File-based systems are frequently used by organizations to organize, store, and manage information. File integrity monitoring (FIM) is a technique used to monitor and validate the integrity of files and systems within a computing environment. Identifying and alerting users to unauthorized or unexpected changes to files, folders, and configurations is the key objective of FIM. It helps safeguard critical data and systems from cyber threats and unauthorized accesses.
A FIM solution protects data against unauthorized changes, ensuring its accuracy. Changes that are monitored include:
- Creation, deletion, access, modification, or renaming of files and folders—along with any failed attempts to perform these actions.
- Contextual data such as who actually made the modification, when it happened, and where it happened.
Why is file integrity monitoring important?
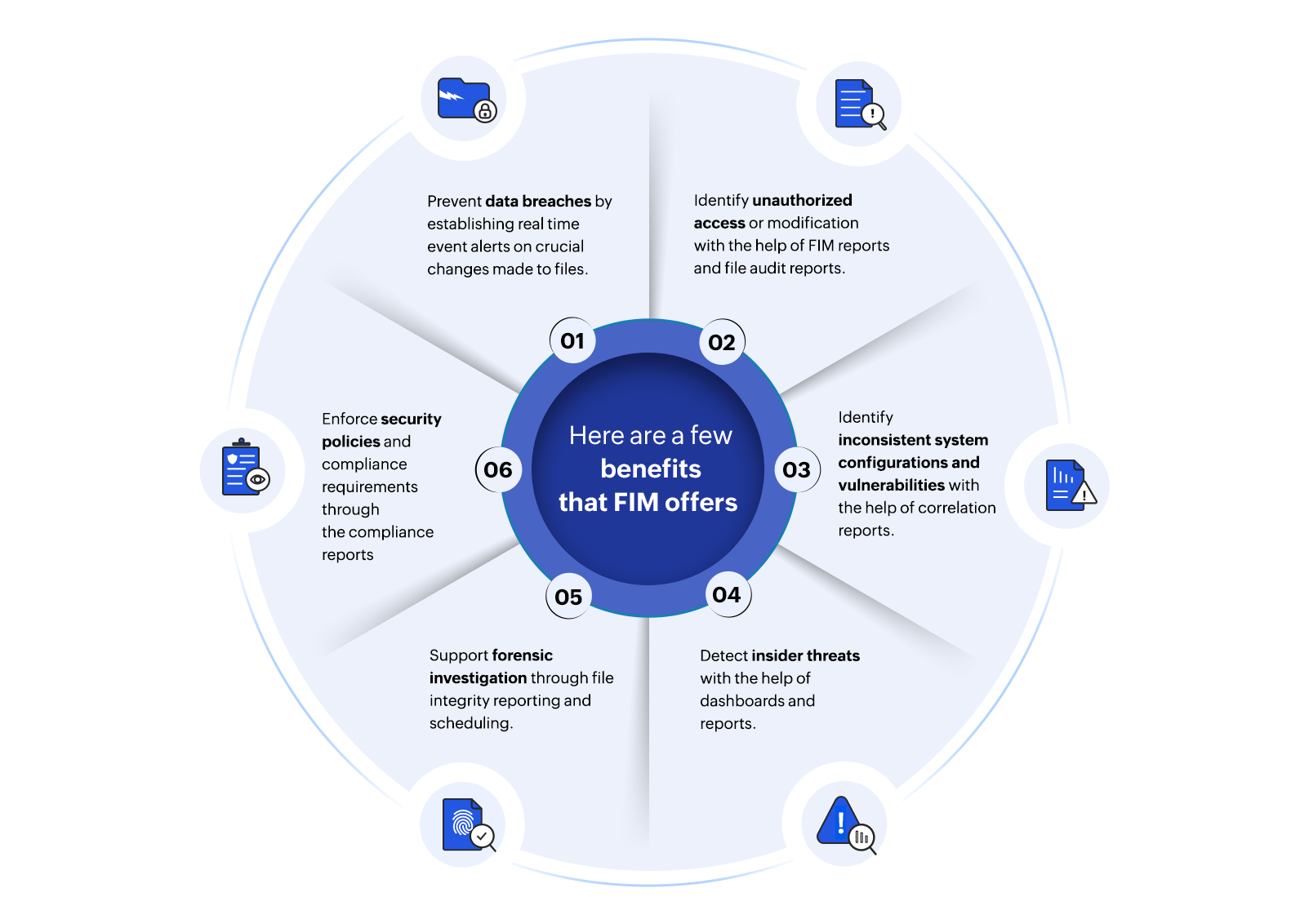
Figure 1: The importance of implementing file integrity monitoring
Security threats affect organizations of all sizes on a regular basis. The primary goal of cybercriminals is to access sensitive data belonging to a business, such as confidential customer information, financial data, or system passwords.
A strong cybersecurity plan must include file integrity monitoring, which enables organizations to quickly identify and address security threats while preserving the confidentiality and integrity of their data and systems. Here are several key reasons why it's important:
- Identifying unauthorized changes: FIM solutions keep an eye out for any unauthorized additions, deletions, or changes to files and directories. This is essential for identifying malicious activities, including insider or hacker tampering.
- Compliance requirements: The implementation of FIM as a security best practice is required by numerous regulatory standards and compliance frameworks, including PCI DSS, HIPAA, and GDPR. In order to stay out of trouble and keep stakeholders' and customers' trust, compliance with these standards is crucial.
- Data breach prevention: Unauthorized modifications to important files may result in system compromise or data leaks. By quickly identifying and notifying security professionals of any suspicious activity, FIM contributes to the prevention of such incidents.
- Maintaining system integrity: System files, configuration files, and other data are protected from corruption and change by FIM. This is necessary to keep the system reliable, performant, and stable.
- Forensic analysis: By logging file and folder changes, FIM offers important forensic information in the event of a security incident. Security teams can use this information to look into the incident's primary cause and implement the necessary remediation measures.
Files that store the sensitive data are essential to an organization's daily operations, collaboration, interaction, compliance, and decision-making processes across all industries. In today's digital environment, maintaining productivity, efficiency, reputation, and competitiveness of an organization requires effective file management and security.
Approaches employed in FIM to monitor the changes made to files and folders:
- Comparing the baseline: Establishing a baseline of known business critical files and configurations that represent the system's authorized condition is known as baseline FIM. Periodically or continuously, the established baseline is compared to the current state of files and configurations. Any deviations from the baseline trigger alerts or notifications, indicating potential unauthorized changes. Using the cryptographic checksum (such as the SHA-2 or MD5 hash algorithms) for monitoring a file and comparing it to the previous hash calculation that serves as a baseline is one of the reliable approaches.
- Notifying the changes in real time: Real-time FIM systems track modifications as they occur and monitor specified files and configurations continuously. It does not use a predefined baseline. Rather, its primary objective is to identify any deviations from the present condition of the systems. In the event of unauthorized file access or modifications, the security administrators are immediately notified about the change through alerts. Alerts trigger immediate response actions, such as isolating affected systems, rolling back changes, or launching further investigation.
Why choose a real-time FIM over baseline FIM?
Real-time FIM and baseline FIM serve similar purposes but have differences in their approaches and advantages. The following are a few benefits of real-time FIM compared to baseline FIM:
- Real-time FIM keeps a close eye on file modifications and immediately detects any unauthorized changes or suspicious activities. As a result, potential damage due to data loss is reduced, and prompt response to security incidents is made possible.
- Organizations can minimize possible downtime caused by security incidents by taking prompt action to mitigate risks and avoid further damage.
- By immediately alerting administrators of unauthorized modifications, possible malware infections, or insider threats, real-time FIM offers enhanced security. This aids in stopping security breaches and preserving the accuracy of important data and systems.
- Real-time FIM offers granular visibility into file changes, including details such as who made the changes, what changes were made, and when they occurred. This level of accuracy is useful for compliance and forensic analysis.
- Real-time FIM outperforms baseline FIM in dynamic environments where files and systems change often. It does not require recurring baseline updates because it adjusts to changes in real-time, providing continuous security.
- Whether they are small businesses or large enterprises, real-time FIM solutions are frequently scalable and flexible enough to meet changing organizational needs. Without compromising accuracy or performance, they can manage a large number of file modifications.
ManageEngine Log360 employs real-time FIM to monitor the files and folders in order to provide proactive and continuous protection against security risks, providing organizations the visibility and control they need to preserve the integrity of their data and systems in today's rapidly evolving threat landscape.
What are the primary components of file integrity monitoring?
The following are the 3 primary components for the functioning of FIM(refer figure 2):
- A database system: Cryptographic hashes of your files' and configurations' original states are stored in this database. The original files are also preserved, just in case a rollback is initiated to return them to a previous baseline of operation.
- Agents: These technical components measure the condition of devices and systems in order to track file changes, then they upload the data to the database for analysis and comparison.
- User interface: Users typically use a centralized web portal as the center for reporting, alerting, remediation, change management, and change control analysis.
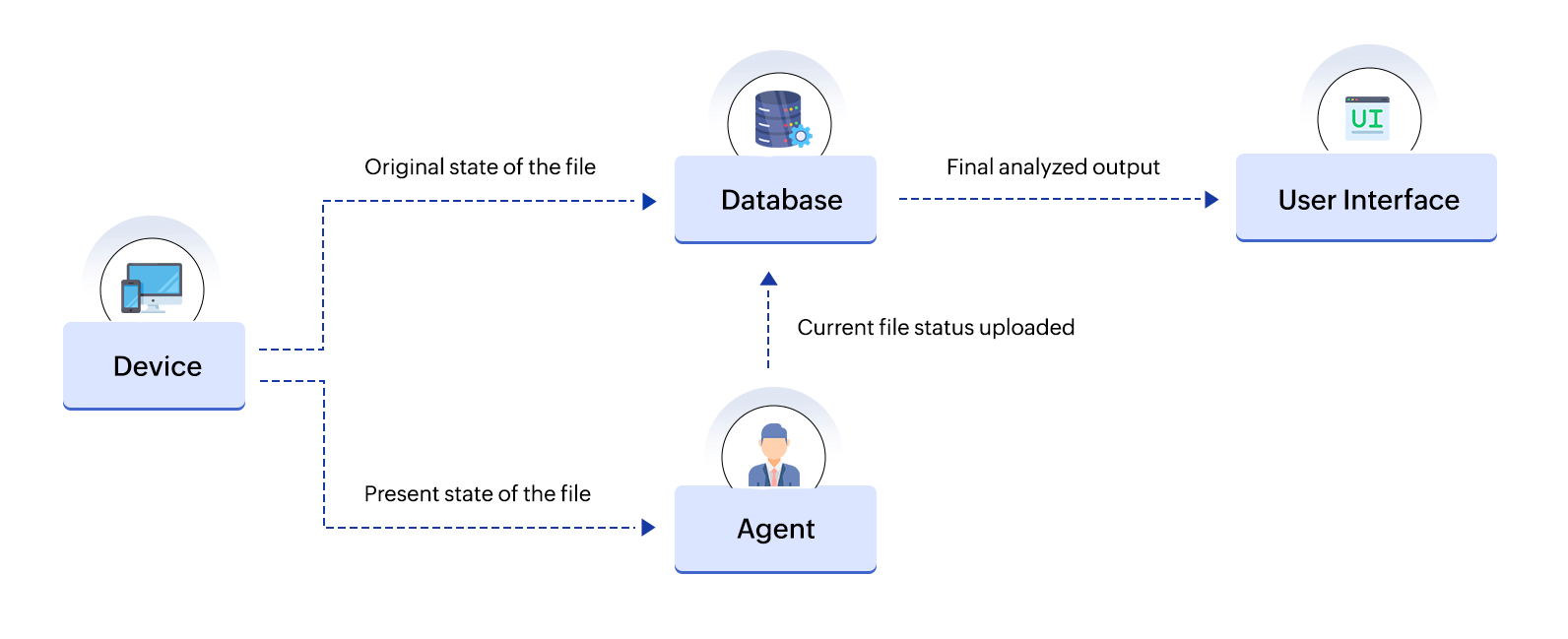
Figure 2: Components of file integrity monitoring
How does file integrity monitoring work?
Here is the process through which file integrity monitoring works(refer to figure 3):
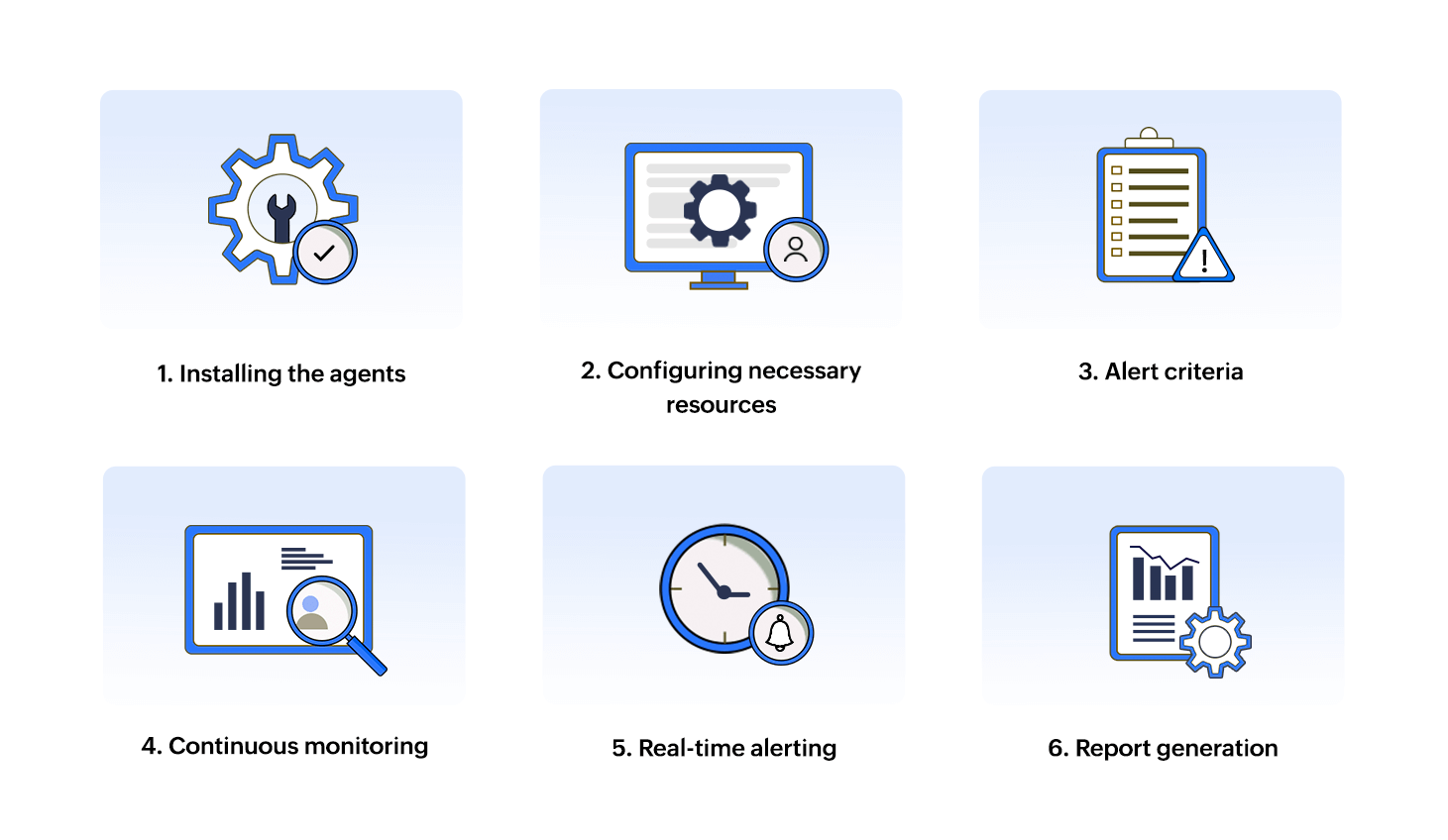
Figure 3: How does file integrity monitoring work?
- Installing agents: Agents should be installed on the device for which you want to monitor the files and folders.Once an agent is installed on a device, it gains access to the internal activities of the device and obtains the log data from it. Then, the SIEM server will index the logs and proceed further.
- Configuring necessary resources: The network components that must be watched over—including files, folders, and directory servers—must be specified when configuring FIM. Resources that hold sensitive data, and are more prone to improper handling can benefit from this.
- Alert criteria: By ascertaining the users' regular usage behaviors, an alert criteria can be set by the administrators. Then, using this alert criteria as a guide, FIM analyzes events occurring in real time.
- Continuous monitoring: After the relevant policies have been set up and an alert criteria has been established, the FIM module begins monitoring the files and folders in accordance with the policies.This aids in identifying any unusual activity.
- Real-time alerting: When an event crosses the set up threshold, an alert is generated and forwarded to the appropriate authority, who analyzes the issue and takes the required action to rectify it. These alerts may include details such as the type of change, the affected files or directories, and the time of the event.
- Report generation:All of the actions performed (creation, deletion, access, modification, or renaming) are represented to the users in the form of reports for identifying the threats effectively. Also, to provide proof of compliance with regulations like PCI DSS and HIPAA, FIM reports must be generated in order to compile every relevant information for auditing purposes.
To know more on the architecture and implementation of FIM, refer to this page.
FIM use cases
1. Insider threat detection: By monitoring theemployees' unauthorized and unusual file operations, FIM can help spot insider threats. Security teams are able to react quickly to any malicious activity or possible attempts at data exfiltration from within the organization.Also, to quickly determine the cause and scope of the security event, securely store the entire set of forensic data with FIM reports and dashboard.
2. Ransomware protection: FIM provides strong protection against ransomware by monitoring file creations and modifications. Security analysts can step in and stop the encryption of important information by responding quickly to any unusual spike in file changes that triggers immediate alerts
3. Compliance assurance:FIM is a useful tool for meeting compliance standards since it ensures the security and integrity of crucial files and configurations. FIM tracks all file and folder actions with integrated compliance management and file monitoring to provide comprehensive insights on user behavior, data access, privilege abuse, and more. Demonstrating compliance is made simple with the audit-ready compliance reports generated by FIM solutions.Organizations can utilize FIM solutions to demonstrate compliance with industry-specific laws and standards by taking a proactive approach to cybersecurity and data protection.
Why is FIM required in order to satisfy compliance requirements?
Compliance regulations mandate organizations to protect sensitive data and nurture a secure environment. File integrity monitoring is essential for maintaining compliance requirements since it assists organizations in meeting the security and data protection standards (such as such as PCI DSS, HIPAA, GDPR, and SOX) required by numerous regulatory frameworks and industry regulations. Here are a few more reasons on why FIM is necessary to ensure compliance:
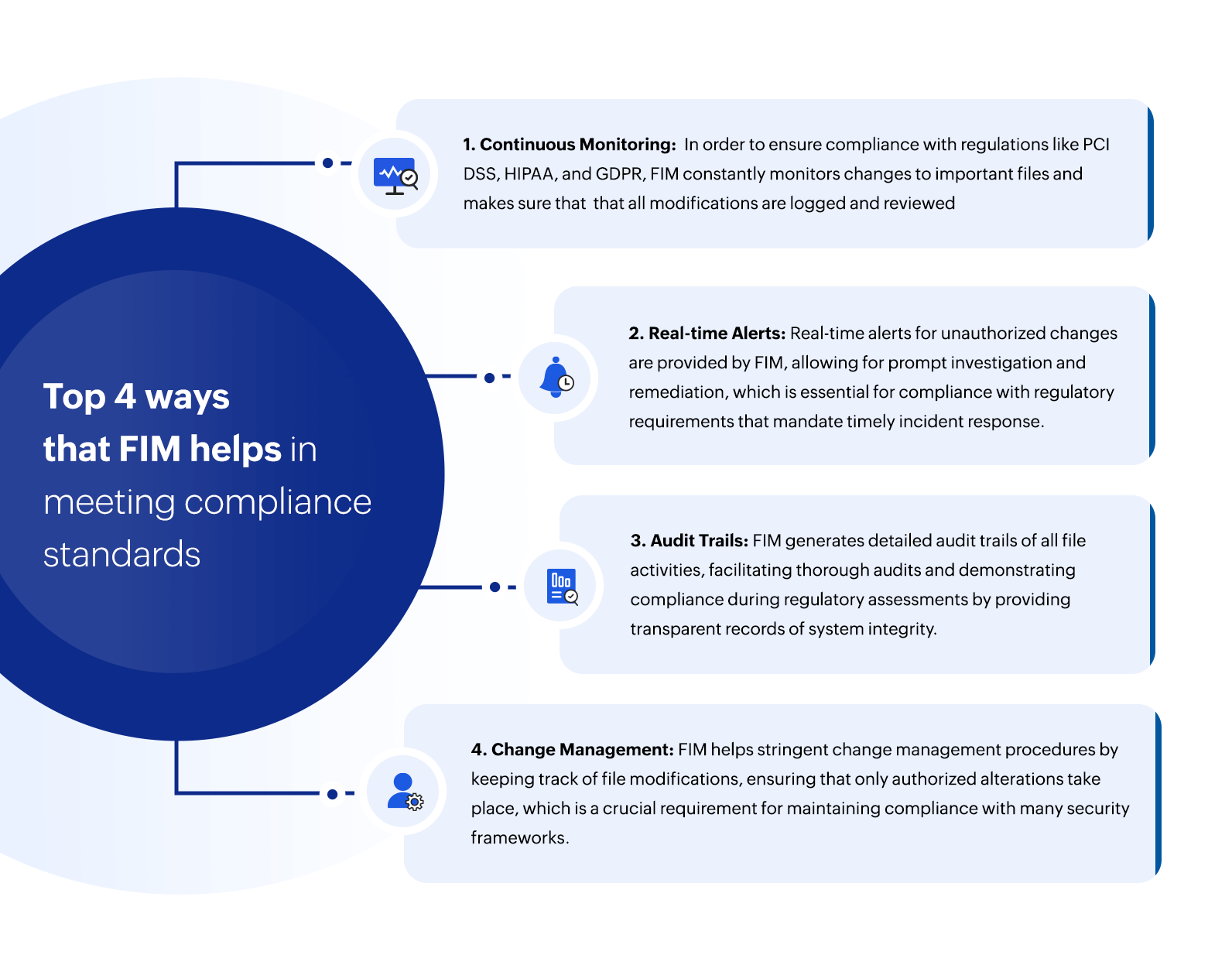
Figure 4: How FIM helps in meeting the compliance standard
- FIM enhances data protection and security by providing alerts when unauthorized modifications are identified. It enables organizations to continuously monitor files, directories, and configurations for any deviations from the specified policies, and provides out-of-the-box reports for major compliance mandates, including FISMA, PCI DSS, SOX, HIPAA, GLBA, GDPR.
- Organizations can access thorough audit trails of file modifications with FIM, which include information about the type of change, the file or configuration that was impacted, the user or process that made the modification, and the event's timestamp. In the event of a security incident, this information makes it easier to prove compliance with regulatory requirements and promotes accountability.
- In order to safeguard organizations from security risks and vulnerabilities, compliance regulations place a strong emphasis on risk management and mitigation techniques. By quickly identifying and reacting to unauthorized modifications, FIM assists organizations in managing security risks by decreasing the possibility of fraud, data breaches, and other security incidents that could result in financial losses, harm to their reputation, or legal repercussions.
Also, to know how file integrity monitoring help ensure the other compliance requirements in depth, check out this page. Also, to know how file integrity monitoring help in ensuring the PCI DSS requirement, check this page.
FIM in healthcare
In the healthcare industry, where safeguarding sensitive patient data is crucial, file integrity monitoring is an essential component of security. In order to identify any unauthorized changes or modifications, FIM involves continual monitoring and analysis of files and systems. Also, the patient data must adhere to strict privacy laws like HIPAA. Thus, FIM can improve the healthcare organization's security posture and reduce the chance of unauthorized access and data breaches.
File integrity monitoring can be valuable for the healthcare sector in several ways, such as:
- It can help in the identification of insider threats, by monitoring on employee actions and identifying any suspicious behavior, such as unauthorized access to important files or any other information.
- Assuring compliance to pertinent industry standards, cybersecurity regulations, and data protection law, including the HIPAA.
- Preventing data breaches by detecting and alerting administrators to suspicious activities or unauthorized access attempts in real time.
- Unauthorized access to patient information or manipulation of medical data can result in data theft. FIM prevents this by continuously monitoring files and folders for any unauthorized changes or modifications
- Keeping track of modifications to files and system configurations within the systems that store EHRs, helping to guarantee the confidentiality and integrity of important documents.
To know more on how data security in healthcare can be enhanced with file integrity monitoring, check this page.
FIM in education sector
The education industry can benefit immensely from file integrity monitoring (FIM), where it is essential to preserve sensitive data. FIM helps educational institutions in maintaining ensuring the confidentialityand integrity of their data repositories and systems.Educational institutions can improve their security posture and preserve the integrity of their digital assets by putting strong FIM solutions into place.
File integrity monitoring (FIM) can be a valuable for the educational sector in several ways, such as:
- Continuously monitoring files and folders for any unauthorized changes or modifications.
- Preventing data breaches by detecting and alerting administrators to suspicious activities or unauthorized access attempts in real time.
- Mitigating insider threats by monitoring user activity and identifying anomalous behavior patterns that might indicate unauthorized or suspicious activities by students, faculty, or staff members.
- Supporting incident response efforts by providing forensic evidence and detailed logs of file access and changes.
- Leveraging UBA to investigate suspicious file activities by employees, such as an unusual volume of file activity.
- Assuring compliance to pertinent industry standards, cybersecurity regulations, and data protection law, including the FERPA and the GDPR.
To know more about how the student data privacy can be protected with file integrity monitoring, check out this page.
FIM in banking and finance
The banking, financial services and insurance (BFSI) sector deals with a plethora of sensitive files that contain customer PII, account numbers, income statements, insurance claims and credit history. These files are stored and shared across diverse networks and devices, and are accessed by numerous users. Thus, maintaining the integrity of these files becomes tedious, making file integrity monitoring the most suitable change monitoring solution for this sector.
FIM helps to ensure data integrity in the financial sector in the following ways:
- Monitor unauthorized user attempts to read, write, and copy critical financial records, insurance agreements or income statements to safeguard data security and privacy.
- Detect suspicious file creation activities and attempts to modify or delete sensitive files in shared folders that are accessible to financial stakeholders to forbid data manipulation and tampering.
- Correlate suspicious file activities and file-related user behavior to identify potential insider threats.
- Trigger alerts in real time to identify suspicious user activities on critical file servers and systems to prevent data theft.
- Generates reports to comply with regulatory mandates like PCI DSS, GLBA, SOX and GDPR.
To learn more on how File integrity monitoring helps in preventing attacks related to banking and finance, visit this page.
FIM for enterprises
Enterprises are large, complex, and sophisticated networks with thousands of workstations populated with substantial volumes of data that are predominantly sensitive. These sensitive files are in continuous transit across the enterprise network and are stored, shared, and accessed by several users and entities, impacting the integrity of data. This makes a file change auditing solution like FIM imperative for an enterprise network. The essential capabilities of an enterprise FIM to bolster data security and sustainability are:
- File change auditing intelligence that fortifies the integrity of sensitive files and folders.
- File server audit to monitor critical files and folders in file servers and file shares.
- Correlate anomalous file activities and identify potential insider threats.
- Behavioral analysis of users and entities to determine risk scores based on file activities.
- Real-time alert generation to detect unauthorized file access, file change, data tampering, and data theft attempts as and when they occur.
- Adherence to regulatory compliance mandates by reporting file-based security incidents in real-time.
- Scalability to cater to the security needs of an expanding network.
To learn more on how File integrity monitoring helps in preventing attacks related to enterprise, visit this page.
10 things to take into account when choosing a FIM tool
- In order to identify unauthorized modifications to files, directories, and system configurations immediately as they occur, the FIM tool should have real-time monitoring capabilities.
- When unauthorized changes are noticed, the FIM tool should automatically generate alerts so that prompt response and remediation are achievable.
- Make sure the FIM tool offers granular visibility into file modifications, including details about the kind of modification, the impacted file or configuration, the accountable person or process, and the event's timestamp.
- Select a tool that is scalable with the size and complexity of your system, supporting a massive amount of files, directories, and endpoints without experiencing any performance lag.
- To fit the unique needs and security guidelines of your organization, look for a solution that provides flexibility and customization choices for monitoring policies, alerts, and reporting.
- To improve threat detection, response, and collaboration capabilities, take into account whether the FIM tool connects with other security solutions, such as SIEM platforms, incident response tools, and ticketing systems.
- Make sure that the FIM solution has extensive reporting features, such as audit trails, evidence of proactive monitoring, and records of security incidents and remediation measures to satisfy compliance needs.
- Choose a user-friendly tool with an intuitive, easy-to-use interface and a centralized management console for configuring policies, monitoring alerts, and managing settings.
- Pick a vendor that offers timely software updates for the FIM tool, including technical help for any problems or questions.
- Examine the FIM tool's performance and resource requirements to make sure it can function well without putting an undue burden on your network infrastructure or systems.
The role of a FIM integrated SIEM tool in file monitoring
Gartner considers file integrity monitoring (FIM) a compliance requirement and emphasizes the integration and evaluation of FIM capabilities with other technologies as part of its best practices. One of the most successful integrations for FIM tools is with a security information and event management (SIEM) solution.
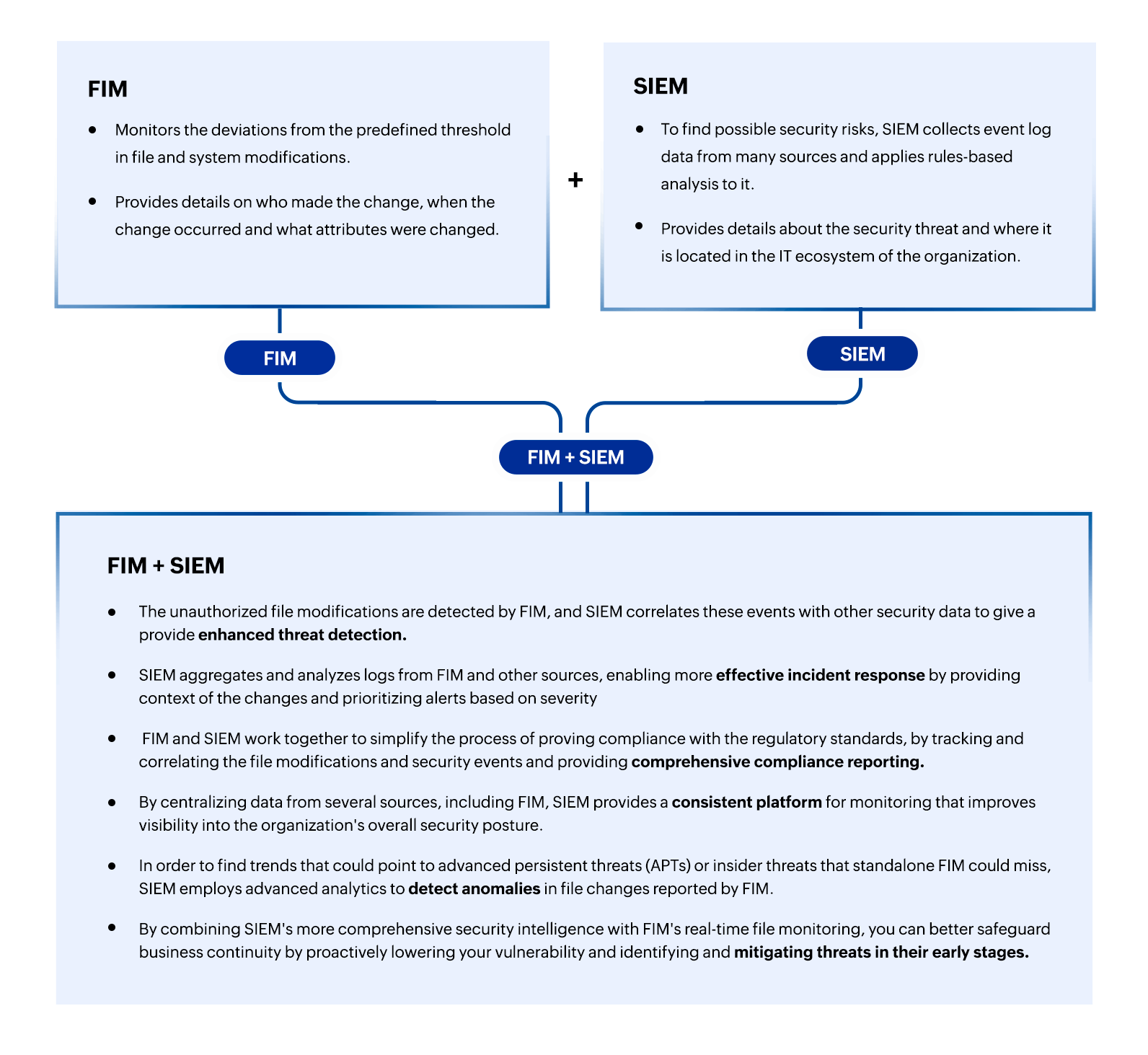
Figure 5: How integrating SIEM and FIM helps?
For enterprises looking to strengthen their cybersecurity posture, the combination of FIM and SIEM systems offer several advantages. Together, FIM's granular visibility into file changes, configurations, and system activities facilitates SIEM in identifying unauthorized file modifications and insider threats. Organizations can obtain a thorough understanding of security incidents and anomalies by using SIEM solutions to combine and correlate FIM data with other security events and logs from across the IT infrastructure. Also, organizations can identify and mitigate security threats more effectively with the help of these integrated technologies, which make threat detection, incident response, and forensic analysis more accurate and timely. Furthermore, by establishing the proactive monitoring and control measures taken to safeguard sensitive data and preserve the integrity of vital systems, makes compliance reporting easier.
The following are the necessary abilities for efficient file integrity monitoring:
- Monitoring of changes to system configuration to ensure that your cloud network, services, and apps are safe and satisfy your requirements.
- Auditing the creation, modification, and deletion of files across servers.
- In-depth reporting on modifications to make analysis and troubleshooting easier
Thus, the combination of FIM and SIEM systems improves an organization's overall security posture and resistance to evolving threats by enhancing its capacity to identify, respond, and mitigate cybersecurity risks.



