Organizations are shifting their IT infrastructure from on-premises to the cloud to gain advantages in cost, productivity, and uptime. Though cloud offerings are typically secure, the possibility of a cyberattack should not be overlooked. As the number of organizations moving to the cloud increases, this brings its own set of security challenges.
The popularity of Linux servers has grown recently, grabbing the attention of hackers. As detection techniques advance, attackers are adopting new and surreptitious methods to stay undetected and accomplish their nefarious motives. One such method that impacts the security of your Azure environment is the Secure Shell (SSH) brute force attack on Linux machines. Let's find out what happens in an Azure SSH brute force attack and the ways to detect and defend the attack.
The role of SSH in Azure cloud security
SSH in Azure enables encrypted communication for accessing virtual machines (VMs) remotely. SSH key pairs are used for authentication, reducing the risk of password-based attacks in Azure. By controlling access to VMs, SSH in Azure enhances cloud security and prevents unauthorized access to sensitive data in Azure cloud, ensuring data security in the cloud.
SSH brute force attack on Azure
Exposing SSH services is a common misconfiguration that increases the vulnerability of Linux systems. Brute-forcing SSH channels is a popular method for gaining access to the cloud. After an initial successful SSH brute force attack, the attacker delivers a further payload to the host by downloading scripts. Once complete, the attacker continues to move laterally, accessing sensitive data.
How to detect and defend SSH brute force attacks in Azure cloud
- A common indicator of a SSH brute force attack is the sudden change in the amount of traffic. Monitoring network traffic helps identify potential attacks and keep hackers at bay. SIEM solutions like ManageEngine Log360 with cloud monitoring capabilities can help you monitor network activities in real time with out-of-the-box reports and real-time alerts. It also provides insightful information to IT administrators to ensure data security in the cloud. Figure 1 depicts a comprehensive dashboard of network activities in Log360.
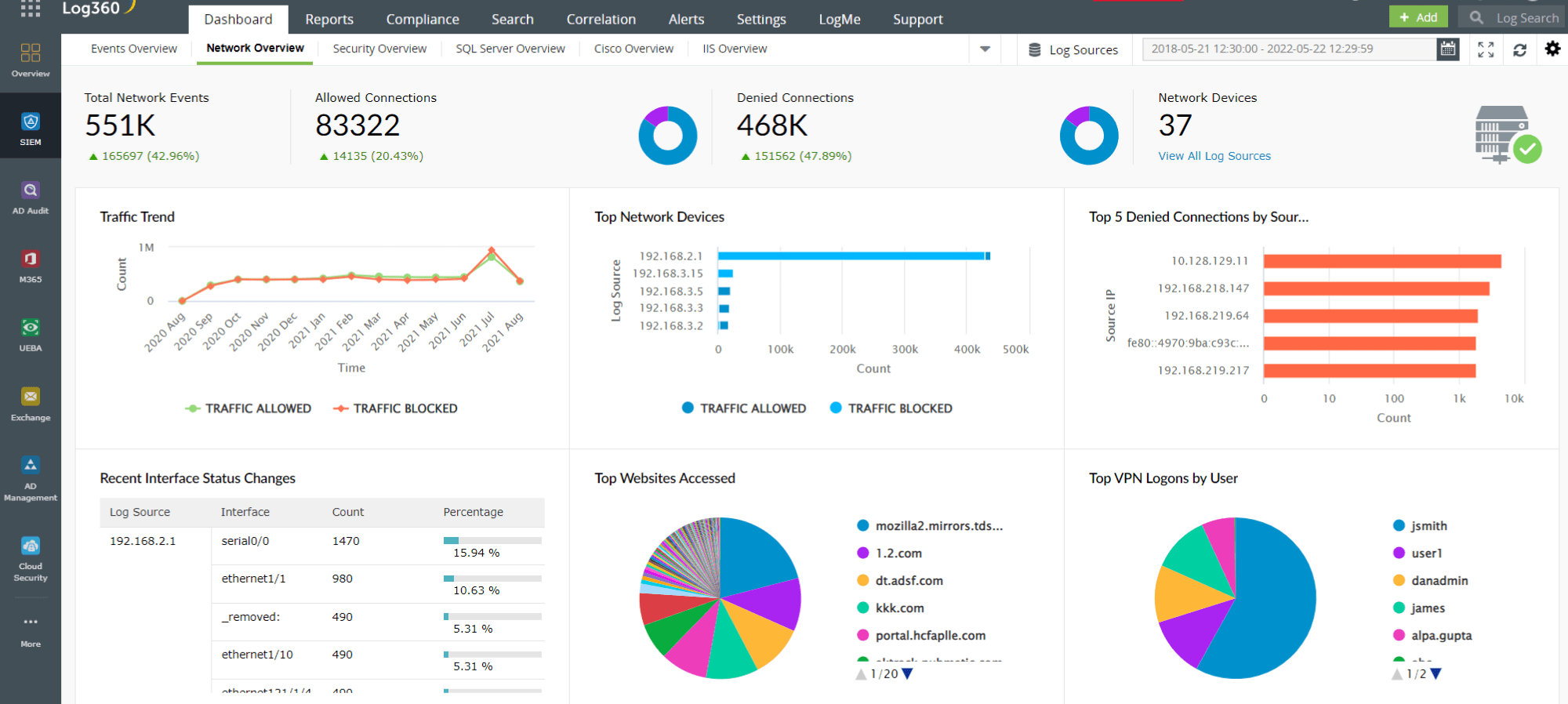
Figure 1: Network overview dashboard in Log360
- Monitoring Azure Linux instances for multiple failed logons in an unusually short period can help you detect a potential brute-force attack. Once a brute force attack is identified, you can block the IP address of the attacker to prevent any such attempts in the future.
- SSH in Azure secures access to VMs in Azure cloud. By brute forcing Azure, attackers gain direct access to Azure virtual machines and exfiltrate sensitive data. Monitoring virtual machine (VMs) created in Azure and keeping track of events such as creation, deletion and modification of VMs is another way of detecting unauthorized VM access via SSH brute force attack and preventing cloud data loss. Log360 provides extensive reports on VM related activities in Azure that help you monitor anomalous and unauthorized access to Azure virtual machines and ensure data security.
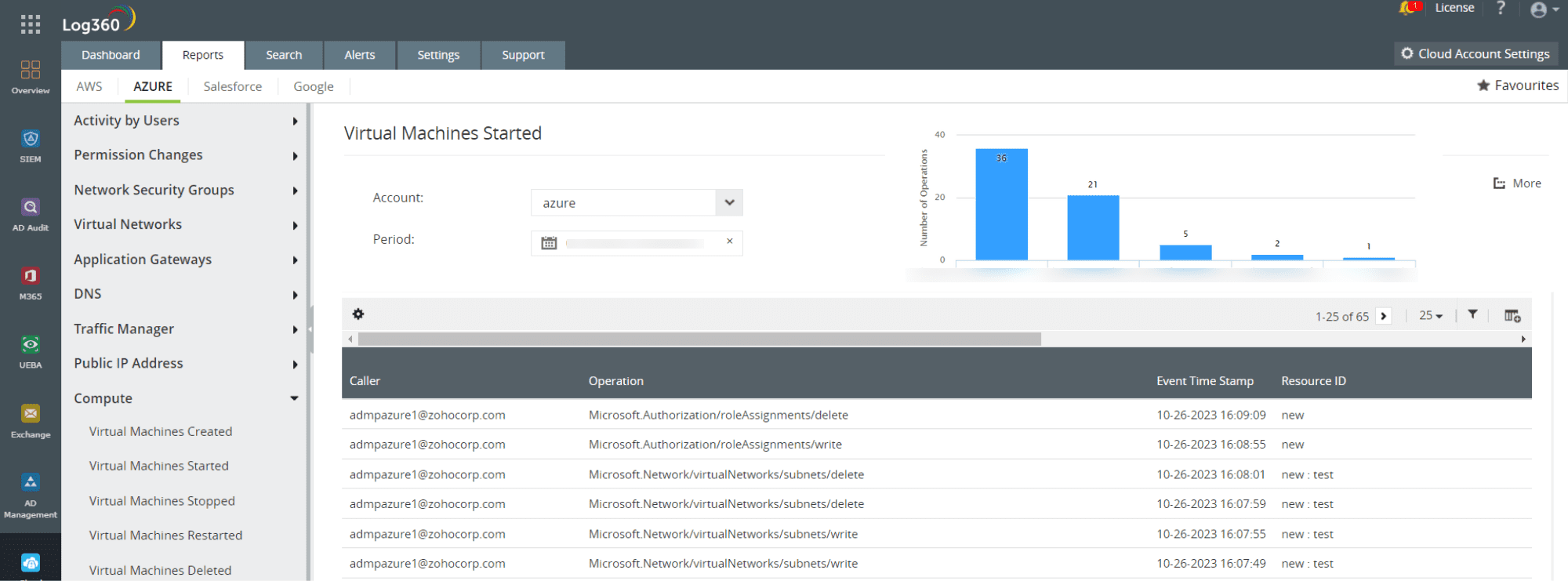
Figure 2: Azure virtual machines started report in Log360
- Log360 also enables you to create custom alert profiles to detect a SSH failed login in a Linux machine that can indicate a potential brute force attack in Azure. It also comprises incident response workflows that can be enabled to defend the propagation of the attack in the network, thereby ensuring Azure cloud security and data security.
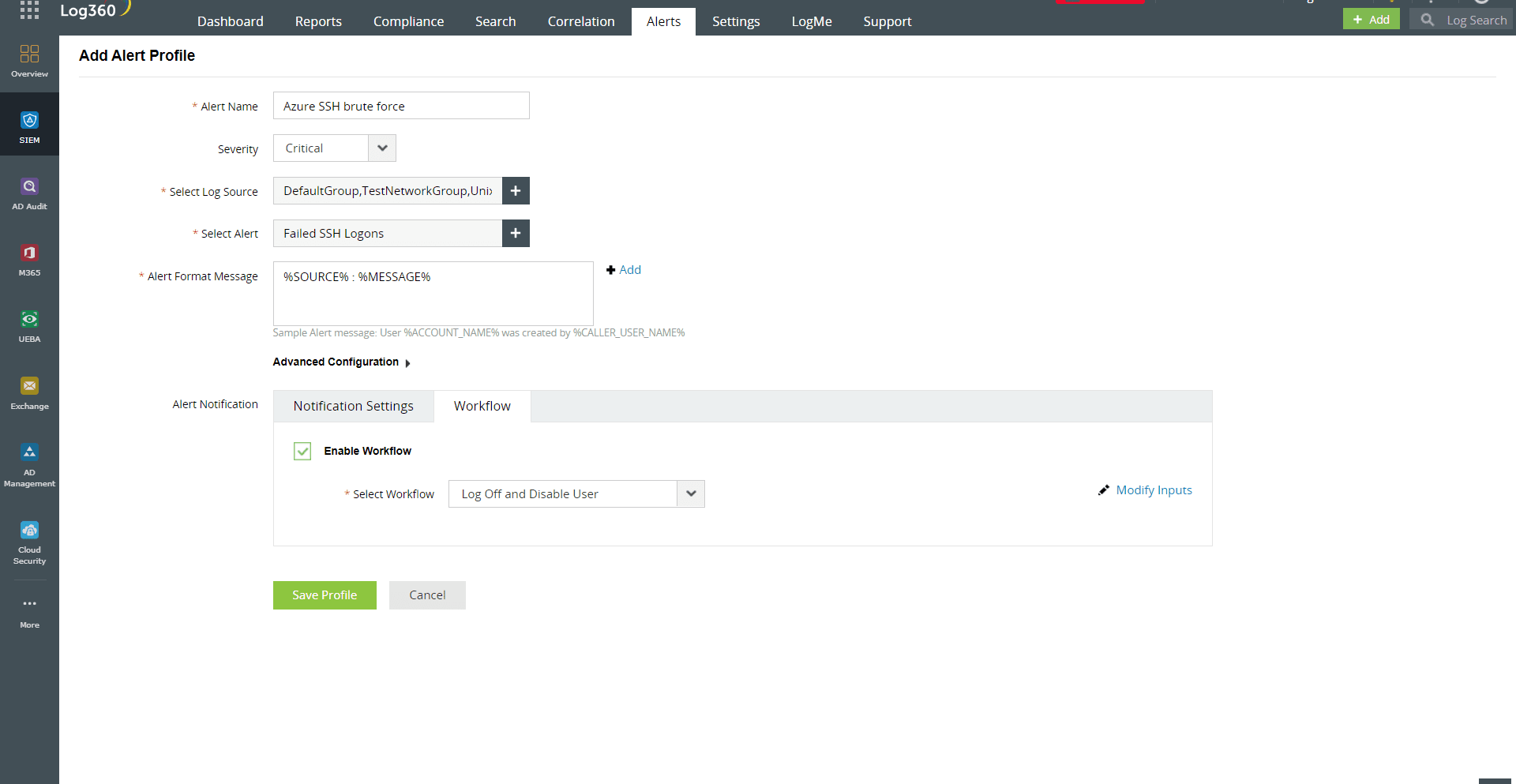
Figure 3: Custom alert profile for Azure SSH brute force attack in Log360
Enhancing cloud security with Log360
ManageEngine Log360 is a comprehensive SIEM solution that supports cloud platforms such as Amazon Web Services, Google Cloud Platform, Salesforce, and Microsoft Azure along with on-premises security monitoring. The solution enables you to secure your cloud infrastructure and helps you reinforce your cloud security posture with advanced threat detection, real-time correlation, alert generation, UEBA powered anomaly detection and proactive incident response mechanism. Try a free, 30-day trial of Log360 to test these features firsthand, or schedule a free demo with one of our product experts.



