Scalable and resilient architecture
Built on a distributed, high-availability architecture to support growing log volumes while ensuring uninterrupted collection, indexing, and analysis.
Learn more
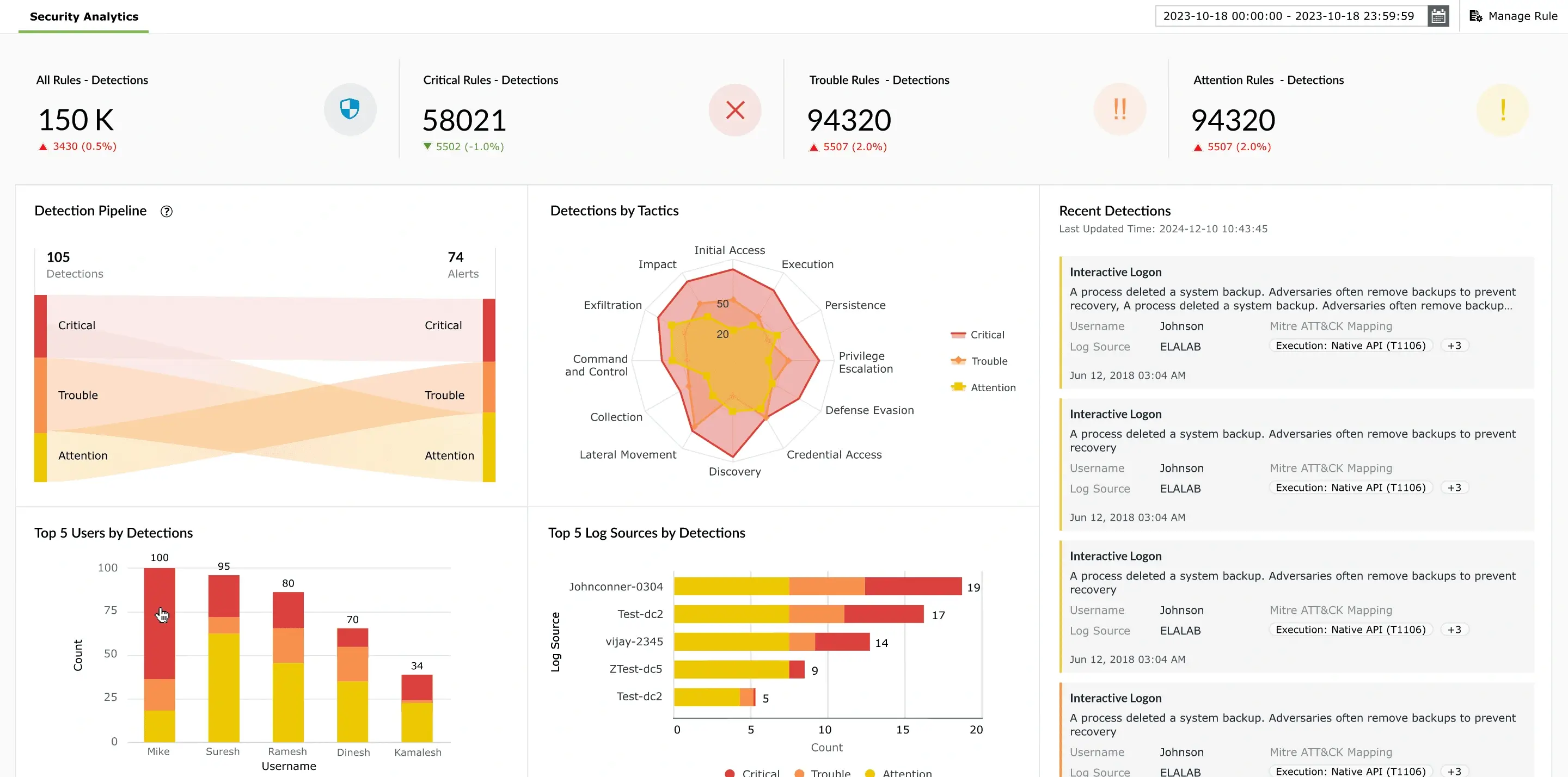
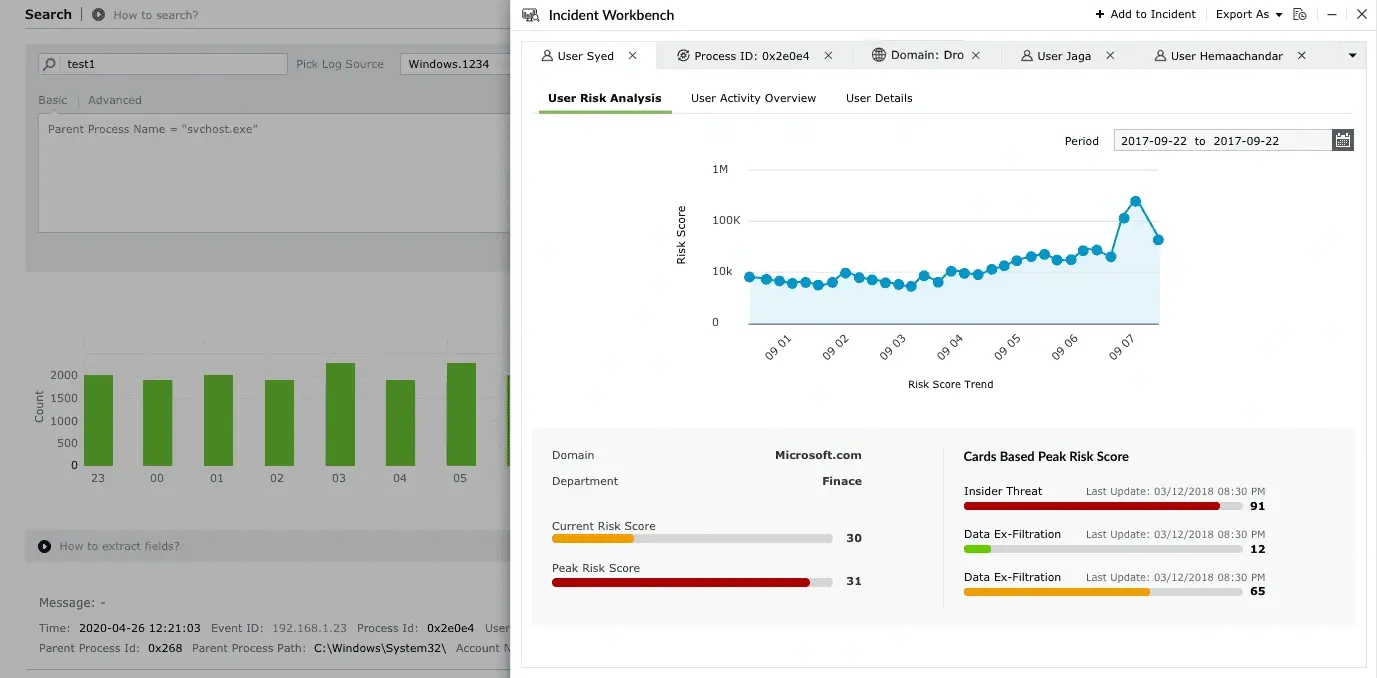
Real-time security analytics
Delivers unified insights across endpoints, networks, and cloud environments, enabling faster detection, investigation, and response.
Learn more
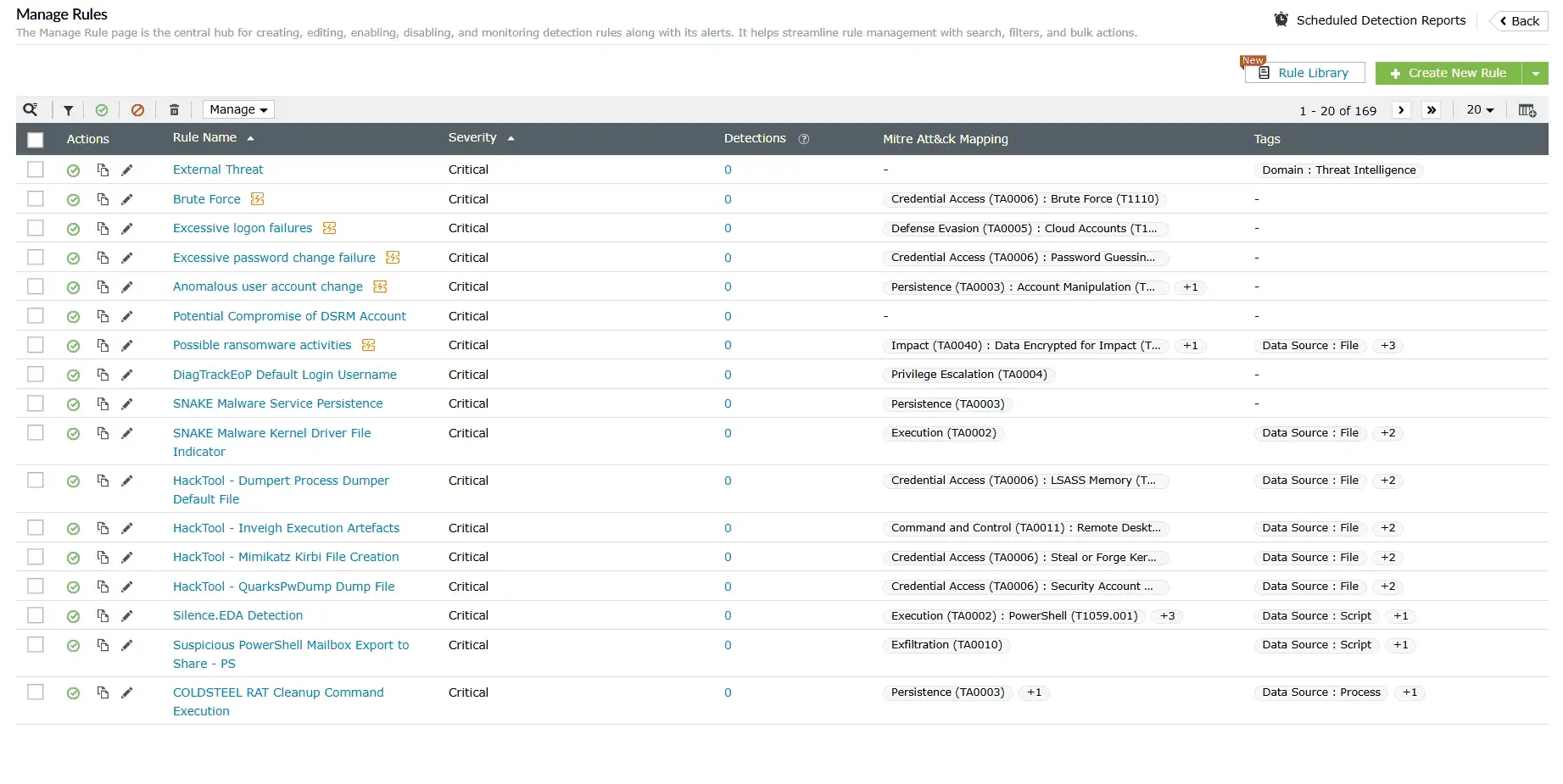
Automated incident response
Leverages prebuilt playbooks to automate alerts, notifications, and remediation, minimizing response time and reducing impact.
Learn more
External and dark web intelligence
Combines threat, credential, and attack surface intelligence to provide visibility into emerging risks, exposed assets, and compromised data across external sources and the dark web.
Learn more
Streamlined compliance management
Simplifies adherence to over 30 regulatory mandates including the GDPR, HIPAA, the PCI DSS, and more with secure log archiving and audit-ready compliance reports.
Learn more
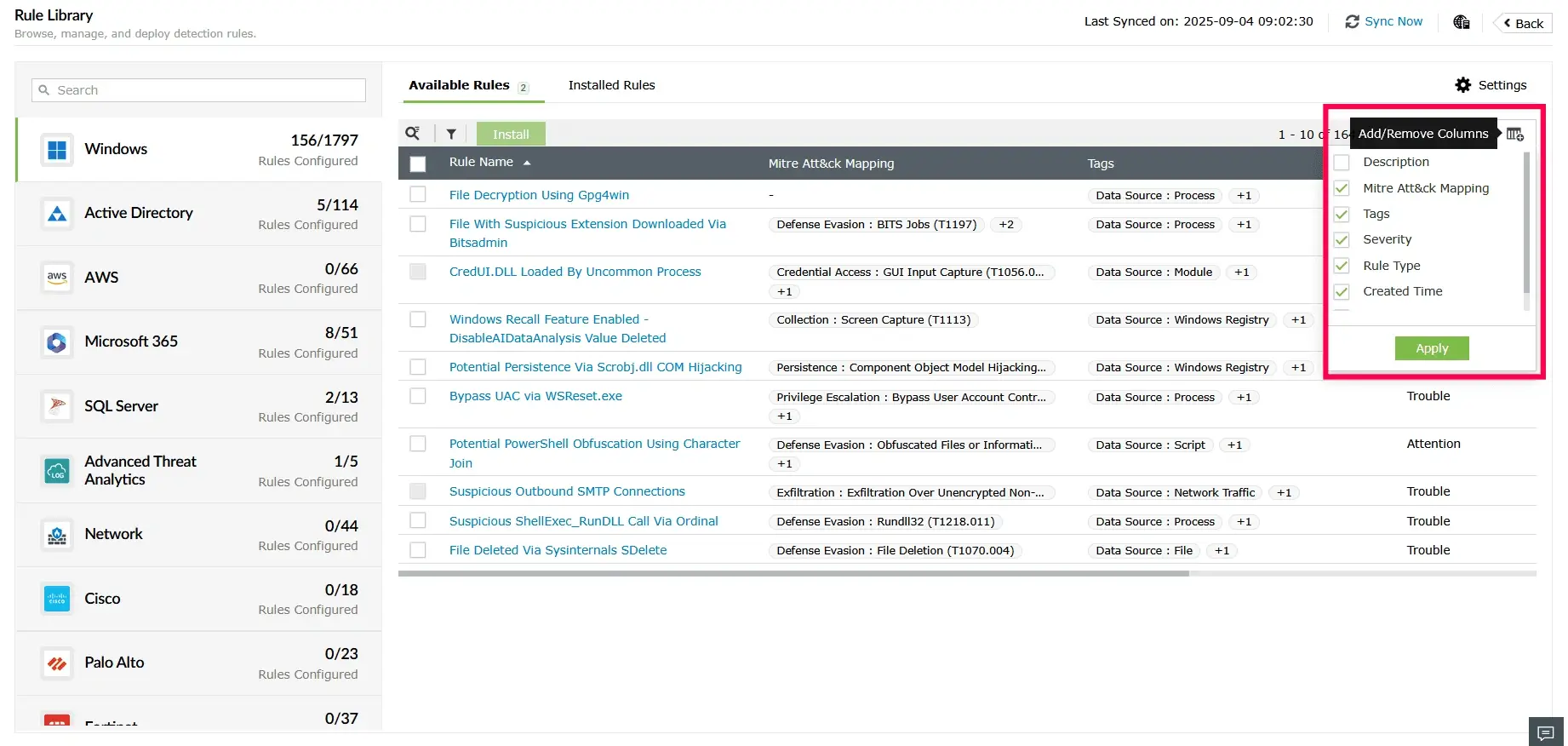
Flexible, extensible security ecosystem
ntegrates seamlessly across hybrid infrastructures and extends capabilities seamlessly without disrupting ongoing operations.
Learn more