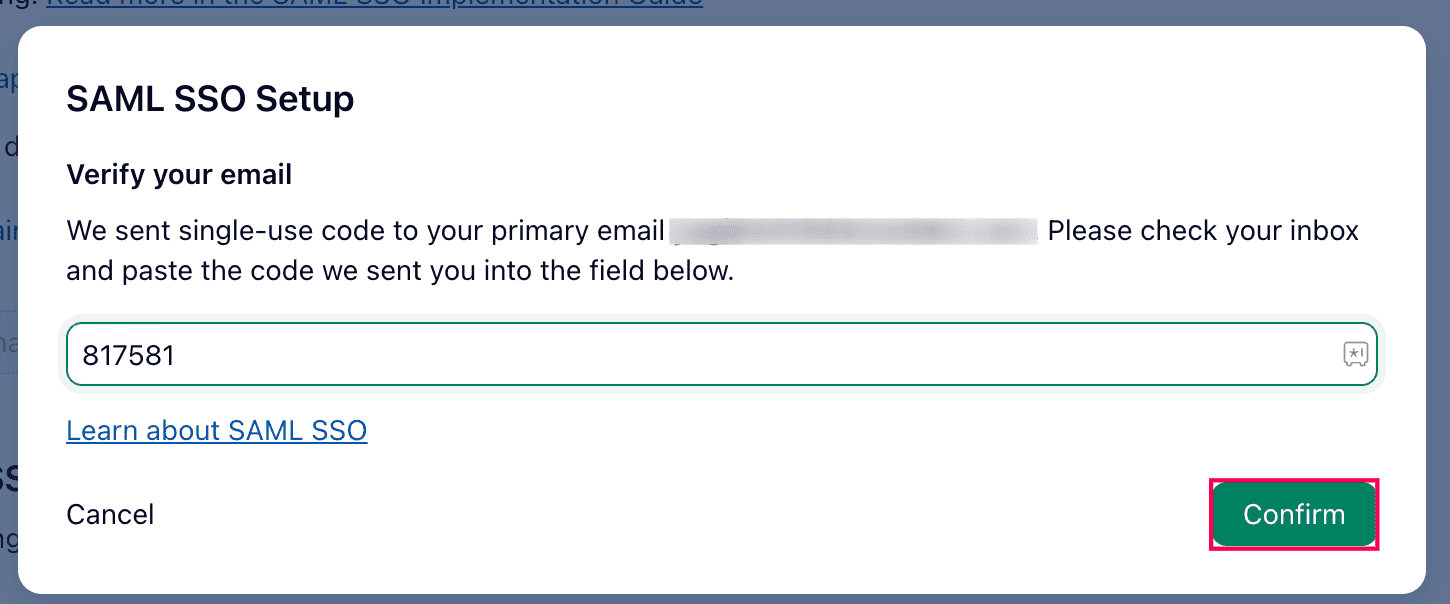 Email verification from Wrike.
Email verification from Wrike.
- Click Save SAML settings.
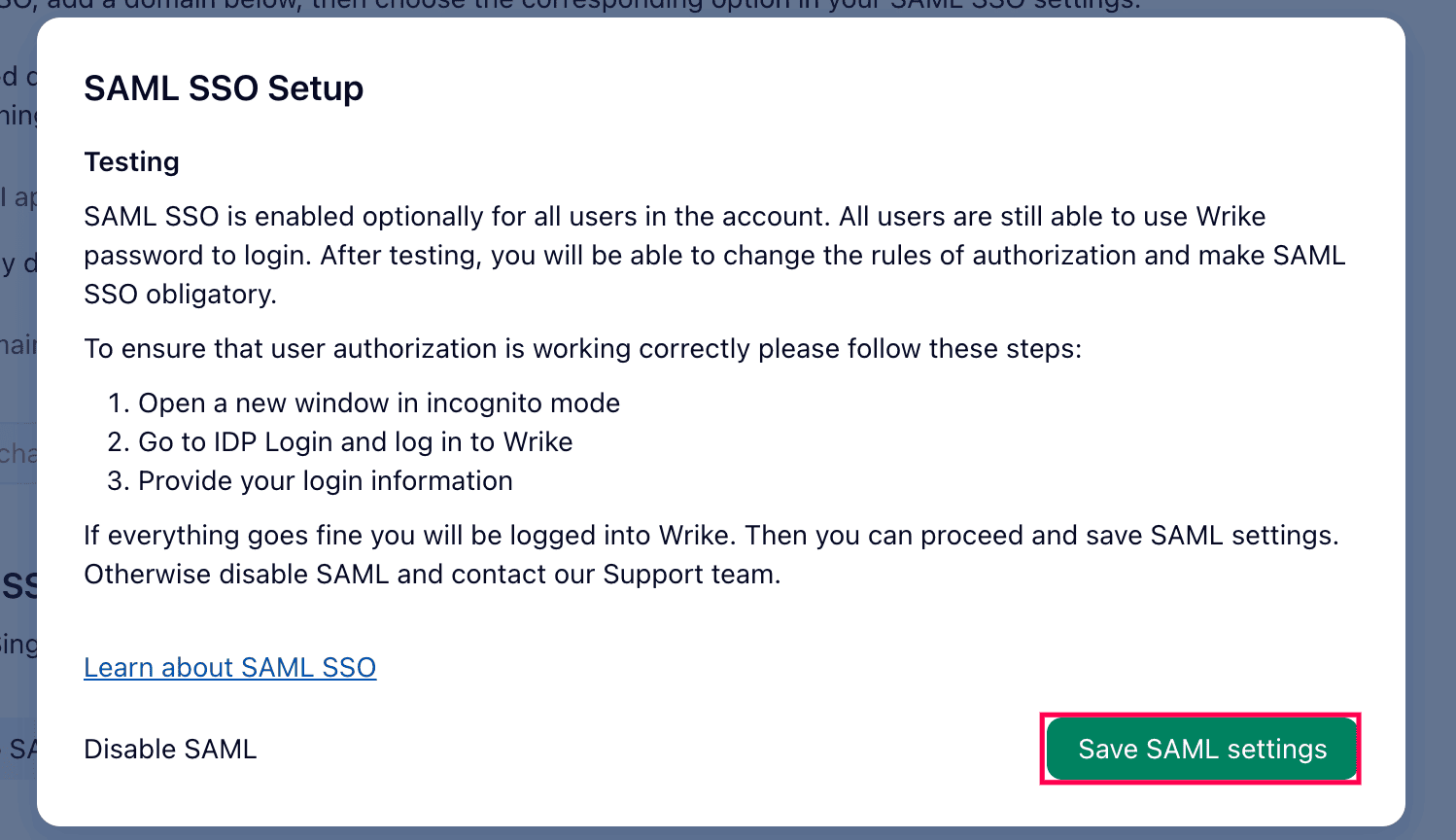 SAML settings saved in Wrike.
SAML settings saved in Wrike.
Identity360 (identity provider) configuration steps
- Switch to Identity360's application configuration page.
- Enter the Relay State parameter, if necessary.
Note: Relay State is an optional parameter used with a SAML message to remember where you were or to direct you to a specific page after logging in.
- Click Save.
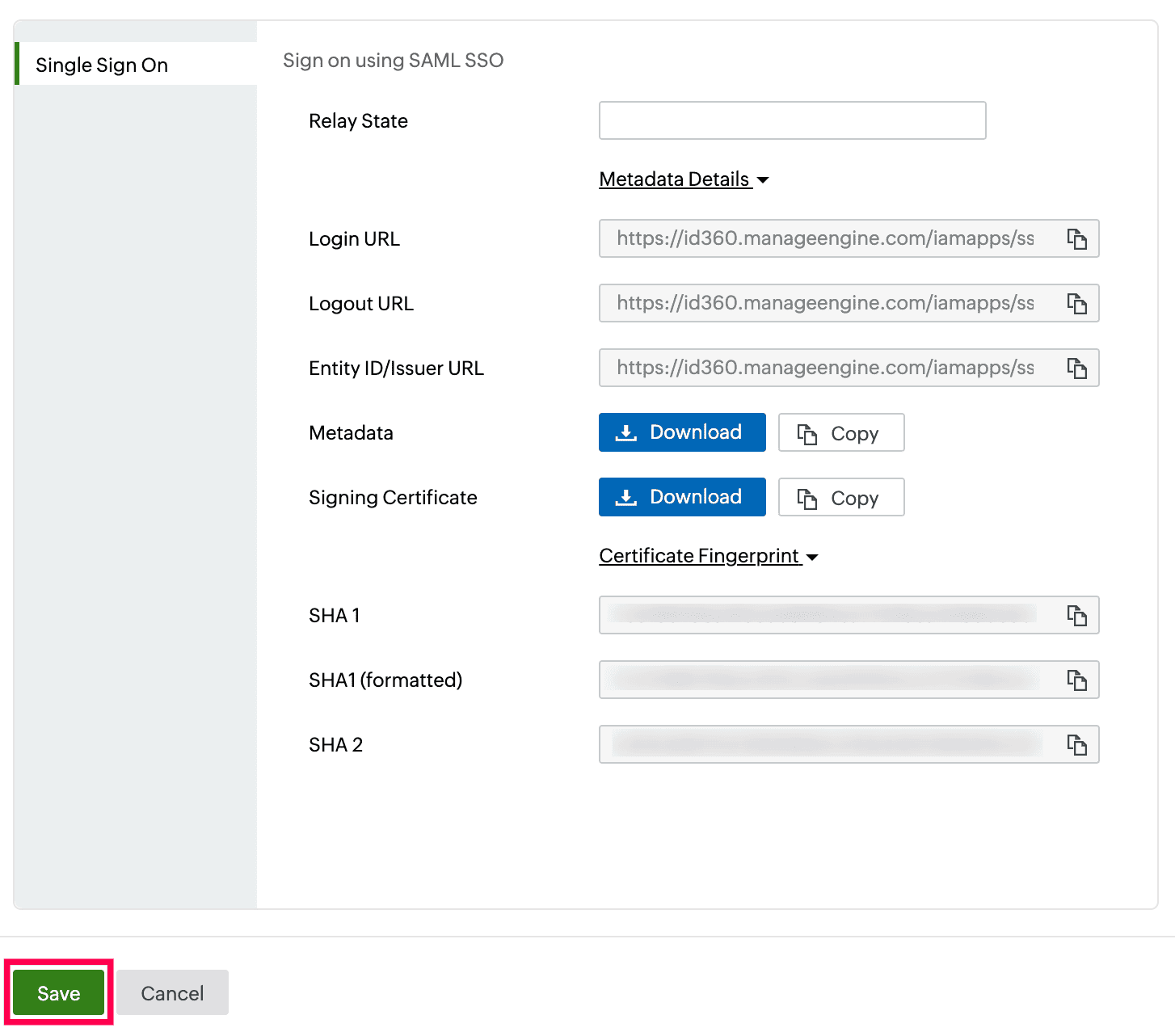 Integration Settings of SSO configuration for Wrike.
Integration Settings of SSO configuration for Wrike.
- To learn how to assign users or groups to one or more applications, refer to this page.
Your users will now be able to sign in to Wrike through the Identity360 portal.
Note: For Wrike, both SP-initiated and IdP-initiated flows are supported.
Steps to enable MFA for Wrike
Setting up MFA for Wrike using Identity360 involves the following steps:
- Set up one or more authenticators for identity verification when users attempt to log in to Wrike. Identity360 supports various authenticators, including Google Authenticator, Zoho OneAuth, and email-based verification codes. Click here for steps to set up the different authenticators.
- Integrate Wrike with Identity360 by configuring SSO using the steps listed here.
- Now, activate MFA for Wrike by following the steps mentioned here.
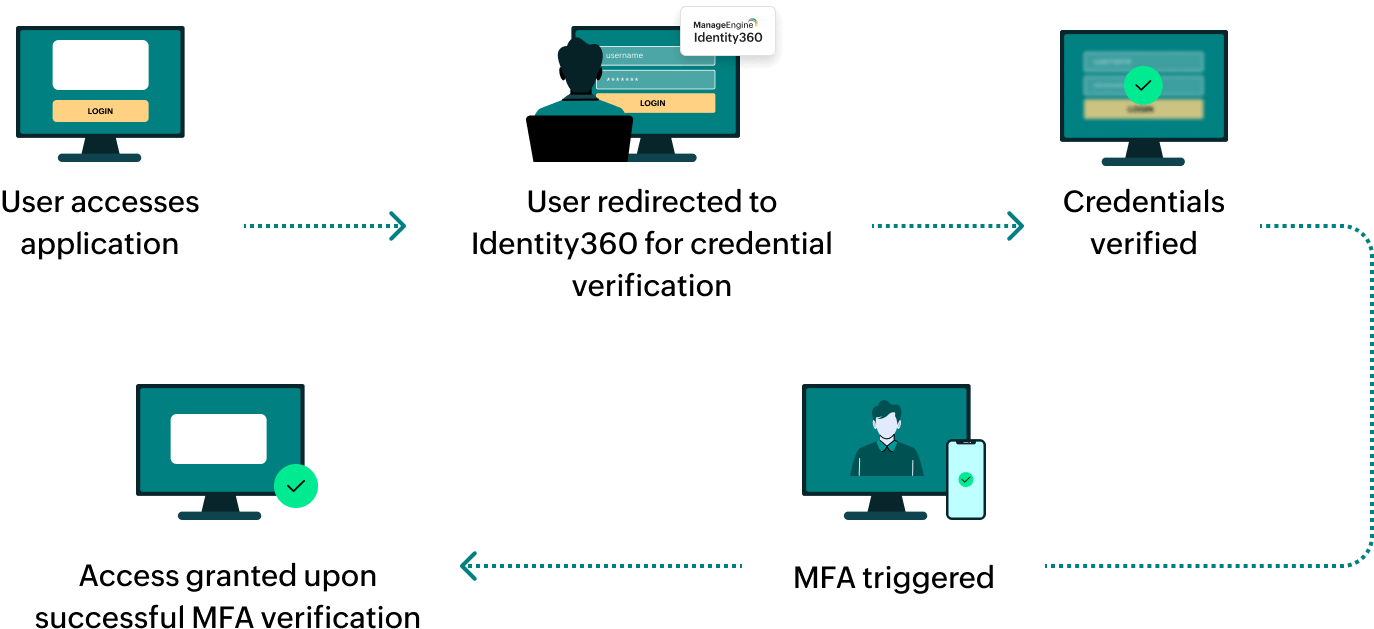
How does MFA for applications work in Identity360?
 General Settings of SSO configuration for Wrike.
General Settings of SSO configuration for Wrike. Integration Settings of SSO configuration for Wrike.
Integration Settings of SSO configuration for Wrike. Portal view of Wrike.
Portal view of Wrike. Security settings of Wrike.
Security settings of Wrike. Identity provider selection for SSO setup for Wrike.
Identity provider selection for SSO setup for Wrike. Wrike metadata.
Wrike metadata. Identity provider metadata configuration in Wrike.
Identity provider metadata configuration in Wrike. Enabling SAML settings in Wrike.
Enabling SAML settings in Wrike. Email verification from Wrike.
Email verification from Wrike. SAML settings saved in Wrike.
SAML settings saved in Wrike. Integration Settings of SSO configuration for Wrike.
Integration Settings of SSO configuration for Wrike.