Cloud security posture management (CSPM) is the process of continuous risk assessment in multi-cloud environments. It is an automated method of identifying cloud misconfigurations and compliance risks across cloud infrastructures like Infrastructure as a Service (IaaS), Platform as a Service (PaaS) and Software as a Service (SaaS). According to Gartner, "the core of CSPM applies common frameworks, regulatory requirements and enterprise policies to proactively and reactively discover and assess risk and trust of cloud services configuration and security settings".
Why is CSPM important?
In a multi-cloud environment, data breaches might occur due to a multitude of misconfigurations or out-dated configurations. Some factors that attribute to these misconfigurations are the complexity of multi-cloud infrastructures, cloud vulnerabilities, and security blind spots in the cloud. Further, identifying the threats and remediating them are affected by alert fatigue, manual threat detection practices, and burnout in the SOC teams. This makes the cloud vulnerable to cloud-based cyberattacks that affect the security of cloud data.
CSPM best practices help you secure your cloud with automated threat detection and incident response abilities. It helps you achieve complete visibility into your cloud environment and reinforces the security posture of the cloud. By employing CSPM, you can ensure 360-degree security in the cloud.
How to implement CSPM
CSPM is a process that needs to be implemented in day-to-day cloud operations. It requires security teams to automate the process of cloud resource discovery and configuration, threat detection, alert generation, and incident response. This complex process can be simplified by employing a robust CSPM solution that helps you identify misconfigurations and security breaches in the cloud by automated incident monitoring and response. Further, a CSPM solution also generates reports on cloud security incidents and can help you prove adherence to compliance mandates.
Use cases of CSPM tools
Visibility into cloud assets
Organizations often lack visibility into the different cloud resources in their network and their respective configurations. This lack of visibility can give rise to misconfigurations that can go undetected for long periods of time. A CSPM tool helps you attain clear visibility into multiple cloud environments. ManageEngine Log360, a SIEM tool with CSPM capabilities, offers complete visibility into various cloud platforms like Amazon, Azure, Salesforce and Google. Figure 1 depicts an intuitive dashboard with graphs in Log360 that help you oversee the security posture of AWS.
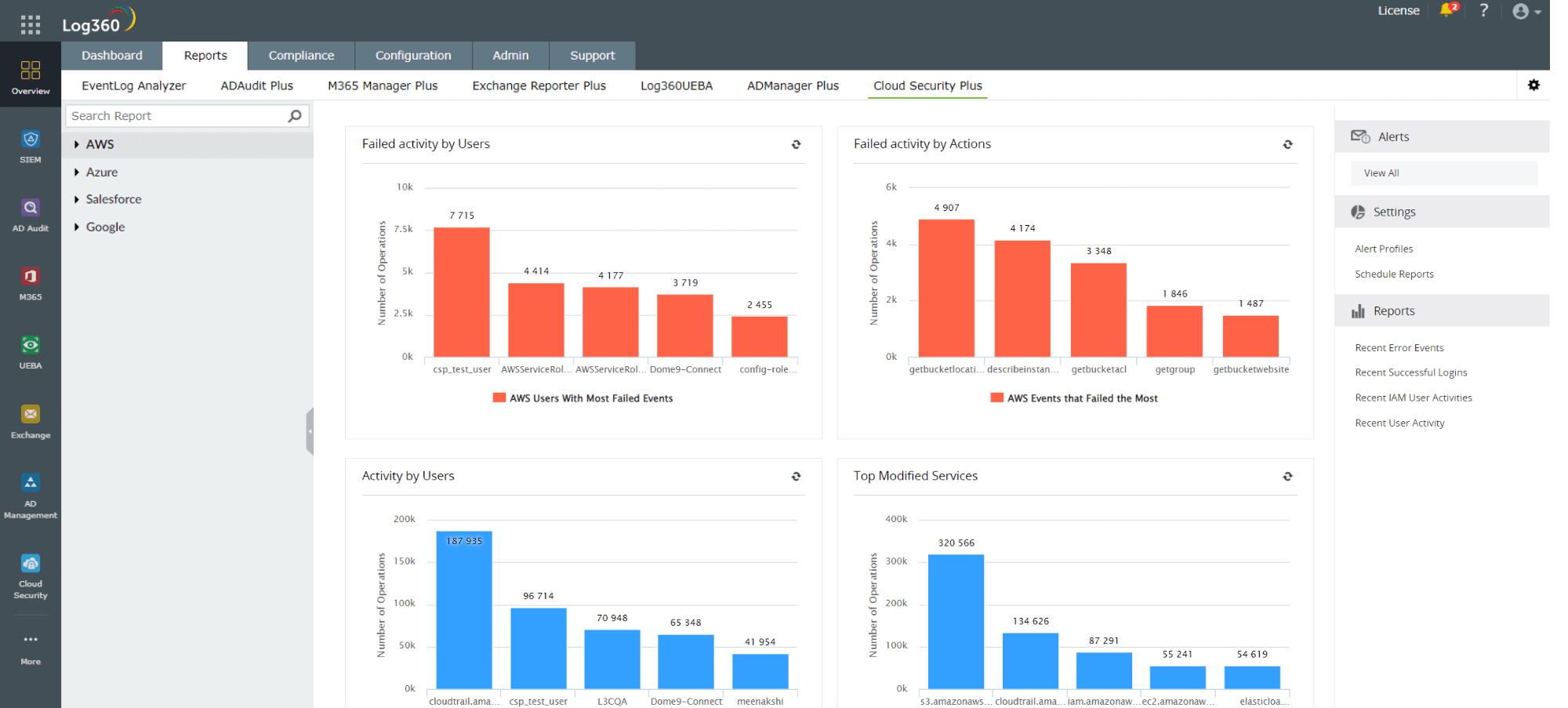
Figure 1: Cloud security dashboard in Log360
Automated monitoring
A CSPM tool automatically monitors and identifies any misconfigurations in the cloud environment that attackers can take advantage of, and remediates them. Log360 helps you attain this advantage of a CSPM tool with comprehensive and detailed reports on cloud activities. Figure 2 depicts an AWS report in Log360 that helps you monitor recent successful user login activities in AWS.
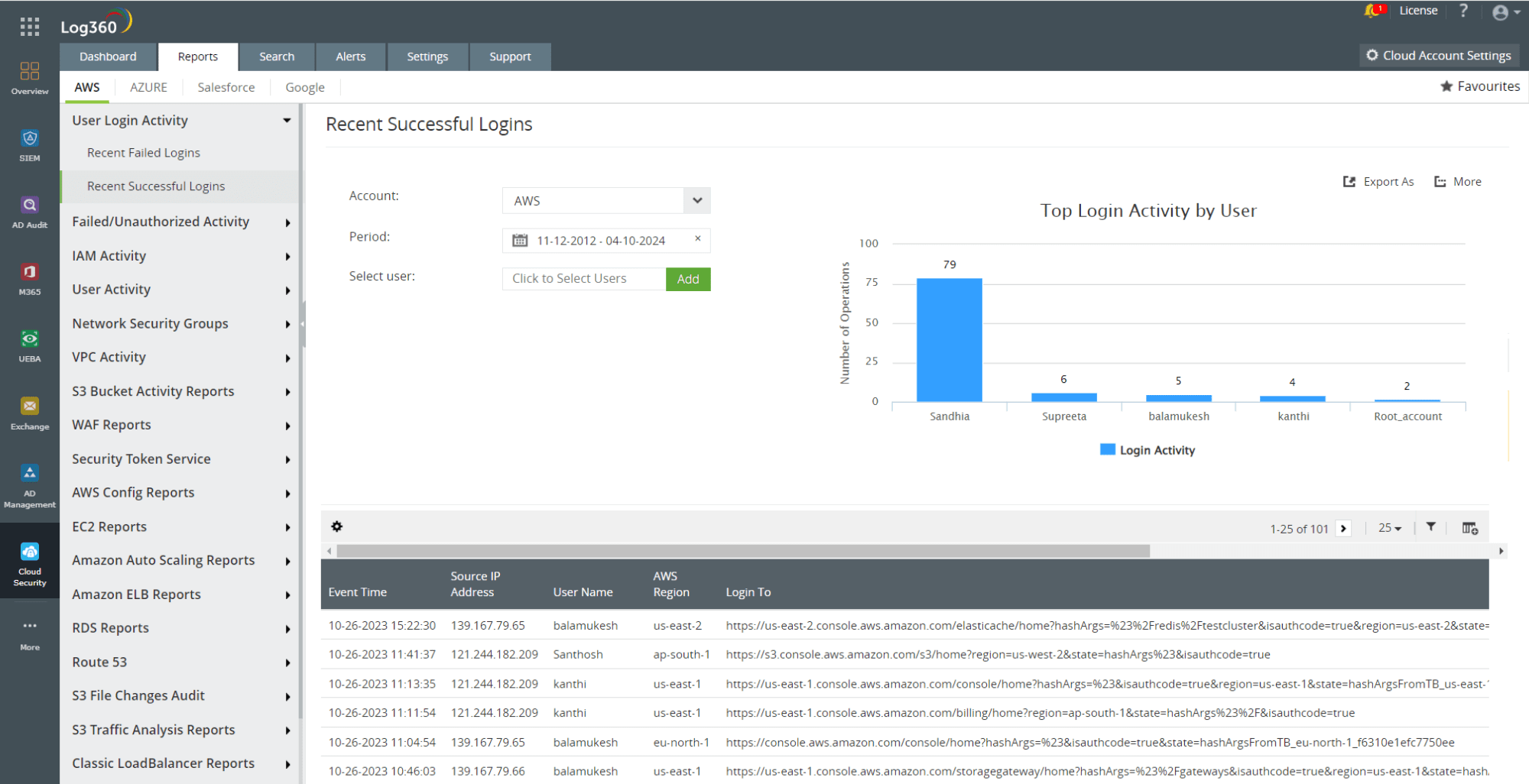
Figure 2: AWS recent successful login report in Log360
Compliance management
Organizations that use cloud platforms are expected to be compliant with the laws and regulations that apply for those using the cloud. Similar to a CSPM security tool that aids in ensuring compliance, Log360 also ensures your organization's compliance with mandates such as GDPR, HIPAA, PCI DSS, and FISMA. Figure 3 shows the various reports that help adhere to PCI DSS compliance using Log360.
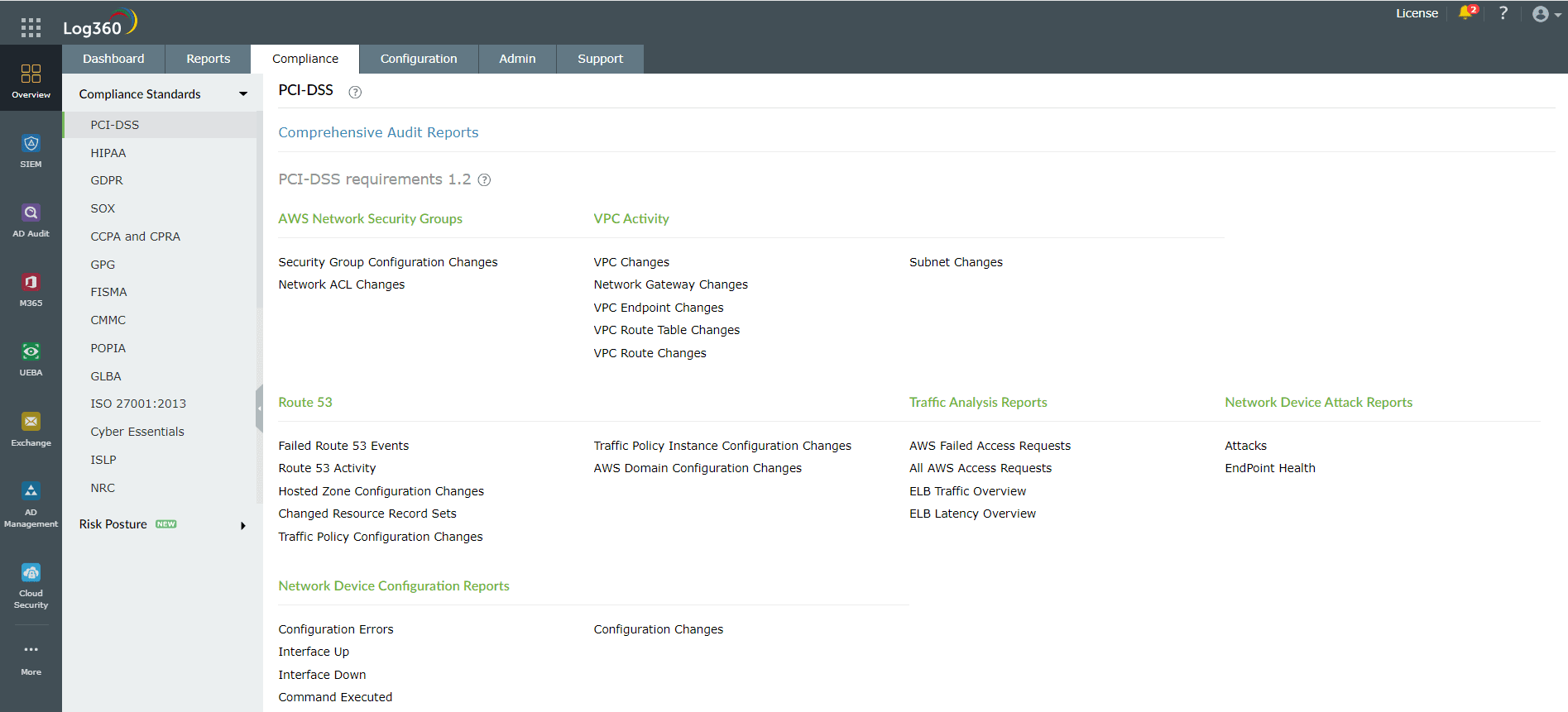
Figure 3: Compliance reports in Log360
Real-time alerting and incident response
CSPM tools identify threats to an organization's security posture, including unauthorized access or activity in the cloud, using real-time threat detection and alerting capabilities. Log360 offers a set of predefined alert profiles for detecting security breaches on cloud platforms and also allows you to create custom alert profiles based on the risk posture of your cloud environment. It further enables the configuration of incident workflows for these alerts, facilitating proactive incident response as soon as the alerts are triggered. Figure 4 shows a custom alert profile for Azure misconfiguration with an incident workflow in Log360.
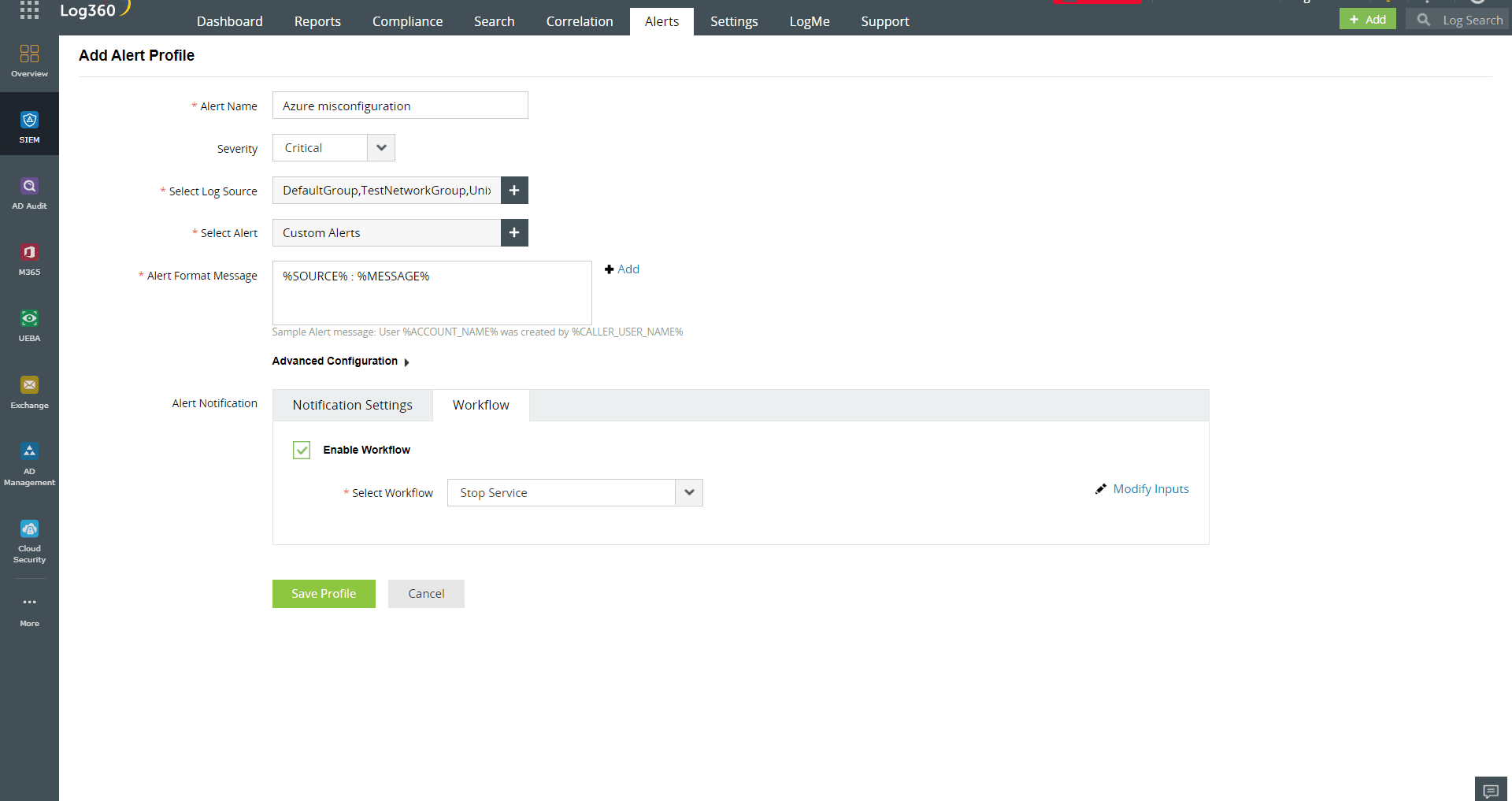
Figure 4: Custom alert profile for Azure misconfiguration in Log360
Log360 can be your alternate to CSPM to secure your cloud infrastructure and reinforce your cloud security posture. Try a free, 30-day trial of Log360 to test these features, or schedule a free demo with one of our product experts to learn more.



