SharpHound is a data collection tool that is a part of the BloodHound framework, primarily utilized for reconnaissance in AD environments. Let's understand the usage and severity of this tool, how it can be exploited, and how we can detect its usage in Log360.
What is the BloodHound framework?
BloodHound is a MITRE-listed open-source software used for analyzing and visualizing relationships within an AD environment. Developed by SpecterOps, BloodHound enables security professionals to uncover potential attack paths and identify high-risk users by using a graph database and calculating the shortest path between objects by using its links. BloodHound collects data by using an ingestor called SharpHound.
Attack Summary
- Environment: Active Directory
- Objective: Data collection for attack profiling, reconnaissance, and decoding domain level permissions for compromise.
- MITRE ATT&CK phase(s): Reconnaissance, Collection, Privilege Escalation, Lateral movement
- Risk score: Stealthy attack, Medium level difficulty to detect.
Understanding SharpHound
SharpHound, a part of the BloodHound tool set, is specifically designed for data collection within AD environments. Developed in C#, SharpHound gathers detailed information about users, groups, computers, permissions, and other relevant data points. It extracts the sensitive information from the AD and archives this data as a single zip file.
Sysadmins can use SharpHound from a defensive standpoint to identify complex attack paths that may pose security risks within an AD. However, it can also be leveraged by the adversaries for in-depth reconnaissance.
How does the data collection in Sharphound work?
SharpHound can be executed either as a .exe or as a PowerShell script, both options contain the same assembly code, although the PowerShell script version may be shortened. When executed, it collects information about the AD.
< Collecting data from systems which most likely have user session data >
< Limiting data collection based on a search >
- SharpHound, however, operates within the permissions of a regular user account, to gather information from the AD environment. It doesn't need any elevated permissions.
- It outputs the collected data in JSON format, making it structured and suitable for further analysis.
- The JSON files generated by SharpHound are fed into Neo4j database, which is a graph database management system for storing and querying graph-based data structures.
- In the context of BloodHound, the collected data about users, computers, groups, permissions, etc., are represented as nodes and relationships within the Neo4j database.
- Once the data is stored in the Neo4j database, it can be visualized using a the BloodHound GUI for visualizing the relationships and paths of attack within the AD environment.
Which stage(s) of a cyberattack can leverage SharpHound?
| Domain | Technique ID | Technique name | Use |
|---|---|---|---|
| Enterprise | T1560 | Archive Collected Data | BloodHound can compress data collected by its SharpHound ingestor into a ZIP file to be written to disk. |
| Enterprise | T1106 | Native API | BloodHound can use .NET API calls in the SharpHound ingestor component to pull AD data |
| Enterprise | T1069.002 | Permission groups discovery Domain groups | Egregor can conduct AD reconnaissance with tools like SharpHound and ADfind. |
Source: MITRE ATT&CK
- Reconnaissance:
SharpHound gathers detailed information about AD objects, such as users, groups, permissions, and trust relationships. Typically, BloodHound can use .NET API calls in the SharpHound to pull AD data.
- Privilege escalation:
Sharphound can gather information on domain-level permission groups, which can help adversaries determine the misconfigured permissions and users with elevated permissions, such as domain administrators.
- Credential theft:
SharpHound helps attackers identify high-privilege accounts or accounts with weak passwords, which can be targeted for credential theft.
- Collection:
SharpHound aids in compressing and/or encrypting the data prior to exfiltration. This can help minimize the amount of data sent over the network. Here, BloodHound can easily compress the data collected by its SharpHound ingestor into a ZIP file.
- Lateral movement:
SharpHound's insights into the AD environment enable attackers to identify paths for lateral movement, allowing them to move laterally across the network and escalate privileges further.
How can Sharphound files be detected?
Local configuration of SharpHound Enterprise occurs within two files, both located within the installation directory of the service. (Default location is C:\Program Files (x86)\SHService)
The most common process name or the file name originally ends with SharpHound.exe or SharpHound.ps1.
However, just blocking the executables is not enough, given that SharpHound is a stealthy tool. It requires a combination of network monitoring, endpoint detection, and behavioral analysis.
- Network traffic analysis: Monitoring network traffic for suspicious patterns or communication with known C2 servers used by SharpHound.
- File integrity monitoring: Monitoring event ID 5145, which means to audit attempts to access files and folders on a shared folder, is one imperative detection mechanism which can help you identify suspicious file access and modification.
- Endpoint monitoring: Monitoring suspicious activities on endpoints, such as unusual processes or file accesses associated with SharpHound/BloodHound execution.
- Behavioral analysis: Using anomaly detection techniques to identify unusual data collection activities within the AD environment, which may indicate SharpHound reconnaissance.
How can Log360 help with SharpHound detection?
Log360 is an SIEM solution which helps you with the SharpHound detection in several ways.
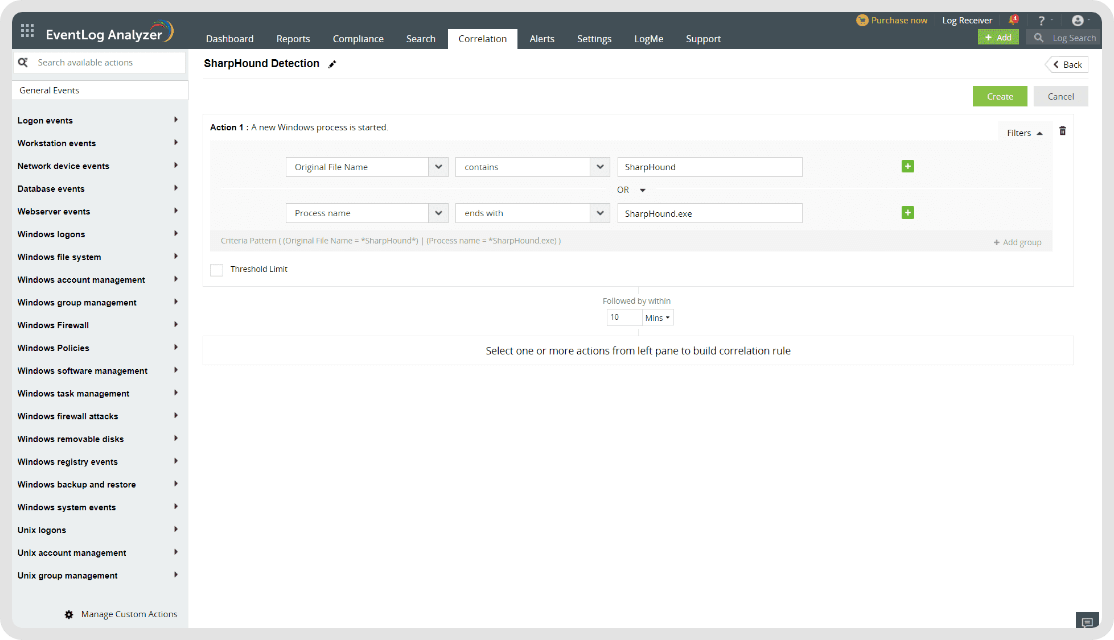
Predefined correlation rules
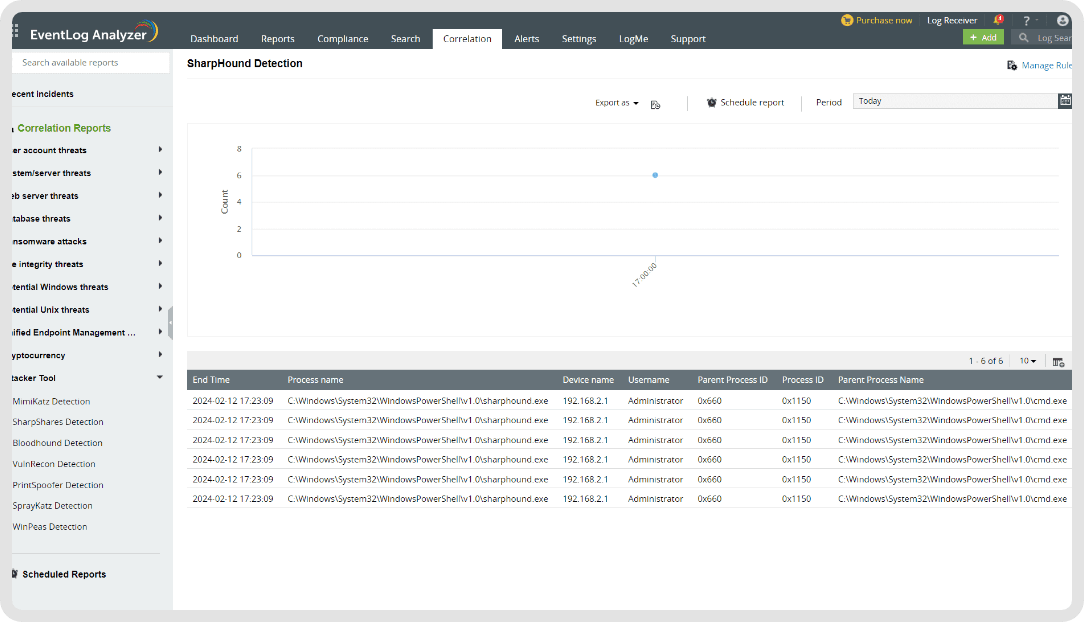
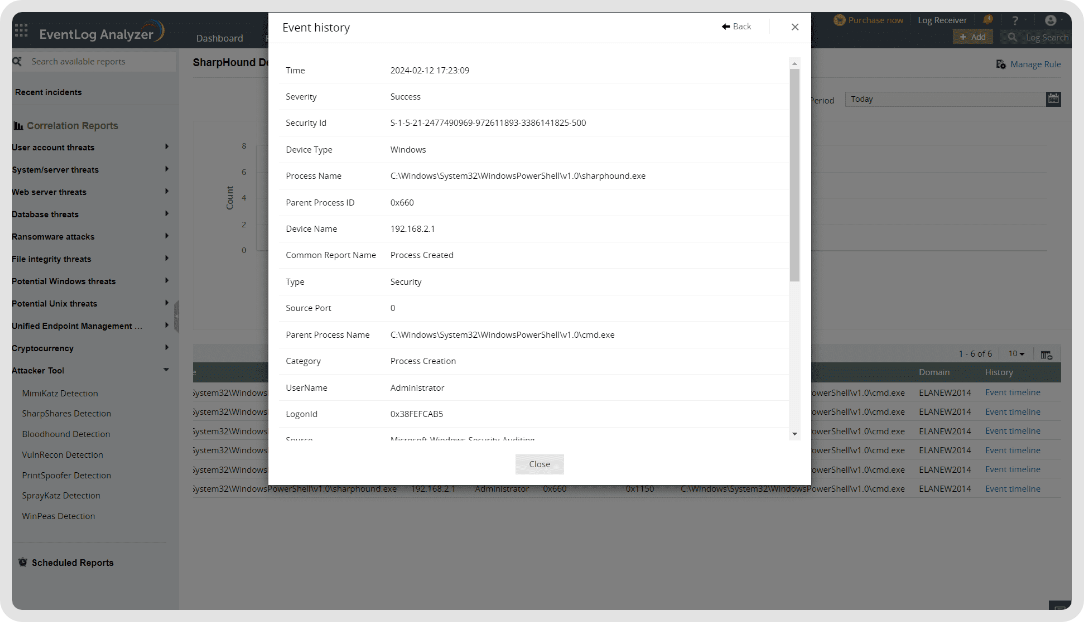
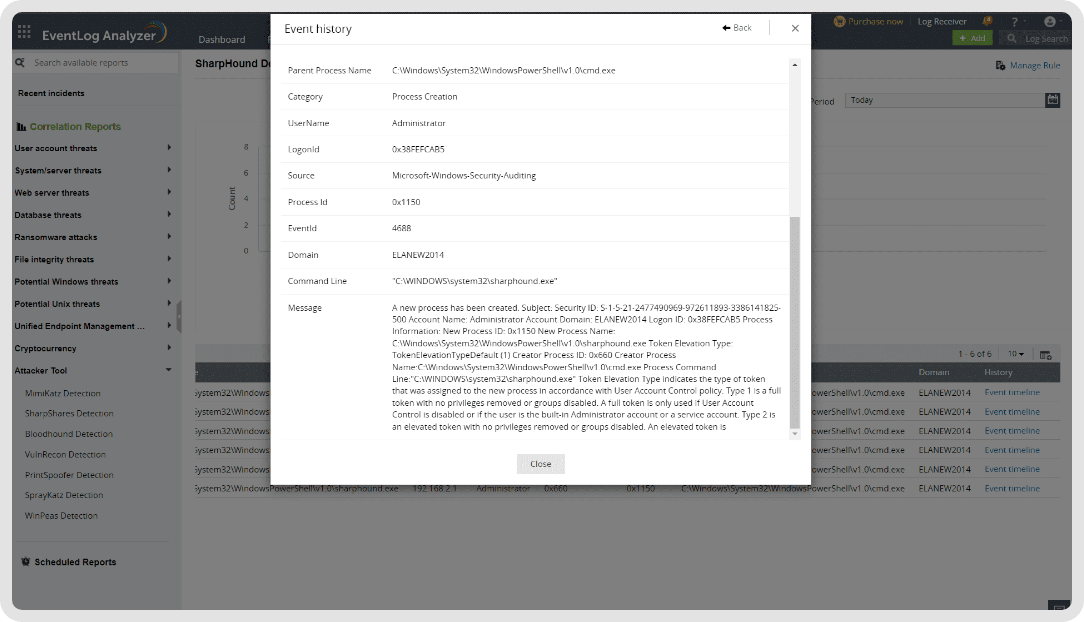
Log360 helps with predefined event correlation rules, which when met, the solution raises an alert for SOCs. In the SharpHound detection context, an immediate alert is raised when the the original file name or the process name contains "SharpHound" in it.
What's next?
Interested to explore how Log360 uncovers SharpHound attempts with real-time visibility and alerts? Get in touch with our solution experts
- What is the BloodHound framework?
- Understanding SharpHound
- How does the data collection in Sharphound work?
- Which stage(s) of a cyberattack can leverage SharpHound?
- How can Sharphound files be detected?
- How can Log360 help with SharpHound detection?



