Table of contents
FIDO2 authentication with Identity360
ManageEngine Identity360 enhances security by implementing FIDO2 authentication, which is designed to provide phishing-resistant and passwordless access to enterprise applications, Identity360 portal, VPNs, and more. Identity360 provides secure and customizable FIDO2 authentication with the WebAuthn API. This supports both platform and roaming FIDO2 authenticators.
What is FIDO2 authentication?
FIDO2 (Fast Identity Online) is an open authentication standard developed by the FIDO Alliance, a coalition of industry leaders dedicated to eliminating the world's reliance on passwords. FIDO2 authentication marks a significant advancement in secure, passwordless access. It enables users to authenticate without relying on traditional passwords, which are often weak and prone to breaches. Instead, FIDO2 uses advanced cryptographic methods to secure user identities, providing a strong layer of protection across various platforms.
What is the FIDO Alliance?
The FIDO Alliance is a non-profit organization founded in 2013 with the mission of reducing the world's over-reliance on passwords. The alliance brings together leading technology companies, service providers, and financial institutions to develop and promote authentication standards that enhance security while improving the user experience.
How does FIDO2 authentication work in Identity360?
FIDO2 authentication utilizes a robust framework of public key cryptography, where each FIDO credential—commonly referred to as a FIDO passkey—consists of a unique pair of keys: a public key and a private key. The private key is securely stored on the user's device, which can be a computer, mobile phone, or a dedicated security key, using advanced hardware encryption methods. Meanwhile, the public key is safely kept by Identity360, linked specifically to the user and their registered device.
When a user attempts to authenticate, the process begins with the user verifying their identity on their enrolled device. This verification can be accomplished through various methods, such as entering a PIN, providing a one-time password (OTP), or using biometric data like fingerprints or facial recognition.
Once the identity is confirmed, the device generates assertion data, which includes a digital signature created using the user's private key. This assertion data is then sent to Identity360 for verification. The system checks the validity of the assertion by utilizing the corresponding public key stored in its database for that specific user. If the verification is successful, access is granted; if not, access is denied.
The user verifies their identity on their enrolled device using a PIN, OTP, or biometric data.
The device generates assertion data, including a digital signature created with the user's private key.
The assertion data is sent to Identity360 for verification.
Identity360 verifies the assertion data using the corresponding public key stored in its database.
Access is granted if verification is successful; if not, access is denied.
Types of FIDO2 authenticators
Before a device can create a unique set of FIDO2 passkeys, it must first ensure that the individual requesting access is authorized and not a malicious entity. This verification is carried out using an authenticator, which is a device capable of accepting various forms of user input, such as a PIN, biometric scan, or other gestures.
FIDO authenticators supported by Identity360
Roaming authenticators
Roaming authenticators are portable devices that operate independently from the user's primary device. These include portable security keys like YubiKey and Google Titan. Users can authenticate themselves by either inserting a FIDO key and pressing a button or by providing a biometric input, such as a fingerprint, on their mobile device. Roaming authenticators are versatile, allowing users to authenticate across multiple platforms and devices from virtually anywhere.
Platform authenticators
In contrast, platform authenticators are built directly into the user's devices, such as desktops, laptops, tablets, or smartphones. These authenticators utilize biometric capabilities and specialized hardware chips to safeguard passkeys. To authenticate, users must log in to FIDO-supported services using their device and then verify their identity through the same device, typically using a biometric scan or a PIN. Examples of platform authenticators include Windows Hello, Apple Touch ID, or Android Biometrics.
Use cases of FIDO2
Remote work and VPN security
FIDO2 provides secure, passwordless VPN access for remote workers, enhancing security and reducing credential theft in hybrid work environments.
Digital identity verification
FIDO2 streamlines digital identity verification for online services, such as e-commerce, enhancing trust in transactions while simplifying account creation and purchases.
Banking and financial transactions
In banking, FIDO2 enhances transaction security by allowing customers to approve payments and transfers with biometric authentication, reducing fraud and enhancing transaction security.
Government services access
FIDO2 secures access to government services like tax filing and social security, enhancing data protection and providing a user-friendly online experience.
What are the benefits of FIDO2 authentication with Identity360?
Passwordless experience
FIDO2 delivers a hassle-free, passwordless login experience with biometrics or FIDO2 security keys, eliminating the need for password management.
Multiple passkeys support
Using Identity360, users can enroll up to five FIDO2 passkeys corresponding to different devices and platforms.
Customizable authenticators
With Identity360, organizations can use both platform and roaming authenticators, customizable to suit their specific needs and user preferences.
Cost savings
FIDO2 authentication helps organizations cut IT support costs by minimizing password related issues like resets and account lockouts.
Phishing resistance
FIDO2 inherently protects against phishing attacks, as authentication is bound to the user’s device and is not susceptible to replay attacks or man-in-the-middle attacks.
Compliance and future-proofing
FIDO2 adoption keeps organizations compliant with data security standards like GDPR and provides a future-ready solution for evolving authentication needs.
Implementing FIDO2 authentication using ManageEngine Identity360
Customizable configuration
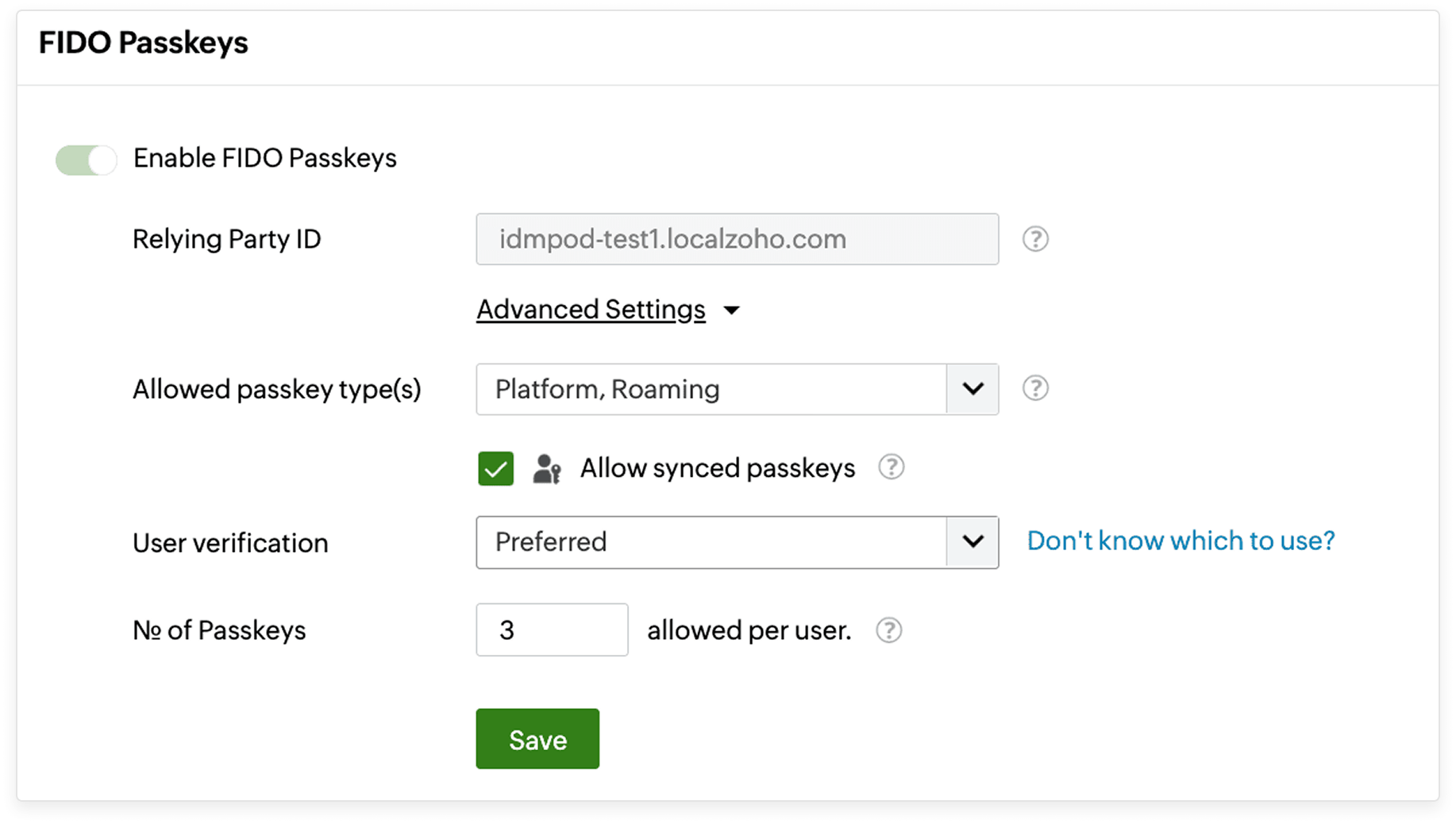
Choose the type of passkeys, preference of user verification, and set the number of credentials users can enroll.
Simple enrollment
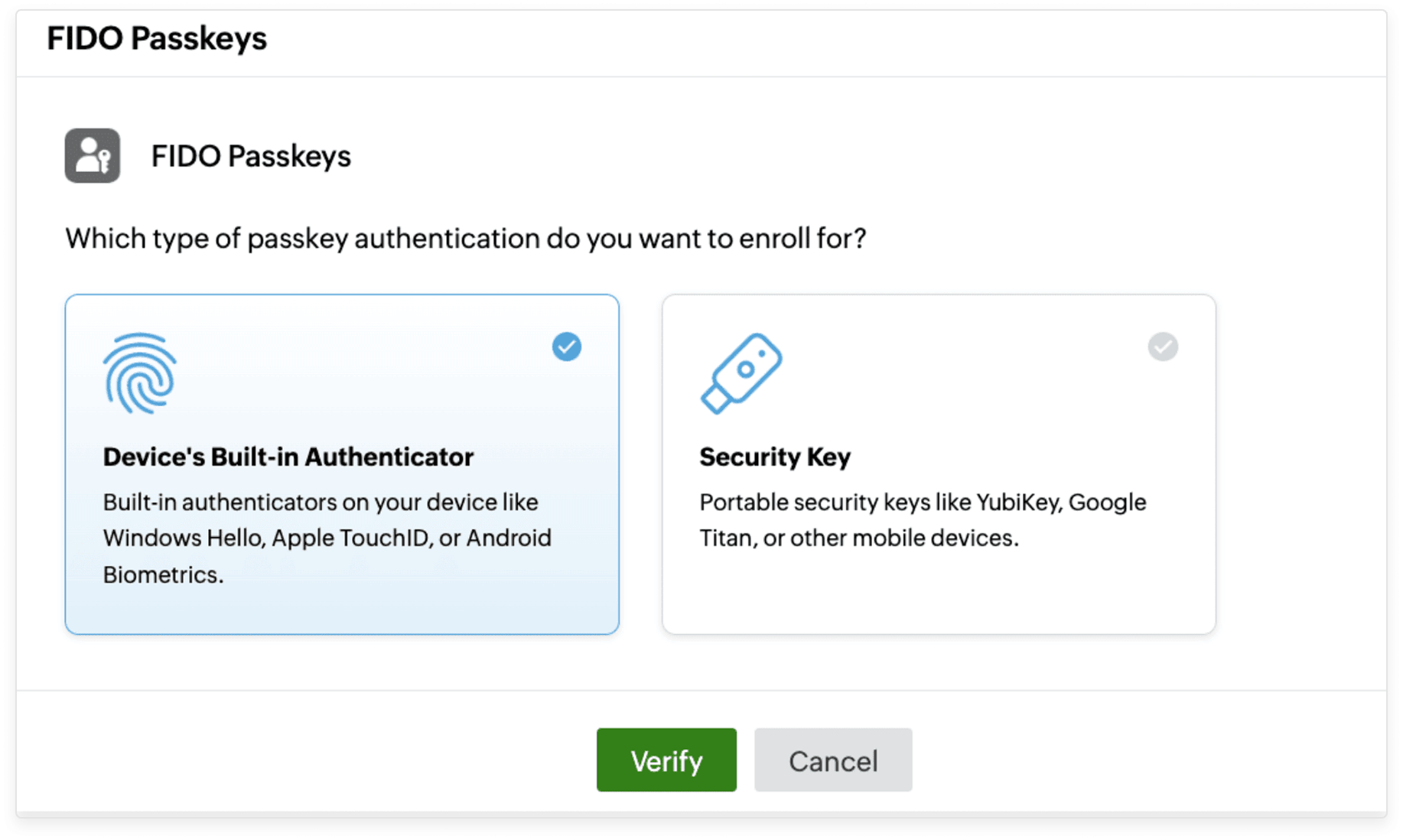
Provide an intuitive console for easy FIDO2 enrollment and authentication for your users.
